Emily Austin & Mark Ellzey
UPDATE 2023-02-15
Please see our new post, The Evolution of ESXiArgs Ransomware, for further updates.
UPDATE 2023-02-13
Over the weekend (2023-02-09 through 2023-02-11), we’ve seen a slight increase in the number of infected hosts, where at the time of writing, there were 1,994 hosts found in our search engine. We are awaiting a new historical search index to drop and will have more detailed updates ready on February 14th, 2023.
Below are some general stats about the current state of infected VMWare instances we have observed on the internet.

| Country |
Host Count |
| France |
649 |
| Germany |
281 |
| United States |
203 |
| Canada |
136 |
| Netherlands |
66 |
| United Kingdom |
60 |
| Finland |
33 |
| Ukraine |
26 |
| South Korea |
14 |
| Switzerland |
13 |
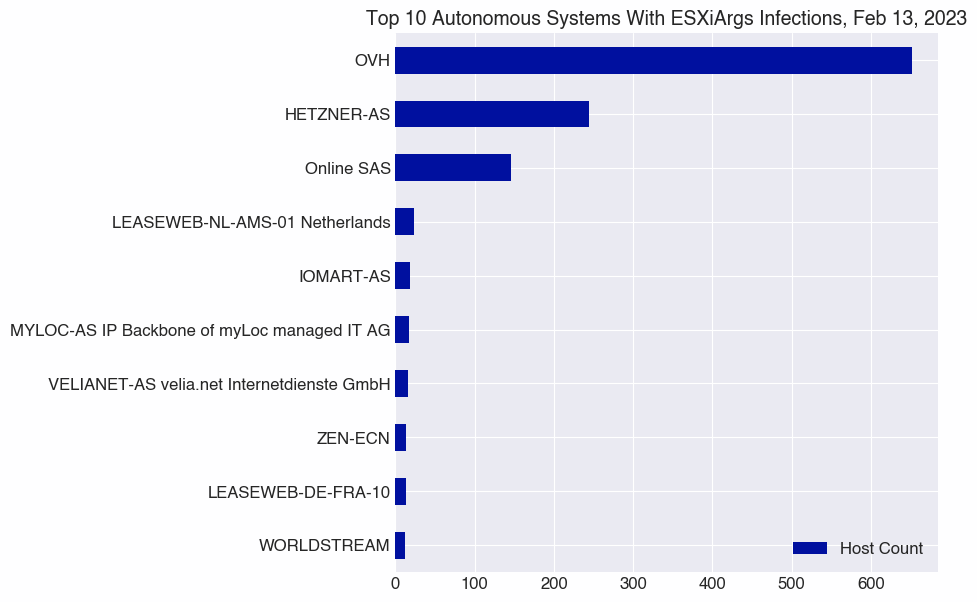
| Autonomous System |
Host Count |
| OVH |
652 |
| HETZNER-AS |
244 |
| Online SAS |
146 |
| LEASEWEB-NL-AMS-01 Netherlands |
23 |
| IOMART-AS |
18 |
| MYLOC-AS IP Backbone of myLoc managed IT AG |
17 |
| VELIANET-AS velia.net Internetdienste GmbH |
16 |
| LEASEWEB-DE-FRA-10 |
13 |
| ZEN-ECN |
13 |
| WORLDSTREAM |
12 |
UPDATE 2023-02-09
Executive Summary, Update:
- We’ve observed a new variant of ESXiArgs emerge over the last 24 hours. Key updates to this version include:
- A new ransom note with no BTC addresses–making it more difficult for researchers to track payments
- Encryption of additional data, rendering existing decryption tools ineffective
- In the last few days, we’ve seen just over 3,800 unique hosts compromised, and 1,800 which are online currently. Over the last 24 hours, just over 900 hosts have upgraded to the latest ransomware variant.
- As we reported yesterday, OpenSLP does not appear to be the method of attack, given that multiple compromised hosts did not have SLP running.
