According to the 2022 Verizon Data Breach Investigations Report, web servers are the top asset most commonly impacted in breaches. This is not surprising – after all, web servers often make up the bulk of an organization’s Internet-facing infrastructure, and therefore are more likely to be exposed than other types of digital assets.
Finding hacked web servers can be useful in a number of ways:
- Defenders can track threat actors as they’re working, meaning they can quickly locate the affected hosts and immediately take action before any further damage is done
- Researchers can track insecure servers and monitor trends in adversary behavior and methodology, learning from these attacks in order to hopefully prevent similar future attacks.
There are endless methods of hunting for affected web servers. In this article, we’ll show you one way to find hacked web servers using Censys Search to get you started. Navigate to search.censys.io to follow along.

Finding hacked web servers using Censys Search
We’ll begin with one of the simplest ways to find defaced web servers: searching for the string “hacked by”. Threat actors commonly “sign their work” by leaving a message on a website, such as “Hacked by [actor handle]”. Think of it like an artist’s signature on a work of graffiti. Luckily these signatures help defenders and researchers who are hunting for affected web servers. We can use Censys to search for these affected sites all over the world simply by looking for defacements.
Our simple query will restrict results to Censys-visible HTTP servers that include the string “hacked by” on their web interface. We can include virtual hosts in these search results by first toggling the gear icon on the search homepage and selecting “Virtual Hosts: Include” as seen below.
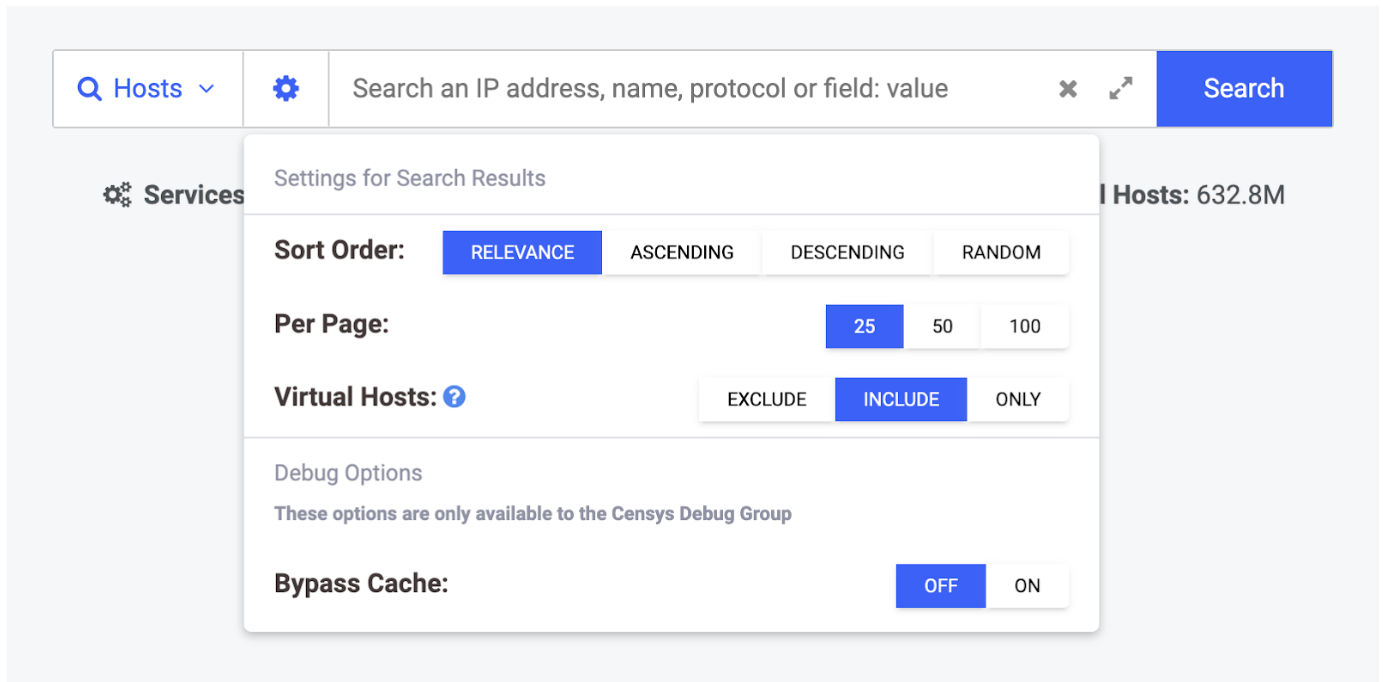
Next we can run our search by typing in this query and clicking “Search”:
services.service_name=`HTTP` and services.http.response.html_title:”hacked by”
This will grab all Censys-visible hosts running HTTP, regardless of which TCP port it’s running it on.
