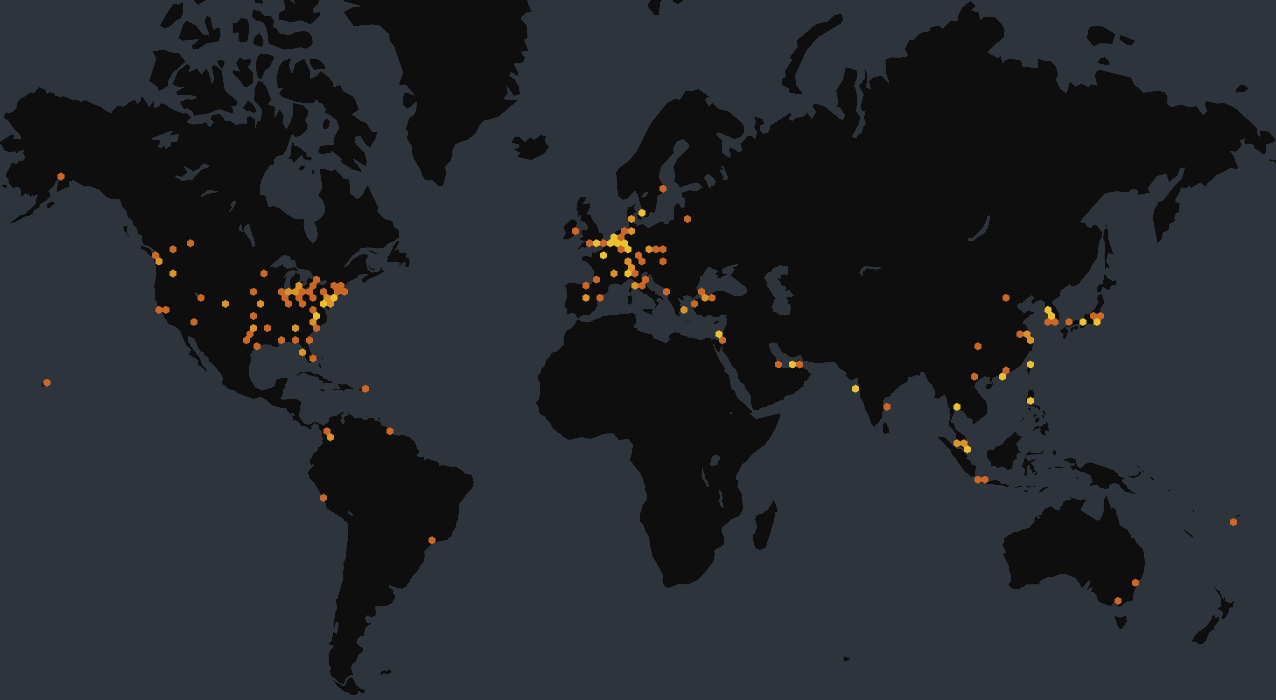
Compromised Ivanti Connect Secure IPs
Update January 31, 2024:
Two new vulnerabilities, CVE-2024-21893 and CVE-2024-21888, have been identified in Connect Secure, Policy Secure, and ZTA gateways, the former of which is seeing active exploitation. Ivanti has released a new mitigation that serves as a workaround until official patches are available.
A patch is now available for the previously disclosed CVE-2023-46805 and CVE-2024-21887 in Connect Secure (versions 9.1R14.4, 9.1R17.2, 9.1R18.3, 22.4R2.2 and 22.5R1.1) and ZTA version 22.6R1.3. In their advisory, Ivanti recommends a factory reset of the appliance before applying the patch as a precautionary measure. Customers who have applied this patch do not need to implement the mitigation.
Summary
- CISA’s Emergency Directive 24-01, issued last Friday, requires all FCEB agencies to mitigate an exploit chain in Ivanti Connect Secure and Policy Secure, currently seeing mass exploitation (CVE-2023-46805 and CVE-2024-21887)
- When these two CVEs are used, an unauthenticated threat actor can leverage these vulnerabilities to execute arbitrary commands on vulnerable servers.
