Understanding and managing your organization’s internet-facing assets is crucial to minimizing cybersecurity risk. Attack Surface Discovery takes inventory of every asset—including the ones your team may not be aware of— and allows security teams to quickly identify vulnerabilities and remediate critical exposures before attackers can exploit them. A new CISA-sponsored report from the Cyentia Institute finds that exploited, public-facing applications are the number one initial access vector for ransomware. The findings underscore the need for comprehensive, real-time attack surface visibility.
Maintaining an accurate asset inventory of internet-facing assets is challenging, especially with accelerated digital transformation and cloud migration strategies. As assets proliferate across on-premises, cloud, and distributed environments, they introduce significant risks. Attackers thrive on the unknown, exploiting vulnerabilities in assets that organizations may not even realize they have. Without full visibility, security teams are left in the dark, unable to mount a proper defense. The reality is simple: without visibility, security is just guesswork.
Attack Surface Discovery with Censys
At Censys, we offer visibility from the attacker’s perspective, uncovering assets the way a malicious actor would. Our platform gives organizations the ability to see their external attack surface as an attacker sees it, identifying internet-exposed assets, weak points, and entry paths that would otherwise go unnoticed. This visibility is critical for achieving attack surface protection and ensuring that no vulnerabilities go undetected.
We’re able to offer this unmatched perspective because we’ve defined the standard for comprehensive Internet scanning technologies. In 2013, our co-founder Zakir Durumeric introduced zMap, an open-source network scanner specifically architected to perform internet-wide scans and capable of surveying the entire IPv4 address space in under 45 minutes from user space on a single machine, approaching the theoretical maximum speed of gigabit Ethernet.
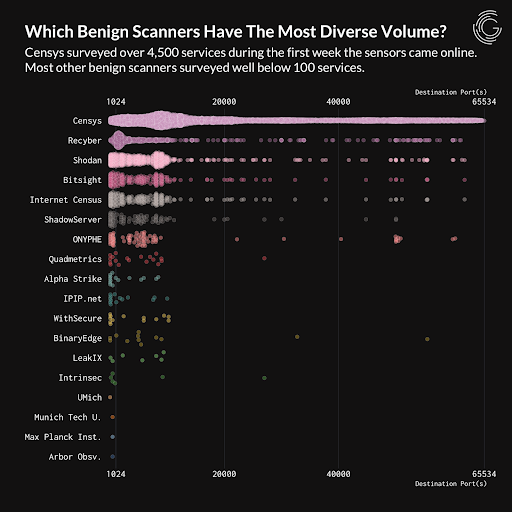
Since then, we have iterated on the core technology to build the world’s most comprehensive and accurate map of the internet, which we use to empower security teams to uncover exposures and act swiftly—before attackers do. We scan the internet faster and more comprehensively than anyone else, covering all 65K+ ports and maintaining the largest x.509 certificate repository on the internet. For example, an independent study by GreyNoise, Censys was found to be the #1 fastest benign internet scanner to connect to a new node on the internet.
Discover Your Attack Surface
Attack Surface Discovery 101
Before we jump into how Censys specifically supports attack surface discovery, let’s talk about what it means to “discover” an attack surface. Attack surface discovery is the process of identifying and associating all external, internet-facing assets to an organization. These internet-exposed assets are the same entry points targeted by attackers to extract sensitive information and gain initial access to an organization. Asset discovery encompasses:
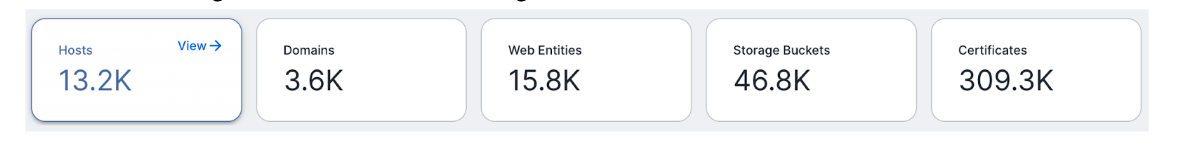
- Hosts are any internet-connected devices or servers that provide services, run applications, or store data accessible via IP addresses. These include physical servers, virtual machines, and cloud instances.
- X.509 Certificates are used to establish secure, encrypted communications between a client (e.g., a web browser) and a server. These certificates authenticate the identity of websites and services, ensuring that data transferred between them remains private.
- Web Entities encompass all internet-facing web services and applications associated with an organization, including websites, APIs, and microservices. These entities are often associated with specific domains or subdomains and may include various web technologies and frameworks.