Based on the search results that come back and the highlighted text, you can immediately see that we’re uncovering some gems with this approach.
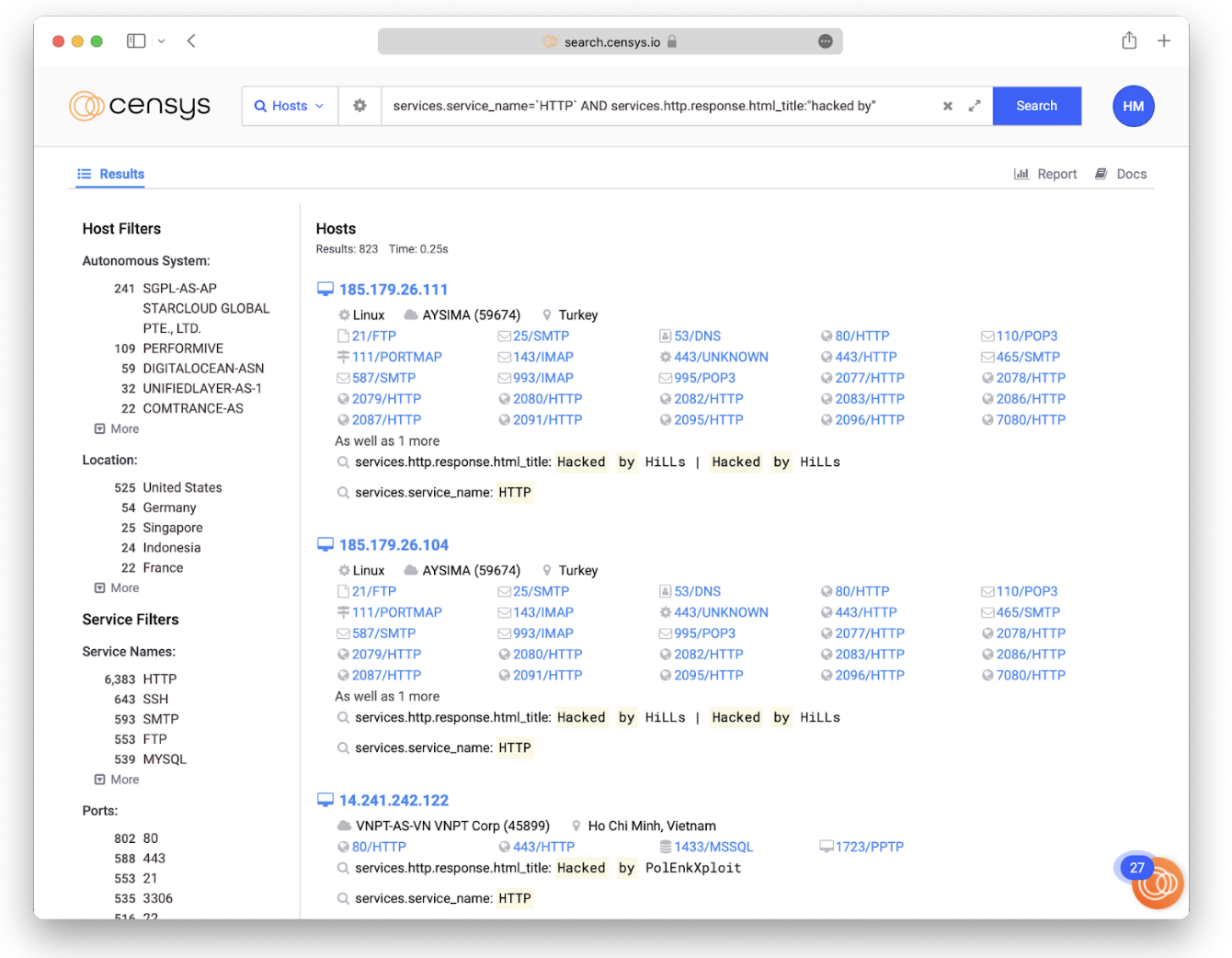
Spot-checking the search results can be used to confirm the value of this approach — it has a high true positive rate. When accessing these hosts be sure to use a secure method such as a VPN, proxychains, or Tor.
