GoAnywhere MFT Breaches by high-profile ransomware groups have now affected 8 confirmed organizations (and counting)
Executive Summary:
- In early February 2023, Censys reported on a zero-day RCE vulnerability in Fortra’s “GoAnywhere MFT” (Managed File Transfer) software. The Clop ransomware gang claimed that they exploited this vulnerability to breach the data of 130 organizations. What’s more, it looks like other ransomware groups are jumping on the bandwagon.
- Over 2 months after this zero day was disclosed, Censys continues to observe almost 180 hosts running exposed GoAnywhere MFT admin panels, with 30% of these (55 hosts) showing indications of remaining unpatched and potentially vulnerable to this exploit. A single vulnerable instance has the potential to serve as a gateway to a data breach that could potentially impact millions of individuals.
- You can continue to track exposure using our interactive dashboard. Censys Exposure Management customers can check their inventory for vulnerable assets by using this query: risks.name:”GoAnywhere MFT Admin Console RCE Vulnerability [CVE-2023-0669]”
Timeline:
- On February 1, 2023, Fortra (the developer behind the infamous Cobalt Strike penetration testing tool) announced a pre-authentication RCE vulnerability in their “GoAnywhere MFT” (Managed File Transfer) product (CVE-2023-0669). According to Fortra’s investigation published last week, suspicious activity was observed as early as January 18.
- On February 6, a proof of concept of the exploit was released by security researcher Florian Hauser, followed by an emergency patch from Fortra in GoAnywhere MFT version 7.1.2
- Soon after, the Clop ransomware gang claimed that they hacked 130 organizations’ data using this vulnerability. Clop said they’re not encrypting systems with ransomware and are just stealing files stored on compromised servers, but so far no data has been posted on their data leak site. Researchers at At-Bay discovered that another prominent gang, BlackCat/ALPHV, has also been exploiting this vulnerability.
- In the months since, the list of confirmed victims of GoAnywhere MFT breaches has grown long, including Community Health Systems, Hatch Bank, Hitachi Energy, Rubrik, the City of Toronto, Procter & Gamble, Saks Fifth Avenue, and Crown Resorts.
- In March, Clop began to extort victims by demanding ransom payments. On its data leak site the gang claims that release of stolen data is “coming soon” but at the time of writing this no victims’ data has been leaked publicly.
- Below, we share an update on the current state of exposed and potentially vulnerable GoAnywhere MFT devices from Censys’s Internet-wide scanning perspective
The Internet’s Response:
We observe a slow and steady patch response to this actively exploited vulnerability. Since this zero-day was first disclosed, Censys has seen an approximate 46% decrease in the number of exposed GoAnywhere Admin Panels in our data (note that the software’s web client interface is not affected by this vulnerability). As of April 25, 2023, there are still 179 hosts running exposed instances, with 55 of these (30%) showing indications of running vulnerable versions of the software (versions earlier than 7.1.2).
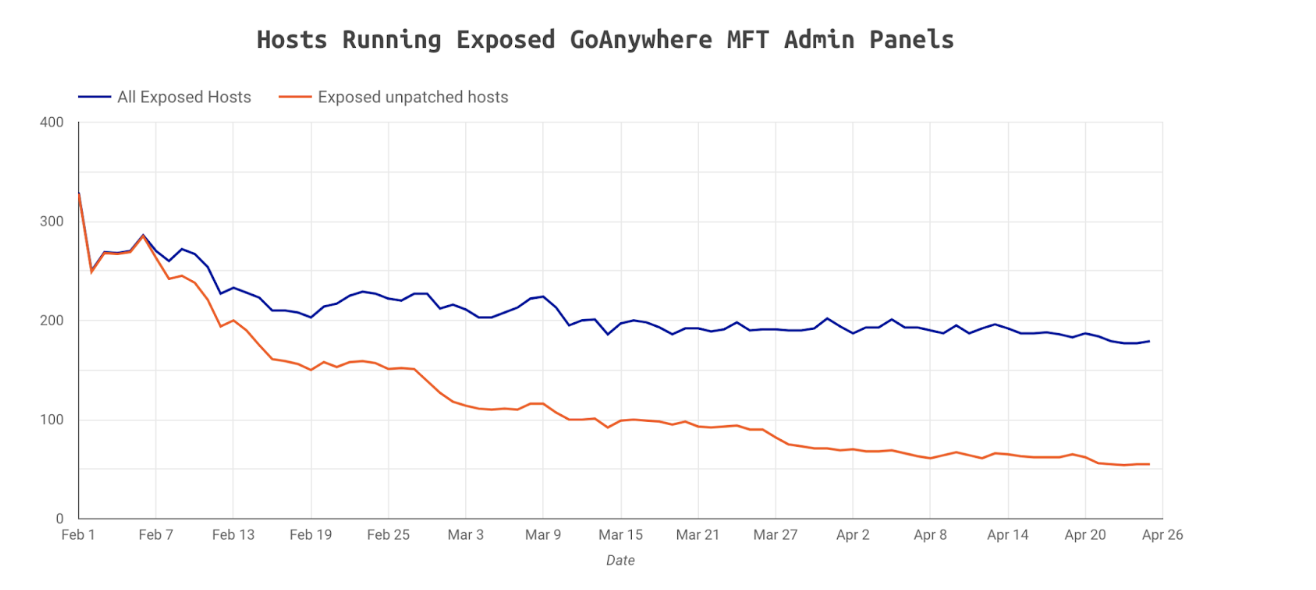
GoAnywhere MFT Exposures Since the Zero Day Disclosure in Early February
The region with the highest level of exposure is the United States, accounting for over half of exposed GoAnywhere MFT instances (~56%), followed by Australia, the U.K., and Ireland.

