In Case You Missed Them: A Look Back at Some of Our Favorite Blogs from 2022
Miss a few Censys blog posts this year? You’re in luck. As 2022 comes to a close, we’re revisiting some of our favorite posts of the year. Check out our year-in-review list for a recap of Censys research findings, our take on cybersecurity trends, our thought leadership in the attack surface management space, and more.
Russian Ransomware C2 Network Discovered in Censys Data
In June, Censys researchers discovered two Russian hosts containing an exploitation tool, Metasploit, and a Command and Control (C2) tool, Deimos C2. Historical analysis indicated that one of these Russian hosts also used the tool PoshC2. These tools allow penetration testers and hackers to gain access to and manage target hosts. In this blog post, Censys Director of Federal Applications Matt Lembright breaks down how we uncovered the nefarious ransomware, and shares steps you can use to proactively hunt ransomware yourself.
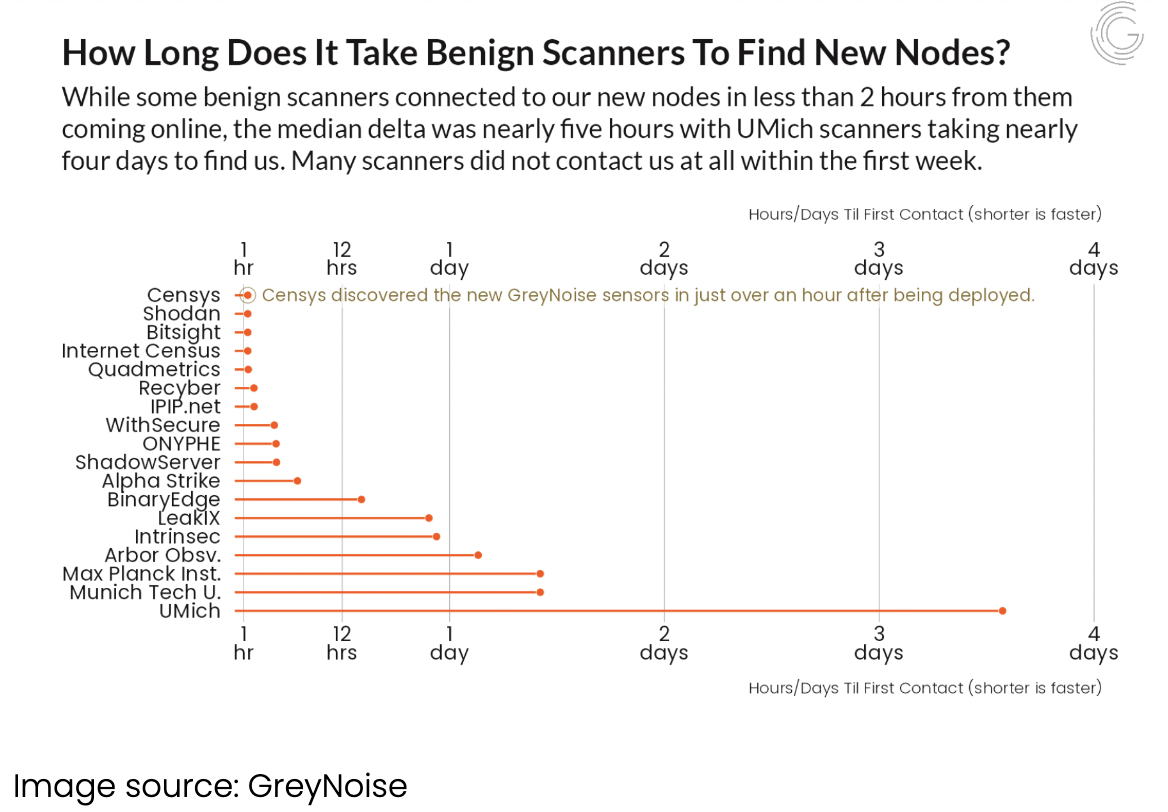
GreyNoise Research Finds Censys Scanning Data Is Fastest, Most Comprehensive
Who doesn’t love a little third-party validation? In a recent study of internet scanners, research firm GreyNoise found that Censys scanners were able to find new nodes faster than any other observed competitor. Censys scan data was also shown to be more comprehensive than data from the competitive set. In this blog article, Censys Senior Solutions Engineer Kevin Garrett walks through the GreyNoise data and provides a recap of their findings.
Finding Hacked Web Servers with Censys Search Data
Cybersecurity researcher? Threat hunting defender? No matter your role, you can use this step-by-step guide to find hacked web servers with the Censys Search tool. Follow along as our Censys researcher walks through the simple sequence of queries you can run to uncover a hacked server (which, according to research, is the asset most commonly impacted in cybersecurity breaches).
Tracking Deadbolt Ransomware Across the Globe
Deadbolt ransomware was the (unwanted) gift that kept on giving this year – and our research team was there to track it every step of the way. In this Rapid Response article from May, the team recaps how deadbolt spread around the world, and shares a Censys dashboard folks can use to track the ransomware themselves.
Where ASM Fits: A Comparison Guide of Security Tools
If you’ve heard about attack surface management (ASM) but have never really understood what it’s all about, or if it makes sense for your security team, this blog article is for you! Read up on the basics of ASM and how an ASM solution can fit within your existing security tech stack.
The Censys 2022 State of the Internet Report: Key Findings
This year marked the launch of our inaugural State of the Internet Report, a first-of-its-kind research endeavor that offers up a global perspective of the internet as a whole. In this blog, we round up some of the report’s most notable findings, including what we observed about the attack surface of the internet and how the internet responded to recent major vulnerabilities. (Ex: Did you know that misconfigurations actually make up the majority of risks observed on the internet?
Who’s Down with IPP? Finding Internet-Connected Printers with Censys
When you think of network security, internet-connected printers probably aren’t top of mind. But the reality is that every device that’s connected to the internet, regardless of how inconsequential they may seem, presents an open doorway to a network. And if you don’t know which printers are connected, securing that network becomes all the more challenging. That’s why in this how-to article, we’re showing you how to use Censys Search to quickly identify the internet-connected printers tied to your corporate infrastructure.
The Evolution of the Zero Trust Framework: The Origins
The conversation around the Zero Trust Framework, now a pillar of cybersecurity strategy, has been ongoing for nearly three decades. In this retrospective, our Censys Senior Solutions Engineer revisits how the Zero Trust Framework came to be and how its place in the cybersecurity space has evolved over the years.
How Censys ASM Delivers ROI for an International Real Estate Company
We can talk about the value of attack surface management all we want, but it’s best to let the results speak for themselves. In this case study recap, learn how an international real estate firm we partnered with gained qualitative and quantitative returns on their investment with Censys ASM.
In Support of the New CISA Directive: What It Means (& How to Take Action)
Learn more about the binding operational directive CISA issued in October, including: 1) Why we support it 2) How it affects various federal agencies and 3) How an attack surface management strategy can help teams meet the requirements. Not a federal agency? This blog is still worth your while – CISA’s directive lays the groundwork for best practices that organizations in all industries can use as a guidepost going forward.
You can expect more articles like these from the Censys team in 2023! Subscribe to the blog below and follow us on social for the latest and greatest.
Looking for more content in the meantime? Head on over to our Resources page, where you can find ebooks, reports, webinar recordings, and more.