We can narrow down these results further based on what we’re interested in. Some additional filters you may want to add in specific use cases:
- If you run a network (for example a university, a hosting company, or an Internet Service Provider) or need to triage reports for your clients, you can constrain this query — for example, if you work at a national CSIRT organization you can filter by the “location.country” attribute (e.g. just add “AND location.country: [your country]” to the above query).
- If you’re working for a state government and helping your organization identify successful hacking events, you can filter by the “location.city” attribute.
- If you are running an Internet Service Provider, you can filter by your autonomous system number using the “autonomous_system.asn: [your asn]” attribute. Using the API you can make these calls on a regular basis and keep updated as we find these servers.
For Defenders: What to do if you find hacked servers tied to your organization
Reactive version: you’re responding to a breach after the fact
If you’re doing damage control, you have a bit of a challenge ahead of you. However, there are a great deal of helpful guides and tools from people who’ve been in your shoes (and there are many who have, you aren’t alone!) which may prove useful if you’re reacting to a breach. Dreamhost and Sucuri both offer guides on cleaning up after a website hack, which are both great first steps.
Initially, you’ll need to remove the problematic content, restore the site from a backup, close security gaps that you’ve uncovered after tracking the attack(s), and add some security tooling around it in order to prevent future issues. Ideally, you’d want to react by reinstalling your breached systems onto an updated, secured platform, but we realize that’s very often not a realistic option for most companies.
As Censys never attempts to gain access to any of the hosts across the Internet (we strongly believe in good Internet citizenship) we don’t collect any data on how a server is hacked. However, Censys data can help you identify the possible routes that an adversary took to access your system. An example would be that perhaps an attacker left FTP on, which you would be able to see with a bit of forensic analysis. This creative analysis is key so that you can determine what happened to close the security gap and prevent it from happening again. Censys can give you the critical visibility into Internet-exposed services that you need in your threat hunting efforts and help you find attacker trails and behaviors in order to track, pivot, and protect your organization.
Without the knowledge that you have hacked web servers tied to your organization, threat actors could continue damaging your systems for years to come. So even though finding that you’ve been affected by adversaries can feel like a defeat, you’ve still done the work to locate those problematic hosts and address the security gap before it gets any bigger.
For Researchers: Discover and track trends across the Internet
If you’re a researcher, the types of security trend data you can uncover in Censys can be highly useful for existing research projects and for brainstorming new projects.
A suggested first step is to begin exploring interesting Internet-wide security trends by analyzing data on a global scale with Censys searches, relying on our report builder function:
Let’s build a report from the search results we uncovered earlier in this post, aggregating by the country each web server is hosted in using the “location.country” field. We can make the data more or less granular by adjusting the “Number of Buckets” field.