Over the last 24 hours, we’ve observed an updated variant to this ransomware campaign which makes the ransomed files harder to recover:
“New ESXiArgs ransomware attacks are now encrypting more extensive amounts of data, making it much harder, if not impossible, to recover encrypted VMware ESXi virtual machines..” (via BleepingComputer)
Our suspicion that OpenSLP (CVE-2021-21974) was not the method of attack due to observing several compromised servers not running the SLP protocol seems to have been correct:
“Preliminary reports indicated that the devices were breached using old VMware SLP vulnerabilities. However, some victims have stated that SLP was disabled on their devices and were still breached and encrypted.”
This new variant also updates the ransom note itself, which removes the bitcoin address from the HTTP body, making it harder for researchers to track the transactions. Below is a screenshot that shows the changes made to a compromised host’s services when attackers installed the new variant. Now victims are asked to contact the attackers to obtain the BTC wallet.
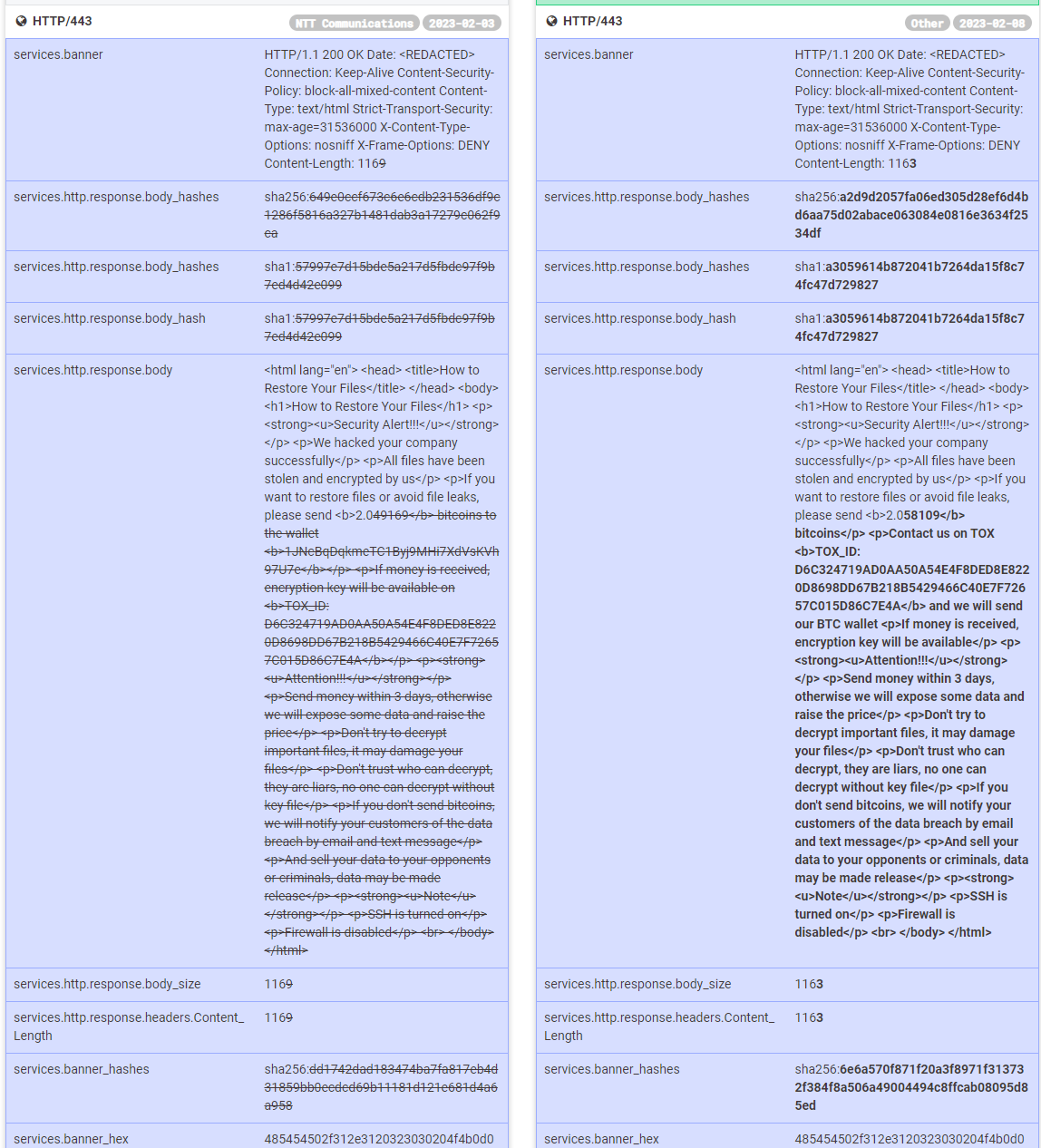
The timing of this update seems like a direct response to CISA’s decryptor and observations made by security researchers. They likely followed updates from the security community. They realized that researchers were tracking their payments, and they may have even known before they released the ransomware that the encryption process in the original variant was relatively easy to circumvent. In other words: they are watching.

