Summary
Censys has found evidence of a network of botnet management systems running a modified version of Nosviak, a little-known command-and-control service that has gained traction over the past few months. Many of this network’s systems share resources such as SSH keys, domains, and service branding, which alludes to a more extensive operation around selling denial-of-service attacks and proxy services to willing customers.
Introduction
Nosviak is a botnet command-and-control (C2) system that supports various callback communication protocols, including those used by Mirai and Qbot. Despite its capabilities, it has yet to be the subject of much research or scrutiny compared to other systems in this domain. However, over the past seven months, there has been an increase in hosts tagged as Nosviak in ThreatFox, a platform dedicated to sharing indicators of compromise (IOCs) associated with malware. Yet, still, we could not find anything more detailed than a label on a community-driven website.
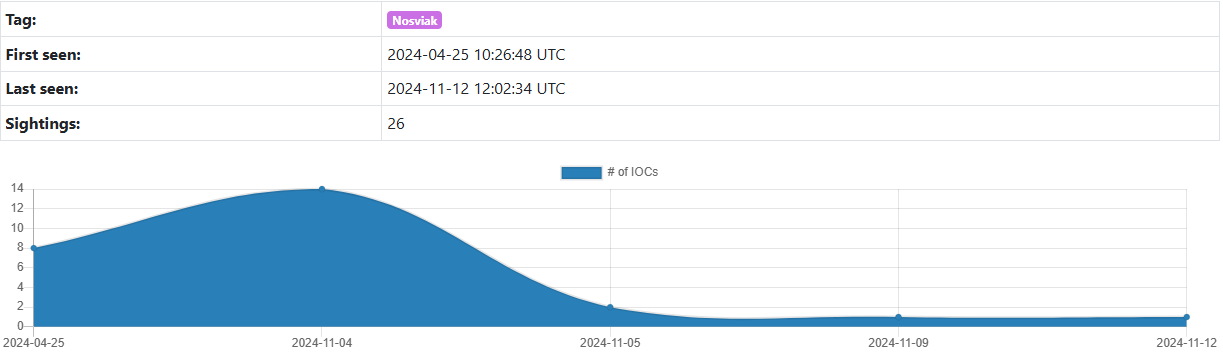
ThreatFox entry for Nosviak
After developing a Nosviak fingerprint for Censys, we set out to uncover more information about this software. At the time, information on Nosviak was scarce, scattered across obscure corners of the internet. What we did find, however, was a fragmented trail of clandestine GitHub repositories, some littered with insults and cryptic taunts, while others surprisingly contained the complete Nosviak2 source code alongside custom branding and configuration files.
We then focused on the hosts already flagged in Censys running Nosviak2. Through various pivoting strategies, we began identifying patterns and characteristics that provided some insight into a specific ecosystem built around the Nosviak2 software. What started as a simple analysis of Nosviak soon unraveled into a broader discovery of a small network of interconnected hosts that managed a Nosviak-derived “DDoS-as-a-Service” operation.
“Stress-Testing” as a Service
Censys uncovered a botnet frontend operating under multiple aliases and storefronts, primarily offering DDoS and proxy services disguised as “stress testing” tools. These storefronts often share identical HTML templates, differentiated only by unique branding, names, and pricing structures. Our analysis reveals a strong reliance on the Nosviak C2 server, with many of these services using its branding API to apply distinct themes while potentially operating on shared infrastructure.
At the time of writing, the network consisted of over 150 hosts spanning twenty countries and autonomous systems, serving in the control, operation, and sale of these DDoS and proxy services. Some hosts may also function as operational relay boxes (ORBs). Despite operating under different names, many of these entities maintain direct or semi-direct connections.
Key examples of these storefronts include Moonrise c2, Rotate C2, Monolith C2, Runtz C2, and the Cindy Network. While these services flaunt distinct names, their websites follow a near-identical template – the only meaningful variations lie in the superficial elements like branding and wording.
The promotional language on these storefronts often includes slogans like “Feel the true power” or “Test your website security,” which consistently appear across all these websites. Below are some examples of this:
While we cannot definitively confirm that these servers are running Nosviak without direct access to the physical machines, several key indicators support this conclusion. In the following sections, we will reference the Nosviak2 source code, which we have mirrored here.