- As of Monday, January 22, 2024, Censys observed:
- Over 26,000 unique Connect Secure hosts are exposed on the public internet. This software’s supported versions (9.x and 22.x) are vulnerable if the reported workarounds/mitigations are not applied to the device.
- 412 hosts remain compromised with a backdoor used for credential theft.
- At the time of writing, no official patch has been made available. However, Ivanti has published recovery steps for customers to mitigate their systems in the interim. It’s strongly recommended that you apply this mitigation ASAP and run your systems against the vendor’s Integrity Checker Tool to check for compromise.
Last Friday, CISA issued Emergency Directive 24-01 mandating all Federal Civilian Executive Branch (FCEB) agencies to address two actively exploited vulnerabilities in Ivanti Connect Secure and Ivanti Policy Secure. These vulnerabilities, CVE-2023-46805 (an authentication bypass vulnerability) and CVE-2024-21887 (a command-injection vulnerability), when exploited in combination, allow malicious actors to achieve remote code execution (RCE) on vulnerable servers. All supported versions, including Version 9.x and 22.x, are affected by these vulnerabilities (refer to Ivanti’s version support matrix).
FCEB agencies had until 11:59 EST on Monday, January 22, to implement Ivanti’s recovery steps, run the vendor’s Integrity Checker Tool, and take additional action if signs of compromise were detected.
This directive is no surprise, considering the worldwide mass exploitation observed since Ivanti initially revealed the vulnerabilities on January 10. These vulnerabilities are particularly serious given the severity, widespread exposure of these systems, and the complexity of mitigation – especially given the absence of an official patch from the vendor as of the current writing. Ivanti outlined a plan to release patches on a staggered schedule beginning this week.
Volexity researchers first identified exploitation attempts dating back to December 2023. Subsequent analysis revealed that the initial activity was likely the work of an unidentified threat actor tracked by Volexity as “UTA0178.” A Proof of Concept was published on January 16.
Censys researchers conducted scans to dig deeper into the extent of compromised servers.
Censys Findings
As of Monday, January 22, 2024, Censys observed the following:
| Description |
Value |
| Number of Unique Connect Secure Hosts |
26,095 |
| Number of Unique Compromised Connect Secure Hosts |
412 |
| Percentage of Hosts Compromised |
