Executive Summary
Background
On August 28, 2024, the Federal Bureau of Investigation, Cybersecurity and Infrastructure Security Agency (CISA), and the Department of Defense Cyber Crime Center (DC3) published a joint Cybersecurity Advisory (CSA) “to warn network defenders that, as of August 2024, a group of Iran-based cyber actors” (aka “Fox Kitten”) continues to exploit U.S. and foreign organizations.”[1] The CSA included a list of 17 IOCs (12 IP addresses/hosts, five domain names) with “First Seen” and “Most Recently Observed” dates but added, defenders should “investigate or vet these IP addresses prior to taking action….” and “[T]he FBI and CISA do not recommend blocking of the indicators in Table 11 based solely on their inclusion in this CSA.”
Censys’ Perspective
Censys assisted defenders in these tasks of investigation and vetting by leveraging its historical, global internet perspective to analyze the IOCs’ profiles during the timeframe of nefarious activity outlined in the CSA. This allows defenders to compare those historical profiles against the hosts’ current dispositions and determine if enough similarities exist to recommend blocking the IOCs in question.
Censys’ Findings
By investigating the hosts connected to the IOC IPs as well as the hosts and certificates connected to the domain IOCs listed in the FBI/CISA Advisory for Fox Kitten, Censys was able to uncover extremely unique patterns amongst these hosts over time. These patterns were then used in searches to:
- Find active hosts not mentioned in the Advisory that have:
- Matching patterns and Autonomous Systems (ASs) as Hosts D, E, & G from the report, and could be part of the same infrastructure to possibly be used in future attacks
- Matching domain IOCs to Host G and matching ASs to Hosts J & C from the report and could be part of the same infrastructure to possibly be used in future attacks
- Identify timeframes outside of those specified in the Advisory where IOC hosts appear similar or identical to the timeframes of nefarious activities, possibly indicating previously unknown durations of threat activity
- Find current certificates with matching domain IOCs that could be used on future hosts.
Analysis
