Summary of Events so Far
| October 12, 2022 |
Censys observes two hosts with a similar (but different) ransom note as the current campaigns. |
| January 31, 2023 |
The attackers update the same two October 2022 hosts with a ransom note similar to the current campaign on port 443. |
| February 2, 2023 |
Censys observes thousands of hosts compromised with this ransomware. |
| February 8, 2023 |
Attackers change their encryption methods and ransom notes on every compromised host. |
| February 11, 2023 |
Censys observed a burst of new compromised hosts. |
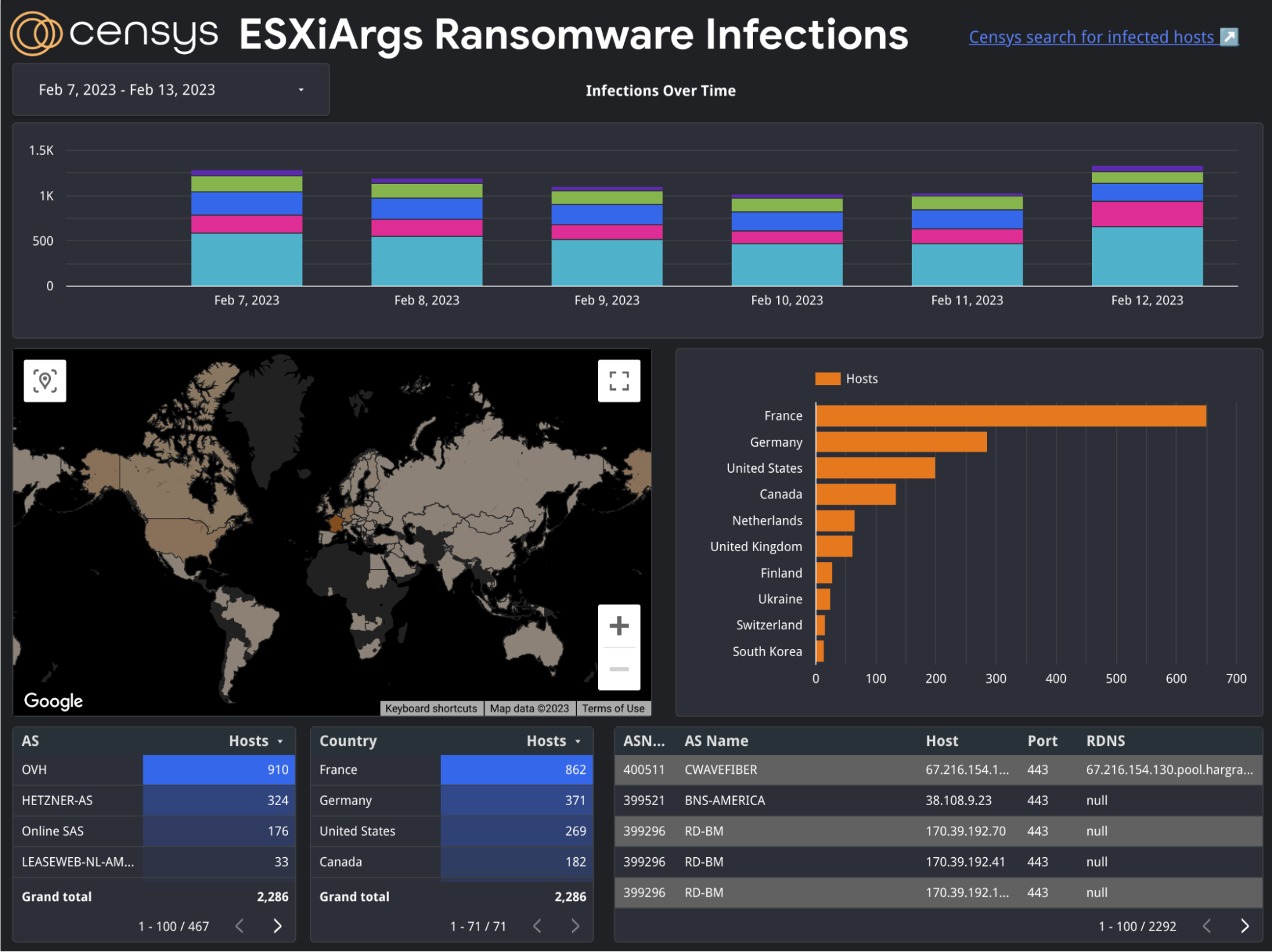
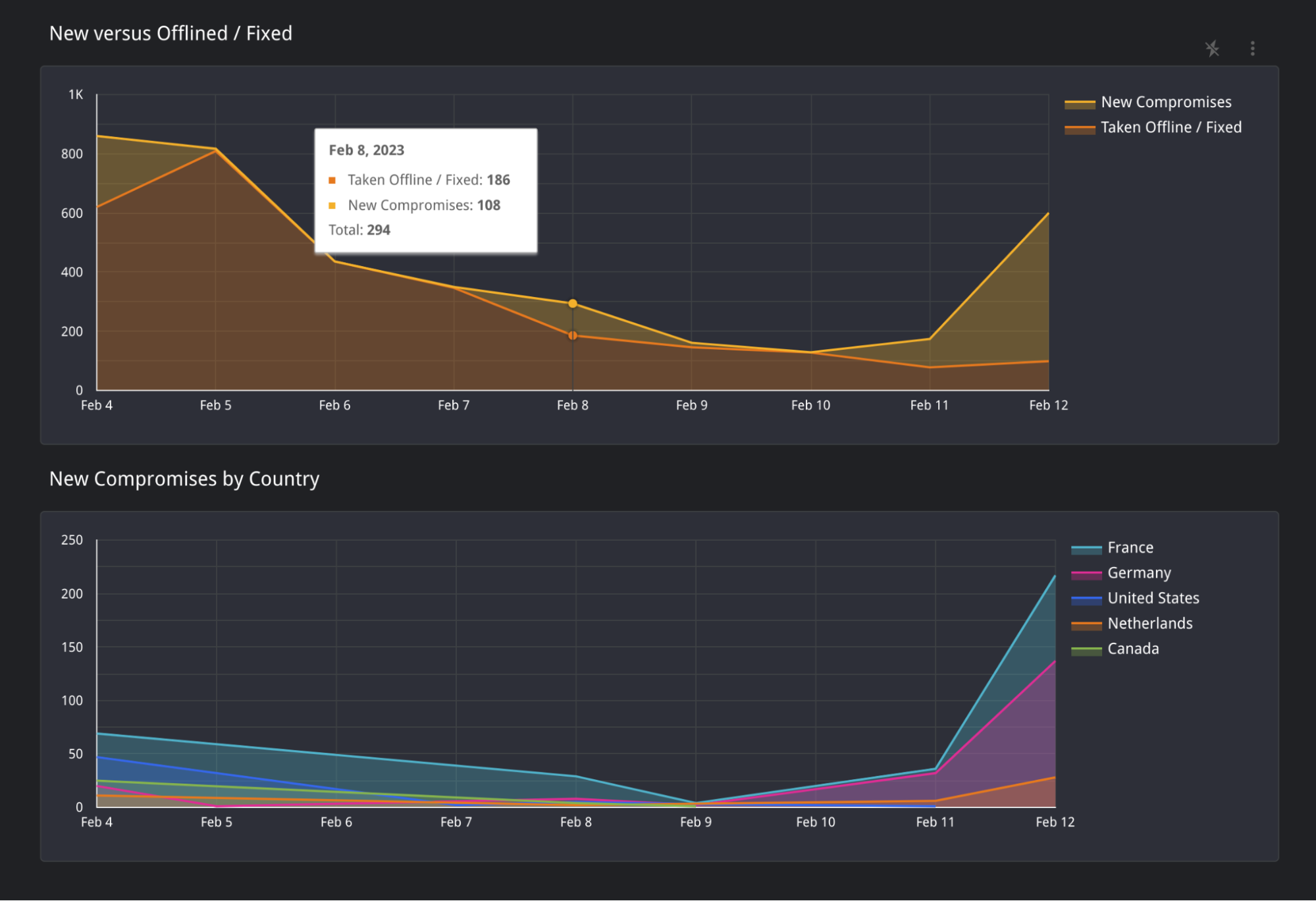
Over the last few days, Censys has observed just over 500 newly infected hosts. This sudden surge of attacks is particularly interesting because most of these newly infected hosts are isolated to the country of France, Germany, the Netherlands, and the United Kingdom. For more details about all other countries, please visit our ESXiArgs Dashboard (discussed further down) and use the location filter in the “Changes over Time” tab.
