(As reported in “Russian Ransomware C2 Network Discovered in Censys Data”)
Executive summary
In late January 2023 Censys analysts reviewed Host F (95.213.145.99), which was previously identified in Censys reporting as a Russia-based, probably malicious host running a Command and Control (C2) ransomware kit with callbacks to an associated Bitcoin wallet. Upon return to the host, it was observed that the primary ports running the C2 software and cryptocurrency callbacks have been removed, however the host now actively maintains a port running Metasploit Pro (a commercial penetration testing software). Following the history of the host through Censys data, it is assessed that the host is likely maintained by the same user(s) as during the time of previous reporting. Additionally, the active maintenance of a port expressly for Metasploit in addition to Censys’ historical observations may indicate that the host has shifted its previous responsibilities of hosting ransomware kits and facilitating direct access and payment, to a more managerial role seeking new attack victims.
Observations
Context:
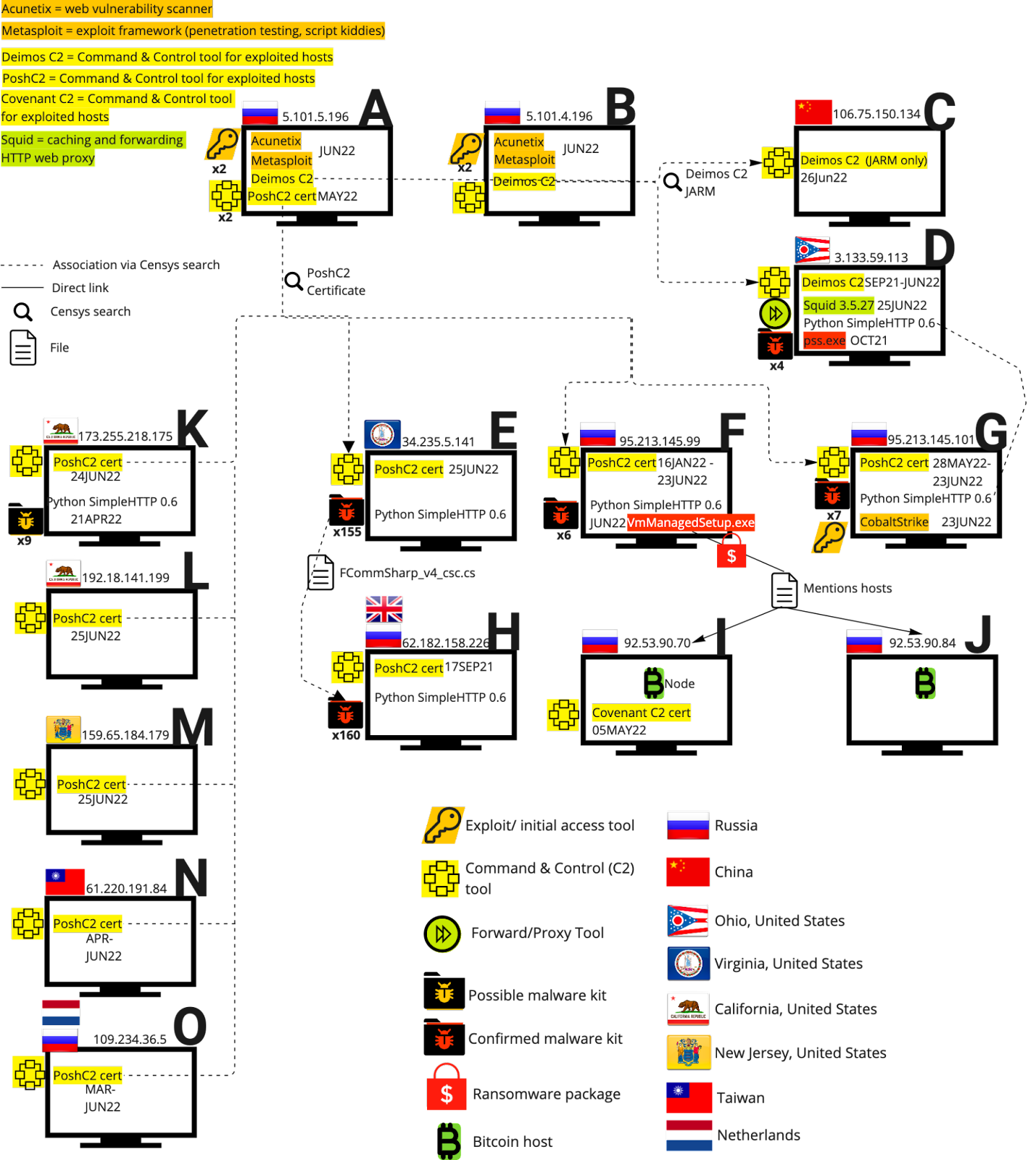
Reference: This Follow-up focuses on “Host F”, as identified in Censys’ 18 July 2022 report “Russian Ransomware C2 Network Discovered in Censys Data”. All other referenced host names and identities are of those in said report; see diagram below.
