Open directories have long been targeted by threat actors looking to access and expose sensitive data. Open directories refer to HTTP hosts with directories enabled, which means all the files and directories in a specific directory are listed when you access the index page.
If a directory is made publicly available, anyone can find it by conducting a search for web servers with HTML titles containing phrases like “index of” or “directory listing for” and manually sift through the results.
If your organization maintains open directories, you probably either have a legitimate use case for maintaining them (like repositories on scientific papers or archived software), or their existence is accidental and you’ll want to address.
Open Directories for Threat Actor Infrastructure
However, threat actor interest in open directories goes beyond data exposure. Threat actors will also leverage open directories to launch and facilitate attacks.
Open directories enable bad actors to conveniently house and distribute the infrastructure needed for nefarious activity. For example, they can easily store and deliver malware files and supporting software from open directories. C2 servers are also commonly found on hosts with open directories.
In their article, “A Beginner’s Guide to Hunting Malicious Open Directories,” Embee Research provides examples of malicious open directories discovered using Censys Search. The ability to see these malicious open directories can be incredibly useful to blue teams investigating threat actor infrastructure.
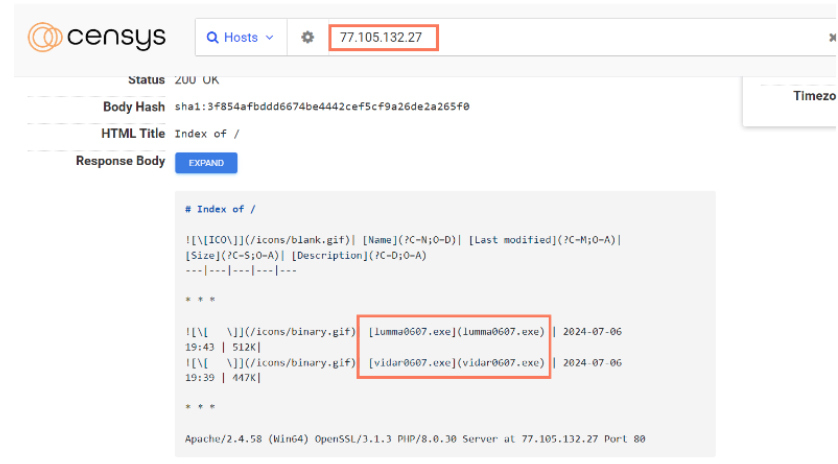
Open directory hosting both Vidar and Lumma malware
Accelerate Your Investigations with “Suspicious-Open-Dir”
Identifying and investigating these open directories using Censys Search has become even more efficient with our new suspicious-open-dir label. Users can now narrow their search for open directories to only those that Censys suspects are being used for nefarious purposes. Simply submit “labels: suspicious-open-dir” in the query search bar or add the label to an existing query string. This means that any open directories without suspicious file names will be excluded from your returned results.
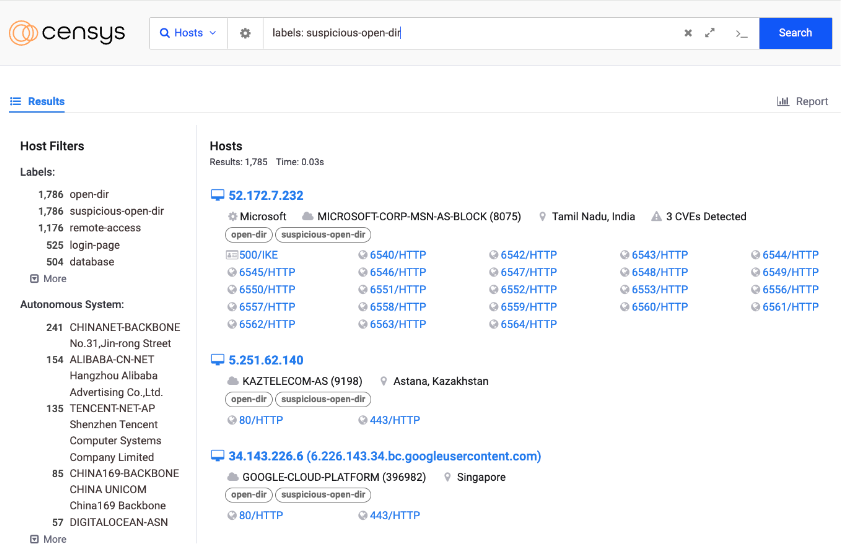
Censys Search results page for “labels: suspicious-open-dir”
In quantifiable terms, the suspicious-open-dir label brings 400,000+ open directory results in Censys Search down to about 1,700 (at the time of writing). Note that Censys Search users interested in all open directory results, both legitimate and suspicious, can still apply our broader “open-dir” label to a query.
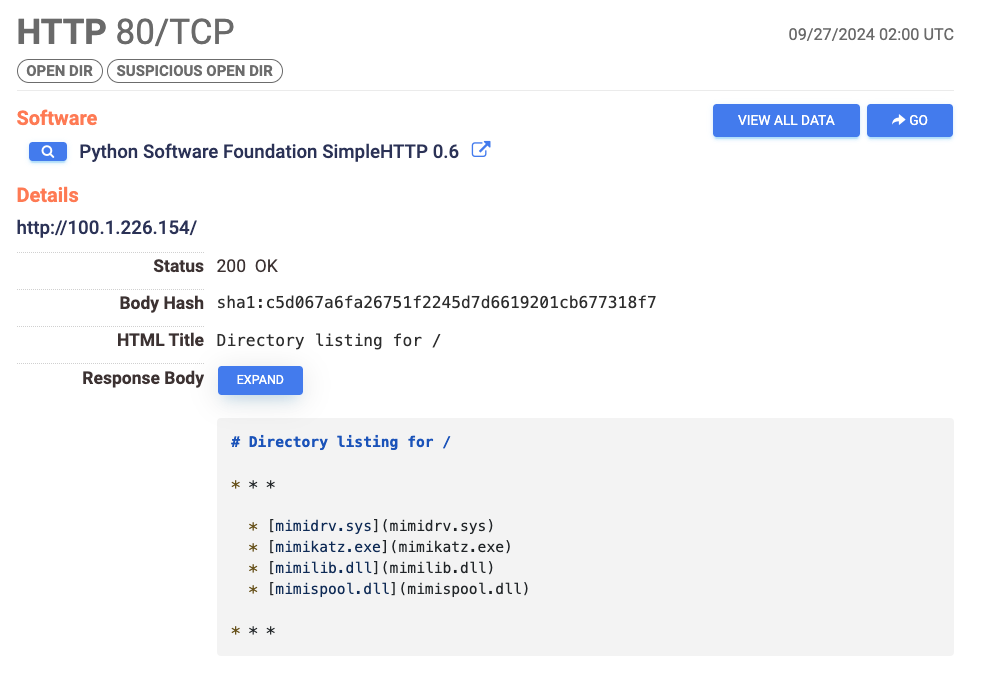
Example of suspicious open directory found with Censys Search
Share Your Findings
Censys Search users are already digging into numerous suspicious open directories using the suspicious-open-dir label, including those used for phishing setups, DDOS tools, and PowerExploit exfiltration modules.
Is the suspicious-open-dir label helping your security or research efforts? Let us know! Tag us on X or Mastodon with your findings, or post in the Censys Community Forum to connect directly with other engaged Censys users.
You can learn more about Censys’ view of open directories in our research report, “Dorking the Internet: Unlocking Secrets in Open Directories,” and find tips for investigating open directories in Embee Research’s guest blog, “A Beginner’s Guide to Hunting Malicious Open Directories.”