While recently re-evaluating C2 fingerprints I was checking the logic of Agniane Stealer which could be discovered with the following query.
services: (http.response.favicons.md5_hash=”ef05ae61e6cfce0f261635b68bacd524″ and http.response.body: “https://t.me/agniane”)

Historical Virtual Host – Running on Cloudflare
We haven’t seen any Agniane Stealer in some time so I decided to look at hosts with the string “https://t[.]me/agniane” in the HTTP body. I got 11 results but none of them were labeled as Agniane Stealer.
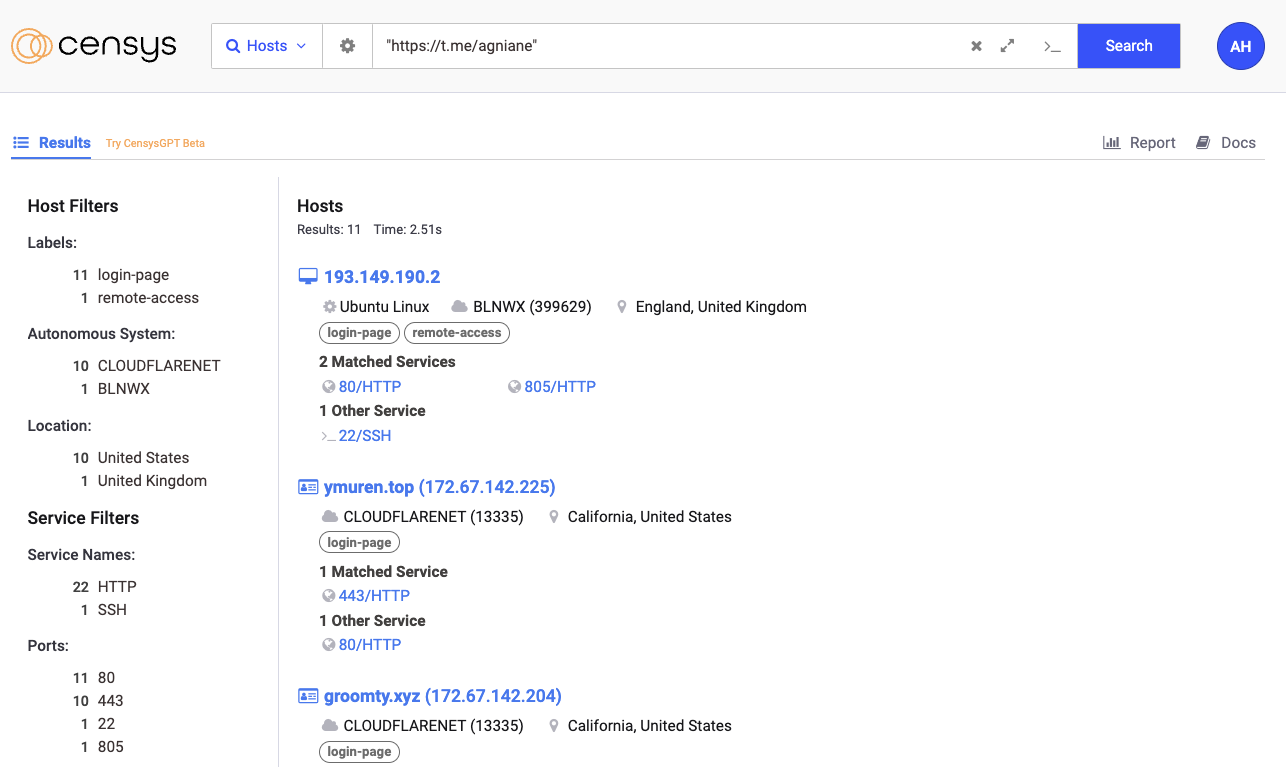
However, only one was a raw host that wasn’t behind Cloudflare, 193.149.190[.]2.
Looking at the Markdown preview I am able to see there is a header “xehook.stealer” and the same Telegram channel /agniane. XehookStealer is a piece of known malware as a service infostealer that targets Windows systems. It also uses SmokeLoader binaries for distribution. It has overlapping code with Agniane Stealer, that I now confidently can confirm that it has the same author.