Banners and Branding
In the Nosviak2 source code (core/clients/produce.go), the default SSH server banner is initialized with the format string:
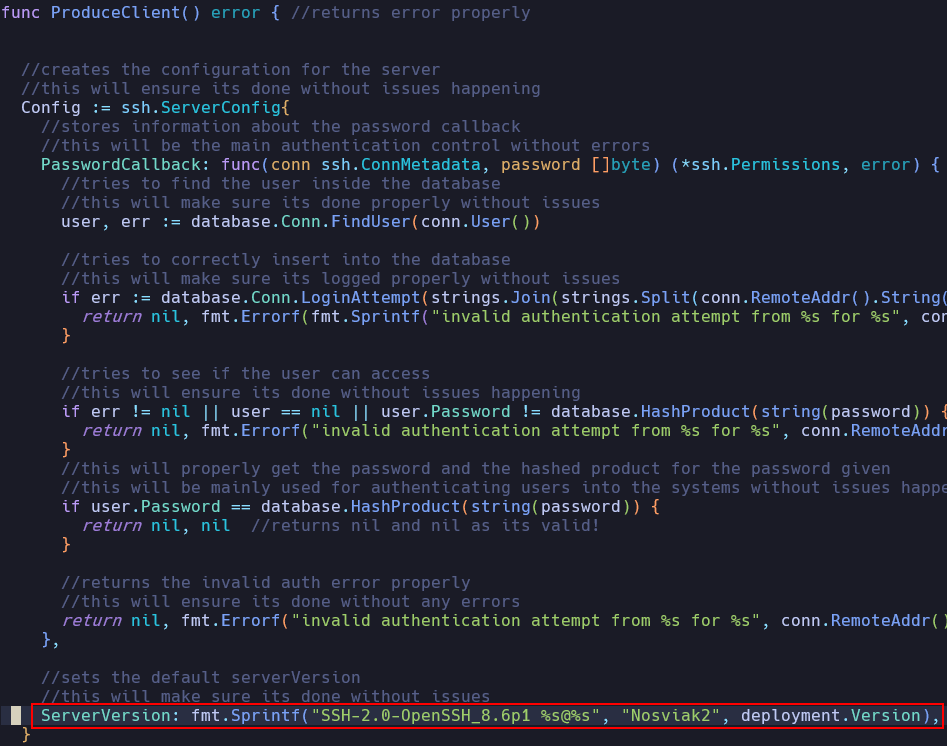
Many of the servers identified in this investigation followed this exact versioning scheme. In some instances, the Nosviak string was replaced with a more customized identifier, or the name was stripped out entirely, but the OpenSSH version (8.6p1) remained consistent across these cases.
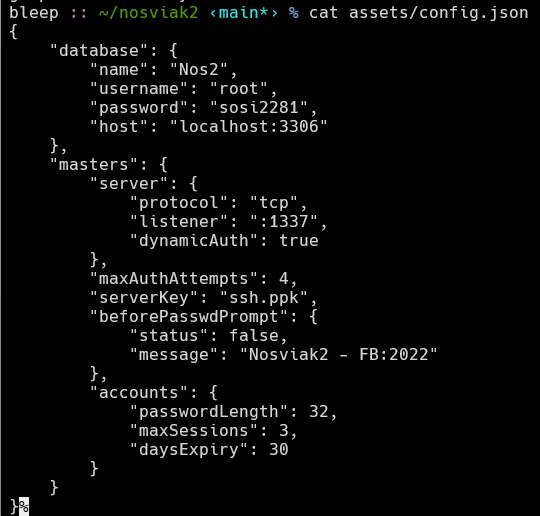
We also note that the default configuration for Nosviak binds SSH to port 1337 as seen here in assets/config.json, and many of the services we identified were actively listening on this port as well.
assets/ $ head -n 4 ssh.ppk
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAzJ56X727XpePjcheS/x0TBwzFpcFuIIyhPzifeMN67yCTKS3KH/D
assets/ $ puttygen ssh.ppk -O private-openssh -o /dev/stdout | \
ssh-keygen -y -f /dev/stdin | \
awk '{print $2}' | base64 -d | \
sha256sum | awk '{print $1}'
1d977c87558d8968e8a485a2f766594cd8de5f3e0e0f437eb23d091682a8823a
Below is a table of the hosts and ports where this SSH key was observed. While some hosts used the default Nosviak banner, others had modified it to include custom branding.