The screenshot above shows the new “encrypt.sh” script being run on a compromised host, which we obtained via a public SNMP interface yesterday (using “snmptable”) at around 2PM EST.
In the last few days, we’ve seen just over 3,800 unique hosts compromised, and 1,800 which are online currently. Over the last 24 hours, we’ve seen just under 900 hosts upgraded to the latest variant of the ransomware.

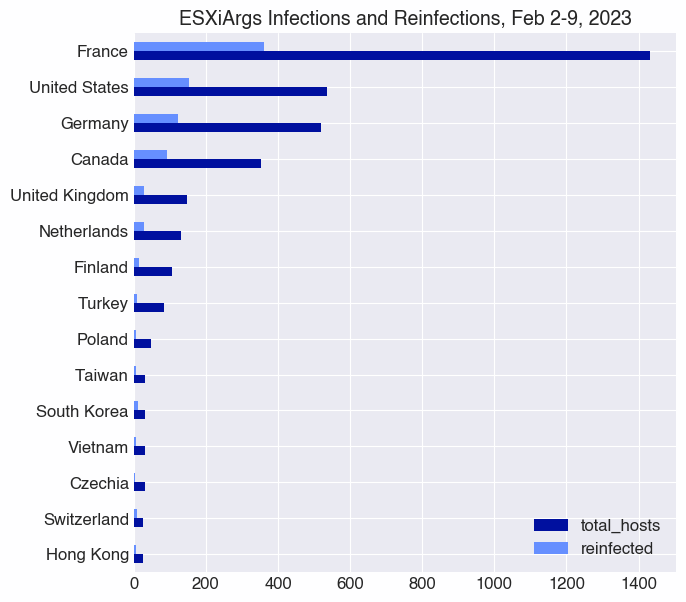
The global distribution of reinfections largely mirrors the distribution of infections we observed previously, with France, the US, Germany, and Canada most prominently affected. However, South Korea has risen above Turkey, Poland, and Taiwan in the number of reinfections, though it has fewer total infections.
Executive Summary, 2023-02-08
- A ransomware campaign targeting VMWare ESXi servers began in early Februrary, 2023. The ransomware, dubbed ESXiArgs, peaked in infections on February 3, with Censys observing 3,551 infected hosts.
- Typically, ransomware takes hosts offline and leaves few artifacts visible to the public Internet. ESXiArgs ransomware, however, presents ransom notes to the Internet, making them visible to Censys’ passive scanners.
- Bitcoin wallet addresses are posted on the ransom pages, allowing us to track payments associated with this ransomware.
- France, US, Germany, Canada, and other countries have seen attacks, with many occurring in France, particularly against hosts on French cloud provider OVH.
Introduction
In early February, reports of a ransomware campaign affecting VMWare ESXi servers began circulating online, including notices from the Austrian CERT, the Italian CSIRT, and French hosting provider OVH. As indicated in the advisories, threat actors are actively exploiting a vulnerability in VMWare ESXi, CVE-2021-21974, to deploy ransomware. As readers may note by the designation of this CVE, it was released two years ago, with a patch available for just as long.
For information about vulnerable versions of ESXi, refer to NIST’s documentation on the CVE.
This CVE allows a threat actor to trigger a heap overflow in the OpenSLP service, which can result in remote code execution. Per the VMWare advisory, to execute such an attack, the actor must have access to a system that resides within the same network segment as ESXi and have access to port 427. This raises the question: how was that initial access gained if local network access is needed to exploit?