1.5% |
| Number of Unique Credential Stealing Receivers / Callback URLs |
22 |
| Compromised hosts per Autonomous System |
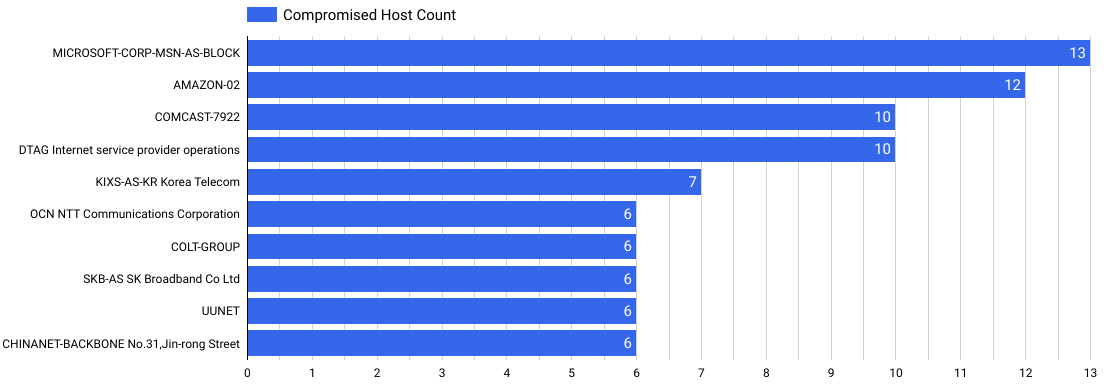 |
| Autonomous System |
Compromised Host Count |
| MICROSOFT-CORP-MSN |
13 |
| AMAZON-02 |
12 |
| COMCAST-7922 |
10 |
| DTAG ISP |
10 |
| KIXS-AS-KR |
7 |
| OCN NTT Communications |
6 |
| COLT-GROUP |
6 |
| SKB-AS SK |
6 |
| UUNET |
6 |
| CHINANET-BACKBONE |
6 |
|
| Compromised hosts per Country |
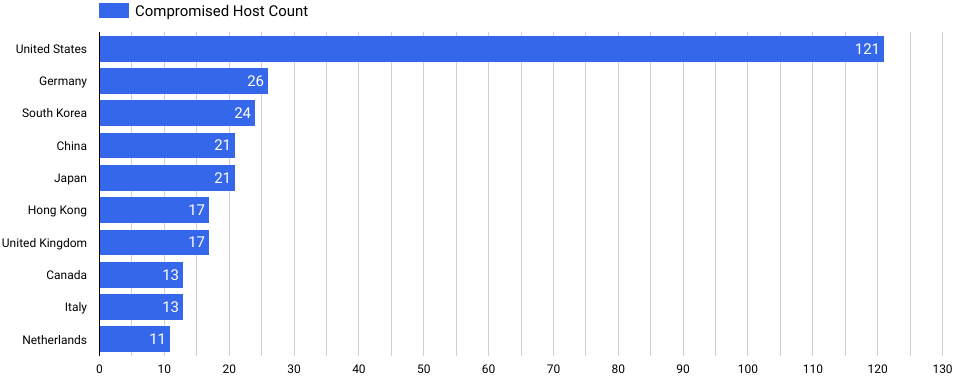 |
| Autonomous System |
Compromised Host Count |
| United States |
121 |
| Germany |
26 |
| South Korea |
24 |
| China |
21 |
| Japan |
21 |
| Hong Kong |
17 |
| United Kingdom |
17 |
| Canada |
13 |
| Italy |
13 |
| Netherlands |
11 |
|
In their research, Volexity noted that a legitimate javascript component (/dana-na/auth/lastauthserverused.js), used to remember the last selected authentication realm, had been found to have been modified by attackers to include various mechanisms to hijack and exfiltrate client login information. This backdoored javascript would send the usernames, passwords, and the URL of the attempted authentication back to an attacker-owned HTTP server.
We conducted a secondary scan on all Ivanti Connect Secure servers in our dataset and found 412 unique hosts with this backdoor. Additionally, we found 22 distinct “variants” (or unique callback methods), which could indicate multiple attackers or a single attacker evolving their tactics.
Censys Search customers can use the following query to identify Ivanti Connect Secure hosts.
services.software.cpe: `cpe:2.3:a:ivanti:connect_secure:*:*:*:*:*:*:*:*`
- Monitor Ivanti’s evolving mitigation guidance for CVE-2023-46805 and CVE-2024-21887.
- If an impacted customer needs additional help, open a ticket with Ivanti support or reach out to CISA or other relevant cyber agencies.
- Check if your Ivanti instance is exposed to the public internet using this Censys Search query: services.software.product: {“Connect Secure”, “connect_secure”}
- Censys Exposure Management customers can search for vulnerable hosts using the following query:
host.services.software.uniform_resource_identifier: `cpe:2.3:a:ivanti:connect_secure:*:*:*:*:*:*:*:*` or web_entity.instances.software.uniform_resource_identifier: `cpe:2.3:a:ivanti:connect_secure:*:*:*:*:*:*:*:*`
- Block the following list of IPs detected making exploitation attempts on GreyNoise Ivanti sensors: IPs that are scanning for, or exploiting, vulnerable Ivanti devices (a la GreyNoise) · GitHub