Executive Summary
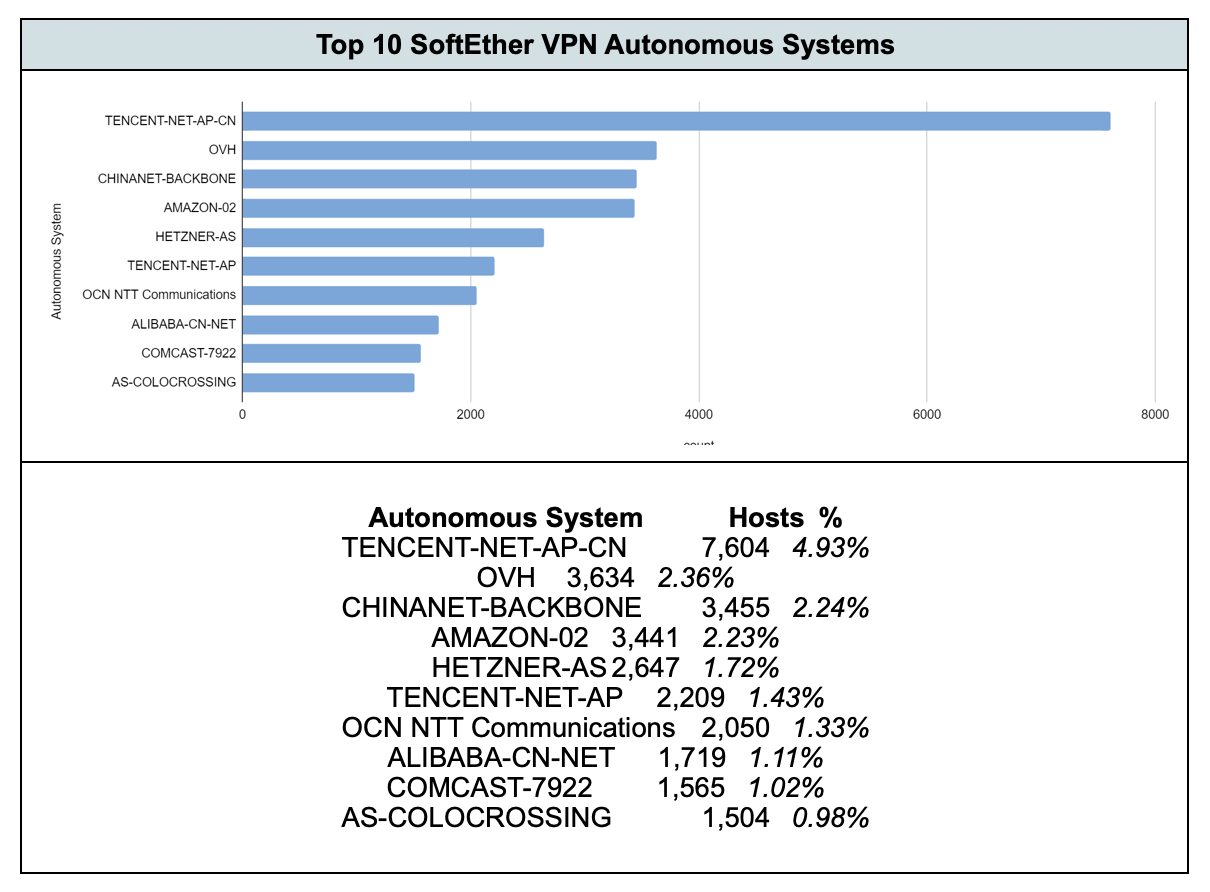
SoftEther VPN is a free, open-source VPN client created by researchers in Japan and used for commercial and non-commercial use. The United States, Japan, and China are the top three countries where Censys observed the highest number of SoftEther hosts. Censys also found that four of the top ten autonomous systems where SoftEther was found are China-based organizations.
From 2019 to February 2023, several threat groups, including APT 41, Gallium, Venomous Bear, and Hydrochasma, have used SoftEther VPN software to maintain persistent access in their victims’ environments. These threat actors install SoftEther VPN on a victim’s host and configure it to connect to the threat actor’s infrastructure. This enables them to create and maintain a foothold in the victim’s network and facilitate follow-on actions (1,2,3,4).
Additionally, the FBI has stated that APT 41, a Chinese-based threat group, has specifically exploited vulnerabilities in the SoftEther VPN software to deploy the “Skeleton Key” malware to create a master password that allows them access to any account on the victim’s domain (5).
Findings
Between 20-21 March 2023, Censys discovered over 148,000 SoftEther VPN servers globally; of those, around 32,000 also run IKE (Internet Exchange Key), a commonly observed VPN protocol, and upwards of 36,000 are running the SSH protocol, which can be used and abused by attackers for remote administration.
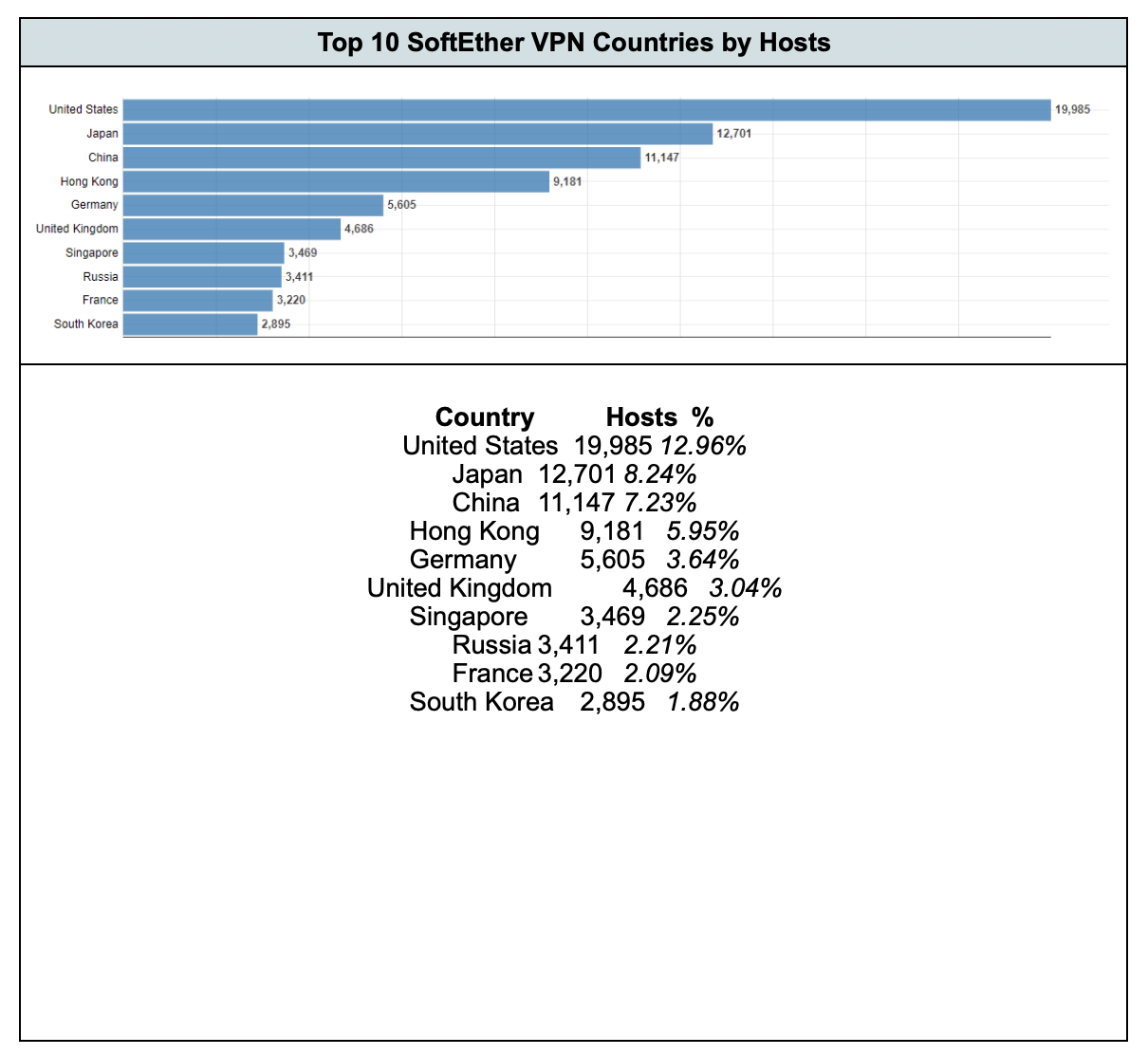
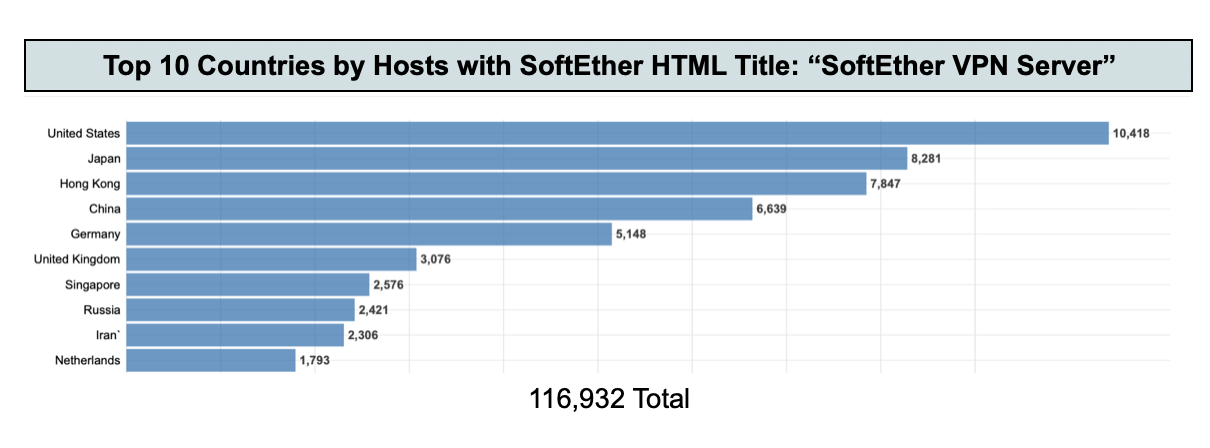
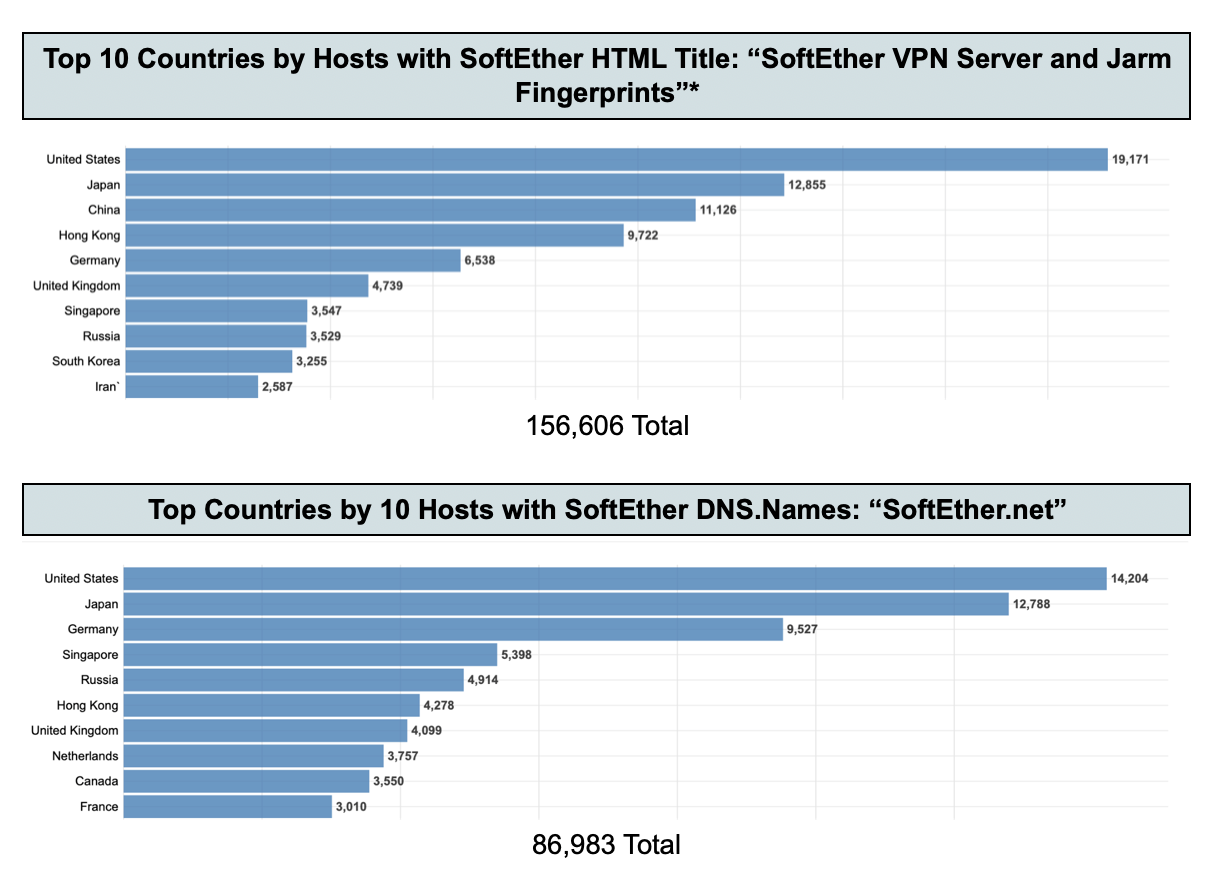
Censys found that nearly 13% of the SoftEther VPN servers Censys identified worldwide (via HTTP HTML titles, and SoftEther-specific Jarm fingerprints) were located in the United States, closely followed by Japan with 8% and China immediately following with 7%.