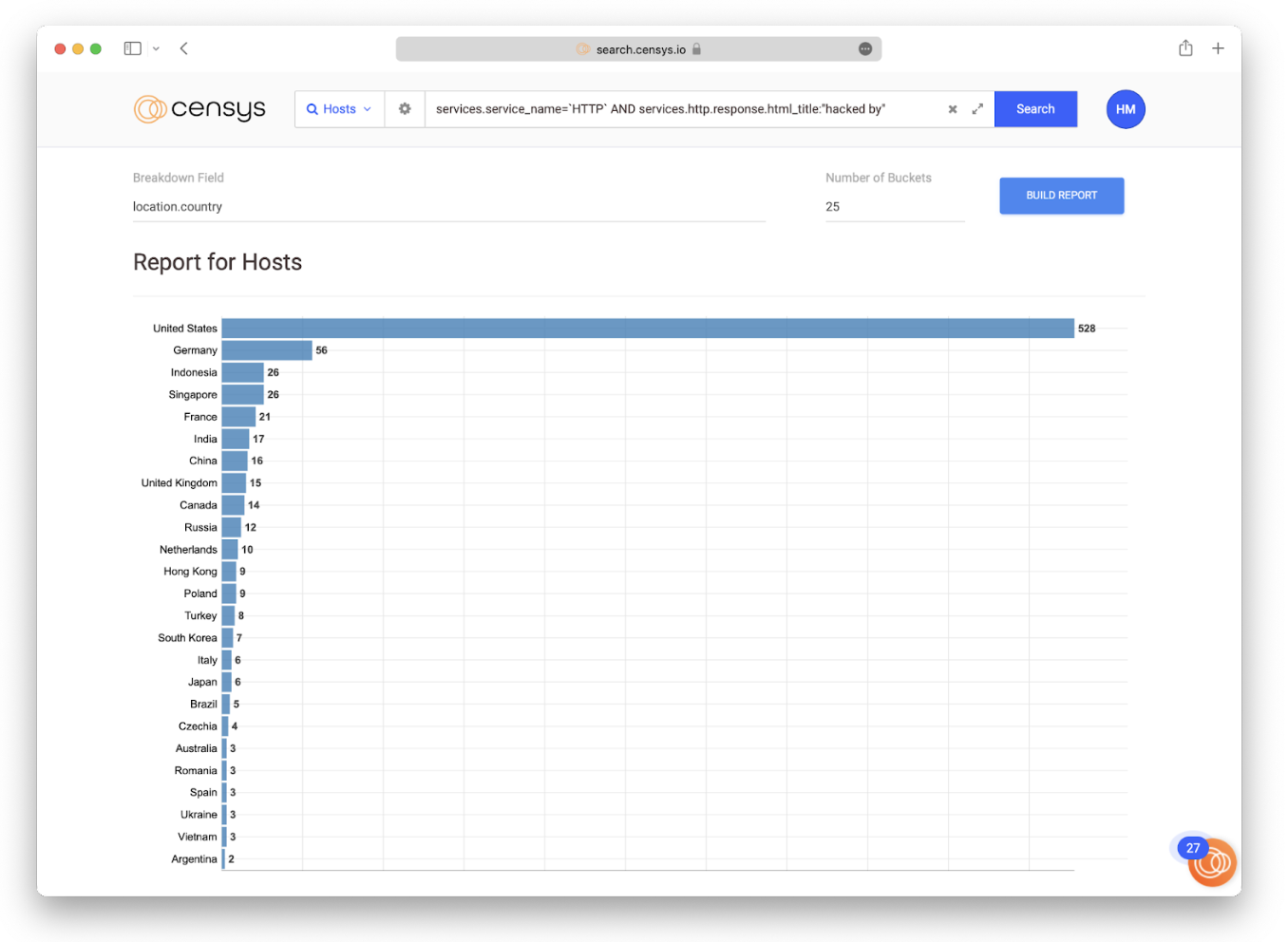
This report reveals that the United States dominates, with 3.46% of hacked servers hosted in the U.S.
But this chart on its own is misleading. If all you were to do is to take those results at face value and make interpretations around it, you’d likely draw some false conclusions. An important distinction to make in this report is that hosts aren’t distributed evenly around the world. The U.S. hosts a good deal of the IPv4 address space, so this trend data may be unfairly skewed toward that country. Think about it this way: if two countries each have 20 servers reporting “hacked by”, but the first country has 100 servers and the second has 10000, that’s a 20% rate vs a 0.2% rate of “hacked by” instances.