Also anomalous is how some of the compromised servers were running SNMP with public access, which we could then leverage to determine if a process was listening on specific ports. Oddly enough, not every compromised server was running the SLP service, although some were. Below are two screenshots showing the output of snmpnetstat against two separate compromised servers, which display processes listening on the network. One shows an SLP service running, the other does not.
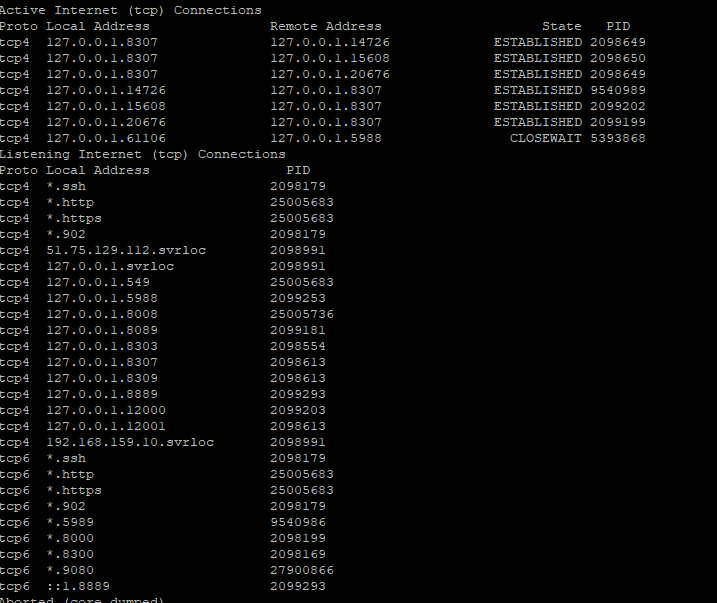
Above: Compromised ESXi service with an SLP server listening (“svrloc”).
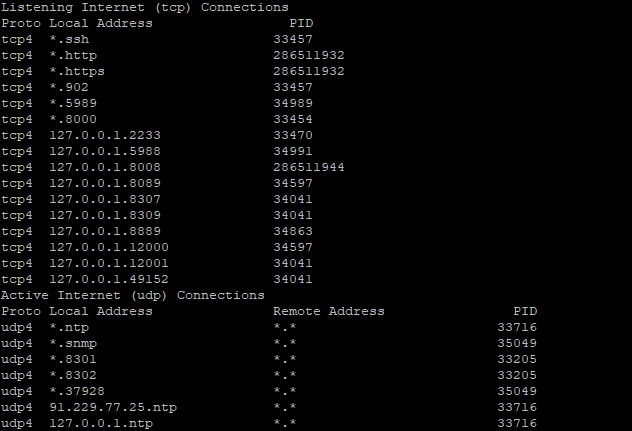
Compromised ESXi service with no SLP listening.
Our View
This ransomware is particularly interesting for us because typically, when systems are ransomed, they go offline, leaving minimal artifacts visible to the public Internet. However, with this ransomware–similar to what we saw with Deadbolt infections–the Internet-facing ransom pages give us a way to track infections.

ESXiArgs ransom note, with wallet address and TOX_ID redacted
Moreover, the BTC addresses included on the pages allow us to track transactions to understand how successful this campaign might be.
Nearly all of the 2,782 Bitcoin addresses found in the ransom notes begin with a “1,” which are Legacy addresses. Only two, bc1q46zs36ey53lem5qv2pryumtmdtmtr352fdk4pj and bc1qdcadgtv5d6kqdl70g9vgg7u3vkqvfy3kwz66qj, are prefixed with “bc1,” which indicates a Bech32 format address. The “bc1” format of addresses are not as widely adopted among exchanges as are their older legacy counterparts, though hardware wallets like Ledger and Trezor offer support for “bc1” Bech32 addresses.
Leveraging BigQuery’s public Bitcoin transaction dataset and blockchain explorer tools, Censys has observed 4 of the BTC addresses receive funds totaling roughly $88,000 USD, since 2023-02-02.
CISA and others have released tools to aid victims in decrypting their data, which may be one explanation for why relatively few payments appear to have been made.