Despite operating under different names and aliases, many of these DDoS “services” share striking similarities. These include (other) shared SSH server keys, nearly identical web pages, and reused favicons.
These services heavily rely on Discord, Telegram, or both as their primary communication platforms. These channels act as central hubs for promoting their offerings, providing user support and updates, and showcasing “proofs” of their activities. Operators frequently share screenshots of successful attacks to demonstrate their capabilities and attract new customers.
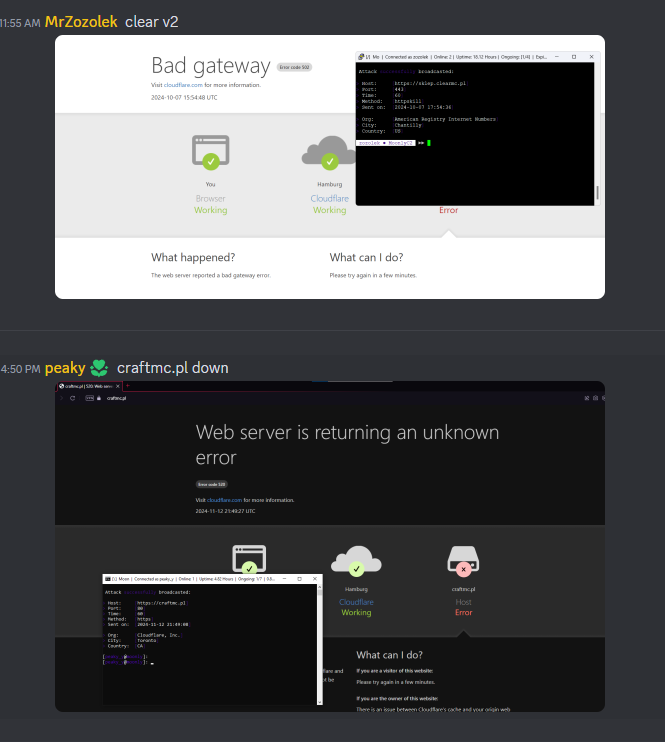 |
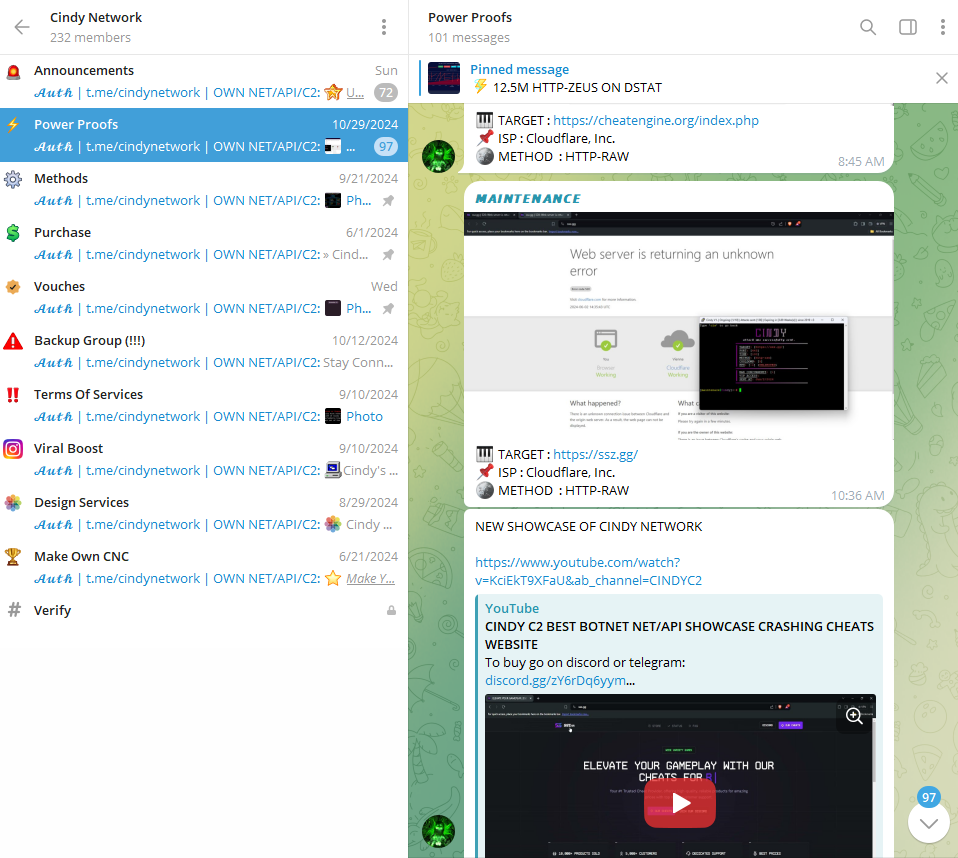 |
| MoonlyC2 Discord (discord[.]gg/moonlyc2) “proofs” |
Cindy Network Telegram (t[.]me/cindynetwork) “proofs”. |
Pivoting from the Nosviak SSH Fingerprint
By pivoting from the default Nosviak SSH key, we can find links to other hosts that share some commonality with different hosts. For example, while Sentinel Network, Moonly C2, RCNC, and Cindy Network use the default Nosviak SSH key, they also run web servers that include HTML elements found on several other hosts offering similar services. We can then use those elements as a jumping-off point to find other potentially related infrastructure.
