The Neverending Story of Deadbolt
Published on 09.10.2022
Introduction
Deadbolt, a ransomware campaign haunting QNAP NAS customers for the last few months, has seen a consistent number of infections on a fairly regular cadence. But recently, Censys has observed a massive uptick in Deadbolt-infected QNAP devices. The Deadbolt crew is ramping up their operations, and the victim count is growing daily.
* Censys Deadbolt Tracking Dashboard
* Censys Search for Deadbolt Infections
A quick refresher on QNAP Deadbolt ransomware
QNAP is a manufacturer of network-attached storage (NAS) devices. In January of this year, a group calling themselves Deadbolt targeted a series of QNAP NAS devices made for consumers and small businesses that run the QNAP QTS (Linux-based) operating system, infecting the devices with ransomware.
Instead of encrypting the entire device, which effectively takes the device offline (and out of the purview of Censys), the ransomware only targets specific backup directories for encryption and vandalizes the web administration interface with an informational message explaining how to remove the infection.

Due to how this ransomware communicates with the victim, Censys could easily find infected devices exposed on the public internet via this simple search query. Besides broad information about which hosts were infected with Deadbolt, we could also obtain and track every unique bitcoin wallet address used as a ransom since the BTC address used for ransom drops is embedded within the HTML body.
Recent News.
On September 3rd, 2022, QNAP released a new statement that alludes to a newly discovered zero-day vulnerability used to infect hosts with ransomware. This new exploit affects specific QNAP NAS devices running Photo Station when connected to the internet.
QNAP claims that this vulnerability has been fixed, tracked as CVE-2022-27593, and involves the following versions of their QTS operating system:
- QTS 5.0.1: Photo Station 6.1.2 and later
- QTS 5.0.0/4.5.x: Photo Station 6.0.22 and later
- QTS 4.3.6: Photo Station 5.7.18 and later
- QTS 4.3.3: Photo Station 5.4.15 and later
- QTS 4.2.6: Photo Station 5.2.14 and later
Bigger, Better, Faster, More.
Deadbolt infections haven’t ever really stopped, but it’s never been as big as it is now.
The last time we spoke about the QNAP NAS infecting Deadbolt ransomware was in May 2022. At this time, we introduced our Deadbolt dashboard, which the community could use to track the spread of this virulent campaign that infected thousands of QNAP devices on the internet. And if you have been paying attention over the past few months, you may have noticed a constant ebb and flow of infected devices, and it has been a pretty wild and scary thing to watch.
On July 9th, 2022, there were a total of 2,144 Deadbolt infections observed on the internet, but by July 15th, that number had risen to 7,783, an increase of 5,639 infections. By July 27th, that number had dropped to a little over 6,000, but by July 30th, infections shot up again to 9,091.
But the waves of infections over August have nothing on what happened at the beginning of this month. On September 2nd, 2022, we saw the number of unique hosts infected with Deadbolt jump from 7,748 to 13,802, and by September 4th, that number had risen to 19,029!
Deadbolt seems to have a relatively common cadence of new infections. On average, there seem to be seven to twelve days between each campain. Below is a timeline of unique hosts showing signs of Deadbolt for each day between July 27th and September 7th. Highlighted in red are the days where we saw the most upward trends in activity.