What we need to do is start adding context into the picture. In this example, we’ll tie together two sets of results from Censys:
- The number of HTTP servers with the string “hacked by” by country
- The number of total hosts running HTTP by country (see the figure below)
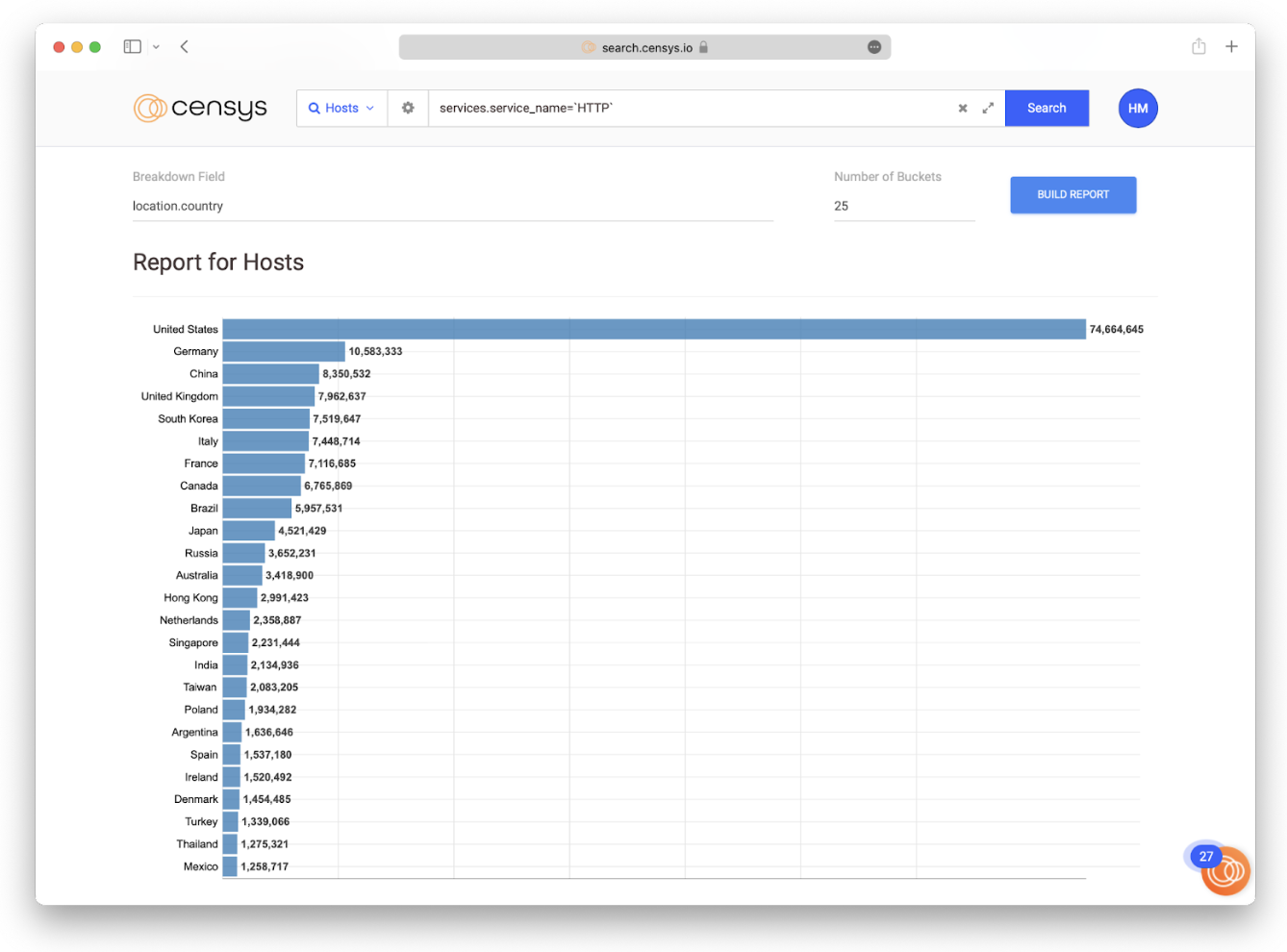
When we scale the “hacked by” values (the first data set) by the number of web servers in each country (the second set), filtering out countries where the former value is trivially small (n<5), we see a different picture.
Tables 1 and 2 break down the top 10 and bottom 10 instances of “hacked by” per capita web servers for those countries. Surprisingly, Indonesia leads the pack as a percentage of population at a rate of about triple the second-place country Singapore, but that may be due to the smaller web server population in that country compared to Singapore.
