Update, June 26, 2024
As of 7:15 PM ET on June 25, Progress has updated the CVSS score for CVE-2024-5806 in MOVEit Transfer from 7.4 to 9.1, changing the severity from High to Critical.
Their advisory now includes reporting on additional “newly identified” vulnerabilities in a third-party component used by MOVEit Transfer. The original patch for CVE-2024-5806 does not mitigate these issues, and Progress urges customers to:
- Block inbound RDP access to MOVEit Transfer
- Limit outbound access to only trusted servers
Executive Summary
- On June 25, 2024, Progress Software announced two authentication bypass CVEs affecting the SFTP module in their MOVEit Transfer and Gateway products
- At time of publication, Censys observed 2,700 MOVEit Transfer instances online, primarily in the US
- When compared to MOVEit Transfer exposure numbers from 2023, the numbers are remarkably similar, as are the geographies and networks where MOVEit Transfer is observed
- Censys has published a dashboard to help track MOVEit Transfer exposures over time
Introduction
On June 25, 2024, Progress Software announced two CVEs affecting the SFTP module in their MOVEit Transfer and Gateway products:
- CVE-2024-5806, CVSS 7.4 (High), Auth Bypass in MOVEit Transfer
- Affects MOVEit Transfer versions from 2023.0.0 before 2023.0.11, from 2023.1.0 before 2023.1.6, from 2024.0.0 before 2024.0.2
- CVE-2024-5805, CVSS 9.1 (Critical), Auth Bypass in MOVEit Gateway
- Affects MOVEit Gateway version 2024.0.0
MOVEit Transfer is a popular managed file transfer (MFT) solution, designed to facilitate file transfer between and within organizations. In May and June 2023, MOVEit Transfer faced multiple critical vulnerabilities that were mass-exploited by the Clop ransomware and extortion gang to steal data from hundreds of organizations. Disclosures from affected organizations–both first- and third-party users of MOVEit–continued throughout much of 2023.
MOVEit Gateway is a proxy service designed to facilitate safer deployments of MOVEit Transfer. MOVEit Gateway can be deployed in the DMZ (demilitarized zone) of a network to allow MOVEit Transfer to reside in the local network, rather than being exposed on the public Internet.
