Last Friday, we published our observations regarding the recent zero-day arbitrary file read vulnerability (CVE-2024-24919) affecting various Check Point VPN gateway products.
In this follow-up, we investigate the potential impact in more depth, providing statistics on globally exposed and potentially vulnerable devices.
Executive Summary
- As of June 3, 2024, Censys observed 13754 exposed Censys-visible CheckPoint VPN gateways running one of the software products associated with CVE-2024-24919.
- Of the exposed Quantum Spark gateways among these, just under 2% are running Check Point’s patched version, while approximately 4.6% show signs of running a potentially vulnerable version. This is likely an underestimate since most Quantum Spark gateways do not disclose their version. It’s also important to note that only devices with IPSec VPN or Mobile Access blades are vulnerable, however our perspective does not account for this as we cannot probe the internal configurations of these devices.
The Impact of CVE-2024-24919
When assessing the impact of this vulnerability, defenders should take several factors into account:
Reasons for Concern:
- This is a critical vulnerability that’s being actively exploited in the wild
- The exploit requires no user interaction or privileges, making it easy to exploit remotely
Mitigating Factors:
- This only affects gateways with specific configurations (IPSec VPN or Mobile Access software blades enabled)
- Successful exploitation does not necessarily mean full device compromise; other circumstances need to be in place, like the presence of exposed password files on your device’s local filesystem
While the vulnerability is undoubtedly severe, its impact is somewhat limited by the specific configurations required for exploitation.
Let’s take a look at Censys’s updated perspective as of Monday, June 3, to better understand the potential scope of this vulnerability.
Censys’s Perspective
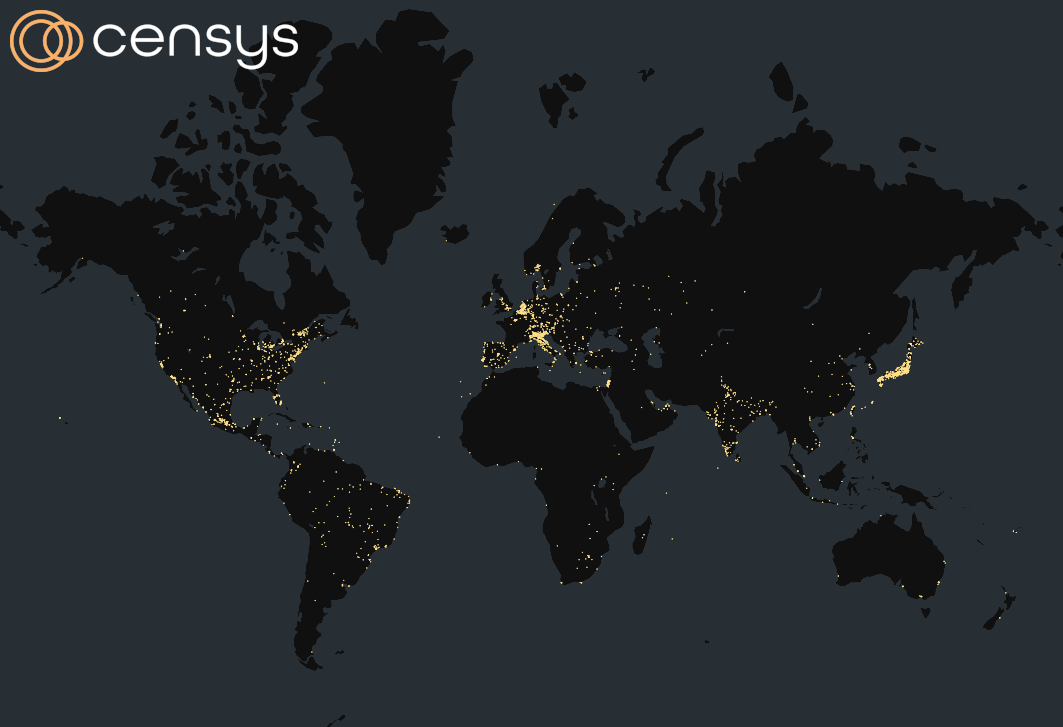
Map of Exposures of All Affected Censys-visible Hosts as of June 3, 2024
As of Monday, June 3rd, Censys observed 13,754 internet-exposed hosts running one of the three affected Check Point software products we can reliably fingerprint in our data:
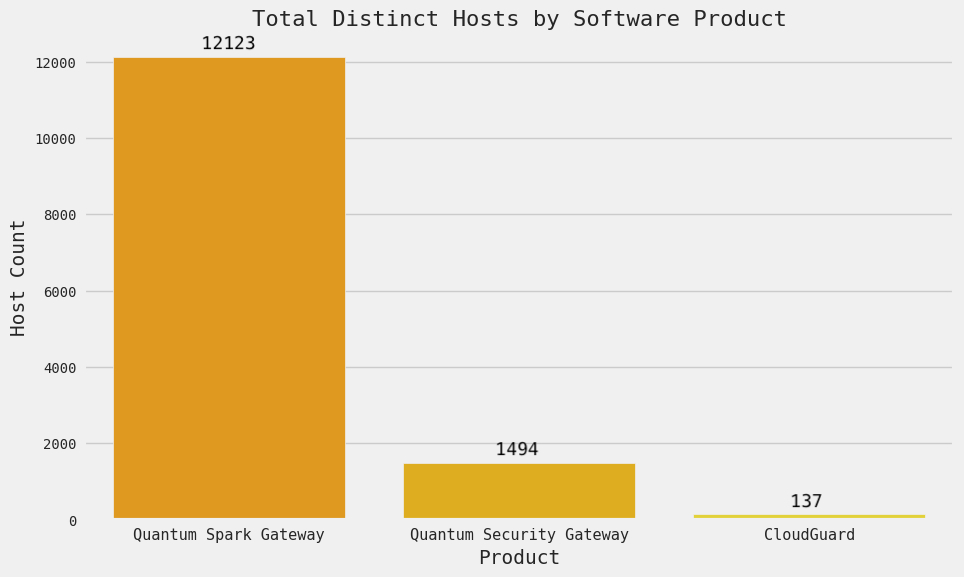
Comparison of Exposures of Each Affected Software Product
This is a minimal decrease from the 13,800 exposed hosts observed on May 3, 2024. A continual, more significant drop could indicate users deactivating VPN gateways or restricting public access. Note that not all of these instances are necessarily vulnerable, but the scope of this exposure is relatively high. The graph above highlights the extent of Quantum Spark Gateway’s exposure compared to the other software products.
As we reported last Friday, Japan has the highest concentration of exposed hosts by far at just under 6,000.
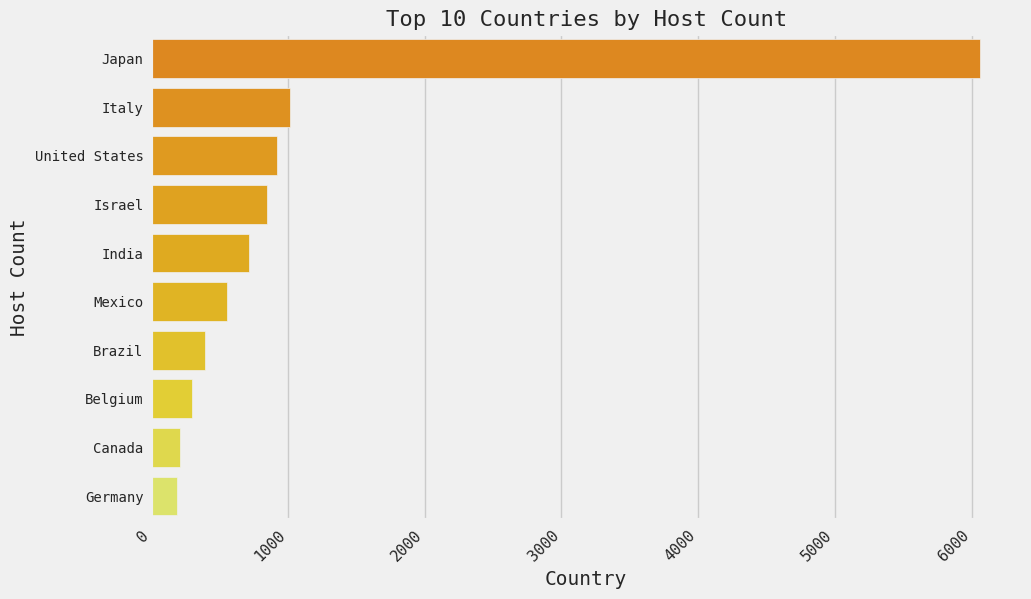
| Country |
Distinct Hosts |
| Japan |
6059 |
| Italy |
1012 |
| United States |
917 |
| Israel |
845 |
| India |
716 |
| Mexico |
556 |
| Brazil |
393 |
| Belgium |
295 |
| Canada |
211 |
| Germany |
191 |
When we examined the distribution of these exposures across various autonomous systems, we discovered that the highest concentration of hosts is the OCN NTT Communications Corporation. These hosts are likely part of OCN (Open Computer Network), a large ISP operated by NTT Communications Corporation in Japan.