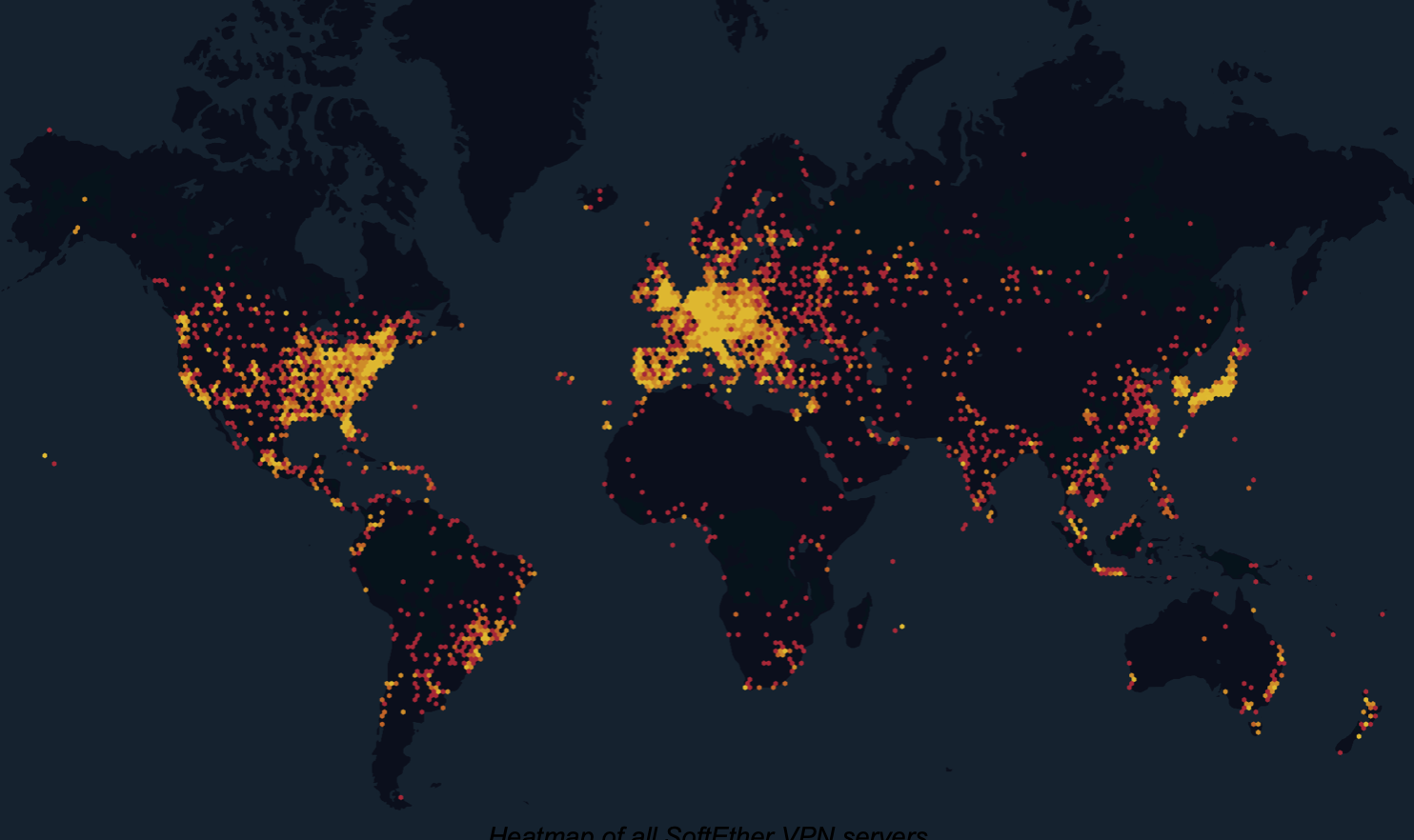
Heatmap of all SoftEther VPN servers
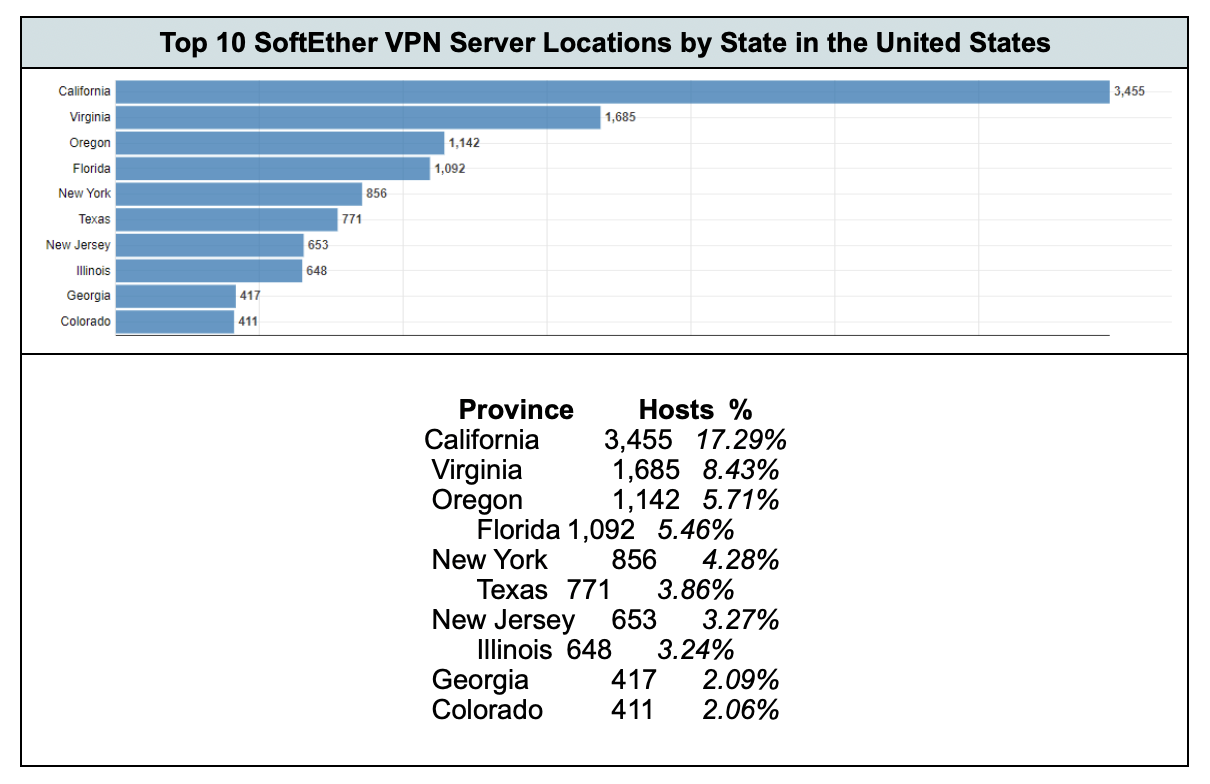
At the time of writing, the following are the top ten countries where Censys could observe SoftEther VPN hosts, along with a short detailed breakdown of these servers in the United States.
The following statistics depict the top-ten Autonomous Systems (based on BGP routing) that