Many of these hosts led us to uncover even more infrastructure; for example, Elite Proxy’s web server at IP address 185.17.0.31 was identified using the same Runtz SSH key. This server hosted four distinct SSH services on ports 22, 1337, 8080, and 9090. The SSH service on port 9090 used a different SSH key shared with five additional hosts. Among these hosts, two were running Nosviak login panels.
Another host that was discovered using the Runtz SSH fingerprint was Dream C2 at 37.114.63.131 that operated a secondary SSH server on TCP port 9999 with a fingerprint (d281…69b6) shared with 18 additional hosts, a subset of which was branded as “Erf CNC”.
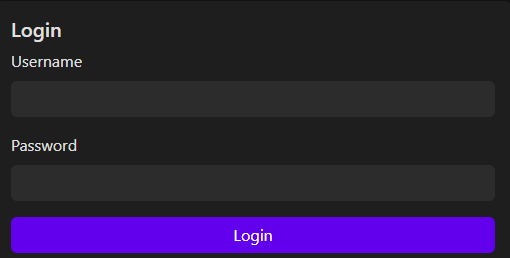
ErfCNC Login Panel
Tracer C2 is linked to other services, such as 93.123.85.191 (WaterNetworkk / 2af0…14cc), which ran a status page on port 80 listing the types of attacks it supports.

For instance, 103.211.201.207 (with an HTML title of “SSN Funnel Build” (possibly related to Nosviak’s “Funnel” feature)) and 167.114.4.98 (“SSN API Build”) both host HTTP servers on port 80 that appear to be API build status pages specific to the botnet.
The same GitLab favicon is also present on several standalone hosts: 160.30.21.74 features a status page on port 80 with the HTML title “Tajima C2/API”, while 212.193.31.66 identifies itself as the “CRIMINALITY API”.
This suggests that admins are automating the provisioning of new API servers using GitLab as a CI/CD, allowing them to iterate faster on new releases.
Along with the various domain names that we’ve already discussed, several others were found to be associated with this network:
nordnetface[.]sbs
rotate-c2[.]fr
noltranspstrer[.]cfd
noltranspstrer[.]top
akarui[.]fyi
tcppegasus[.]xyz
freeddos[.]fun
zopz-api[.]com
novac2[.]fun
homicide-api[.]lol
primeapi[.]lol
cybersecurity-solution[.]net
hydroapi[.]xyz
trainingdevsecops[.]com
doner-api[.]ru
kymev[.]com
nekofish[.]cc
overdose[.]sbs
cindynetwork[.]xyz
zytlink[.]top
kailulu[.]fun
aetherc2[.]com
kodachi[.]xyz
wintermc[.]fun
filexland[.]fun
hurtproxy[.]online
cardiacapi[.]xyz
sparkestops[.]cfd
aetherapi[.]com
sparkunsr[.]top
moonlyc2[.]xyz
stressermarket[.]xyz
proxypro[.]io
At the time of writing, the majority of this infrastructure is hosted on OVH (AS16276) and Aeza (AS216246), all geographically spread across Germany, the Netherlands, the United States, Russia, and other regions where such operations can seemingly go unnoticed or without enforcement.
The reality is that many of these services appear deceptively innocent, often reflecting a network of individuals—possibly younger enthusiasts—applying their technical skills and interests in ways that could lead to harmful outcomes. While the primary target audience seems to be those aiming to disrupt game servers and chat servers, this does not rule out the potential for these networks to be abused for far more malicious purposes.
We have developed a single Censys search query consolidating all the indicators discussed in this post. At the time of writing, the query identifies over 155 hosts.
Below is a table that breaks down each element in the search query into the specific thing it is looking for.
| Description |
Fingerprint |
Censys |
| The SSH fingerprint for the default Nosviak server. |
1d977c87558d8968e8a485a2f766594cd8de5f3e0e0f437eb23d091682a8823a |
Search |
| The SSH fingerprint that was found on Runtz C2 which is shared across over 90 other hosts. |
2af0ec35b4f2039e850d50b4cb613ebb025512a1524226accddce9cb63d014cc |
Search |
| The SSH fingerprint for the Rotate C2 hosts. |
f38b96889a770641f3e64d831a1229b9d553bfe7747a677a567e2a299738955b |
Search |
| SSH fingerprint was found on a Dream C2 host shared with 19 other hosts. |
d281264986ed864f0891bc1edc7c40d07a8695d36ac9e30d2f76e8a85aa569b6 |
Search |
| SSH fingerprint found on an Elite Proxy host that is shared with several other hosts. |
2d361a7de23e20f38cf353395b3a35e468b170da984adfdff855a0a9b9896c70 |
Search |
| SSH fingerprints of unknown origin found running alongside an SSH server with the default Nosviak SSH server key. |
| c7cd4b5c81522a6bb519b7f6e60286a005fd5e1340656728803b9748f7dd6a0b |
| 077fba6a621d64761b246c36fa5832cf6ec4400a12e78434c3243d3f48353a80 |
|
Search |
| The HTTP body hash of an SSN C2 build status page. |
sha1:e9371aca7b792814d55df07b56a9aafd25ee3b89 |
Search |
| Moonly C2 API Management server. |
sha1:c1a12dd0ac8283f60349f8800e5ac889d495b4cf |
Search |
| Status pages which may be used to determine what hosts are currently up or down within the network. |
| sha1:7894a2cf11597ca5b3dcd8516294d2b06528d3fa |
| sha1:8b1ebc6832852a06ab02097af10c4984b557a957 |
| sha1:3e2561532be10aa91242c3867f3257f6a005b1b8 |
|
Search |
| Admin panels for Erf CNC |
sha1:63060ac2fb64f9045b054bbdd8d73d4f6905b4f3 |
Search |
| API management server for Erf CNC |
sha1:911936199d078877a5ccd93537471044251806ca |
Search |
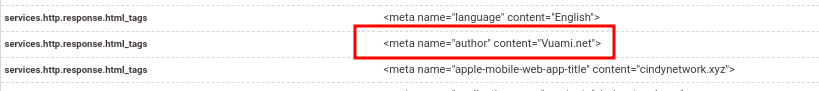
| Shared HTML elements found on several advertised services such as Moonrise C2, Rotate C2, Monolith C2, Runtz C2, and the Cindy Network |
| assets/647538aa3b2ddd2dc925b188_logoorb.webp |
| <meta name=\”author\” content=\”Vuami.net\”> |
|
Search |
| The rarely used GitLab favicon that was found on many “build status” pages found throughout this research. |
06d4abc973616ca572b82ac4c7a2078b |
Search |
| Various HTML titles that were discovered. |
| Login – Nosviak4 |
| SSN Funnel Build |
| SSN API Build |
| Herios – Feel The True Charms of DDoS |
| CRIMINALITY API |
| Cardiac API Online |
|
Search |
| The hash of a certificate that was found running on “Nosviak4” dashboards. |
dc51f51e8094f7a19089a1b8776fdbddb89a6bbd612858c490ed0a7239958a5d |
Search |
| Various modified SSH banners which have been seen with Nosviak installed that indicate that specific networks owner. |
| CindyCNC |
| MoonlyC2 |
| Sentinel V2 |
| RCNC |
| Nosviak2 |
| SSN CNC |
|
Search |