The public-facing internet is a vast, interesting, and complex space, and at Censys, we’ve made it our mission to help folks understand what’s on it. It’s why we’ve built the most comprehensive, accurate, and up-to-date map of global internet infrastructure available, what we call the Censys Internet Map.
This map offers an unparalleled view of the internet. No other source offers the same breadth and depth of scanning, or the context to go with it. This makes our data very relevant to cybersecurity efforts. Researchers, enterprises, and governments use our data as part of their threat hunting and exposure management efforts.
You can explore the map’s data using our Censys Search tool. Censys Search is exactly what it sounds like: a tool to search the internet. It’s styled just like a typical search bar, and anyone can access a community version of it by visiting search.censys.io and creating an account. Users can unlock advanced Censys Search capabilities, including pattern matching searches (more on this below), higher search limits, access to historical data, and more with a paid license.
As with any search engine, getting the information you’re looking for requires knowing what to ask. And to do that in Censys Search, it means creating Censys queries.
Your Query Starter Pack: A Review of the Essentials
Queries are the “language” that Censys Search speaks. This language is pretty intuitive, but for those fresh to Censys Search, understanding common queries can help you get to what you’re looking for even faster. Keep in mind that there are lots of filters and parsing fields within Censys Search that help make digging further into query results easy.The best place to find a complete, detailed explanation of our query language is our search language guide. In it, you can also find a comprehensive list of all of the fields that can be searched within our dataset (spoiler: there are a lot).
That said, consider the following for quick reference of some of the most common types of Censys queries:
Services:
IP Addresses & Subnets:
Autonomous Systems:
Certificates:
Operating Systems & Products:
Click below for an at-a-glance view of more common Censys Search queries.
Leveling Up: Combining Query Inputs
With basic queries mastered, you may want to conduct more detailed searches with queries that combine inputs. For example, rather than just looking for a certain type of service, you may want to look for that type of service in a specific location.
You can find examples of how to combine inputs below:
Services in a specific location:
services.service_name: MODBUS and location.country: Germany
Hosts based on geographic coordinates:
location.coordinates.latitude: 40.78955 and location.coordinates.longitude: -74.05653
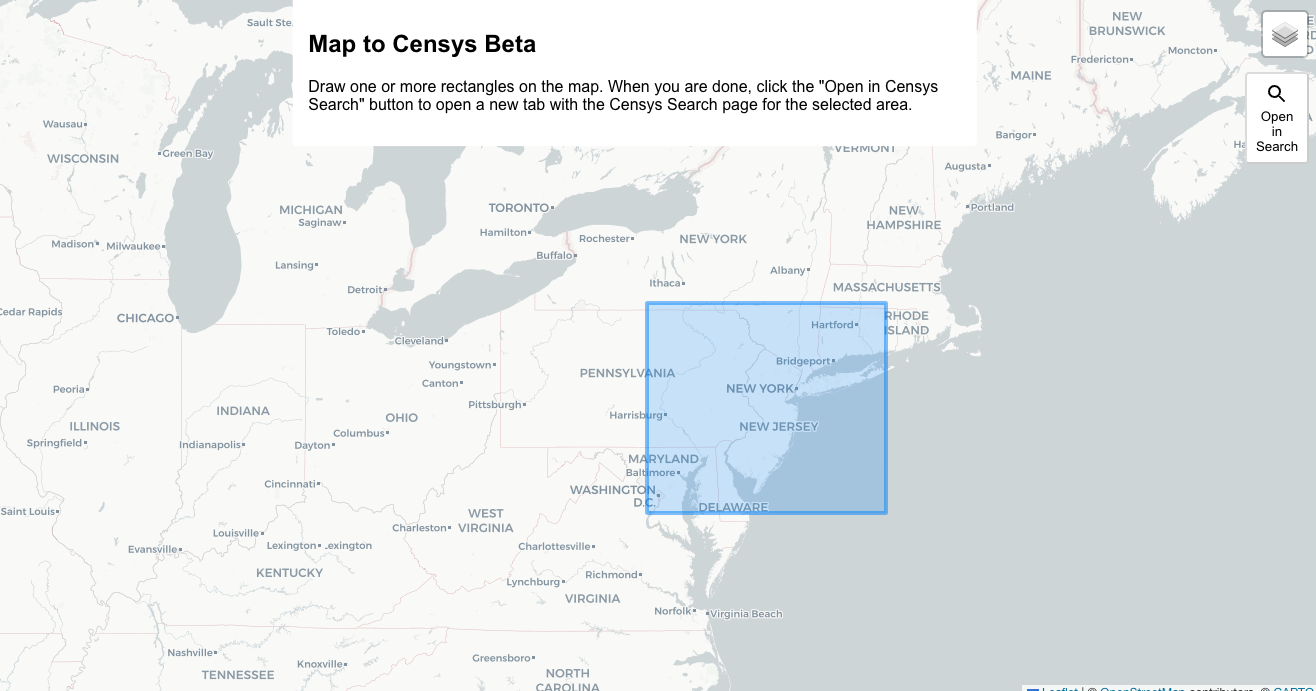
Pro Tip: Use our beta feature Map To Censys Beta to draw a box over the geographic area of interest and click “Open in Search” to see hosts in the area.
Unexpired certificates for a specific domain:
labels=`unexpired` and names: censys.io
Self-signed certificates observed in Censys host scans:
ever_seen_in_scan: true and labels: “self-signed”
Trusted certs from a specific CA expiring on specific day:
parsed.issuer.organization: “Let’s Encrypt” and labels: “trusted” and parsed.validity_period.not_after: 2023-10-13
Specific range of IPs:
ip: [1.12.0.0 to 1.15.255.255]
A specific service on a specific port:
same_service(services.service_name: HTTP and services.port:1337)
Exploring Nefarious Activity & Other Interesting Artifacts
Censys Search can be used for more advanced exploration into the global internet infrastructure, including for the purposes of threat hunting. In fact, at Censys our own researchers have used Censys Search to uncover evidence of Russian ransomware, which you can read about here. Queries that someone conducting a more advanced investigation might find useful include:
Open directories:
services.http.response.html_title: “Index of /”
Cobalt Strike:
services.cobalt_strike: *
Compromised MikroTik Routers:
services.service_name: MIKROTIK_BW and “HACKED”
Services on port 53 that are not DNS:
same_service(services.port: 53 and not services.service_name: DNS) and services.truncated: false
Network devices with exposed login pages:
same_service(labels:{network.device, login-page})
If you’re hunting for threats, you may be interested in uncovering Command and Control infrastructure, and can use queries like:
Deimos C2:
same_service((services.http.response.html_title=”Deimos C2″ or services.tls.certificates.leaf_data.subject.organization=”Acme Co”) and services.port: 8443)
Posh C2:
services.tls.certificates.leaf_data.subject_dn: “C=US, ST=Minnesota, L=Minnetonka, O=Pajfds, OU=Jethpro, CN=P18055077”
Advancing Your Search with Regex Queries
Censys Search users with a paid license can run Regular Expression (Regex) queries to unlock advanced search capabilities. Regex queries give users more flexibility to define their search criteria. Rather than submitting a query limited to a single static string, users can run Regex queries that ask Censys to identify patterns in the data.
For example, a Community user might run a query that asks: “Which (unnamed) hosts with an HTTP service contain a reference to any string containing .js?” using the static string query: services.http.response.body:*.js*
A user with a paid subscription to Censys Search could broaden their criteria with a query that asks: “Which hosts have an HTTP location header that includes the sequence ../ (which is vulnerable to directory traversal attacks), followed by one of the more common executable page types like .js, .php, or .asp?” using the Regex query: services.http.response.headers.location=/.*(\.\.\/)+.*(\.asp|\.php|\.js|\.cgi).*/
Regex queries are best used when simple pattern matches won’t suffice, and are ideal for fields whose values are long strings. Popular hosts to write Regex expressions for are “http.response.body” and “services.banner.”
Additional examples of Regex queries include:
You can find a guide to Regex query syntax that explains how to use all of the backslashes, periods, and other placeholder characters, here.
Incident Response: Queries for a Zero-Day
Censys Search can also be a valuable tool when responding to a zero-day. When a critical vulnerability hits, security teams need to know if their networks are affected. To do so, they can run queries on Censys Search to determine if assets have been compromised by the attack. For example, during this year’s MOVEit CVE, users could run this query on hosts to identify potentially vulnerable assets:
services.http.response.favicons.md5_hash=af8bf513860e22425eff056332282560
When a zero-day hits, the Censys Research team deploys rapid response articles that explain the scope and impact of the attack, and include the queries that users can run to determine if they’ve been affected.