Table 1: Top 10 Most Affected Countries per Capita Web Servers
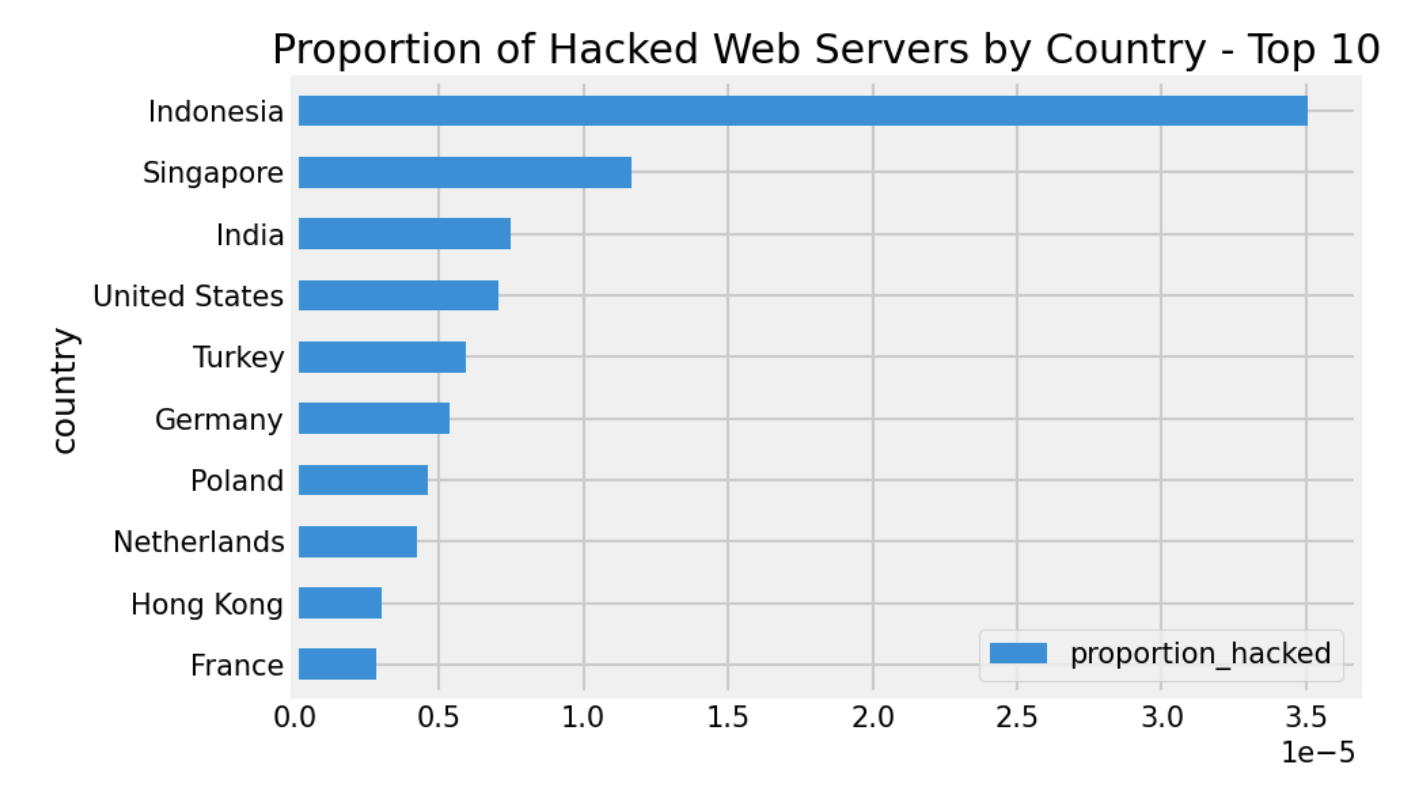
Italy, by contrast, has the lowest rate of defaced web servers from our perspective. It’s interesting to study various factors that may explain these findings, which may point to the opportunity for a broader study.