are announcing IP addresses that host SoftEther VPN servers. Four of the autonomous systems Censys found in the top ten are China-based organizations.
Censys also looked at the three Chinese-owned Autonomous Systems from the above listing (TENCENT-NET-AP-CN, CHINANET-BACKBONE, TENCENT-NET-AP, and ALIBABA-CN-NET) and broke out the IP addresses being announced inside of the United States and found 1, 154 hosts running SoftEther VPN servers. California has the most China-announced US hosts, with 1,143 (99.05% of the total), while Virginia had only 11 hosts (0.95%).
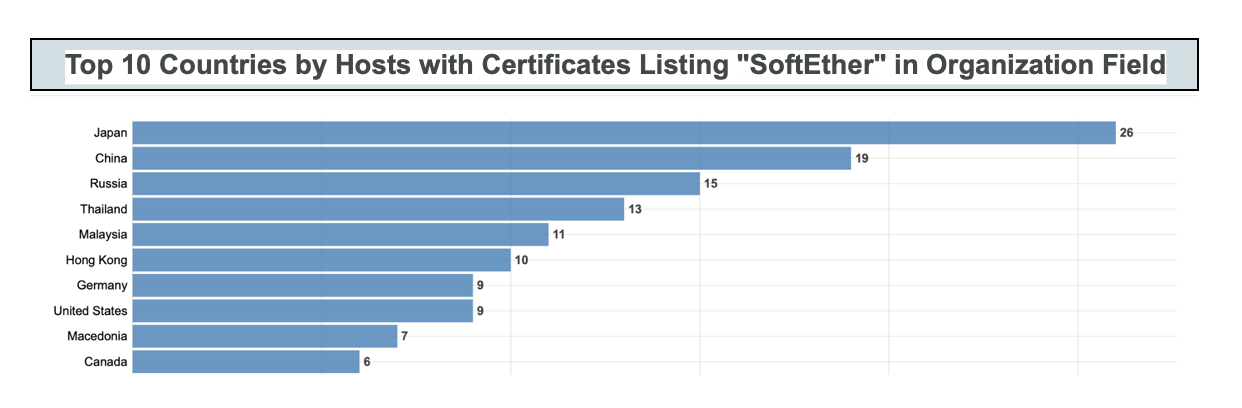
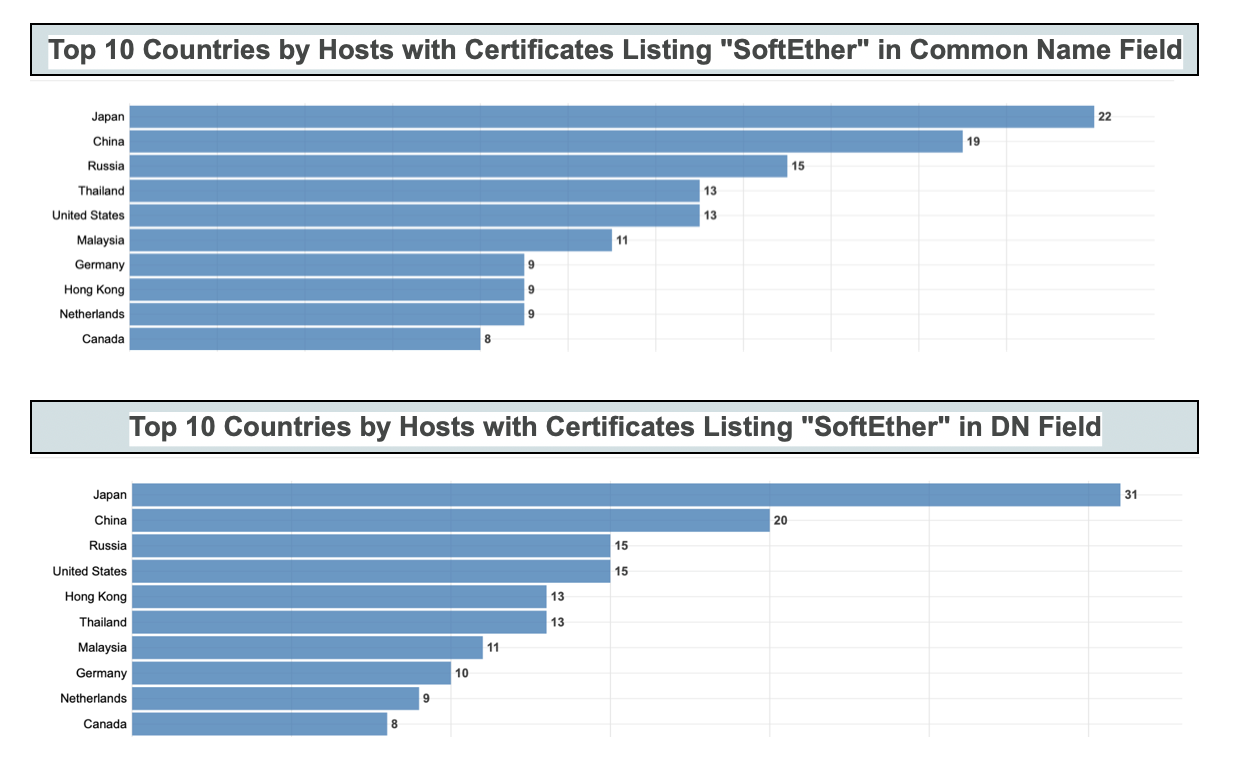
The following statistics cover the number of hosts by top ten countries based on the following Censys syntax searches:
In addition to the above data, Censys identified “SoftEther” within a number of certificates presented on a total of 606 hosts globally.