Executive Summary
- On October 19th, the number of compromised Cisco devices has ebbed to 36,541, over 5,000 less than 24 hours ago.
- On October 18th, we have seen an increase in the number of infections from 34,140 to 41,983 hosts.
- On October 16, Cisco released an advisory regarding a critical zero day privilege escalation vulnerability in their IOS XE Web UI software
- This vulnerability, tracked as CVE-2023-20198, has already been used to exploit tens of thousands of devices to install a backdoor
- As of this post, Censys researchers observe 34,140 devices that appear to have the backdoor installed

The Vulnerability
The last few weeks have seen their fair share of potential sky-crumbling advisories: The Exim vulnerability, which amounted to much of nothing, and the HTTP/2 “Rapid Reset” attack, which was only a problem for the top internet providers running bleeding-edge web technologies in heavily proxied environments. But this time, Apollo, I think we have a problem.
On Monday, October 16th, Cisco released information about a vulnerability that affects devices running the IOS XE software alongside the web administration interface. Tracked as CVE-2023-20198, this vulnerability has the highest criticality score of 10 and can be exploited remotely without authentication, granting the attacker full administrative privileges.
If that wasn’t bad enough, attackers have already used this vulnerability to exploit tens of thousands of devices to gain access and install a backdoor. This backdoor activity was found because of an existing detection rule for an older vulnerability, CVE-2021-1435. The Cisco Talos team on Monday said the following:
“Leveraging existing detections, we observed the actor exploiting CVE-2021-1435, for which Cisco provided a patch in 2021, to install the implant after gaining access to the device. We have also seen devices fully patched against CVE-2021-1435 getting the implant successfully installed through an as of yet undetermined mechanism.“
Identifying Compromised Hosts
Talos also details an indicator of compromise (IOC) which any user can use to determine if their device has fallen victim to this attack:
curl -k -X POST "https[:]//DEVICEIP/webui/logoutconfirm.html?logon_hash=1"
If the server responds with a 200 status code, along with an 18-byte hexadecimal string, then the device has been compromised and is running the injected backdoor.
In order to aid researchers, Censys deployed a new label for finding these specific Cisco web interfaces: labels=`cisco-xe-webui` which will tag potentially vulnerable hosts over the next 48 hours. It should be noted that this does not say whether the device is compromised or not, just that it is running a Cisco IOS-XE web interface.
We have also conducted a secondary scan to analyze just how widespread this vulnerability is by using Censys data as a baseline and utilizing the open-source utilities censys-cli, httpx, and jq to conduct our analysis.
$ censys search 'services.labels=cisco-xe-webui' \
| jq -cr '.[] | . | .ip as $ip \
| .matched_services[] \
| { ip: $ip, sn: .extended_service_name | ascii_downcase, port: .port } \
| "\(.sn)://\(.ip):\(.port)"' | \
httpx -bp -title -sc -x POST \
-path /webui/logoutconfirm.html?logon_hash=1 -mr '([a-f0-9]{18})'
The Censys View
October 19th, 2023
In the past 24 hours since our last update on the ongoing compromises, there’s both promising and concerning news. While the initial surge of compromises appears to have diminished, we’re now grappling with a substantial number of compromised routers. This poses a potential threat to many organizations.
Our recent scan from this evening showed encouraging results: a notable decrease in infected devices. More than 5,400 Cisco XE devices have either removed their web interface from the internet, been taken offline, or had their configurations reset. However, Censys has identified 36,541 devices that remain online and compromised.
The silver lining is that awareness about this attack has spread. Amplifying this message is crucial, as the safest move is to take these devices offline. The fact that over 5,000 devices have been secured or disconnected in just one day is commendable, but we’re not out of danger yet.
October 18th, 2023
We reran the scan overnight and found a sharp increase in infections. Iterating on our current query to find potential targets, we updated it with some more generic conditionals, hoping to find even more potentially vulnerable hosts. Unfortunately, the updates were successful, and we found even more compromised hosts this morning. Here is an updated set of statistics.
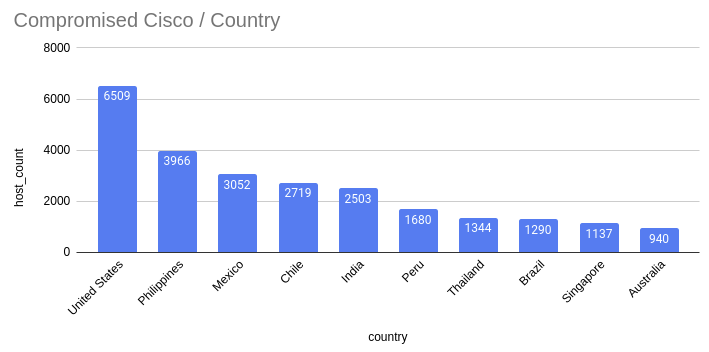
| Country |
Host Count |
Delta |
| United States |
6,509 |
+1,850 |
| Philippines |
3,966 |
+742 |
| Mexico |
3,052 |
+720 |
| Chile |
2,719 |
+385 |
| India |
2,503 |
+588 |
| Peru |
1,680 |
+370 |
| Thailand |
1,344 |
+17 |
| Brazil |
1,290 |
+190 |
| Singapore |
1,137 |
+214 |
| Australia |
940 |
+17 |
This increases the number of infections to 41,983 hosts from the previous number of 34,140 hosts
October 17th, 2023
In our data analysis, we identified 67,445 hosts utilizing the Cisco web interface. Alarmingly, 34,140 distinct hosts—slightly more than 50%—showed evidence of the backdoor associated with the recent CVE, indicating they have been compromised.