Table 2: Least 10 Affected Countries Per Capita Web Servers
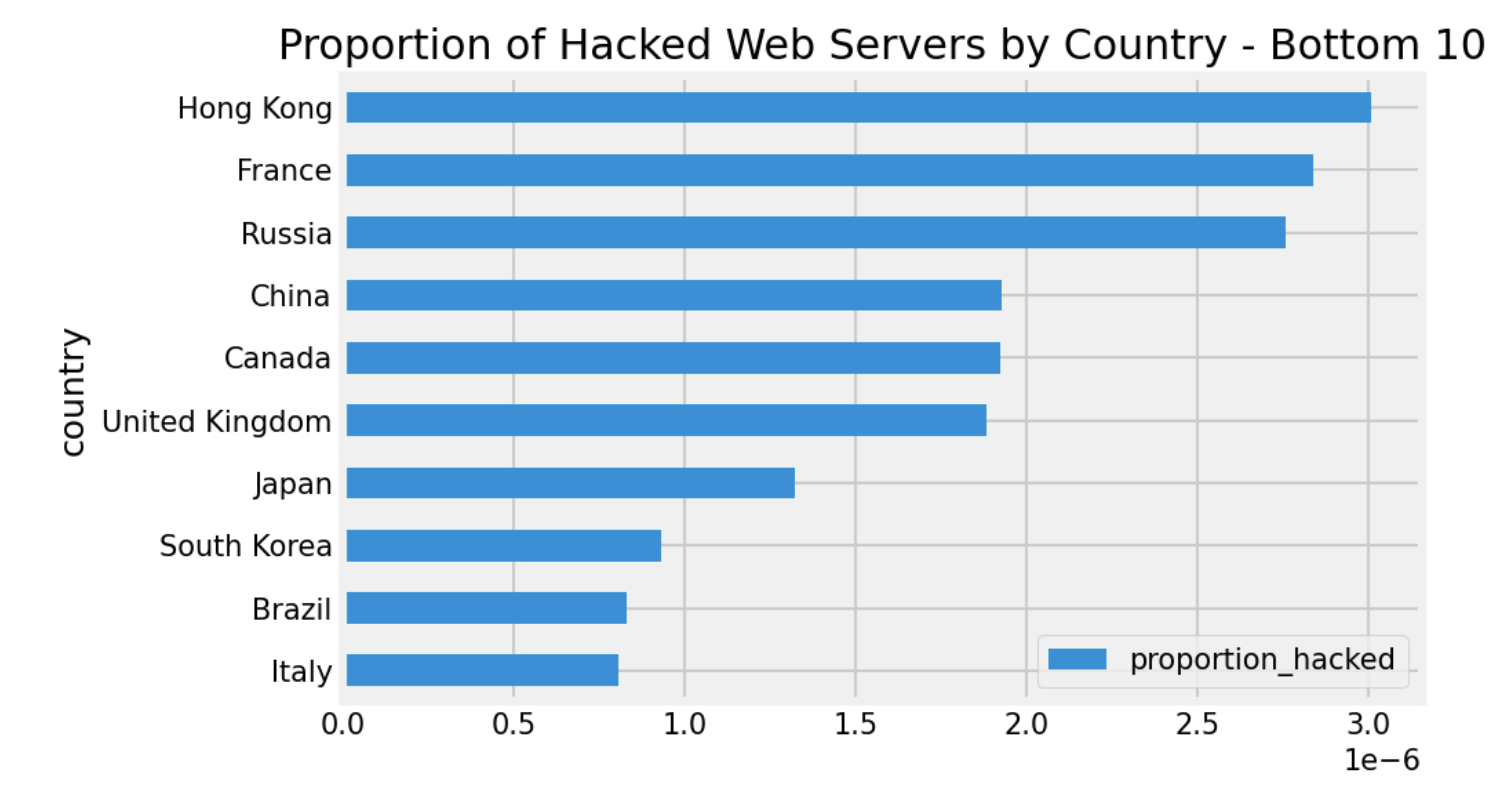
These data points can lead to a larger question: what attributes, regulations, and social trends could potentially impact why Indonesia or Iceland, for instance, would have more hacked websites per capita than other countries. As you can imagine, Internet data alone isn’t enough to demonstrate causation, but it can be used to pull together interesting data trends to support a huge variety of research projects.
A global perspective on Internet security
Internet data can uncover what we don’t know about our own organization, while also illuminating real-time data trends that tell a bigger story about global Internet security.
Finding hacked web servers is just a simple example that we hope will get you thinking creatively about how you can use Censys data. Our broad, global perspective and the depth of relevant security data we make searchable, you can get the visibility required to improve security.
An earlier version of this post written for Censys Search 1.0 appeared in our blog archives. This tutorial is up-to-date with Search 2.0 features as of its writing.