The list of organizations who have come forward as victims of a GoAnywhere breach has grown long: Community Health Systems, Hatch Bank, Hitachi Energy, Rubrik, the City of Toronto, Procter & Gamble, Saks Fifth Avenue, and Crown Resorts.
update 2023-03-17
Hitachi Energy has become the 3rd organization to report a data breach in its GoAnywhere file systems carried out by the Clop ransomware gang.
update 2023-03-02
Hatch Bank, a digital fintech banking platform, has become the 2nd major organization to come forward to report that just under 140,000 customer’s names and SSNs were stolen by threat actors who exploited this vulnerability in its systems. Clop’s claim that they are responsible for these attacks remains unverified. You can now track the status of this vulnerability with our interactive dashboard.
UPDATE 2023-02-21
The notorious Clop ransomware gang claimed that they exploited the GoAnywhere MFT vulnerability to gain unauthorized access to the data of 130 organizations. While this claim remains unconfirmed, Huntress Threat Intelligence linked recent GoAnywhere MFT incidents to a threat group that has deployed Clop ransomware in the past. In a recent SEC filing Community Health Systems, one of the largest healthcare providers in the U.S., reported a data breach in their GoAnywhere MFT instances impacting up to 1 million patients. This vulnerability continues to be actively exploited — if your organization is a GoAnywhere MFT customer, patch your software as soon as possible.
TL;DR
- An actively exploited pre-auth RCE vulnerability in GoAnywhere Managed File Transfer software was disclosed that could lead to sensitive data exposure
- As of February 13, 2023, Censys found 330 distinct hosts running exposed GoAnywhere administrative consoles, with 267 of these having indicators of being vulnerable
- Patch your GoAnywhere MFT instances as soon as possible and secure them with proper access controls
Introduction
On February 1, 2023, a company named Fortra (the developer behind the infamous Cobalt Strike penetration testing tool) announced that they had discovered a pre-authentication vulnerability in their “GoAnywhere MFT” (Managed File Transfer) product. Tracked as CVE-2023-0669, an attacker can leverage this to inject code resulting in potential remote code execution (RCE). Fortra has since released an emergency patch in version 7.1.2.
In their statement, Fortra mentions that an attacker only needs access to the web-based administrative console to exploit the service and that “in most cases [the administration console] is accessible only from within a private company network, through VPN, or by allow-listed IP addresses”, but in reality, nothing is preventing a person from configuring the service with a public IP. This vulnerability doesn’t affect the web client interface of the service. A proof of concept of the exploit has been published.
Censys Findings
As of February 13, 2023, Censys has observed 330 unique hosts with active GoAnywhere MFT admin panels exposed to the public internet. The software documentation states that the default administration ports are 8000 for standard HTTP, and 8001 for HTTPS. Censys observed 257 (~78%) of the internet-exposed services run on these default ports.
Top 10 Countries with Exposed Admin Consoles

Top 10 Autonomous Systems

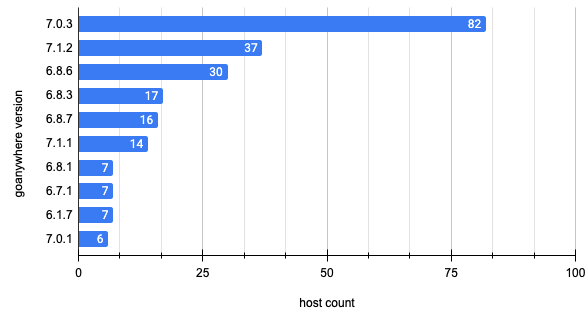
Top Software Versions
Some of the GoAnywhere instances that Censys observed offer information about their specific version numbers via their HTML title. We were able to obtain version numbers from 304 hosts by inspecting this field. Of these, Censys found that 267 appear to be running vulnerable versions of GoAnywhere while 37 indicate having the patched version 7.1.2.
In addition to applying the patch it’s good practice to avoid exposing your GoAnywhere instances to the internet.
Mitigation Recommendations
- Patch your software: upgrade all of your installations to GoAnywhere MFT version 7.1.2. Here’s how to check what version of GoAnywhere is running on your machine: https://forum.goanywhere.com/gateway-version-license-check-1376
- Follow the mitigations suggested in Fortra’s security advisory, including reviewing your admin user accounts, disabling the vulnerable code, and ensuring your admin console is not exposed to the public internet.
- To read the full security advisory on Fortra’s customer portal you need a free account, although Security reporter Brian Krebs has pasted its contents in a public Mastodon post: https://infosec.exchange/@briankrebs/109795710941843934.
Further Reading: