Introduction
In November 2023, the CyberAv3ngers, an Iranian Revolutionary Guard Corps-affiliated hacking group, compromised the Municipal Water Authority of Aliquippa, Pennsylvania. They targeted a water pressure monitoring system at a remote pumping station, exploiting a publicly exposed Unitronics Vision Series programmable logic controller (PLCs) known to ship with default passwords. The actor defaced the system’s interface with an anti-Israel message as part of a broader campaign targeting Israeli-made Unitronics PLCs globally, following regional conflicts.
In January 2024, the Cyber Army of Russia Reborn, a hacking group purportedly linked to Russia’s military intelligence, targeted water facilities in the small Texas towns of Muleshoe and Abernathy. The group claimed responsibility for manipulating human-machine interfaces (HMIs) at these facilities, which resulted in the overflow of water storage tanks and minor, temporary disruption of operations in Muleshoe.
These recent incidents highlight concerns about the security of critical infrastructure across the U.S. Internet exposure of industrial control systems (ICS) increases their susceptibility to attacks, potentially enabling threat actors to access and interfere with critical systems.
While many previous analyses of ICS exposure have focused on exposure of the automation protocols themselves, we explored the exposure of HMIs and web administration interfaces in addition to automation protocols. These protocols rarely provide context about their operations, while HMIs and web interfaces often display location information or other details useful for identifying ownership. We also examined the networks where these protocols and interfaces run in an effort to understand who might own and operate them.
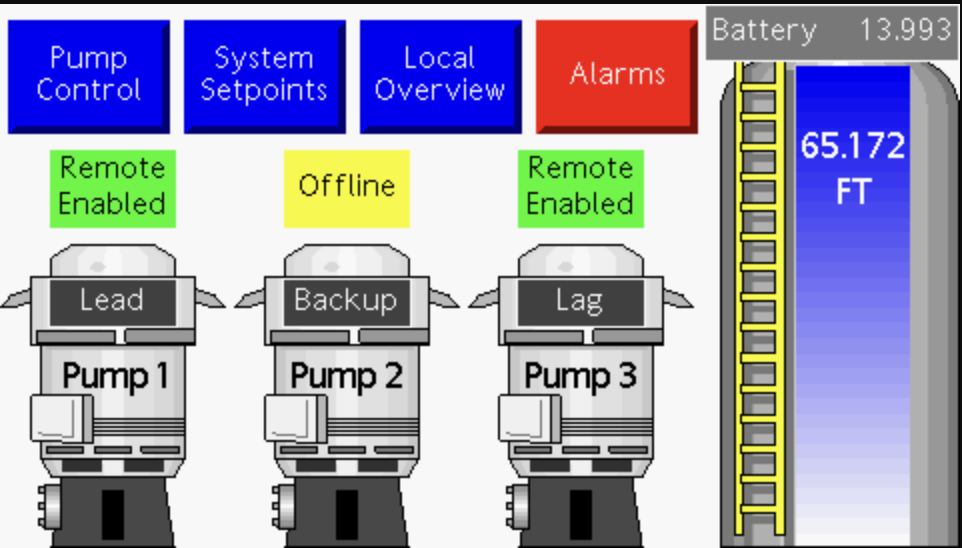
Figure 1: HMI for a three-pump system with options to view alarms, controls, and system setpoints
What did we find?
- Censys identified more than 40,000 Internet-connected ICS devices in the U.S., over half of which are associated with protocols used for building control and automation. Excluding known building control protocols, we find 18,000 exposed devices that are more likely to control industrial systems.
- Over 50% of hosts running low-level automation protocols are concentrated in wireless and commercial/business Internet service providers (ISPs), including Verizon and Comcast. Over 80% of hosts running exposed HMIs are found in wireless networks, such as Verizon and AT&T.
- Nearly half of the HMIs associated with Water and Wastewater (WWS) identified could be manipulated without any authentication required.
- Censys identified approximately 1,500 control systems in the UK exposed on the public Internet, as identified through scans of 18 automation protocols (e.g., EtherNet/IP, PCOM, and DNP3).
- In the UK, we identified roughly 1,700 HTTP devices associated with 26 operational technology (OT) vendors that are publicly accessible; many likely support default credentials. Our preliminary investigation finds over 80% of these administration interfaces are for building controls.
What did we study?
Censys researchers examined the current Internet exposure of ICS devices in the U.S. and the U.K.. Specifically, we studied:
Automation Protocols
Low-level automation protocols enable communication between programmable logic controllers (PLCs), remote terminal units (RTUs), human-machine interfaces (HMIs), and higher-level supervisory SCADA systems. Most are near real-time binary protocols that lack any form of authentication.
Human-Machine Interfaces (HMIs)
HMIs are the primary interface for operators to locally monitor and control industrial systems, but increasingly support Internet protocols to support remote access. HMIs provide easy-to-understand and easy-to-manipulate interfaces, which make them low-hanging targets for threat actors seeking to disrupt operations. In many cases, HMIs expose identifying information about their device owners.
Web Administration Interfaces
The digital footprint and attack surface of SCADA systems extends beyond automation protocols and HMIs. Many PLCs, RTUs, HMIs, and other components have HTTP-based administration interfaces that ship with default credentials.
Conclusions
Quantifying automation protocol exposure is only one part of this story; it’s also important for researchers and analysts to consider the Internet-accessible administration interfaces for many of these devices. Recent attacks highlight how these interfaces can be easily accessed and manipulated by threat actors who may not have detailed knowledge of the systems or associated protocols.
Many of the devices we identified in the U.S. are hosted on cellular networks or commercial/business internet service providers (ISPs). While HMIs and web administration interfaces occasionally offer clues as to ownership (e.g., city or location information in the user interface), automation protocols rarely expose such context, making it impossible to determine sector or organizational ownership for these devices. In turn, this makes notifying the owners of these device exposures impossible in many cases.
Follow Censys on  and
and  for details on our full report coming later this year!
for details on our full report coming later this year!