- Storage Buckets are cloud-based repositories used for storing and accessing large amounts of unstructured data, such as files, images, backups, and logs. These are commonly found in cloud platforms like AWS S3, Google Cloud Storage, and Azure Blob Storage.
- Domains are unique names that identify and provide access to internet resources, such as websites and email servers. They are registered through domain registrars and are often associated with IP addresses through DNS records.
Asset discovery not only makes it possible for security teams to establish an asset inventory and more efficiently identify potential vulnerabilities, but creates opportunities to pursue attack surface reduction strategies.
Attribution 101
Traditionally in cybersecurity, attribution is the process of identifying a specific actor or group responsible for an attack. For External Attack Surface Management, we have a slightly different perspective and define attribution as the set of techniques to ascertain who owns a public-facing internet asset. All external-facing assets owned by an organization represent that organization’s external attack surface. While there are various attribution methods, the accuracy of the resulting attack surface always depends on the quality of the data used: garbage in, garbage out.
We can break Censys Attribution into a few layers:
- Censys Internet Map: The most up-to-date and highest-quality internet scan data available
- Pivot Like an Attacker: Crawling internet and network infrastructure
- Advanced Attribution Techniques: Unmatched coverage and accuracy
Pivot Like an Attacker: Crawling Internet and Network Infrastructure
Attribution starts with seed data, typically consisting of known, verified assets like domain names, Autonomous System Numbers (ASNs), or IP ranges owned by an organization. Seeds serve as the foundation from which additional assets are discovered.
Pivoting in traditional cybersecurity contexts often refers to the lateral movement technique used by attackers to navigate within a compromised network. However, in External Attack Surface Management, pivoting refers to the process of discovering additional external-facing assets by following interconnected network connections such as DNS records, WHOIS registrations, and X.509 certificates.
Examples of common attribution pivots include:
- IP to Domain: An IP address is linked to a domain name through DNS records.
- Certificate to Host: A x.509 certificate is attributed to a host presenting that certificate during a handshake.
- Domain to Subdomain: Hierarchical relationships between domains and subdomains can reveal additional assets.
- Netblock to IP: An IP address is associated with an organization if it falls within a known netblock range owned by that organization.
- Domain to IP: When a DNS record resolves to an IP address, attribution helps confirm whether this IP belongs to the organization.
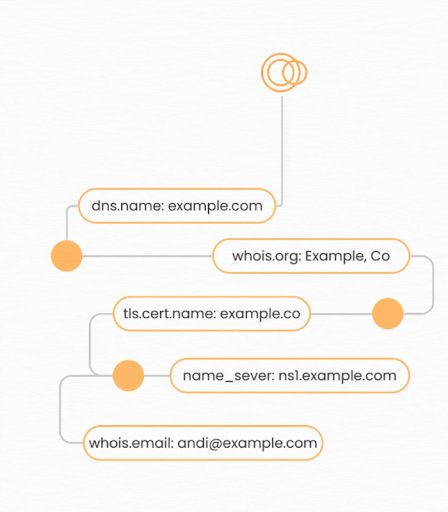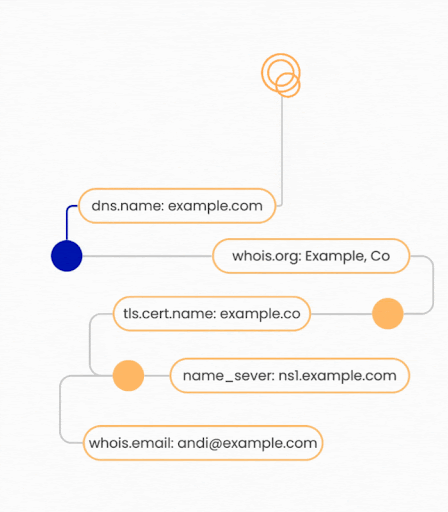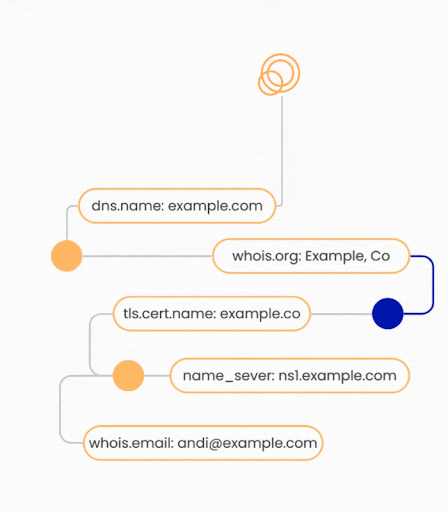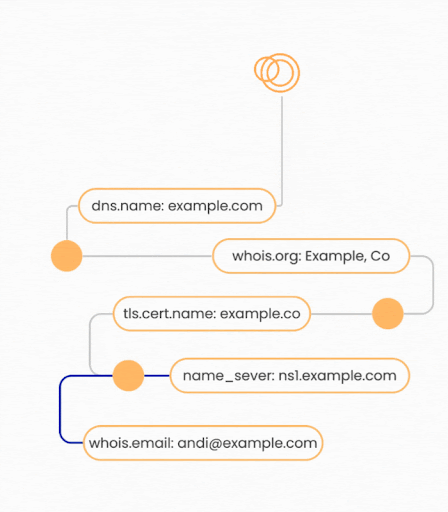
While most competitors only leverage common attribution pivots, Censys is able to leverage both common pivots and unique ones enabled through the Internet Map. For example, if there is no DNS record pointing to an asset, but it has a X.509 certificate with a name pointing back to the organization, Censys is able to find this due to our unique certificate repository.
