At Censys, our goal is to be the one place to understand everything on the internet – for more effective threat hunting and exposure management. With the rapid proliferation of cloud providers, software, web properties, remote devices, and more, it is becoming more challenging for security teams to identify threats or exposures and take action.
One of the main challenges is the sheer volume of services, and where they reside. At one point in time, most internet services lived on a relatively small group of standard internet ports – for instance 21 was for FTP, 80 for HTTP, 443 for HTTP over SSL, and so on. These standard port-service pairings are well-documented by the Internet Assigned Numbers Authority (IANA). Non-standard ports, the ones not documented, were relatively unutilized for web services. But that has changed as more devices and vendors run an ever-growing number of services.
>60% of All Internet Services Run on Non-Standard Ports

The 2023 State of the Internet shows a snapshot of all hosts running an HTTP service from February 28, 2023
There are ~65,000 ports total that can be utilized to run services. The latest data from the Censys research team shows almost 7 in 10 HTTP services are on non-standard ports (read more in our 2023 State of the Internet). And with HTTP being 88% of all internet services, it means more than 60% of all internet services run on non-standard ports. Without intelligent scanning across 65,000 ports and visibility into these services, CISOs and security teams can’t effectively protect their organizations.
External attack surface management products or vulnerability management add-ons typically scan around two to three hundred ports, some more and some less. This lack of service coverage could be leaving significant parts of your external attack surface exposed. Even global scanners for threat hunting don’t provide optimal coverage across 65,000+ ports, especially the non-standard ones. In independent testing done by Greynoise in October 2022, only Censys tested most effectively across 65,000 ports – giving InfoSec pros the most accurate, up-to-date view of the internet. But we’re not resting on our laurels with our Internet Map.
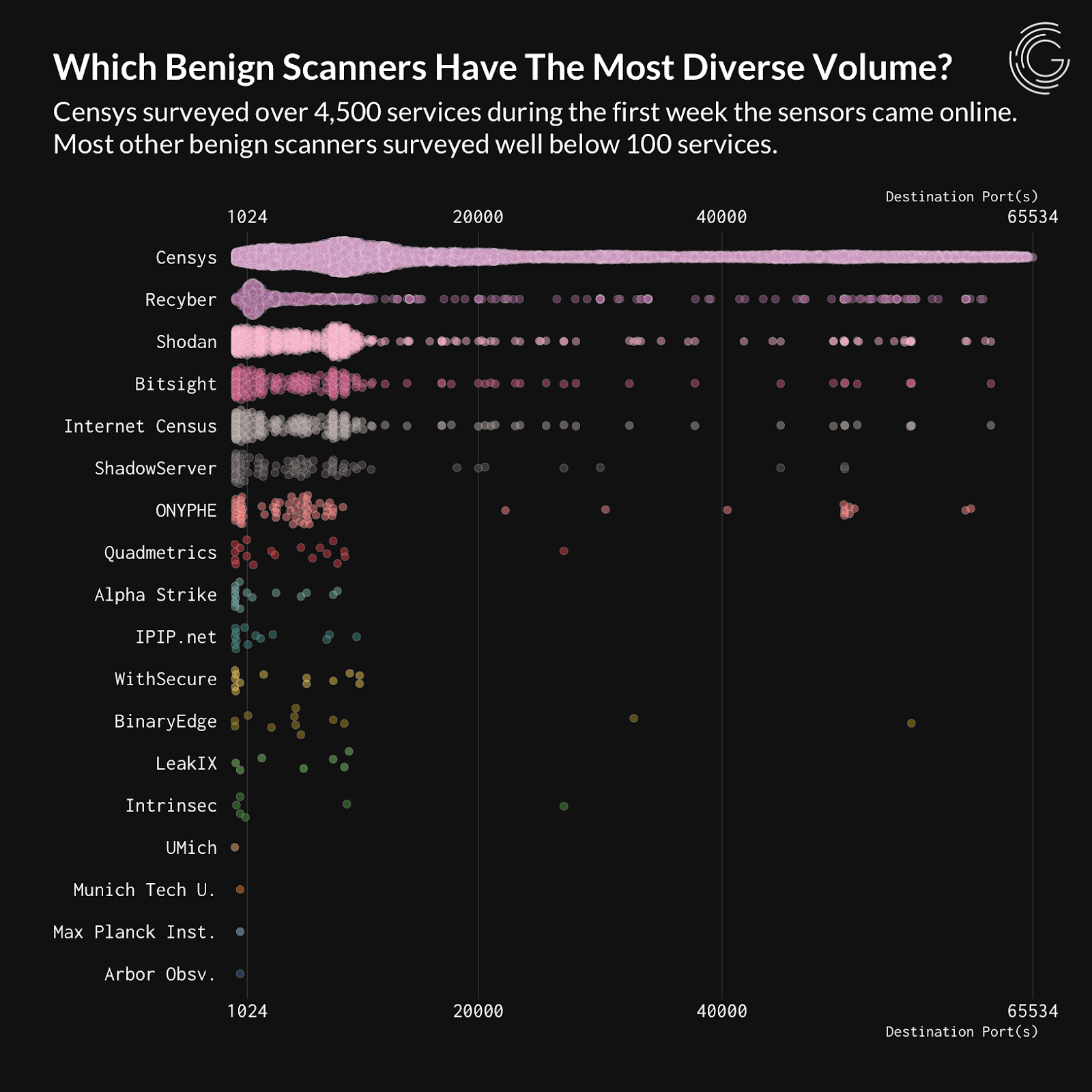
Greynoise’s testing in “A week in the life of a GreyNoise Sensor: The benign view” shows Censys leading in service coverage of non-standard ports
Predictive Scanning Provides Superior Coverage of 65k Ports
