The Internet offers no shortage of risks – but which might your organization be most vulnerable to? To help answer this question, the Censys Research team sampled more than 2 million hosts as part of our 2022 State of the Internet Report. The team chose two dates six months apart and ran risks observed on each date through the risk engine that powers our Attack Surface Management Platform. What we found might surprise you.
Before we dive into the findings, let’s revisit risk categories and common examples we see within each.
Misconfigurations: Unencrypted services, weak or missing security controls, and self-signed certificates
Exposures: Unintentional database exposures, exposed storage, IoT devices, credentials, API keys
Vulnerabilities: End-of-life or outdated software and CVEs
So, what did we find?
After evaluating data pulled from each of the two observation dates, the Censys Research Team identified the following top 25 risks (displayed in the chart below). Keep in mind that these don’t encompass all of the risks that can be found on the Internet. The data we examined had to meet two criteria: it had to be public-facing (something we could see from passively scanning) and it had to have a signature or risk fingerprint for it to show up in our data. Censys currently tracks for 300 different risk fingerprints.
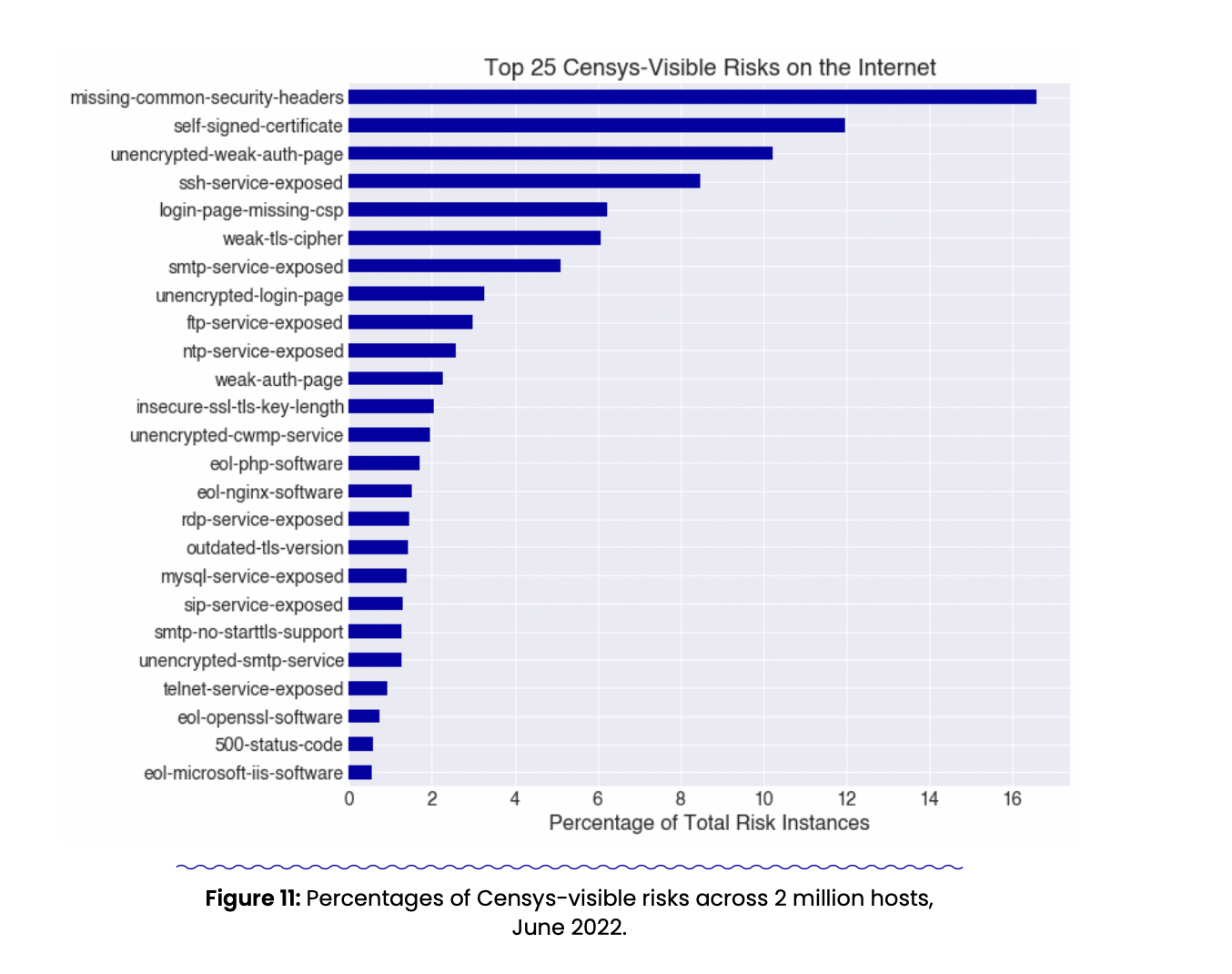
We found that misconfigurations and exposures account for the overwhelming majority of risks observed. In fact, four of the five most common risks are misconfigurations. This is worth underscoring given that misconfigurations and exposures can often be prevented with routine good hygiene. Even though risks like zero days and CVEs get much of the attention, they actually accounted for only 12% of the risks the team observed. In other words: the “boring” risks might be the most likely security weak spots for your organization.
