Censys recently surpassed a remarkable milestone—over a trillion recorded scans in our historical dataset, solidifying our commitment to being the one place to understand everything on the internet. In a world where every vendor claims to have the “best” data it’s easy to get lost in the noise. But when it comes to true, actionable internet intelligence, Censys sets the standard.
The Censys Internet Map isn’t just another data set; it’s the most accurate, comprehensive, and real-time representation of the internet available. We don’t just scan; we predict, identify, and illuminate the dark corners of the internet that others miss. Here’s what makes Censys the authority in global internet infrastructure.
The Best Data Begins with the Best Scanning Infrastructure
The 2023 State of the Internet shows a snapshot of all hosts running an HTTP service from February 28, 2023.
The internet is made up of ever-changing, ephemeral infrastructure, and maintaining true visibility requires continuous scanning to capture real-time changes. Censys was founded by the creators of ZMap, the revolutionary tool that first enabled researchers to scan the entire IPv4 space in under an hour—a task that previously took weeks. Building on this technology, we developed our advanced scanning infrastructure for unmatched performance, reliability, and depth.
Unlike vendors who rely on third-party or open-source data, Censys’ patented scanning infrastructure was designed from the ground up, giving us complete control over the scanning process. This allows for unparalleled accuracy and real-time visibility, eliminating the risks of outdated or incomplete data from external sources.
As our own strongest critics, we continuously innovate to push the boundaries of what’s possible in internet intelligence, aiming to understand the internet more deeply every day. We believe the best data is built, not borrowed. Our technology continually reshapes how we map and understand the global internet at scale.
The Foundation of Internet Intelligence: Coverage, Accuracy, and Time-to-Discovery
At Censys, we define the best data through three key principles: coverage, accuracy, and time-to-discovery. These pillars form the foundation of our approach to internet intelligence and drive every aspect of our scanning and analysis.
Pillar 1: Coverage
There are 65,535 available ports for running services, and Censys research shows that over 60% of all internet services operate on non-standard ports. This means that scanning only standardized ports leaves significant blind spots in attack surface coverage. Traditional methods struggle to scan all 65K ports efficiently, but Censys’ Predictive Scanning technology addresses this by intelligently targeting non-standard ports based on real-world data patterns. Combined with its peering relationships with seven Tier-1 ISPs across three geographic regions, Censys ensures global visibility, uncovering hidden services and threats that conventional methods often miss.
Predictive Scanning now accounts for over 40% of all services identified by Censys, revealing hidden infrastructure like IoT devices, attacker backdoors, and non-standard services often exploited by adversaries. This coverage is further strengthened by Automated Protocol Detection (APD), which analyzes application-layer data to accurately classify services based on behavior, regardless of the port used. For example, if an HTTP request encounters an SSH banner, Censys automatically adjusts to the correct protocol, ensuring accurate identification.
Additionally, Censys offers rapid deployment of custom protocol scanners via a lightweight framework, enabling quick adaptation to emerging or obscure protocols such as industrial control systems or UDP-based services. By specifying the port and method to scan, Censys can create new protocol scanners in hours rather than days. This ensures that as the threat landscape evolves, we can adapt just as quickly.
A recent GreyNoise analysis validated Censys’ unparalleled coverage across all 65K ports, making it the most comprehensive solution for full attack surface visibility. This complete coverage allows security teams to detect and address threats before they can be exploited by attackers.
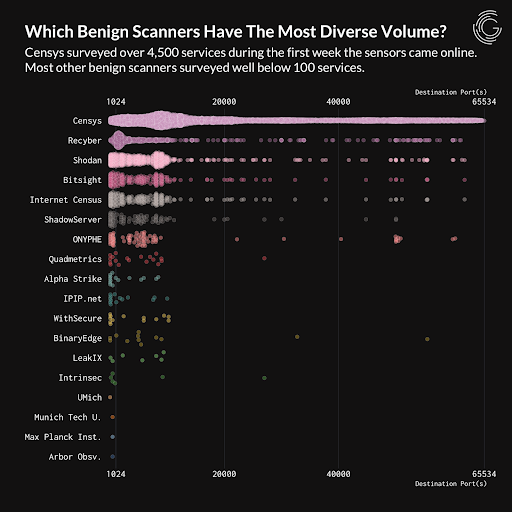
Greynoise’s testing in “A week in the life of a GreyNoise Sensor: The benign view” shows Censys leading in service coverage of non-standard ports.