By tracing these connections, Censys can accurately discover and attribute assets to an organization.
Delivering Unmatched Coverage and Accuracy
While other companies promote black box attribution techniques that rely heavily on behind-the-scenes human curation, at Censys, we err on the side of transparency to help our users understand and trust the data.
Daily Attack Surface Discovery
Our attack surfaces are updated daily. It’s that simple. We want to provide the best continuous attack surface discovery capabilities to ensure your organization is able to effectively close the visibility gap on potential vulnerabilities and secure exposures as quickly as possible. Each asset is accompanied by a discovery trail to help you understand how and why the asset was attributed to your organization.
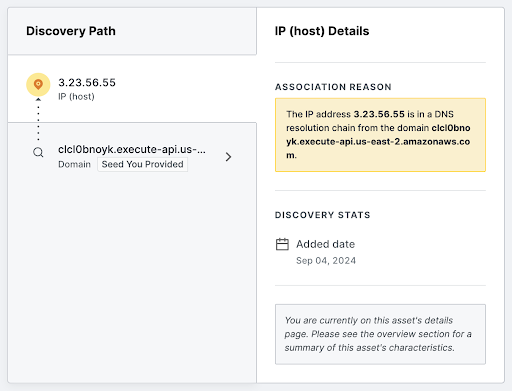
Automated Seed Discovery and Refresh
Providing a comprehensive list of seed information to start attack surface discovery can be daunting, especially when trying to expand visibility to subsidiaries. We know how hard that can be and have partnered with leading business and company intelligence sources to jumpstart the process. The process is relatively simple:
- Start with your organization’s name
- Review subsidiaries
- Validate registrant organization and registrant email addresses
- Approve discovered seeds
As a user, you’ll have complete control over which subsidiaries and seeds are included or excluded from your attack surface discovery to ensure the resulting attack surface is scoped to what you care about.
Over time, your organization changes and so do your seeds. Our entire process evaluates the Internet Map, whois registrations, and business intelligence sources daily to find changes. When a CIDR or domain whois record that was previously added as a seed changes registrant organization or registrant email address, we will send you an alert to remove the seed so that you can mitigate stale seeds from introducing false positives into the attack surface.
Conversely, when a new CIDR or domain is discovered with a matching registrant organization name or email address, we will alert you to approve and add the new seed to your attack surface. Our business intelligence sources help to find bigger changes like divestitures, acquisitions, and mergers. In other words, our automated seed discovery is always on so you don’t have to be.
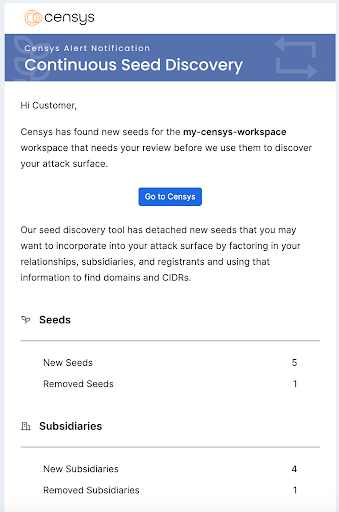
Automated seed discovery and refresh keeps your attack surface accurate by mitigating false positives introduced by stale seeds and reducing false negatives introduced by new acquisitions and CIDR and domain registrations.
65K Port Coverage with Predictive Scanning
Ports are logical endpoints to differentiate between various services or applications when communicating over a network. Each port is associated with a specific protocol or service, allowing multiple services to run simultaneously on the same machine while using the same IP address. When discovering an organization’s attack surface, it is critical to discover assets and all of the services running on those assets as well.
One of the main challenges is the sheer volume of services, and where they reside. There are standard port-service pairings (21 for FTP, 80 for HTTP, 443 for HTTP over SSL, and so on) which are well-documented by the Internet Assigned Numbers Authority (IANA). However, the Censys Research team found 7 in 10 HTTP services are on non-standard ports with HTTP being 88% of all internet services. This means that more than 60% of all internet services run on non-standard ports. Without intelligent scanning across 65,000 ports and visibility into these services, CISOs and security teams are missing key visibility into the exposures on the external attack surface, visibility that’s essential for effective vulnerability management and attack surface protection.
At Censys, we use statistical analysis to identify patterns and build heuristics to target active services and predictively scan across 65K non-standard ports. Predictive scanning adds over 107M new services to the ~3B global internet services we continuously monitor.
We’ve also found a 120% increase in port coverage than our competitor. Attackers scan for the hidden services on your attack surface that you don’t know about so that they can exploit them and gain initial access.
Automatic Protocol Detection
Other internet intelligence providers rely on standard port assignments to natively identify protocols (i.e. 443 = HTTP or 22 = SSH). However, this approach overlooks the reality that threat actors and network administrators often run services on non-standard ports (as discussed above). Automatic Protocol Detection from the Censys Internet Map, on the other hand, inspects application layer data and observes service behavior to identify the running service, giving you critical visibility into otherwise obfuscated exposures. For example, if an HTTP request results in an SSH banner, Censys closes the HTTP connection and reattempts an SSH handshake. Our scanners analyze every server response to identify its service, even if it’s non-standard for the port, allowing us to uncover the vast majority of services in unexpected places.
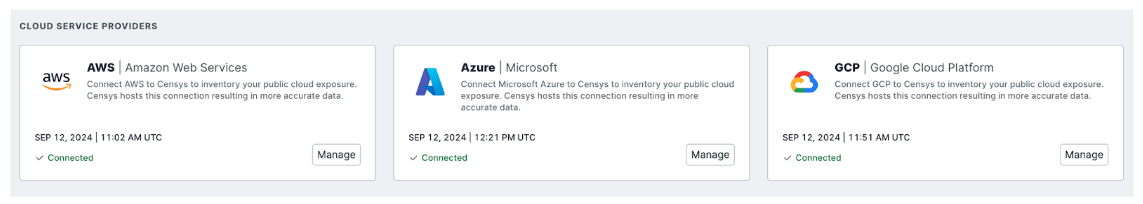
AWS, GCP, Azure Cloud Connectors
Cloud environments are dynamic, with assets being created, modified, or decommissioned frequently. Censys Cloud Connectors seamlessly integrate Censys Attack Surface Management with major cloud providers like AWS, Azure, and GCP to provide continuous visibility into your organization’s cloud assets. Censys Cloud Connectors pull assets from cloud environments up to 6 times per day, finding the assets other competitors miss due to their long scan intervals, and ensuring that cloud assets are as thoroughly monitored and managed as on-premises infrastructure.
Experience
We launched Censys Attack Surface Management in 2018 and have been moving fast and learning all the ways discovering an attack surface can go wrong, so that we can deliver a solution that gets it right. Superficially, pivoting through internet infrastructure is simple, but in practice, the internet is full of surprises, unique configurations, and shared infrastructure. It’s also constantly changing with new privacy regulations like GDPR and privacy guards.
Our team has implemented additional filters to ignore shared certifications, name servers, names, and privacy guards as well as filtering out noise introduced by “super” hosts and wildcard DNS records. We have implemented block lists with over 1300 registrant organizations and over 50 different domain suffixes that reduce false positives. We know that 3rd party data is important but can also be stale, so we cross-validate 3rd party data sources to ensure the highest level of attack surface accuracy.
Last but not least, we enable our customers with the control they need to truly tune the attack surface through adding known seeds or excluding assets because it is nearly impossible to get the attack surface right without partnering and listening to our customers.
Improve Asset Discovery and Vulnerability Management with Censys
At Censys, we invented internet scanning and know the internet better than anyone else. Through years of research and innovating with our customers, we’re proud to have built the most comprehensive, up-to-date, and accurate external attack surface discovery solution on the market.
Reach out to us today to learn more about the specific ways Censys can help your team with attack surface discovery and remediation.
Book Your ASM Demo Now