Let’s take a closer look at the five most commonly-observed risks.
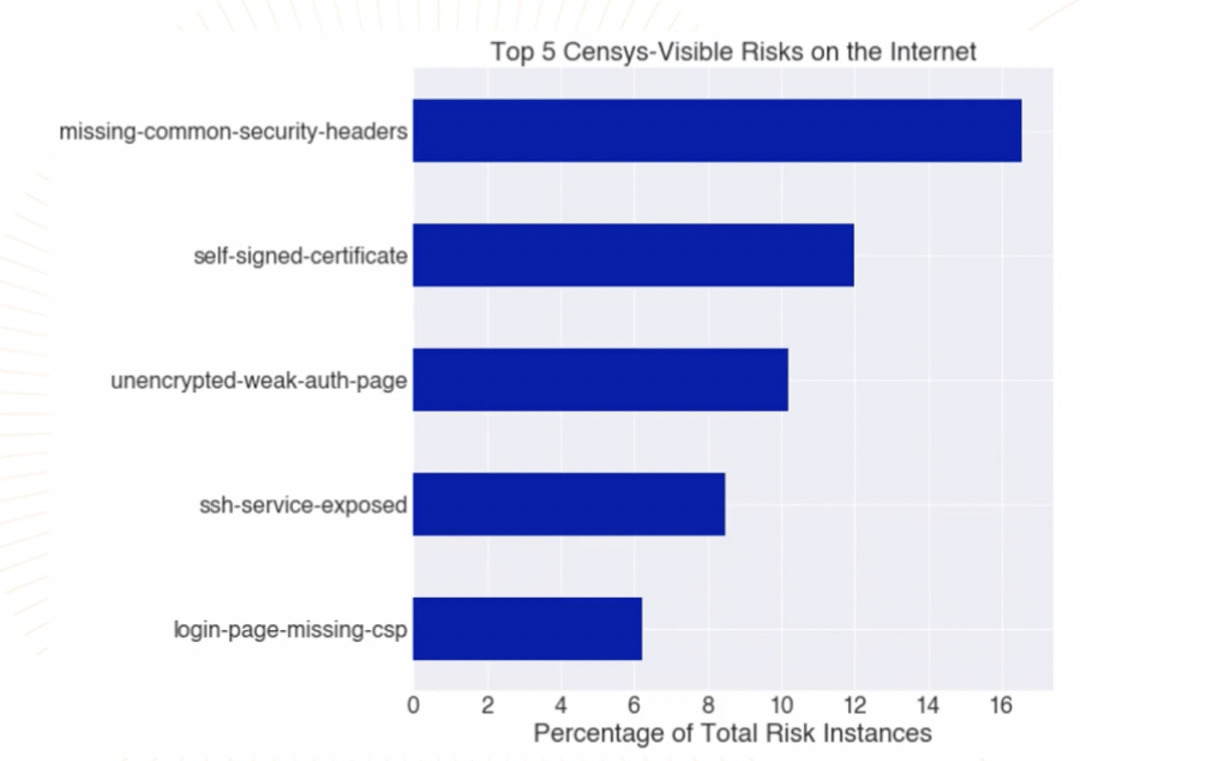
1. Missing security headers comprise 16.4% of total risk instances
Security headers are used to define a set of security precautions for a web browser. Without them your organization can become more of a target for exploitation, through client-side vulnerabilities like cross-site scripting or data injection hacks. Common security headers include Content-Security-Policy (CSP), Cross-Origin Resource Sharing (CORS), and Strict Transport Security (STS). Note that having security headers won’t guarantee that your site is immune from attacks – but they are an important layer of security.
2. Self-signed certificates make up 12% of total risk instances
This refers to an SSL/TLS certificate that was signed by its own private key instead of a trusted Certificate Authority (CA). These trusted certs matter because they provide important identity verification and data encryption; self-signed certificates, on the other hand, are a target for man-in-the-middle attacks and phishing campaigns.
3. Unencrypted weak authentication pages make up 10% of total risk instances
This refers to basic or digest authentication methods, which send credentials in HTTP requests. We see this as a must-address risk. Using basic or digest authentication with TLS leaves credentials vulnerable to theft through man-in-the-middle attacks. While this may not be a new tactic, it’s still a popular one for threat actors.
4. Exposed SSH accounts for 8% of total risk instances
SSH is designed to enable network communication between two devices; when SSH accounts are exposed, they can become the targets of password spraying and credential stuffing attacks.
5. Login pages missing CSP makes up 6% of total risk instances
When content security policies (CSP) are missing on login pages, valuable credential information can be left vulnerable to cross-site scripting attacks. The good news is that CSP is compatible with most major browsers.
For a full breakdown of risks by industry,
download our 2022 State of the Industry Report!
Get the Report