| Date | Infection Count | Delta |
| Jun 27, 2022 | 2,459 | |
| Jun 28, 2022 | 2,404 | -55 |
| Jun 29, 2022 | 2,388 | -16 |
| Jun 30, 2022 | 2,381 | -7 |
| Jul 1, 2022 | 2,320 | -61 |
| Jul 2, 2022 | 2,275 | -45 |
| Jul 3, 2022 | 2,234 | -41 |
| Jul 4, 2022 | 2,210 | -24 |
| Jul 5, 2022 | 2,182 | -28 |
| Jul 6, 2022 | 2,165 | -17 |
| Jul 7, 2022 | 2,154 | -11 |
| Jul 8, 2022 | 2,155 | 1 |
| Jul 9, 2022 | 2,144 | -11 |
| Jul 10, 2022 | 3,214 | 1,070 |
| Jul 11, 2022 | 4,716 | 1,502 |
| Jul 12, 2022 | 6,658 | 1,942 |
| Jul 13, 2022 | 7,060 | 402 |
| Jul 14, 2022 | 7,406 | 346 |
| Jul 15, 2022 | 7,783 | 377 |
| Jul 16, 2022 | 7,679 | -104 |
| Jul 17, 2022 | 7,584 | -95 |
| Jul 18, 2022 | 7,388 | -196 |
| Jul 19, 2022 | 7,093 | -295 |
| Jul 20, 2022 | 6,877 | -216 |
| Jul 21, 2022 | 6,546 | -331 |
| Jul 22, 2022 | 6,445 | -101 |
| Jul 23, 2022 | 6,371 | -74 |
| Jul 24, 2022 | 6,205 | -166 |
| Jul 25, 2022 | 6,121 | -84 |
| Jul 26, 2022 | 6,011 | -110 |
| Jul 27, 2022 | 6,117 | 106 |
| Jul 28, 2022 | 7,666 | 1,549 |
| Jul 29, 2022 | 8,946 | 1,280 |
| Jul 30, 2022 | 9,091 | 145 |
| Jul 31, 2022 | 8,800 | -291 |
| Aug 1, 2022 | 8,560 | -240 |
| Aug 2, 2022 | 8,366 | -194 |
| Aug 3, 2022 | 8,020 | -346 |
| Aug 4, 2022 | 7,954 | -66 |
| Aug 5, 2022 | 7,900 | -54 |
| Aug 6, 2022 | 8,171 | 271 |
| Aug 7, 2022 | 8,282 | 111 |
| Aug 8, 2022 | 8,395 | 113 |
| Aug 9, 2022 | 8,330 | -65 |
| Aug 10, 2022 | 8,835 | 505 |
| Aug 11, 2022 | 9,118 | 283 |
| Aug 12, 2022 | 8,919 | -199 |
| Aug 13, 2022 | 8,600 | -319 |
| Aug 14, 2022 | 8,578 | -22 |
| Aug 15, 2022 | 8,542 | -36 |
| Aug 16, 2022 | 8,467 | -75 |
| Aug 17, 2022 | 8,371 | -96 |
| Aug 18, 2022 | 8,177 | -194 |
| Aug 19, 2022 | 8,647 | 470 |
| Aug 20, 2022 | 8,713 | 66 |
| Aug 21, 2022 | 8,688 | -25 |
| Aug 22, 2022 | 8,875 | 187 |
| Aug 23, 2022 | 8,753 | -122 |
| Aug 24, 2022 | 8,535 | -218 |
| Aug 25, 2022 | 8,390 | -145 |
| Aug 26, 2022 | 8,310 | -80 |
| Aug 27, 2022 | 8,193 | -117 |
| Aug 28, 2022 | 7,948 | -245 |
| Aug 29, 2022 | 7,950 | 2 |
| Aug 30, 2022 | 7,822 | -126 |
| Aug 31, 2022 | 7,826 | 4 |
| Sep 1, 2022 | 7,748 | -78 |
| Sep 2, 2022 | 13,802 | 6,054 |
| Sep 3, 2022 | 18,725 | 4,923 |
| Sep 4, 2022 | 19,029 | 304 |
| Sep 5, 2022 | 17,813 | -1,216 |
| Sep 6, 2022 | 16,597 | -1,216 |
| Sep 7, 2022 | 15,097 | -1,500 |
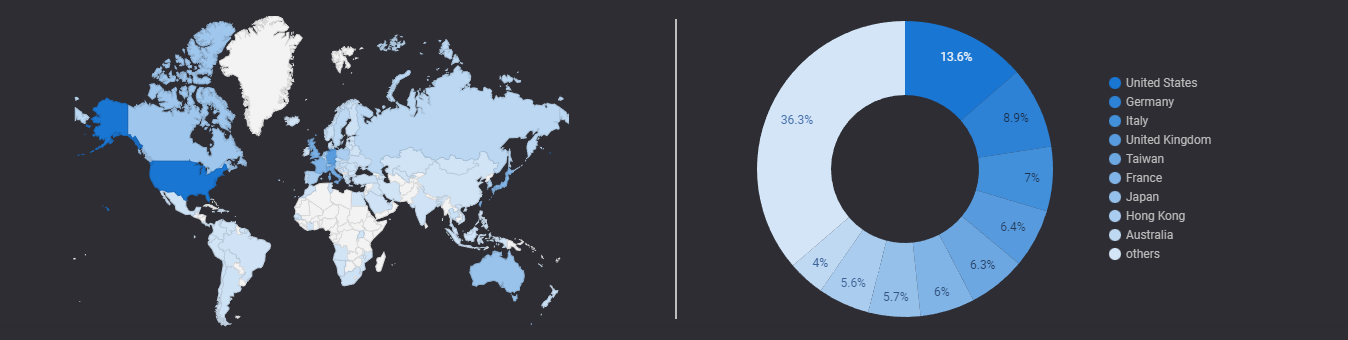
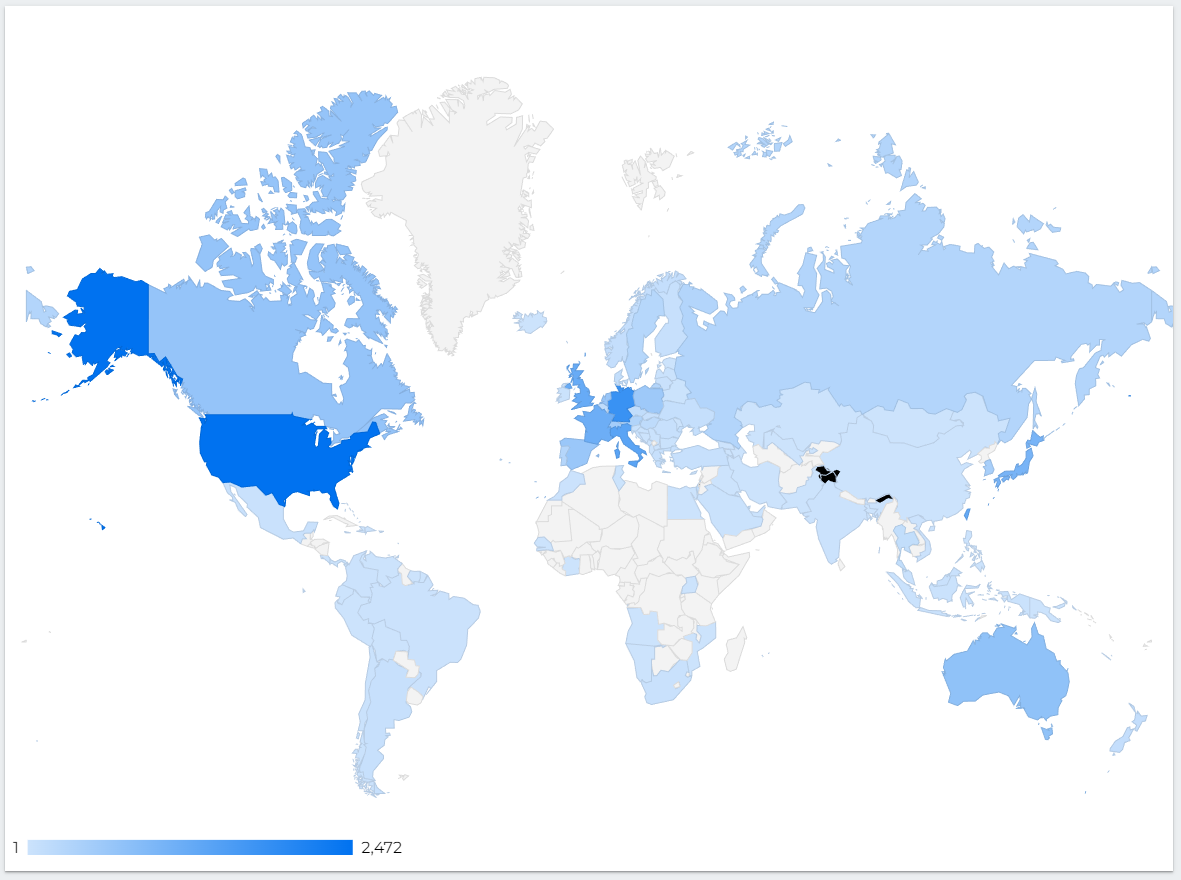