Top 5 New Compromises (February 11th through February 12th)
| Country |
New Infections |
| France |
217 |
| Germany |
137 |
| Netherlands |
28 |
| United Kingdom |
23 |
| Ukraine |
19 |
A Look at Potential Early Victims
On February 3, 2023, a ransomware campaign with the initial ESXiArgs variant began making headlines. As we examined historical trends around this campaign, we searched back to January 31, 2023, for hosts with signs of this ransomware. Prior to widely ramping up a campaign, threat actors often “test” their methods on a select few hosts, so we were hoping to understand more about the earlier stages of these attacks.
Two hosts appeared to have a ransom note on port 443 on January 31, 2023. Both are hosted on OVH; one appears to be running ESXi and the other a VMWare service we can’t further identify. We can’t discern which version of ESXi these hosts may be running, but we’ll note that Versions 6.5 and 6.7 reached end-of-life in October 2022.
Analysis of each of these hosts reveals the presence of a ransom note on port 443 going back to October 12, 2022 (Host-A) and October 14, 2022 (Host-B).
The October note is nearly identical to the version observed with the first significant wave of attacks that began on February 3. Still, there are a few key differences between the October note and subsequent ones:
- Instead of a TOX_ID, the victim is directed to an onion URL to access their decryption key upon payment
- Lower payment–the price in USD has roughly doubled since the October notes
- A proton[.]me email address is included at the bottom of the ransom note
Each variant of the ransom notes from October 2022 through February 2023 are strikingly similar in wording to the note of an earlier ransomware variant, Cheerscrypt, which gained notoriety in early 2022. While they may share a similar ransom note, researchers have determined that they have different encryption methods–meaning they are likely associated with different groups.
We have not found evidence that Cheerscrypt ransom notes were internet-facing, but rather stored on the filesystem of the compromised machine. If that’s indeed the case, then Host-A and Host-B are likely precursors to the current campaign.
Below we examine different ransom notes found on Host-A. Links to Host-B updates can be found at the end of this section.
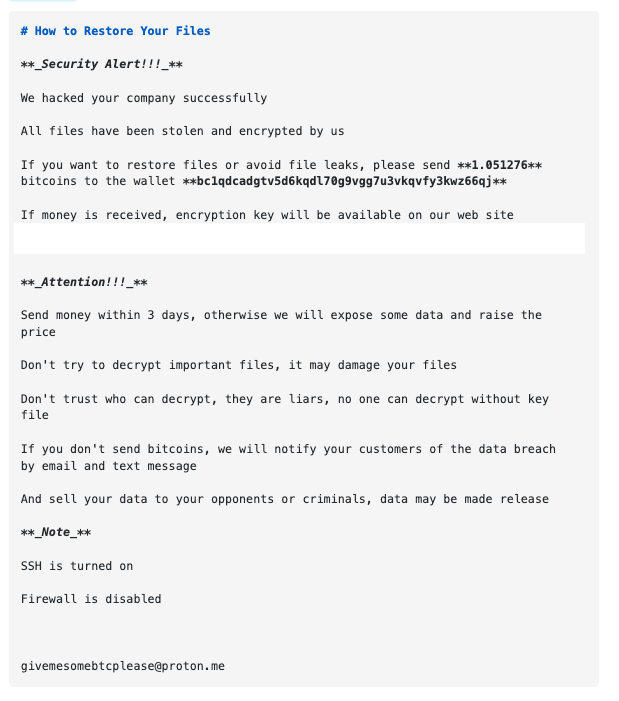
Above: The ransom note on Host-A first appeared in Censys data on October 12, 2022 (requires enterprise Censys account to view; archived raw JSON data for this host can be found here).
On February 4, 2023, the actors altered the ransom note on Host-A to reflect the note associated with the first significant wave of this campaign that began on February 3:

Above: Ransom note on Host-A, February 4, 2023 (requires enterprise Censys account to view; archived JSON can be found here).