Observations
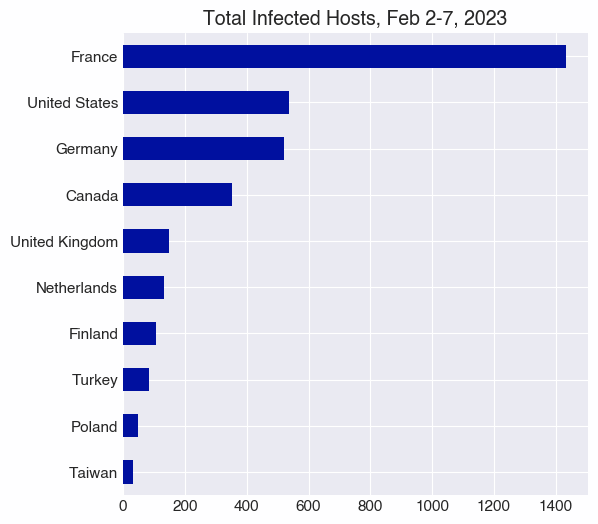
The majority of infected hosts we observed over the period of February 2-7, 2023, are located in France. France’s more than 1,400 infected hosts are an order of magnitude more than infected hosts in the US and Germany, the next most common locations.
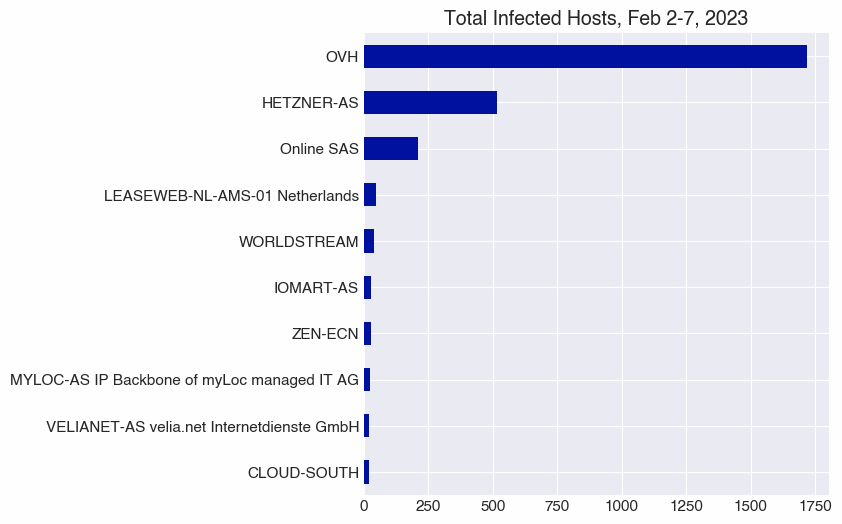
Perhaps not surprisingly, we observed that French cloud hosting provider OVH is by far the most affected autonomous system, with just over 1,700 infected hosts during the 6-day time period we studied.
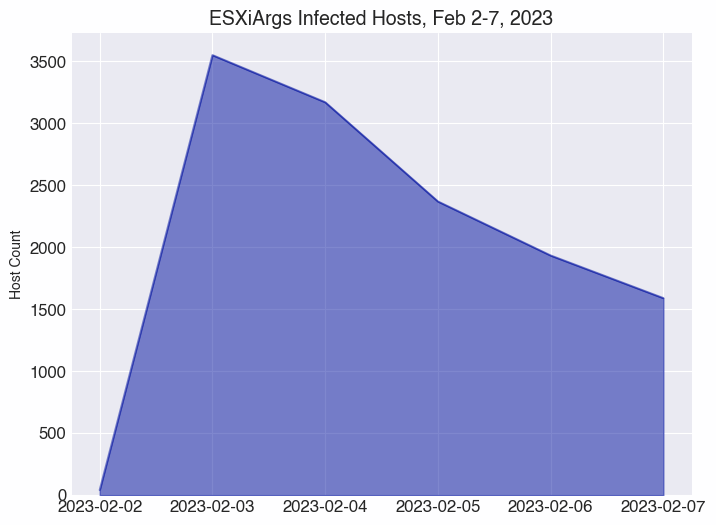
Examining the numbers of affected hosts, it’s clear when the campaign roared to life; we’ve observed a steady decrease of infected hosts online since the peak of 3,551 infected hosts on February 3.
We’ll continue monitoring this campaign for signs of more activity, and you can too, using this Censys search.
Additional Reading