Researchers at watchTowr Labs released a detailed analysis of the authentication bypass vulnerability in MOVEit Transfer. They explain how this particular vulnerability arises not from a simple SQL injection (as we saw last year with CVE-2023-34362 in MOVEit Transfer), but rather the interplay between MOVEit, the IPWorks SSH library used by MOVEit, and issues with error handling.
Below we focus specifically on the scope of exposure of MOVEit Transfer.
The Censys Perspective
We examined the exposure of MOVEit Transfer around this time last year, and few things have changed. As of June 25, 2024, Censys observed 2,700 instances of MOVEit Transfer online. This is relatively close to the 2,600 exposures we observed in early June 2023.
The majority of the exposed MOVEit instances we observed are in the US, with additional exposures observed in the UK, Germany, the Netherlands, and Canada, among other countries. 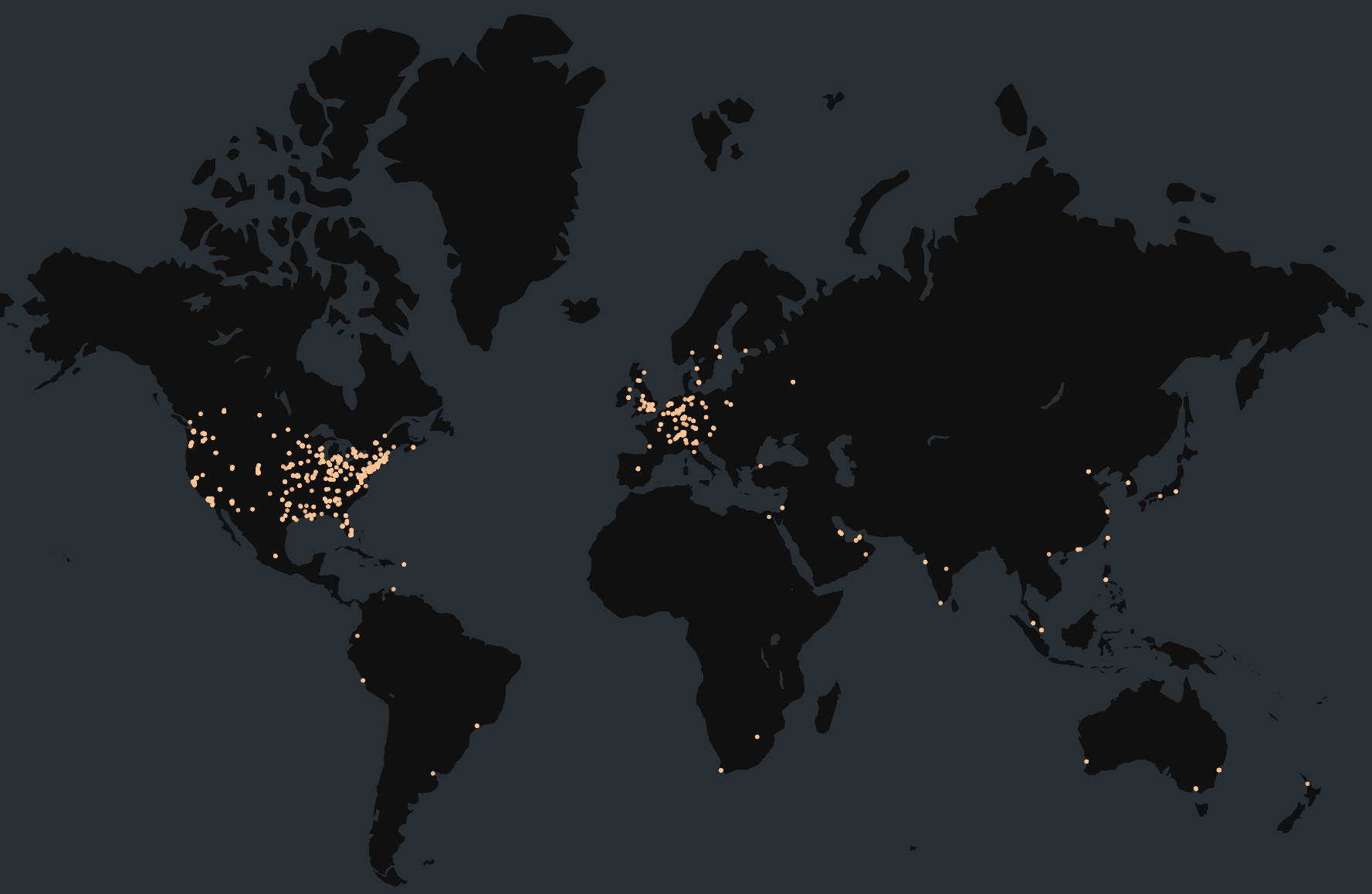
Global map of Censys-visible MOVEit Transfer exposures as of June 25, 2024
This is not surprising, as it closely mirrors the geographic distribution of hosts we observed when examining MOVEit Transfer exposures in 2023.
We also observe similarities in exposure across autonomous systems when compared to the exposure footprint from 2023. Most instances are observed in Microsoft or Amazon ASes.
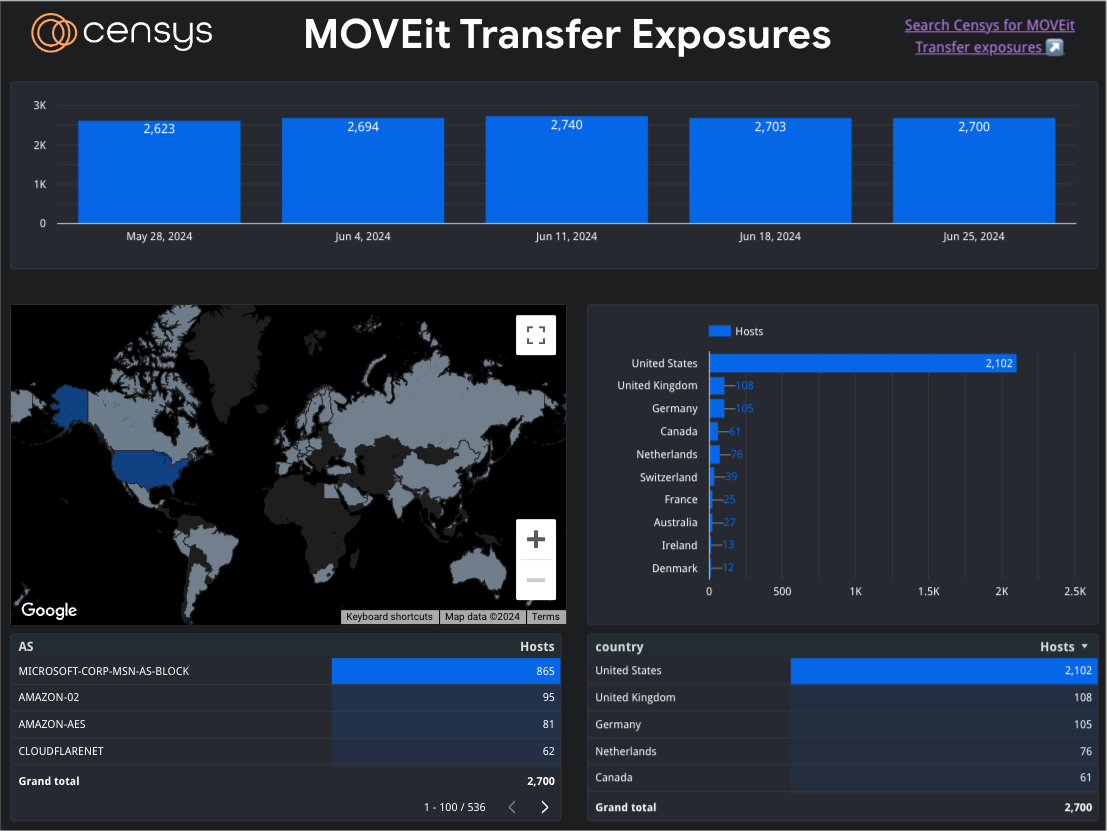
As evident in the data shown above, the level of exposure has remained relatively consistent since May 28, 2024.
We’ve created a dashboard to track MOVEit Transfer exposures over time, geography, and networks.
Conclusion
The similarities between Censys-observed MOVEit Transfer exposure in 2023 versus 2024 may indicate how vital MOVEit is to the organizations where it is in use. While we didn’t necessarily expect a drastic drop in MOVEit Transfer exposure following the 2023 campaign by Clop, the similarity in the exposure numbers serves as a reminder that once enterprise software is in place, it often stays in place, even in the face of massive exploitation.