On February 8, 2023, the day CISA released their decryptor and recovery guidance document, the ransom note on Host-A was updated to remove the BTC address.

Ransom note on Host-A, February 8, 2023 (requires enterprise Censys account to view; archived JSON can be found here).
Host-B Updates (Censys links require an enterprise Censys account, raw JSON dumps do not).
As of February 13, 2023, the ransom note no longer appears on Host B.
Dashboard
To help the community keep an eye out on this ongoing attack, Censys has constructed a dashboard to aid in tracking ESXiArgs ransomware across the globe. A few things to note about the data in this dashboard:
- Data in this dashboard does not include named hosts (virtual hosts or hosts behind proxies that require a name-based request) – there may be slight differences from what is found in search.censys.io with “virtual-hosts” enabled.
- Data is aggregated once every twenty-four hours at midnight.
Readers can click almost every field within this dashboard to filter down into its particular type. For example, if you click on the country of “United States”, only data will be shown for the United States (and all stats are adjusted accordingly).
The first page (below) includes a summary of the last week’s worth of data broken down by the top five countries (by default). The date range for this can be configured using the calendar control at the top. The rest of the data in this tab is an aggregate of all of the hosts seen within the configured timespan.
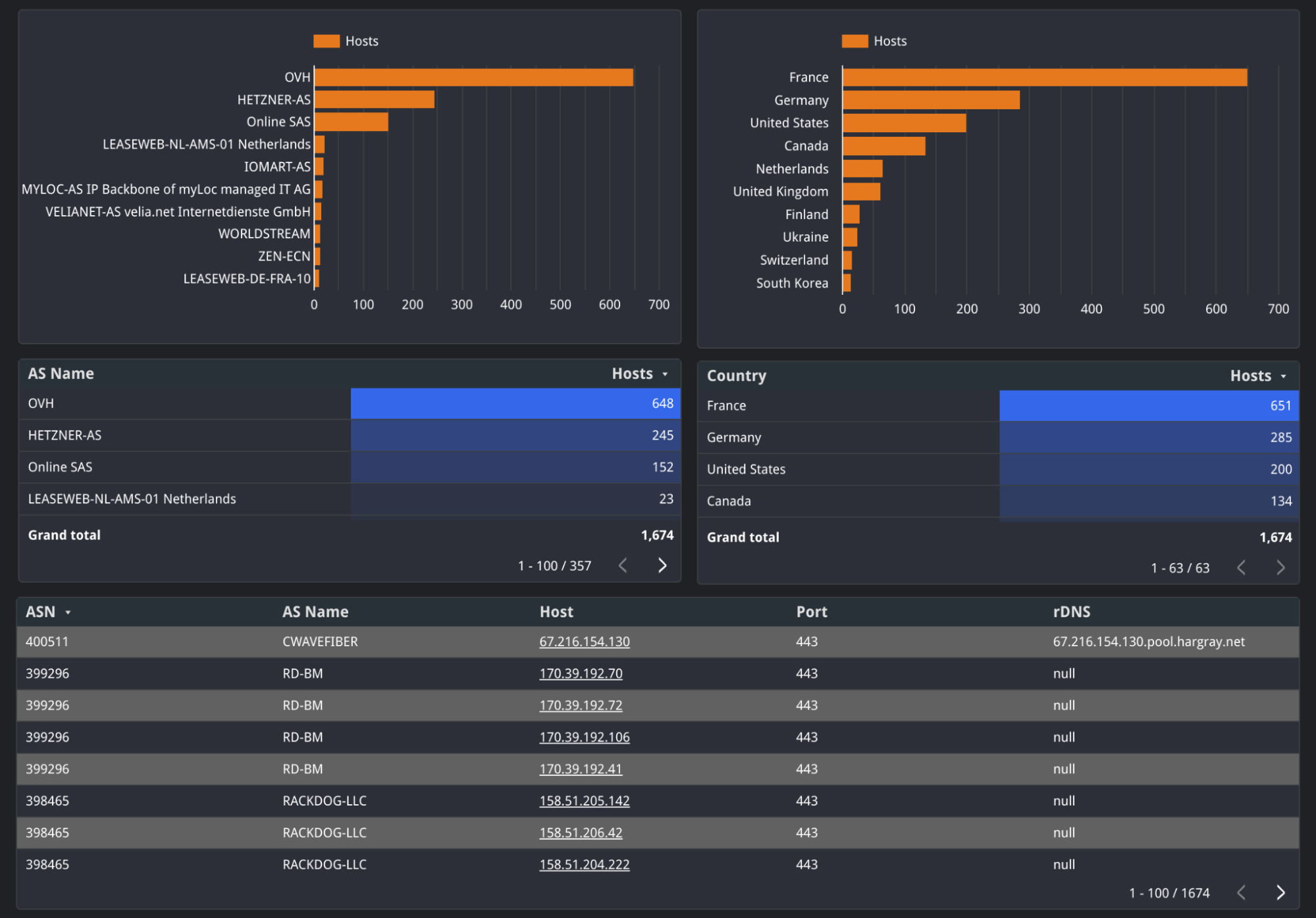
The second page (below) is a detailed view of the most recent snapshot of data, including an exhaustive list of hosts that have been compromised, which includes the autonomous system, ports, and any associated reverse DNS. Clicking on an IP address will take you to the Censys search entry for that host. As with other data in this dashboard, clicking on different fields will filter the data.
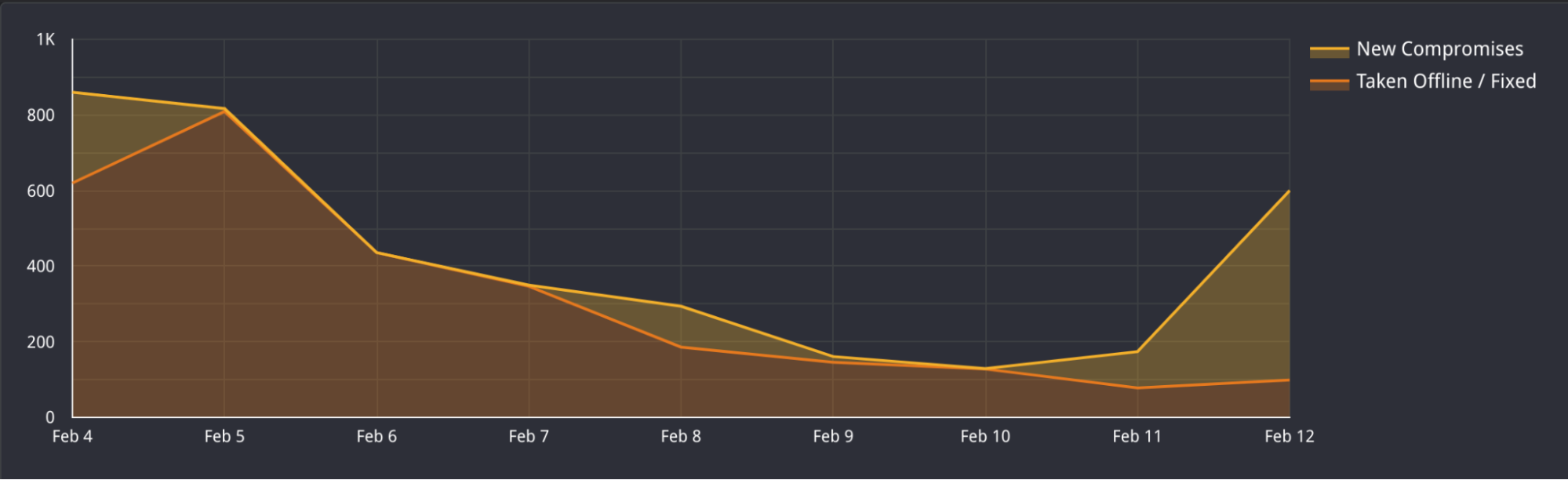
The third and final page is a simple visualization of changes we have observed over time. You will find two areas in the top graph: “New Compromises” and “Taken Offline / Fixed”.
- “New Compromises” is a visual representation of the number of new hosts seen with the ESiArgs Ransomware note that was not seen on the previous date.
- “Taken Offline / Fixed” Represents hosts that were online on the previous date but are no longer found with the ransom note or have been taken offline completely.
You can find the Censys ESXiArgs Ransomware Dashboard Here.