The U.S. has the highest concentration of GoAnywhere MFT Exposures
Here are the networks that we see the most exposed instances running in:
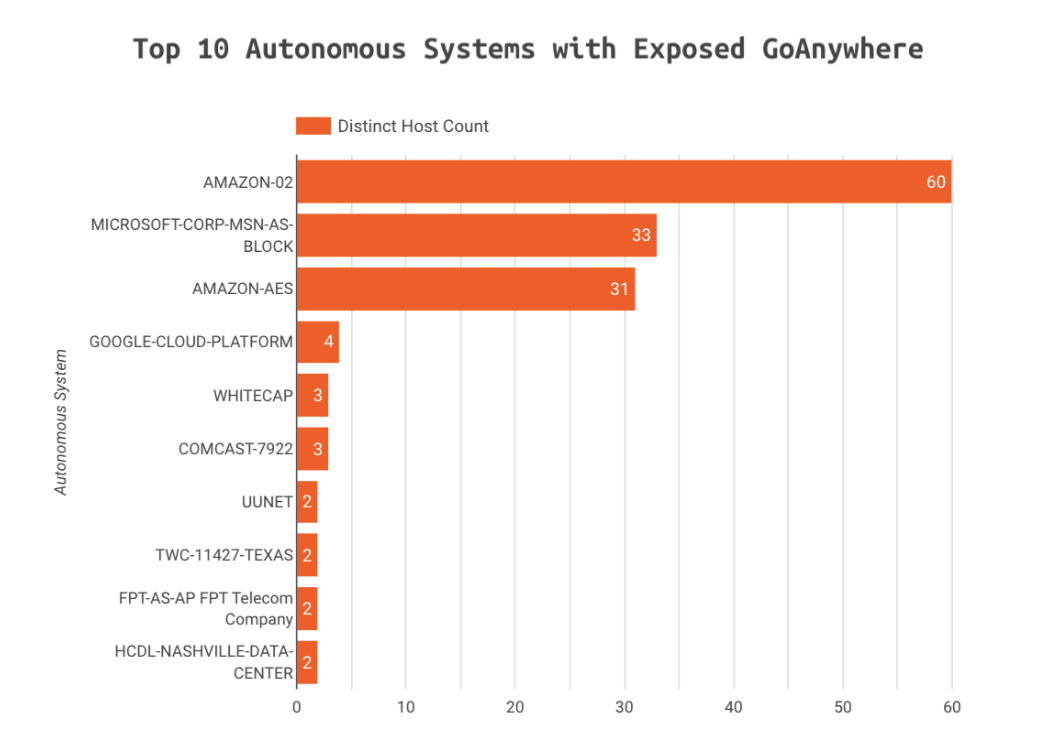
Amazon and Microsoft networks have the most GoAnywhere MFT Exposures
It’s encouraging that the majority of exposed devices we see (80%) appear to be running patched versions of 7.1.2 and 7.1.3. Nevertheless it’s concerning to see instances running versions as old as 5.7.6 still floating around.
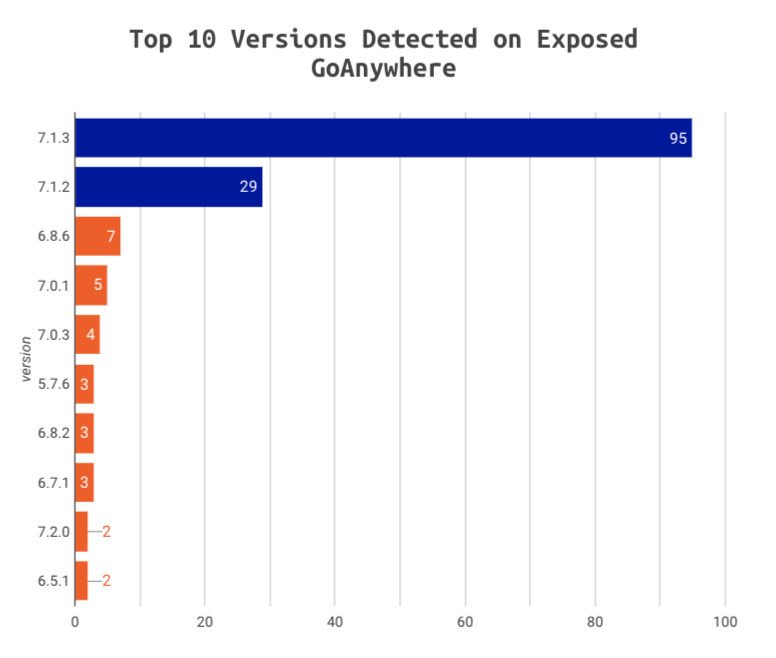
80% of exposed admin panels show indications of being patched. Dark blue denotes non-vulnerable versions, while orange denotes vulnerable versions.
However, just one exposed unpatched instance can be a potential entry point for a threat actor to exploit this zero day. In addition to applying the patch it’s good practice to avoid exposing your admin panels to the internet.
Mitigation Recommendations:
- Patch your software! Upgrade all of your installations to GoAnywhere MFT version to at least 7.1.2. Here’s how to check what version of GoAnywhere is running on your machine: https://forum.goanywhere.com/gateway-version-license-check-1376
- Per the mitigations suggested in Fortra’s investigation, GoAnywhere MFT customers should:
- Rotate your Master Encryption Key.
- Reset all credentials – keys and/or passwords – including for all external trading partners/systems.
- Review audit logs and delete any suspicious admin and/or web user accounts.
- If your admin console is exposed to the public internet, set up access controls using firewall rules, VPN segmentation, or VPC segmentation to reduce the risk of unauthorized access
You can continue to monitor the state of the GoAnywhere zero day with our interactive dashboard.
References: