UPDATES:
- 2023-06-07:
- Last week a critical zero-day vulnerability in MOVEit Transfer file transfer software came to light – now being tracked as CVE-2023-34362.
- Notable threat actors including the Clop ransomware gang have been actively exploiting this vulnerability in widespread data theft attacks. Clop carried out similar attacks on other managed file transfer applications such as Accellion FTA and GoAnywhere MFT earlier this year.
- Over the last week, Censys has observed a drop in the number of hosts running exposed MOVEit Transfer instances from over 3k to just over 2.6k, indicating that some are potentially being taken offline.
- Several of these hosts are associated with high-profile organizations, including multiple Fortune 500 companies and both state and federal government agencies.
- The finance, technology, and healthcare industries are the primary sectors in which Censys has observed significant numbers of exposures. We are continuing to investigate impact across industries and will update as we learn more.
SUMMARY:
Another day, another MFT (Managed File Transfer) product getting pwned. On the heels of the GoAnywhere MFT 0-day, this time, it’s a vendor called Progress Software Corporation and their product, “MOVEit Transfer,” that facilitates the transfer of files between business partners and their customers using a variety of protocols such as SSH and HTTP have been hit with a newly discovered exploit.
Little is known about the threat actors who have used this exploit to potentially breach thousands of devices and organizations. Still, we know that the attack method was a SQL injection vulnerability in MOVEits web interface, as stated in the vendor’s advisory.
We also know that backdoors have been installed in the form of a web shell (usually installed at /human2.asp(x)). This web shell includes logic that will return a 404 status code if the value of a specific header (X-siLock-Comment) does not match a predetermined value.
While some outlets report that these devices have been compromised up to a month before being discovered, GREYNOISE stated they had witnessed scans for MOVEit for over a month.
“Based on the scanning activity we have observed, it is our recommendation that users of MOVEit Transfer should extend the time window for their review of potentially malicious activity to at least 90 days.” – GREYNOISE
Below is the list of affected products and their corresponding updates (pulled directly from the vendor’s advisory).
(vulnerable versions via link)
Censys has identified a significant number of over 3,000 hosts currently utilizing the MOVEit service. Although the exact version of the software cannot be determined with scans, it is highly improbable that all of these hosts have been patched against the newly discovered vulnerability. What is particularly concerning is the diverse range of industries relying on this software, including the financial sector, education (with 27 hosts), and even the US federal and state government (with over 60 hosts).
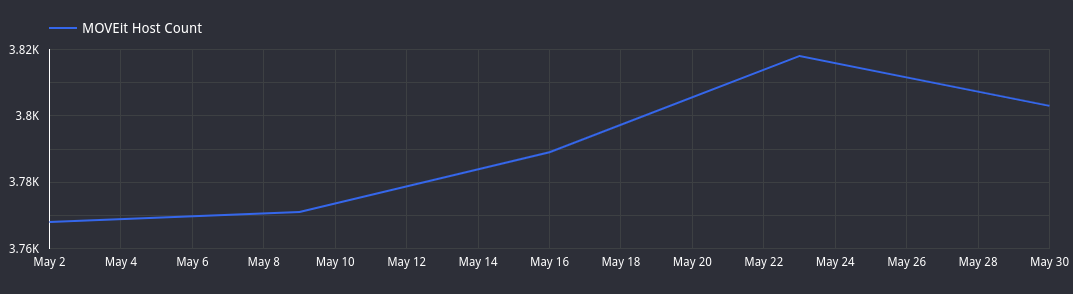
Over the past month, we’ve seen a steady increase in the number of hosts utilizing this product, and as we can see in the graph above, we see over a 100-host increase between May 1st and May 23, 2023, but has seen a small decline up until June since the peak. So if this malicious activity has occurred for up to two months, and we saw even more of this software previously online, we’re looking at even more potentially affected organizations than what is currently visible in Censys (although those hosts are now not publicly accessible, the backdoor may have been installed; thus the damage may have already been done).
Below are some general statistics about the different service providers and locations where these hosts can be found. This seems to be a product almost exclusively used in the United States, with only a few hundred exposed in other countries.