Resource Hub
Filters Added:
-
BlogCenseye: Gadgets!
-
BlogLet’s Look for Bad Stuff Using Censys’ “Suspicious-Open-Directory” Label!
-
BlogFrom Vulnerable to Vigilant: 3 Critical Actions to Protect Healthcare from Cyber Threats
-
BlogWhat Does the Best Data Really Mean?
-
BlogHighlights from the New Unleash the Power of Censys Search Handbook
-
BlogSecuring FinServ: Exploring Cybersecurity Challenges in Financial Services
-
BlogLeveraging Censys Data: From the Classroom to Improving an Internet Monitoring Public Service
-
BlogProactive Cybersecurity: How to Achieve NIST CSF 2.0 Objectives with Censys
-
BlogBack to the Future: How Historical Data Can Enhance Your Cyber Defenses
-
BlogSuperior Internet Intelligence for Advanced Cyber Threat Intelligence Services
-
eBookThreat Hunting 101: Your Guide to Outsmarting Adversaries
-
Blog24 Questions to Ask About Your Data in 2024
-
BlogThe Perils of False Positives
-
eBookHow to Find Hacked Web Servers with Censys Search
-
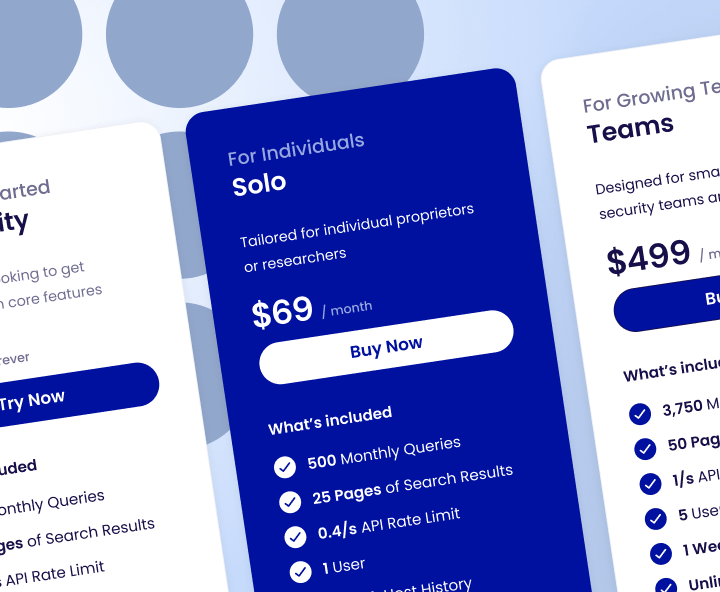
BlogIntroducing Censys Search Solo – The IOT Search Engine
Attack Surface Management Solutions
Learn more