In an effort to understand the evolution of nefarious hosts over time, Censys analysts returned to the hosts noted in previous Censys reporting to observe any significant changes in posture or nefarious developments. As indicated in this reporting, Host F was previously observed hosting C2 ransomware packages which were linked with callbacks to Bitcoin nodes. The progression of Host F via the new addition of a Metasploit port created a cause for concern and potentially identifies Host F as part of a larger ransomware network. This possibility emerges seeing that Host F is now following the observed trends of Host A and Host B to have both C2 software and Metasploit running, with the links to Bitcoin nodes providing further cause for scrutiny and a reasonable assumption of malicious use cases.
Link analysis diagram from referenced report:
Analytic process:
As of 30 January 2023 Host F (95.213.145.99) was running two ports. These ports are 5357/HTTP (which was observed running Microsoft Windows) and 7070/UNKNOWN (while unknown, this port is possibly associated with AnyDesk, as 7070 is commonly identified as the default listener port for AnyDesk remote desktop software).
However, as of the morning of 24 January 2023, Host F was also running port 3790/HTTP, which was observed running Rapid7 Metasploit Pro and NGINX. On this port was a self-signed, untrusted Metasploit certificate (da6330dad891b30e0f92bd0e2e53162ca3dd8dc4f0d6415d69d4d2d9e4efa5e7).
The 3790 port running Metasploit was not observed at the time of Censys’ previous report, and was added for the first time on 13 October 2022. Just three days prior, on 10 October 2022, port 4444 was removed from the host for the last time. (Port 4444/TCP/UDP is the default listener port for Metasploit.) The maintenance of an active listener port for Metasploit immediately followed with the inclusion of an active exploit port likely indicates that the user(s) maintaining this port are still active and are the same as those observed earlier in 2022.
Alongside the change to the Metasploit and probable Metasploit ports running in early October 2022, the Windows associated ports also changed (to the two currently observed ports that 5357 and 7070). This would further solidify the port change explanation as an update to the user(s)’ operating system, as according to Rapid7 (the developers of the Metasploit software) users encountered issues with binding Metasploit to port 3790 after a Windows update or after losing their directory.
Going back historically, port 3790 is removed and re-added approximately every 30 days, alongside the other changes to the Windows associated ports. This removal has been observed to last anywhere from one day to eight days before being re-added. As of 30 January 2023, this port is still removed from the host.
Other ports seen active on the host include port 40815 which self-identified as “Rapid7 Security Console” and port 8834 which was observed with the software for Tenable’s “Nessus” vulnerability scanner. These were observed in early to mid December, and were removed on 21 and 22 December 2022 respectively. Additionally, port 8000 (which Censys reported as including a malware kit and callbacks to a Bitcoin wallet), was last observed by Censys on 13 September 2022, when the port was removed from the host.
Upon further analysis of historical Censys data of Host F, there were no observed consistencies in removal and addition of ports as now noted since the presumed software updates seen in October 2022. All other noteworthy findings were recorded and reported in Censys’ referenced July 2022 report. Upon completion of review, Censys analysts assess that this information may indicate that Host F has shifted its previous responsibilities of hosting ransomware kits and facilitating direct access and payment, to a more managerial role seeking new attack victims. Another possibility is that this host is or was part of a ransomware group and also a penetration tester by day, either during or after the removal of the ransomware kits and the port transitions to Metasploit.
For inquiries, email federal@censys.io. For this report and more, visit censys.io/federal.