Pillar 2: Accuracy
Achieving high-quality data isn’t just about broad coverage—accuracy is equally critical. The internet’s dynamic nature presents challenges, as services often experience temporary outages due to network issues or scheduled maintenance. Without proper mechanisms in place, this volatility can lead to inaccurate results and an overwhelming number of false positives for security teams.
False positives are a significant burden for threat hunters. According to the 2024 State of Threat Hunting Report, nearly one-third of threat hunters encounter false positives in over 20% of their findings, meaning one in five alerts is benign. This creates alert fatigue and wastes valuable resources as teams sift through irrelevant data.
At Censys, we tackle this by re-scanning and refreshing our dataset of ~4 billion services daily, maintaining an average refresh rate of under 16 hours. This active and continuous scanning process delivers real-time intelligence, preventing teams from relying on outdated data that can misrepresent an organization’s attack surface.
Our Smart Refresh feature further ensures accuracy by preventing premature removal of services from our index. Instead of pruning services after a few negative scan responses, Smart Refresh flags non-responsive services and schedules re-scans over a fixed grace period. This approach ensures that temporary disruptions don’t result in false negatives, and only services that remain inactive throughout the grace period are removed.
Pillar 3: Time-to-Discovery
Infrastructure and services are constantly evolving, making time-to-discovery crucial for identifying newly exposed assets, open ports, or vulnerabilities before they can be exploited.
Censys continuously scans the entire public IPv4 space, detecting up to 10,000 infrastructure changes per second. To further streamline time-to-discovery, we perform specialized scans that focus on the most dynamic and active areas of the internet. Our Global Scan covers more than 100 IANA-assigned ports across the entire IPv4 space, enabling us to detect changes in widely used services. This baseline is supplemented by our Cloud Provider Scans, which target approximately 1,000 common ports on major cloud platforms like AWS, Azure, and GCP.
Censys also employs a multi-tiered scanning strategy that combines continuous global scans with dynamic targeting through our Predictive Scanning engine. This engine adapts to both current and historical data, pinpointing high-value IPs and services likely to reveal critical insights. This proactive approach allows us to identify emerging risks and detect new services far faster than traditional static scans.
As a result of these efforts, Censys achieves a median discovery time of 9 hours, significantly reducing the delay between a service becoming exposed and its detection. In fact, a recent study showed that Censys identifies new services six times faster than its nearest competitor. In a landscape where every minute counts, faster time-to-discovery directly translates to reduced risk.

Distribution of discovery times for the intersection of services found by Censys and the nearest competitor.
Censys’ patented scanning methods ensure 63% more service coverage, providing your security team with the complete visibility needed to identify hidden threats and vulnerabilities—where others fall short.
Turning Data into Actionable Insights: Censys ASM and Search
Censys’ data powers our Attack Surface Management (ASM) and Search capabilities, enabling organizations to take decisive action. ASM provides continuous visibility into external-facing assets, allowing industries and governments to monitor, assess, and mitigate vulnerabilities as they emerge. Censys Search offers deep insights into global internet infrastructure, helping security teams track malicious activity, protect brands, monitor critical infrastructure, and evaluate cyber insurance risks.
At its core, scanning is the foundation of visibility into both attack surfaces and malicious infrastructure. Every vendor relies on scanning to achieve this visibility, but the depth and breadth of the scanning are crucial as that data underpins the identification and mitigation of active threats. Without high-quality data, security teams risk relying on outdated or incomplete information, which can lead to missed vulnerabilities and delayed responses. With Censys, organizations benefit from comprehensive coverage, precise accuracy, and rapid time-to-discovery, ensuring true visibility.
The 2023 Forrester Total Economic Impact of Censys External Attack Surface Management study highlights how organizations are leveraging Censys to mitigate risks and streamline operations. Our data doesn’t just fuel dashboards—it drives decisions that directly reduce exposure.
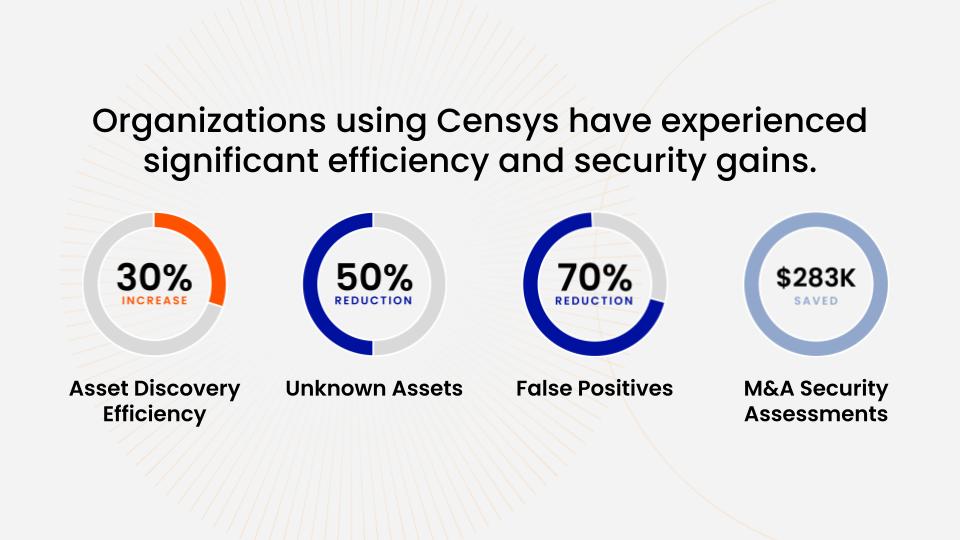
The 2023 Forrester Total Economic Impact of Censys External Attack Surface Management.
Enhancing Threat Detection Efficiency: A European Government Agency’s Success with Censys
A European government agency responsible for safeguarding multiple partnering organizations needed a more efficient way to monitor and manage their attack surfaces. Previously relying on a mix of manual tools and fragmented processes, the team required a solution to streamline asset discovery and improve threat detection capabilities.
By implementing Censys ASM, the agency automated its asset discovery processes, reducing the time spent on manual threat detection from one week to just 20 minutes. The platform provided comprehensive visibility into external-facing assets, identifying previously unknown domains and subdomains that posed potential security risks.
With Censys, the agency significantly enhanced both the accuracy and speed of its threat detection efforts, strengthening its ability to protect critical infrastructure and ensuring a more proactive defense posture.
Powering Cyber Insurance: At-Bay’s Success with Censys
At-Bay, a leader in cyber insurance, leverages Censys’ comprehensive internet data to significantly enhance its risk assessment and underwriting processes.At-Bay uses Censys to assess the cybersecurity posture of prospective clients in under two minutes—a process that traditionally takes significantly longer across the industry. Censys’ data allows At-Bay to quickly identify critical vulnerabilities, including exposed services and misconfigurations, leading to faster and more precise risk assessments.
Beyond initial underwriting, At-Bay utilizes Censys’ continuous monitoring to maintain ongoing visibility across their insured portfolio. This proactive approach enables At-Bay to identify emerging risks in real-time and notify clients of vulnerabilities before they escalate into liabilities. With Censys, At-Bay has not only improved the speed and accuracy of its risk evaluations but also set new industry standards for proactive loss prevention in the cyber insurance space.
Redefining What the Best Data Means
The best data isn’t just about volume—it’s about quality, accuracy, and actionable insights. From comprehensive scanning to unmatched real-time intelligence, Censys empowers organizations to see the unseen and act with confidence. We don’t just offer data; we empower teams with the tools needed to truly stay ahead of threats and drive meaningful decisions. So, what does the best data really mean? It means choosing Censys, the trusted authority in internet visibility. Try our data for free and experience the Censys difference. Want to better understand your external attack surface? Request a demo today.
Request Demo