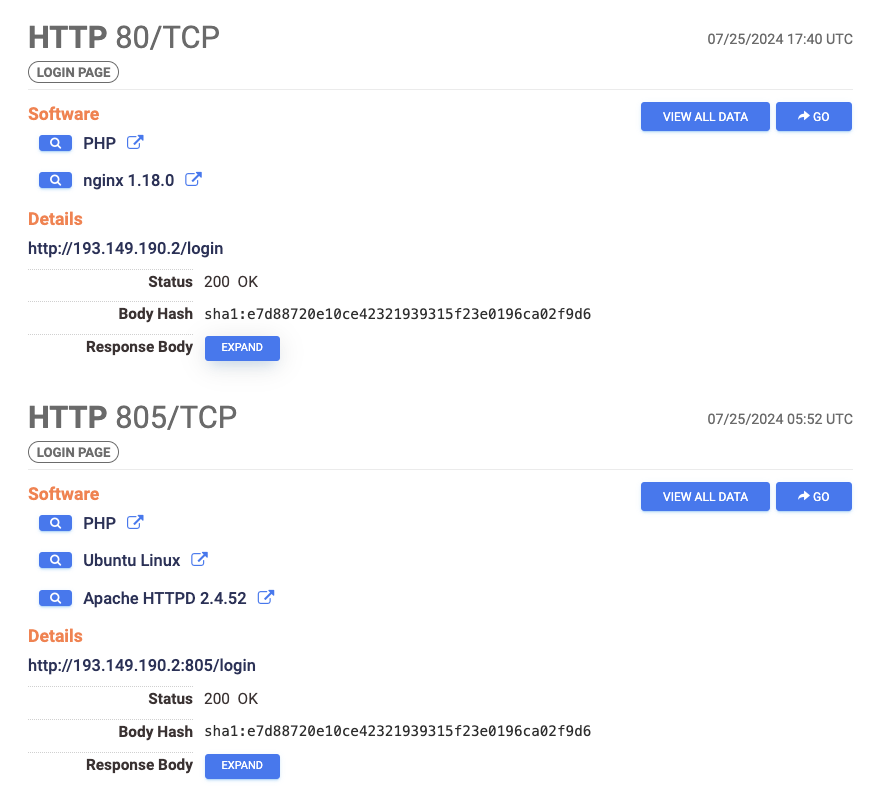
Using urlscan I am able to safely capture a screenshot of the login page.

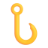
Then I looked at the favicon to find it was a literal hook icon, I went to check the host table view to find the favicon MD5 hash 63e939086ab01ddefcef0cfd052b7368.
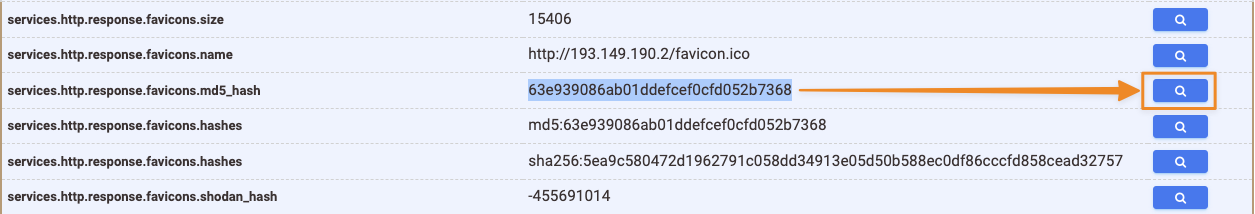
I could then pivot on the hash to see how common that favicon is. I was then presented with the same results as my first search. Those same 11 hosts all have the same favicon, strings in the HTTP body, and the same HTTP endpoint of /login. Those factors lead me to this final query.
services: ((http.response.favicons.md5_hash=”63e939086ab01ddefcef0cfd052b7368″ or http.response.body: “<span class=\”fs-1\”>xehook.stealer</span>”) and http.response.body: “https://t.me/agniane” and http.request.uri: “/login”)