Censys uncovered unique and unusual patterns observed historically on the IOC hosts that seem to have no known, legitimate use. Therefore, the active hosts that match these patterns, discovered via Censys Search are, at worst, part of the Fox Kitten infrastructure and at best, still worth consideration for cyber defenders to guard against as they seem to have no legitimate business function. The same can be said for the two active hosts that have matching domain IOCs.
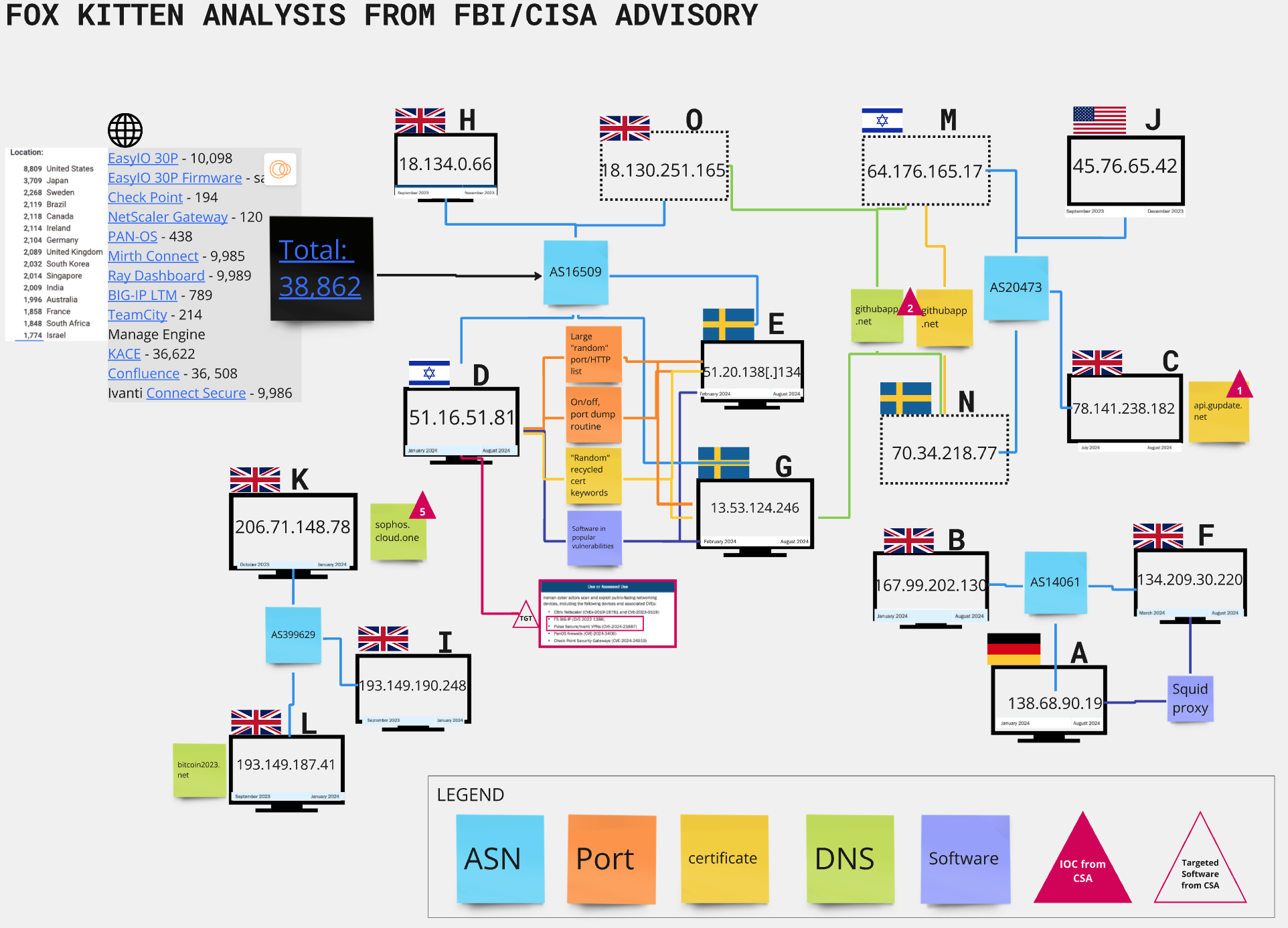
Link analysis diagram of Indicators of Compromise (IOCs) listed in Joint CSA AA24-241A

Consolidated list of IOCs from Joint CSA AA24-241A
Key Findings
Commonalities Amongst IP IOCs from Report
- 9 of the 12 hosts share geolocations
- 7 hosts = London, UK (Hosts B, C, F,H,I, K, L)
- 2 hosts = Stockholm, SWE (Hosts E, G)
- 1 host each= Frankfurt, DE (Host A) Los Angeles, US (Host J) Tel Aviv, IS (Host D)
- All of the hosts have an Autonomous System Number in common with at least one other host from the group
- AS 14061 (DIGITALOCEAN-ASN) = Hosts A, B, F
- AS 16509 (AMAZON-02) = Hosts D, E, G, H
- AS 399629 (BLNWX) = Hosts I, K, L
- AS 20473 (AS-CHOOPA) = Hosts C, J
- Hosts D, E & G are not “identical” but share nearly identical patterns of ports, certificate names, and software/HTTP Titles; these patterns match findings from a Censys Mirth Connect blog from May 2024. An assessment from the blog stated that hosts with these characteristics indicated “a particular variety of honeypot-like entities that seem designed to catch internet scanners.”
- Patterns during times of interest from the report include:
- A long list (20+) of open services/ports, the vast majority of which are HTTP
- HTTP ports with HTML Titles and/or software fingerprints for
- Mirth Connect (also covered in Censys Rapid Response (RR) blog)
- Ivanti Connect Secure (covered in RR blog, RR 08APR24 Advisory)
- Ray Dashboard (covered in RR 28MAR24 Advisory)
- F5 BIG-IP (covered in RR blog)
- Confluence
- KACE
- JetBrains Team City (only Host G)
- ManageEngine (only Host G)
- Certificates presented on HTTP ports that are seemingly random, but reuse a list of names to appear part of legitimate organizations, including “futureenergy.us,” next-finance.mil,” “schneider-electric.oil-bright.mil” etc. The subdomains listed in some of the certificates include some of the same software types listed above including “kace”, “bigip” and “fortinet.”
Note: Using the ‘tarpit’ label in Censys Search (especially on the same AS as Hosts D, E, & G) will help analysts find more of these same hosts with certificates matching the same pattern as the ones mentioned above.
Analysis: It appears that the owners/operators of the IOC hosts may have been attempting to obfuscate relations between the hosts by choosing various ASs, locations, certificates and port configurations among other techniques; however, by viewing the profiles of these IOC hosts in totality, patterns emerge that link the hosts. These links, coupled with their identification as IOCs by the FBI/CISA/DC3, further the claim that they are related to nefarious activity.
Commonalities in Initial Hosts Used to Uncover Possible Additional Infrastructure Not Mentioned in FBI/CISA Report
- A search conducted for the “tarpit” label (indicating hosts with an unusually high number of ports open on a host) on Censys Search within the same ASN as Hosts D, E, & G reveals a total of 38,862 hosts globally that seem to match the same patterns of Hosts D, E, & G of:
- A long list (20+) of open services/ports, the vast majority of which are HTTP
- Those HTTP ports with running software that includes the list above but also includes Easy IO 30P, Check Point (Check Point Security Gateways was also listed as a targeted software product in the FBI/CISA Advisory), and PanOS (again, listed in the FBI/CISA Advisory as targeted).
- Certificates on the HTTP ports follow the same pattern as those on Hosts D, E, & G
Note: Host G exhibited these patterns in SEP & NOV23
Analysis: While further confirmation will be needed, it is logical that these hosts may be part of the same infrastructure owned by the Fox Kitten group due to the amount of similarities between the hosts found through these searches and the known bad actor Hosts D, E, & G listed in the FBI/CISA Advisory. This information can be used by organizations to add to watchlists or blacklists, especially if those hosts match the AS, country of origin, or have similar octets to the IPs uncovered via this search.
Censys Observed 3 Domain IOCs on IOC IPs
- IOC 1 (api.gupdate[.]net) was observed by Censys in the Forward DNS records of Host C as early as 14APR24 which is outside the activity time frame of July – August 2024 in the Advisory. The domain IOC was also in name fields of certificates on the same host as early as 27MAY24.
- IOC 2 (githubapp[.]net) was observed first by Censys in the Forward DNS records of Host G on 24FEB24 which coincides with the first active timeframe for this host in the Advisory. The IOC is still active on this host and others as of the time of this report.
- IOCs 3 & 4 (login.forticloud[.]online & fortigate.forticloud[.]online) were not observed historically on any hosts nor on any current hosts. However, the words “fortios,” “fortiproxy,” and “fortinet” have appeared on certificates of Hosts D, G and other hosts mentioned in this report that match their patterns.
- IOC 5 (cloud.sophos[.]one) was observed by Censys in the Forward DNS records of Host K on 03OCT23. This corresponds to the first active timeframe for this host as a part of Fox Kitten in the FBI/CISA Advisory of October 2023. IOC 5 is not currently observed on any active hosts.
Censys Observed Domain IOC 2 on Three Current/Active IPs Not Mentioned in the Advisory
A search for IOC 2 on active hosts in Censys Search indicates that IOC 2 is currently in the forward DNS records of Host O as well as in certificates on Hosts M & N, none of which were not mentioned in the Advisory. Host O shares an AS with Hosts D, E, G, and H and Hosts M & N share an AS with Hosts C & J.
Recommendation: Defenders should consider adding these host IPs (M= 64.176.165[.]17; N= 70.34.218[.]77; O = 18.130.251[.]165) to their watchlists or blocklists.”
IOC IP Host Profiles Appear Similar or Identical Beyond the Timeframes Listed in the Report
Censys investigated the profiles of hosts tied to the IP IOCs from the CSA and noticed that some host profiles looked very similar or identical before or after the “First Seen” and “Most Recently Observed Date[s]” identified in the CSA. These observations may indicate previous or unreported attacks/activity.
Host C: First seen JUL24; most recent AUG24. Censys observed an identical host profile of Host C as early as MAY24 which is before the first seen date in the CSA, during which IOC 1 can be seen on the host. Commonalities are depicted below.

Host C: MAY24 (left), JUL24 (right)
Host D: First seen JAN24; most recent AUG24. Censys observed a host profile of Host D in DEC23 similar to Host D’s profile in JAN24, which is one month prior to the first seen date in the CSA. Commonalities, depicted below, include a seemingly random, large number of HTTP ports open, software such as Confluence that match other hosts connected to Host D, as well as seemingly random certificate names that use the same set of keywords.
Host D: First seen JAN24; most recent AUG24. Censys observed a host profile of Host D in DEC24 similar to Host D’s profile in JAN24, which is one month prior to the first seen date in the CSA. Commonalities, depicted below, include a seemingly random, large number of HTTP ports open, software such as Confluence that match other hosts connected to Host D, as well as seemingly random certificate names that use the same set of keywords.

Host D: DEC23 (left), JAN24 (right)
Host I: 1st seen SEP23; most recent JAN24. Censys observed a host profile of Host I in DEC23, identical to Host I’s profile in FEB24, which is one month following the most recent date in the CSA. All details are the same, including the SSH key fingerprints, depicted below.

Host I: DEC23 (left), FEB24 (right)
Censys Observed All Domain IOCs from the Advisory on 64 Currently Valid, Self-Signed Certificates
- IOC 1 (api.gupdate[.]net) = 3 valid certificates, 3 expired certificates; all issuers are Let’s Encrypt except for one active certificate with issuer “unknown” with an expiration date in 2049. This certificate was also the first generated with this domain, in 2018.
- IOC 2 (githubapp[.]net) = 11 valid certificates, 12 expired certificates; all issuers are Let’s Encrypt except for one expired certificate with issuer “unknown” and one active certificate with issuer “unknown” with an expiration date in 2049. Like IOC 1, this certificate was also the first generated with this domain, in 2018.
- IOC 3 (login.forticloud[.]online) = 19 valid certificates, 11 expired certificates; all issuers are Let’s Encrypt. The first certificate for this domain was generated in 2023.
- IOC 4 (fortigate.forticloud[.]online) = 5 valid certificates, 11 expired certificates; all issuers are Let’s Encrypt. The first certificate for this domain was generated in 2023.
- IOC 5 (cloud.sophos[.]com) = 26 valid certificates, 4 expired certificates; all issuers are Let’s Encrypt. The first certificate for this domain was generated in 2023.
Analysis: Defenders should continue monitoring for these IOCs within certificates since some host IP IOCs are still active and there are 64 valid certificates that can be used on these hosts or others.
Conclusion
By studying the profiles of the hosts tied to the IOCs from the CSA over time, Censys uncovered patterns and commonalities amongst those hosts, and then used those patterns and commonalities to identify other, currently active hosts and certificates that may be part of the same Fox Kitten infrastructure. In the future, defenders can leverage IOCs, along with known periods of nefarious activity, to study host and certificate profiles before, during and after reported attacks to identify linkages, patterns, and common indicators. They can then leverage those factors to conduct dynamic searches across public scan datasets like Censys’ to observe how those threats may stand up new infrastructure, leveraging the same techniques as previously observed.
Despite attempts at obfuscation, diversion, and randomness, humans still must instantiate, operate, and decommission digital infrastructure. Those humans, even if they rely upon technology to create randomization, almost always will follow some sort of pattern whether it be similar Autonomous Systems, geolocations, hosting providers, software, port distributions or certificate characteristics. If defenders can pick up on these patterns, much the same way that Soldiers in World War 2 picked up on Morse code operators’ “fists” or communication personalities, they have a chance at staying one step ahead of threat actors.
Methodology
Censys used parsed fields to accurately search for the IOCs, trends, patterns, and other indicators mentioned in the Advisory or found over the course of investigation. Censys used historical profiles of hosts to investigate Censys’ perspective at points in time to corroborate IOCs with timeframes listed in the Advisory as well as observations that seemed to match the profiles of IOC hosts, yet were outside of the timeframe listed in the Advisory, possibly indicating a timeframe of staging or nefarious activity not observed previously.
Censys used a link diagram analysis to identify similarities, patterns, and trends across IOCs, hosts, certificates, Autonomous Systems, and various other parsed fields from Censys’ scan dataset.
[1] https://www.cisa.gov/sites/default/files/2024-08/aa24-241a-iran-based-cyber-actors-enabling-ransomware-attacks-on-us-organizations_0.pdf