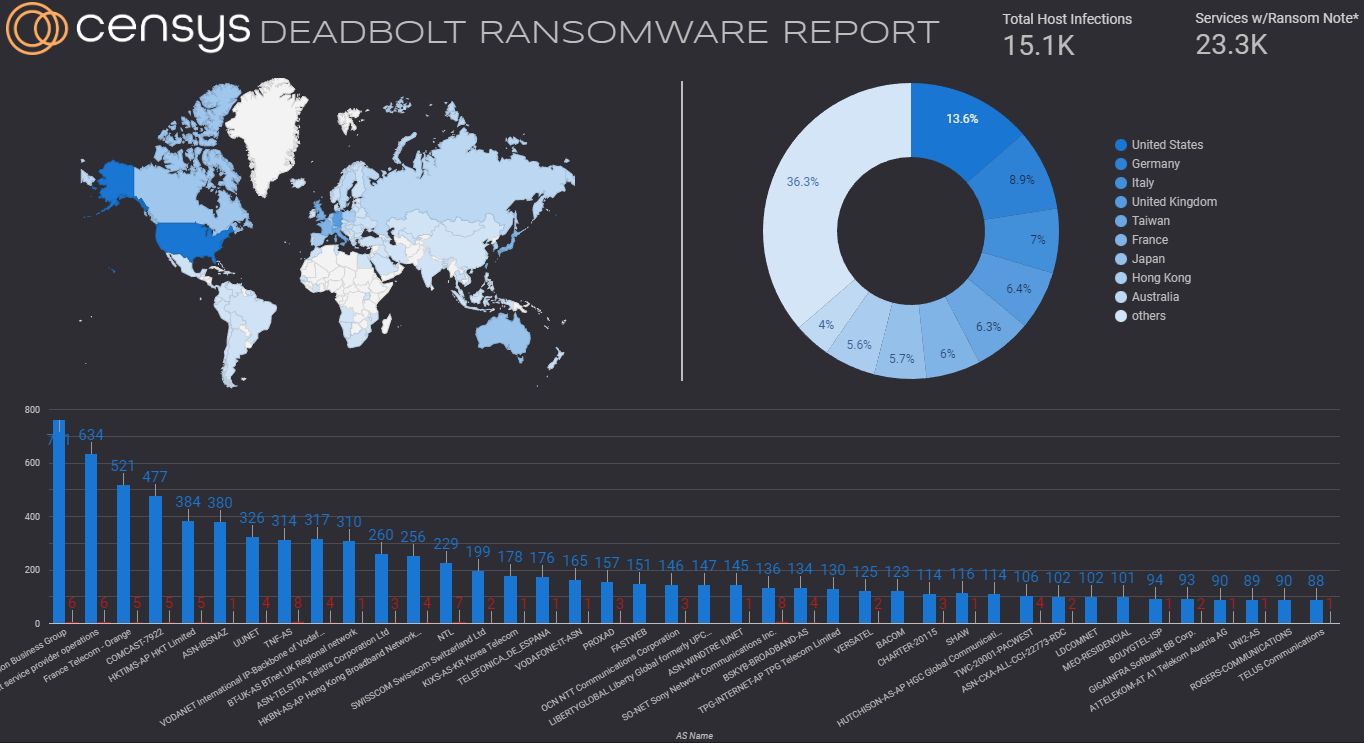
At its height, on September 4th, 2022, the majority of infections were found in the United States, with 2,472 distinct hosts showing signs of Deadbolt, Germany number two with 1,778, and Italy with 1,383. Below is a map displaying the infected hosts from this date.
Below are the top ten countries and autonomous systems with the most Deadbolt infections.
| Country | Deadbolt Infected Hosts |
| United States | 2,472 |
| Germany | 1,778 |
| Italy | 1,383 |
| Taiwan | 1,244 |
| United Kingdom | 1,229 |
| France | 1,155 |
| Hong Kong | 1,074 |
| Japan | 1,024 |
| Australia | 724 |
| Canada | 669 |
| Autonomous System Name | Autonomous System Number | Infected Host Count |
| HINET Data Communication Business Group | 3462 | 1,008 |
| DTAG Internet service provider operations | 3320 | 865 |
| France Telecom – Orange | 3215 | 643 |
| COMCAST-7922 | 7922 | 532 |
| HKTIMS-AP HKT Limited | 4760 | 502 |
| ASN-IBSNAZ | 3269 | 480 |
| VODANET International IP-Backbone of Vodafone | 3209 | 432 |
| UUNET | 701 | 401 |
| TNF-AS | 33915 | 384 |
| BT-UK-AS BTnet UK Regional network | 2856 | 371 |
Tracking Deadbolt
The official Censys Deadbolt Dashboard can be found here.