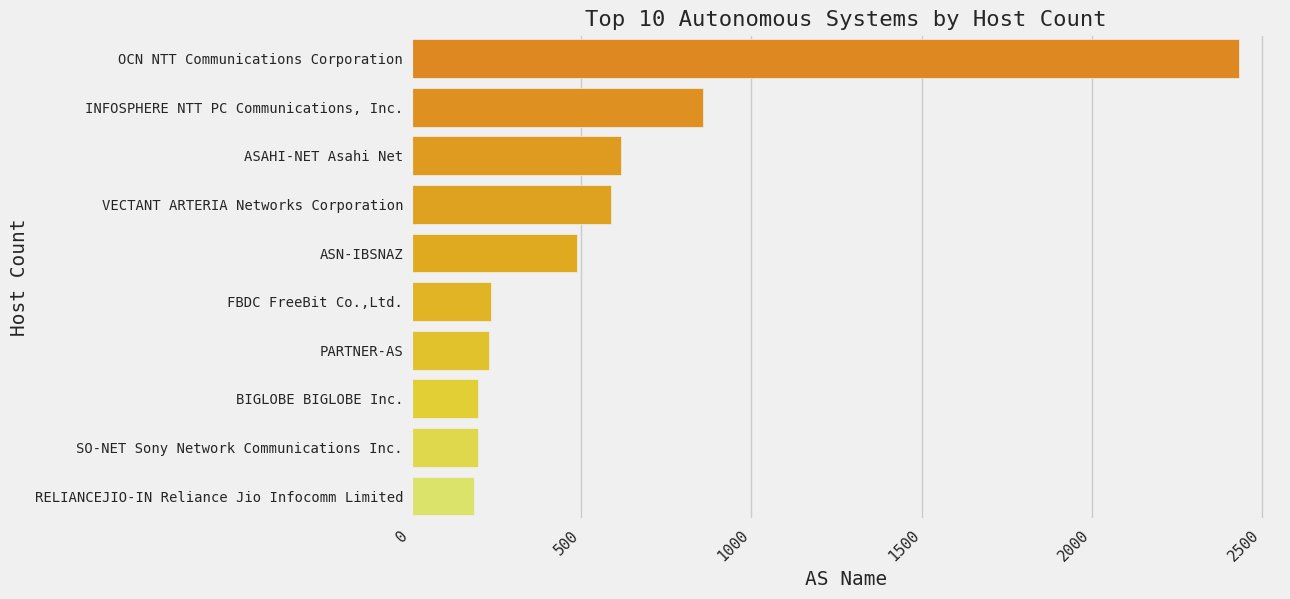
| Autonomous System |
Distinct hosts |
| OCN NTT Communications Corporation |
2433 |
| INFOSPHERE NTT PC Communications, Inc. |
857 |
| ASAHI-NET Asahi Net |
616 |
| VECTANT ARTERIA Networks Corporation |
589 |
| ASN-IBSNAZ |
489 |
| FBDC FreeBit Co.,Ltd. |
234 |
| PARTNER-AS |
229 |
| BIGLOBE BIGLOBE Inc. |
198 |
| SO-NET Sony Network Communications Inc. |
196 |
| RELIANCEJIO-IN Reliance Jio Infocomm Limited |
186 |
Potentially Vulnerable Quantum Spark Gateways
In some cases, Censys was able to obtain versions for Check Point Quantum Spark Gateway instances.
Of the 12123 Quantum Spark Gateways observed:
- 554 (or ~4.6%) of them were identified to be running a potentially vulnerable version. Note that these instances are only affected if they’re also configured with IPSec VPN or Mobile Access enabled, which these statistics do not account for.
- 227, or ~1.9%, were detected as running the patched version R81.10.10.
The overwhelming majority of instances had missing or insufficient data to accurately determine the version they appear to be running.
| Vulnerability Status |
Distinct Hosts |
| NULL VERSION |
10722 |
| UNKNOWN PATCH NUM |
620 |
| POTENTIALLY VULNERABLE |
554 |
| PATCHED |
227 |
|
|
Of the 554 potentially vulnerable instances, over a quarter are geolocated in Japan. The most common vulnerable version we detected running globally was R80.20.50, with 157 hosts.
| Version |
Distinct Hosts |
| R80.20.50 |
157 |
| R80.20.40 |
141 |
| R81.10.00 |
120 |
| R80.20.35 |
66 |
| R81.10.05 |
58 |
| R80.20.30 |
11 |
| R80.20.20 |
1 |
Around 75% of the 227 patched instances are in India, primarily on the Reliance Jio telecom network, with the rest in various telecom operators, ISPs, and broadband providers.
What can be done?
Check Point has released the following security updates to address this vulnerability:
- Quantum Security Gateway and CloudGuard Network Security: R81.20, R81.10, R81, R80.40
- Quantum Maestro and Quantum Scalable Chassis: R81.20, R81.10, R80.40, R80.30SP, R80.20SP
- Quantum Spark Gateways: R81.10.x, R80.20.x, R77.20.x
Censys ASM customers can use the following query to check for vulnerable Quantum Spark Gateways in their environment: risks.name=”Vulnerable Check Point Quantum Spark Gateway [CVE-2024-24919]”
Censys ASM customers can leverage the below queries to identify all Censys-visible public-facing instances of these three products:
- CloudGuard Network (exposures)
- Quantum Security Gateways (exposures)
- Quantum Spark Appliances (exposures and potentially vulnerable versions)