GreyNoise Research Finds Censys Scan Data Is Fastest, Most Comprehensive
Cybersecurity firm GreyNoise Intelligence recently published “A Week In the Life of a GreyNoise Censor: A Benign View.” I’m incredibly excited about this blog because anytime an organization outside of yours conducts research that reinforces statements you make on a daily basis, it’s a wonderful thing. There’s even still some additional nuance to be explored, but from their research and amazing visual graphics, there are some key observations to be made. Let’s work our way top to bottom through each visual with some observations:
How long does it take benign scanners to find new nodes?

Image source: GreyNoise
Lots of organizations clocking in at the ~1hr discovery mark. However, there’s a lot of nuance to this. If you’re just scanning the internet for common ports like 80/443 that are open, it’s not that hard – discovery of assets in other tests and IR events I’ve heard of are as little as 7 minutes. You have to look more closely at the work being done to really grasp the context.
How many benign scanner unique IPs connected?
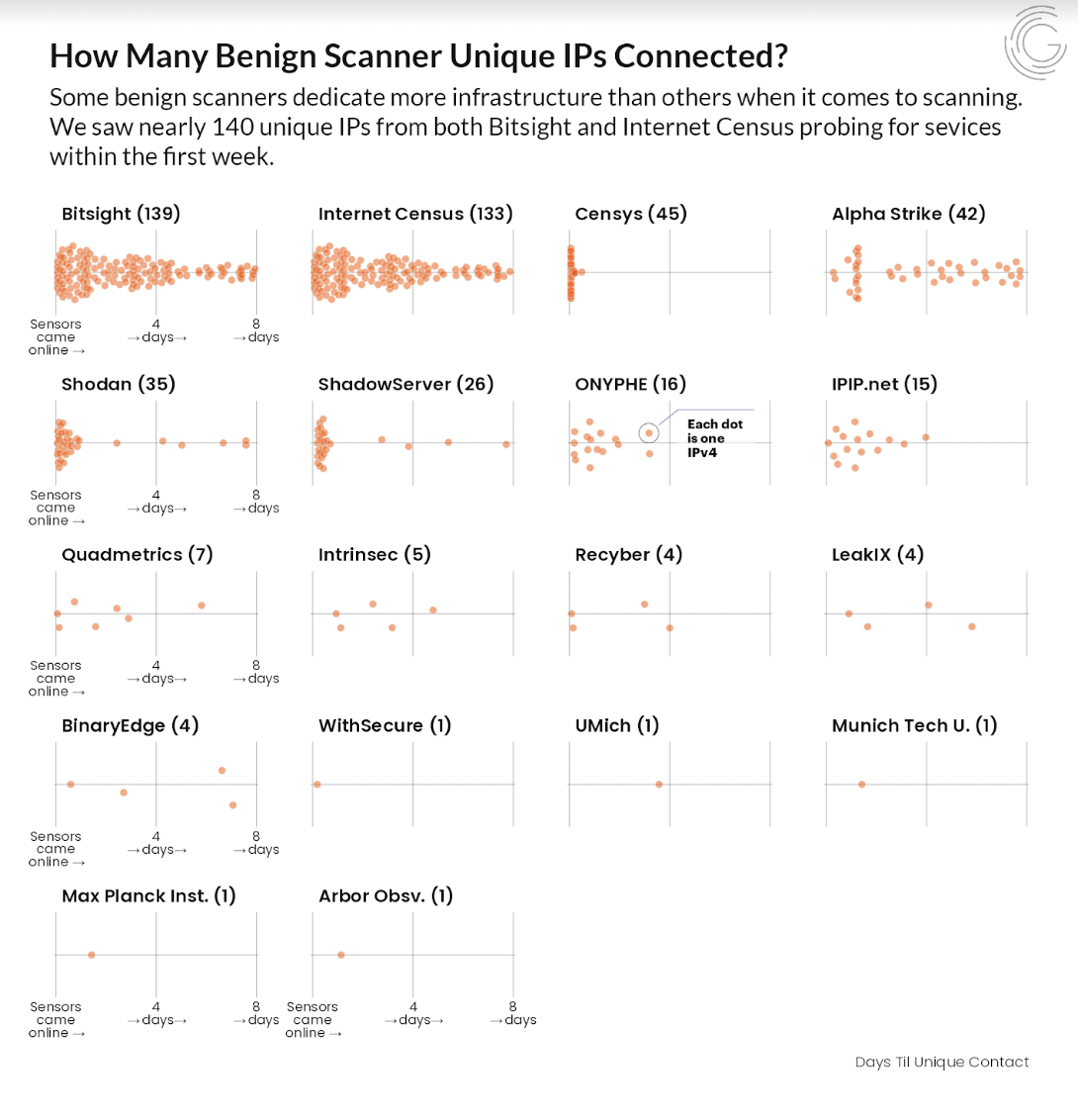
Image source: GreyNoise
The analysis here is the Y-axis of sensors coming online and scanning over an 8 day period. Here we start to see a little more distribution from the previous visual in terms of concentration, but the picture begins to emerge that Censys scanners are doing substantially more work with far fewer resources. For example, BitSight & Internet Census are leveraging right at 3x more hardware (IPs), and 100% of Censys’s hardware scans are concentrated up front. There are some factors that can add more context to this, but it’s an interesting detail nonetheless. Again, taken in context with the horsepower shown later…
How many daily alerts did benign scanners generate?
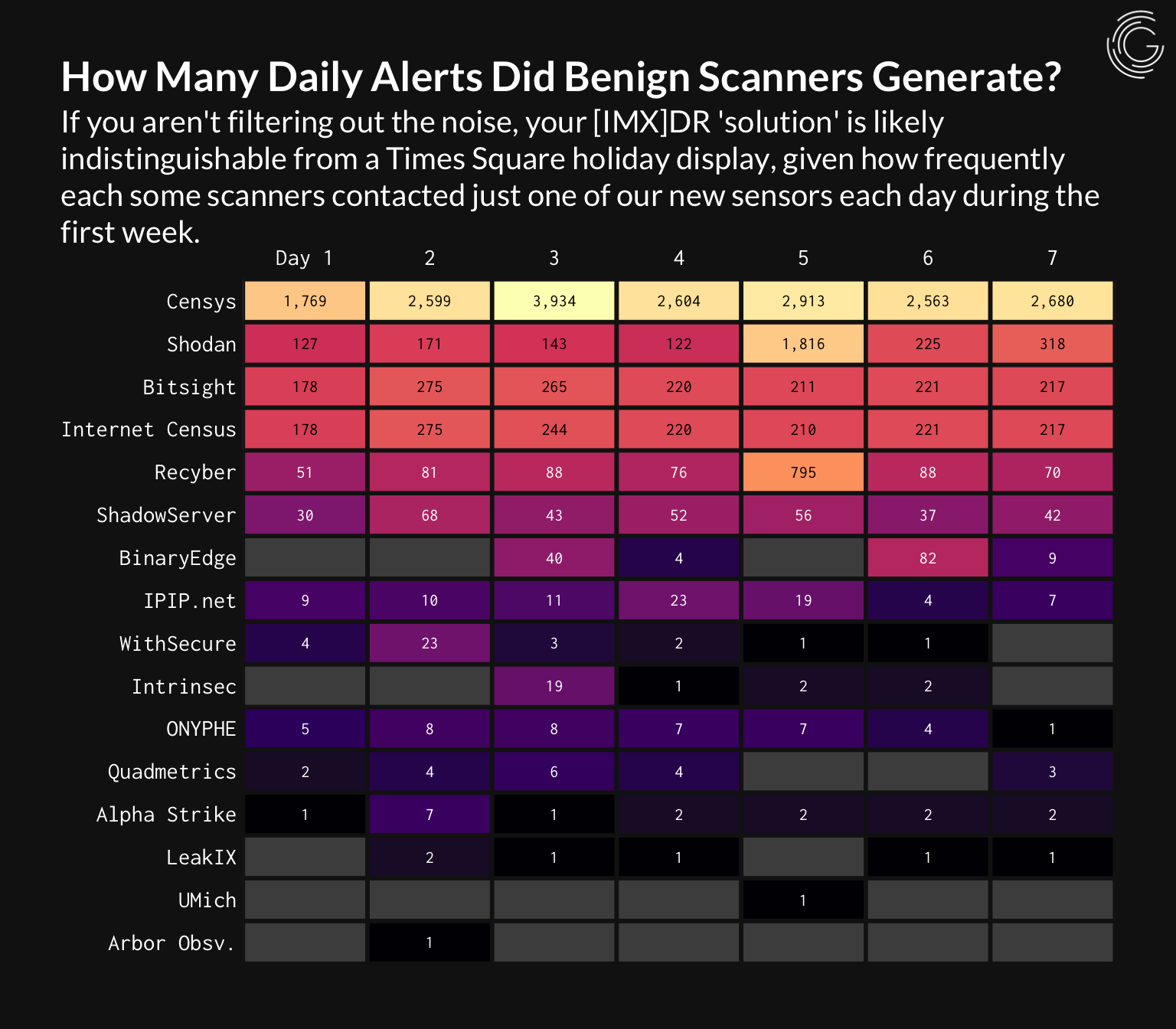
Image source: GreyNoise
Who likes alerts in the security world? No one. Practitioners are truly suffering from constant alert fatigue – enter GreyNoise. This particular heat map is geared towards their direct use case of reducing said alert fatigue, but for our sake serves to illustrate very clearly just how much harder, faster, and with greater consistency the Censys scan is probing the depths of the IPv4 sea.
Which benign scanners have the most diverse volume?

Image source: GreyNoise
This is where it all coalesces to showcase the sheer scale of the work the Censys scanner is doing. This visual is where we start to see the distribution of the specific ports each service is scanning and draw some fairly obvious conclusions. It’s difficult to tell from the Y-axis scale, but it appears to be around 15k ports where the ‘tail’ of the Censys scan data begins to taper off in terms of its density. Left of this, we see that the density of scanning is still much thicker for Censys than the others in the top five, with some variation in terms of scanning density at different levels. We see the profiles for Shodan, BitSight, and Internet Census are basically identical, with ReCyber concentrating their scan efforts around the top ~1,200 ports instead. But – that Censys tail, though, really brings home our conclusions.
Conclusions
Based on the above logic thread, we see a few key trends emerge:
Censys scan data is vastly more comprehensive than anything or one out there on the internet, covering 100% of all 65k ports across the eight day test span, with far greater consistency, i.e. thickness of the tail in the final figure.
Censys does far more with less. This speaks directly to the power of our underlying technology the team has been working so hard on the past few years that is truly second to none.
The final graphic in the GreyNoise article is super interesting to me. It effectively represents the number of scans/attempted connections taking place that are not associated with any known benign scanners out there. Translation: Approximately every 3 minutes unknown and possibly malicious entities on the internet are performing their own scans probing for at best information, at worst opportunities to carry out exploits.
Interested in learning more?
Find more information about Censys Data and Search.