Our rapid-response team has put together an interactive dashboard for tracking Deadbolt infections across the globe. There are currently three individual tabs with different views of the data we have collected over the past few months.
First, our front page includes the total infected host and service count, along with breakdowns by region and autonomous system.
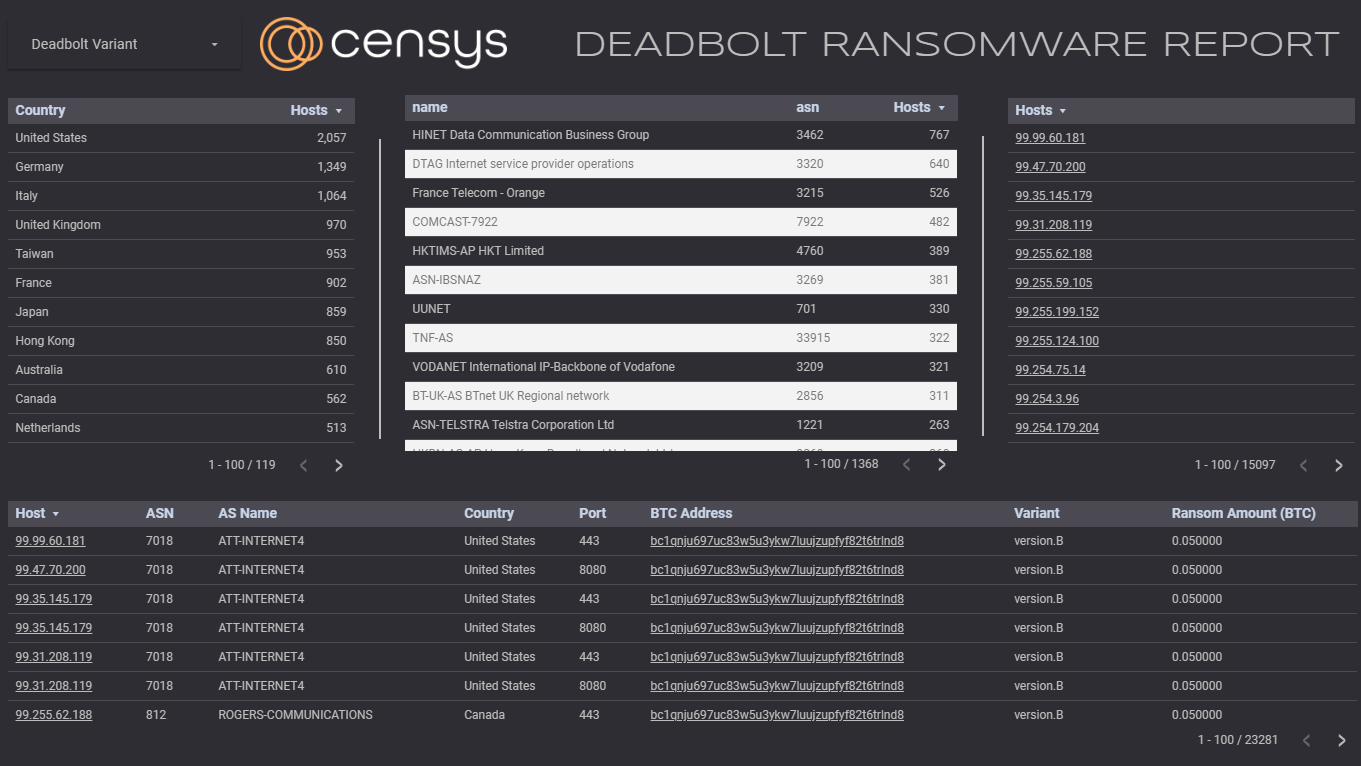
The second set of data is an interactive, configurable detailed breakdown of each infection, including the IP, autonomous system, country, network port, the BTC address used for paying the ransom, and the variant of Deadbolt (we have found two distinct variants). Finally, we display the amount of ransom requested from the victims. These fields are filterable by simply clicking on any part of the dashboard.
Finally, we have a seven-day view of Deadbolt on the internet, including graphs that break infections down by country. Researchers can use the dropdown menus to filter the countries they are most interested in analyzing.

We’ll continue to monitor NAS devices infected with Deadbolt ransomware. In the meantime, you can start exploring the Censys Deadbolt Ransomware Report below.