Introduction
It’s been about two months since we released our 2023 State of the Internet Report. With access to the most comprehensive internet-wide scan data available, narrowing our focus for the report to a specific area or set of technologies on the internet was a formidable challenge. Ultimately, we decided to focus on the web, as it’s an integral part of our lives and impacts many of our day-to-day activities.
In practice, this meant focusing on HTTP, the protocol that powers the web, along with TLS, which facilitates encryption of web traffic. Finally, we examined the state of web security by examining web application misconfigurations and data exposures.
We should note that though the terms “internet” and “web” are often used interchangeably, they are distinct concepts. While the internet is the global network-of-networks that connects devices via physical and wireless connections, the web is the data made accessible via the internet.
Below, we’ll revisit some of our most interesting findings about HTTP, TLS, and web security.
Good news for encryption across the web
Google research indicates that over 90% of web traffic today is encrypted, nearly double the amount of encrypted traffic observed roughly a decade ago.
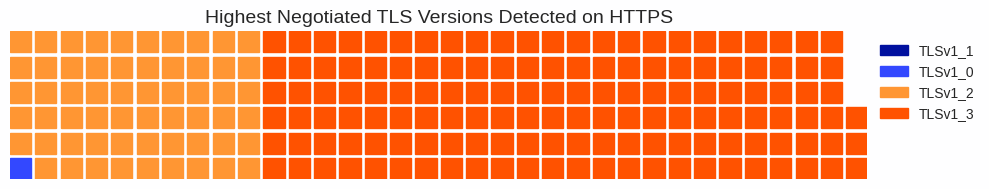
Proportion of HTTPS services by highest negotiated TLS version detected; note that TLS 1.1 is not even represented on this graph because so (relatively) few services negotiate it as the highest version
What’s more, of the encrypted entities we observe–those using TLS–about 95% of them are using TLS 1.2 or 1.3. These are the two latest, most secure versions of TLS, and we observe steady adoption of TLS 1.3 over the last year. All of this is encouraging news for internet users’ privacy and security.
The danger of unauthenticated monitoring tools
Unfortunately, not all of our findings were encouraging. In our investigation of exposed back office web applications, we discovered over 40,000 Prometheus instances exposed to the internet, collectively monitoring over 219,000 endpoints. Prometheus, a popular systems monitoring tool, allows users to collect, store, and alert on metrics about systems in their environment.
However, Prometheus has no authentication by default. Without proper access controls, anyone with internet access can view the activity in a Prometheus instance. Information about an organization’s systems and devices can be useful for a threat actor performing reconnaissance against an organization.
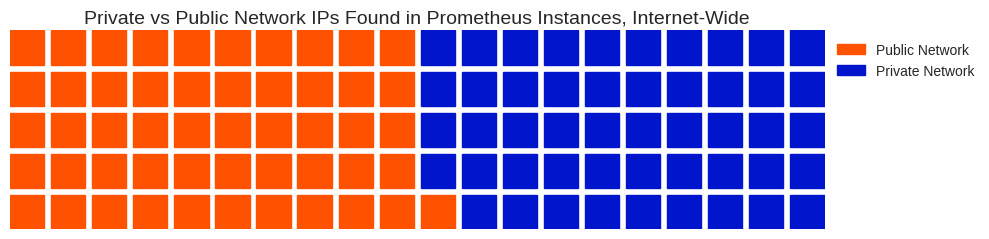
Proportion of private and public network IP exposure observed in internet-exposed Prometheus instances
Perhaps even more concerning than the exposed Prometheus instances themselves, we discovered that 48% of the endpoints being monitored in these tools exist in private IP and DNS space. These private endpoints typically wouldn’t be visible from outside an organization’s network, making this visibility particularly valuable for threat actors.
When considering the reconnaissance value of public versus private IP and DNS space, imagine a thief casing a building as they’re planning a heist. The public IP and DNS information is analogous to walking by the building, noting entrances, exits, and other general information about the structure. Private IP and DNS information, however, is comparable to the thief obtaining blueprints for the building, complete with labels for various offices and other rooms in the building.
This data could allow a threat actor to generate a detailed map of infrastructure prior to ever even gaining access to the network.
Misconfigurations and exposures are still a real problem
Beyond improperly exposed monitoring tools, we identified over 8,000 hosts on the internet hosting various database information, backup files, passwords, Excel worksheets, environment variables, and even some SSL and SSH private keys. These were trivial to find and could make a threat actor’s job very easy.
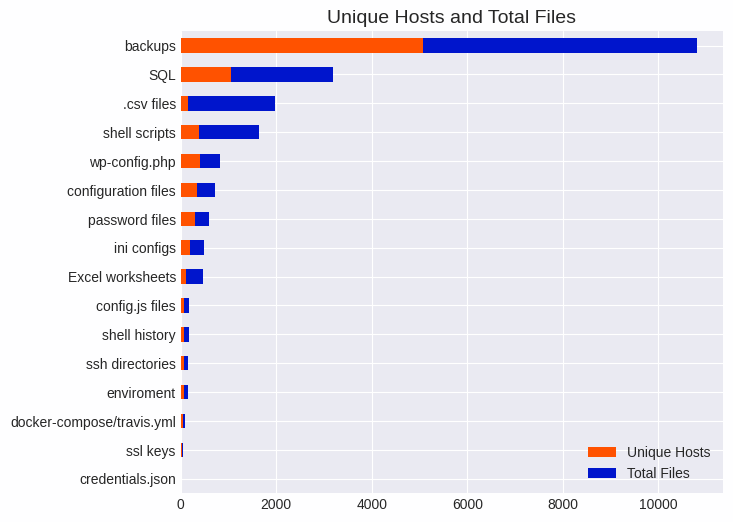
Potentially sensitive file and host counts
While misconfigurations and exposures may not seem quite as exciting as a zero day, we continue to see organizations affected by such security issues.
Where do we go from here?
Good security hygiene is essential for avoiding missteps like the ones outlined above. In particular, it’s important to implement asset, patch, and vulnerability management processes if you don’t already have plans in place. These are foundational pieces of a strong security posture.
Download your copy of our 2023 State of the Internet Report here.