This summer we launched Predictive Scanning to enhance the already industry-leading Censys Internet Map. With Predictive Scanning, security teams have better visibility into all 65k ports, enabling faster detection of services than ever before. Our new Predictive Scanning capabilities add over 107M new services to the ~3B global Internet services we continuously monitor. InfoSec pros can use this powerful data to improve operational impact, reduce false positives, and provide a substantial return on investment and risk reduction.

The 2023 Forrester Total Economic Impact of Censys External Attack Surface Management demonstrates over 440% ROI for businesses in key areas like asset discovery, breach likelihood, employee productivity, mergers & acquisitions, false positives, and incident response
Some common types of services discovered by this new technology include:
- Services from Internet of Things (IoT),which businesses are leveraging for growth but also present high risk due to lagging security standards
- Autonomous Systems only running services on non-standard ports that attackers might utilize to host malicious infrastructure and hide from scanners
- A massive proliferation of newer services by vendors like online portals, data analysis tools, and business productivity enhancers that are especially popular in hybrid and remote environments that are typically run on high, non-standard ports
IoT: With Great Opportunity, Comes Great Risk
While IoT devices present increased business opportunities, they also increase security risk. Security firm Check Point found that every week 54% of organizations suffer from attempted cyber attacks targeting IoT devices. IoT devices frequently run services on non-standard ports and can go undetected. With Predictive Scanning, Censys can proactively identify IoT services associated with your organization to protect IoT-related exposure in this fast-growing sector of the Internet.
For organizations implementing IoT devices, like healthcare, retail, manufacturing, energy, and many others, it’s critical to inventory and secure all IoT devices for compliance and improved data protection. Even one unsanctioned IoT device in an external attack surface presents an opportunity for attackers to get access and exfiltrate data like PHI, camera imagery, or other sensitive data. Exposed controls could allow attackers to disrupt operations or hold those controls for ransom.
Autonomous Systems: Attacker’s Hidden Space No More
The entire internet runs on Autonomous Systems (AS), which are not dangerous by default. But the AS landscape is increasingly complex and large parts can be used for malicious purposes. Censys’ Predictive Scanning has identified entirely-new AS running services on non-standard ports. This additional host visibility provides better overall external attack surface coverage, but more critically, insights for threat hunting.
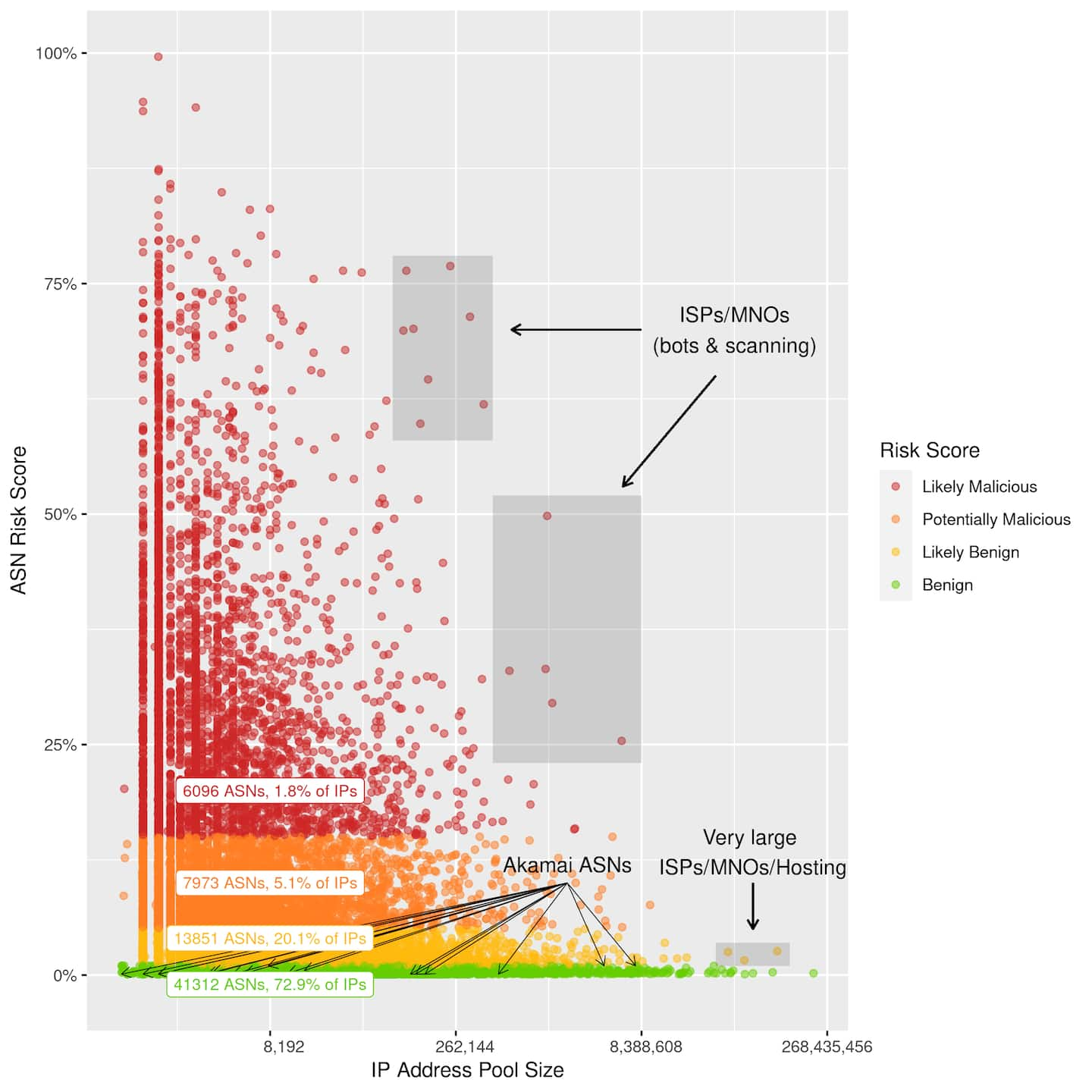
Data from Akamai shows AS with low IP address pool sizes are more likely to be malicious
Small-scale ASes can go undiscovered by almost all automated scanners when using non-standard ports. If automated scanners, like the ones shown in the Greynoise study, don’t cover high, non-standard ports ASes with IPs only running services at high, non-standard ports could not appear at all in results. Research by Akamai has shown the vast majority of low IP volume ASes are likely malicious. These ASes, without sufficient security controls, can become targets or even tools of attackers. Bad actors can more easily leverage IPs to host phishing websites, malicious files, bots, and scanners. Without visibility into these ASes and hosts, investigations to understand the sources of attacks could yield no results and no way to protect against them in the future.
More Services, More Problems
With the massive proliferation of services like online portals, data analysis tools, and business productivity enhancers, the likelihood of services on non-standard ports continues to increase. Hybrid and remote working environments increase this risk. With Predictive Scanning, Censys will identify port patterns for certain vendors and software. It will then predictively conduct non-standard port scanning across 65k ports to more quickly and accurately detect services. Censys will give cybersecurity teams context and risk details, like software versions, to resolve incidents and ensure their external attack surfaces stay secure.
For organizations frequently deploying new services, like technology, software, communications, and finance, “good enough” data on an attack surface or attacker infrastructure is not good enough. Other scanners have limited or no insight into 65k+ non-standard ports, leaving security “to chance” at a time of rapidly-expanding attack surfaces and hybrid workforces that may attempt to circumvent security processes.
Explore our Internet Map, for Free

Censys’ Internet Map provides actionable context and details so InfoSec teams can quickly identify services and protect against exposure or related threats
The Censys Internet Map is so vast and detailed – it’s hard to conceptualize until you try it. With our new CensysGPT (Beta) tool anyone can quickly and easily search our Internet Map. If you’d like a better understanding of your external attack surface, request a demo.