Additional examples of zero-day queries include:
Meta Pixel Trackers
Customers have also recently used Censys Search to determine the presence of Meta Pixel trackers. The Meta Pixel Javascript code tracks website user activity through cookies; however, when present on healthcare-related websites, patient information may be sent back to Meta, which is not a business associate of HIPAA-covered entities. For Meta to receive any patient data, patient consent is required. Censys customers used the following query to determine the presence of Meta Pixel code on their websites:
services.http.response.body:“fbq(‘track’, ‘PageView’);”
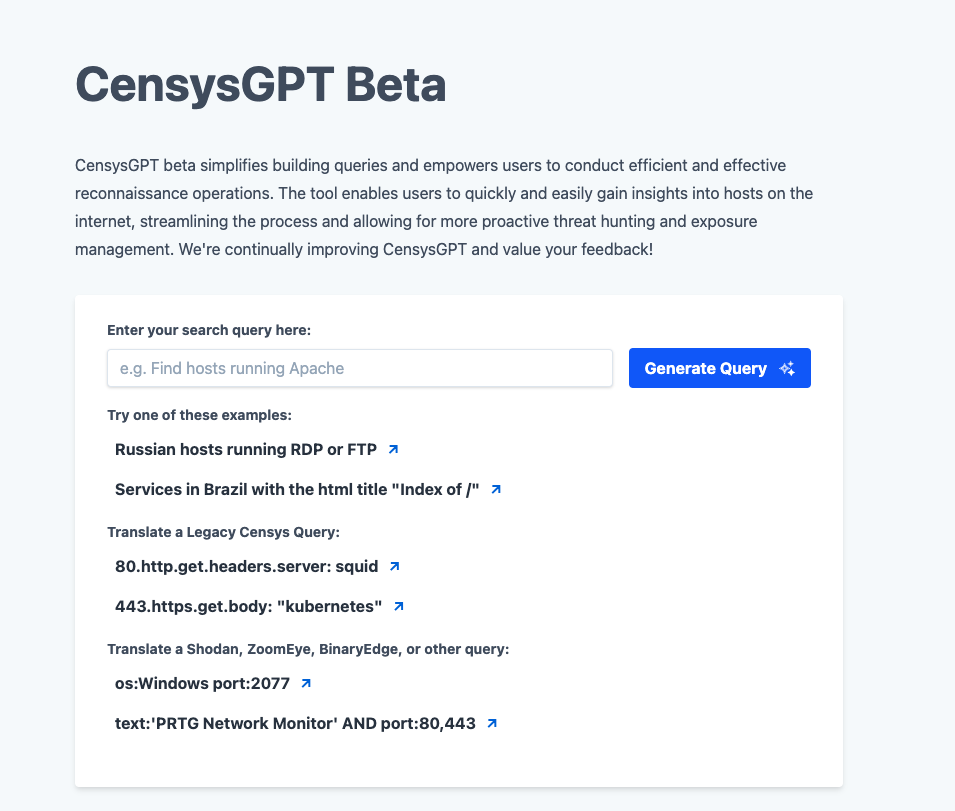
No Need to Get Lost in Translation with CensysGPT
Censys may offer the best view of the internet, but we know it’s not the only view. If you’re familiar with other query languages, you can use CensysGPT to automatically convert your queries into Censys queries. You can access CensysGPT right from the Censys Search home page. With CensysGPT, there’s no need to let the nuances of query language slow down your investigation! Try it out here: gpt.censys.io.
The Tip of the Iceberg
The Censys Search queries we’ve shared here are just the tip of the iceberg. There are many, many different types of queries that security practitioners, government agencies, and others can run to find what they’re looking for. And Censys Search has a whole host of indexing and parsing fields that can be used to drill down into a search result and refine an investigation.
Check out our Threat Profiler’s Playbook or our Where the Weird Things Are: Investigating Unusual Internet Artifacts with Censys Search ebook for more query examples.
Ready to query? Head on over to search.censys.io to get started! To unlock advanced search capabilities, reach out to our team today to learn more about the advantages of a paid license.
Learn More