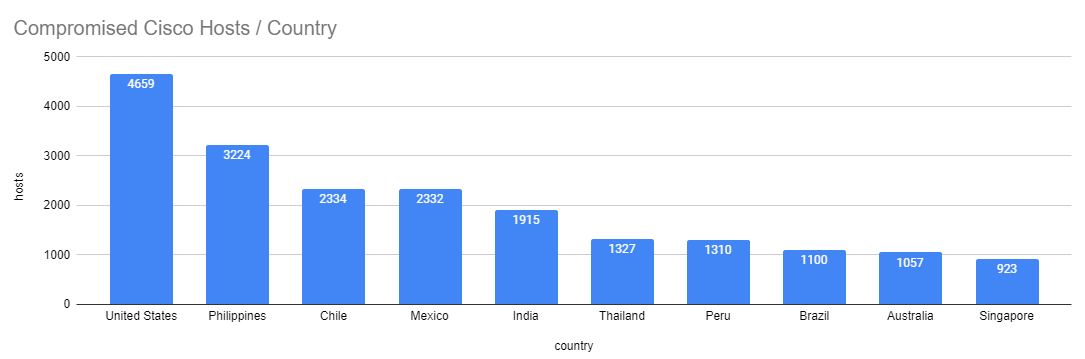
| United States |
4,659 |
| Philippines |
3,224 |
| Chile |
2,334 |
| Mexico |
2,332 |
| India |
1,915 |
| Thailand |
1,327 |
| Peru |
1,310 |
| Brazil |
1,100 |
| Australia |
1,057 |
| Singapore |
923 |
The United States has the majority of compromises, with 4,659 devices having the backdoor installed, along with the Philippines close behind with over 3,200 compromised hosts. But this only paints a small picture. By looking at the autonomous systems that house these compromised devices, we can get a better idea of who the general victims are:
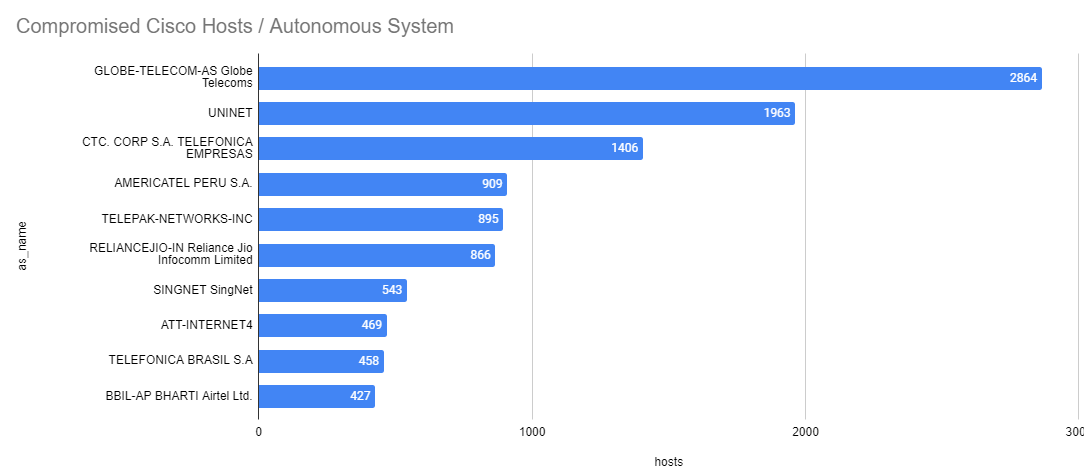
| GLOBE-TELECOM-AS Globe Telecoms |
2,864 |
| UNINET |
1,963 |
| CTC. CORP S.A. TELEFONICA EMPRESAS |
1,406 |
| AMERICATEL PERU S.A. |
909 |
| TELEPAK-NETWORKS-INC |
895 |
| RELIANCEJIO-IN Reliance Jio Infocomm Limited |
866 |
| SINGNET SingNet |
543 |
| ATT-INTERNET4 |
469 |
| TELEFONICA BRASIL S.A |
458 |
| BBIL-AP BHARTI Airtel Ltd. |
427 |
What characteristics do most of these autonomous systems share? They predominantly represent telecommunications companies offering internet services to both households and businesses. Take, for instance, ATT-INTERNET4: while commonly linked with residential internet access, it also delivers business solutions, evident in its use of the enterprise-grade Cisco (XE) router. As a result, the primary targets of this vulnerability are not large corporations but smaller entities and individuals who are more susceptible.
Censys is still gathering data, and the newly created labels are deploying. We will have updates within the next 48 hours, and for now here are a few links: