Executive Summary:
- On May 20, 2024, CISA added a previously disclosed unauthenticated remote code execution (RCE) vulnerability in NextGen Healthcare Mirth Connect to its KEV (Known Exploited Vulnerabilities) catalog, tracked as CVE-2023-43208. All versions before 4.4.1 are vulnerable.
- Affected Products: Mirth Connect is an open-source healthcare data integrations platform used widely in the healthcare industry.
- Impact: An unauthenticated threat actor can leverage this as an initial access vector to compromise a Mirth Connect gateway or access potentially sensitive healthcare data. This poses a significant concern, given the ease of exploitation reported by Horizon3.ai, the popularity of healthcare organizations as ransomware targets, and the consequences a healthcare data breach could pose for patient privacy, healthcare operations, and regulatory compliance.
- Patch Availability: This issue is patched in versions 4.4.1 and later of Mirth Connect. Censys cannot identify the active versions of software running in this instance.
- Exploitation Status: A PoC is available, and Microsoft has reported observations of active exploitation of both CVE-2023-37679 and CVE-2023-43208 among the group of 120 nation-state actors and cybercrime groups it tracks.
- Censys’s Perspective: As of May 20, 2024, Censys observed 1061 distinct hosts exposing a Mirth Connect administrator interface. Not all of these are necessarily vulnerable to this exploit – however, anything running a version under 4.4.1 is highly likely to be exploited, given the valuable nature of the healthcare data they likely handle.
- Detection:
Background
On Monday, May 20, 2024, CISA issued a warning about the active exploitation of CVE-2023-43208, an unauthenticated remote code execution (RCE) vulnerability in Mirth Connect. Mirth Connect is an open-source healthcare data integration platform developed by NextGen Healthcare, described on its GitHub page as “The Swiss army knife of healthcare integration.” It’s intended to improve the interoperability between various healthcare data platforms, such as electronic health records tools (EHRs). NextGen states in the README that they “help many of the nation’s largest, most respected healthcare entities streamline their care-management processes to satisfy the demands of a regulatory, competitive healthcare industry.” The GitHub repository shows indications of active maintenance.
This vulnerability affects all versions before 4.4.1 and stems from an incomplete patch for a previously disclosed critical RCE, CVE-2023-37679.
Timeline of Key Events:
Potential Consequences of Successful Exploitation:
This unauthenticated RCE vulnerability is easily exploitable, with a well-documented attack vector that exploits a bug in the Java XStream library, as demonstrated in the PoC published by Horizon3.ai. Threat actors can use it to compromise a Mirth Connect instance, which could potentially lead to a data breach. Given that Mirth Connect is reported to be adopted by many entities in the healthcare industry, it’s possible that a breach could expose various types of sensitive healthcare data, such as protected patient data.
The increasing number of ransomware attacks targeting healthcare organizations emphasizes the valuable nature of patient information data and the need for robust security measures in healthcare networks. However, many healthcare organizations face resource limitations, making it challenging to secure their sprawling networks effectively.
Servers running versions older than 4.4.1 are highly susceptible to exploitation. CISA required that federal agencies update to Mirth Connect version 4.4.1 or later by June 10, 2024 to mitigate this risk.
Censys’s Perspective
On May 20, 2024, Censys observed 1,061 hosts running exposed Mirth Connect administrator interfaces on the internet. Censys does not have visibility into versions – not all of these are necessarily vulnerable, but they definitely should not be exposed to the public internet.

Map of ~1k Censys-Visible Hosts Exposing Mirth Connect administrator interfaces on the Public Internet as of May 20, 2024
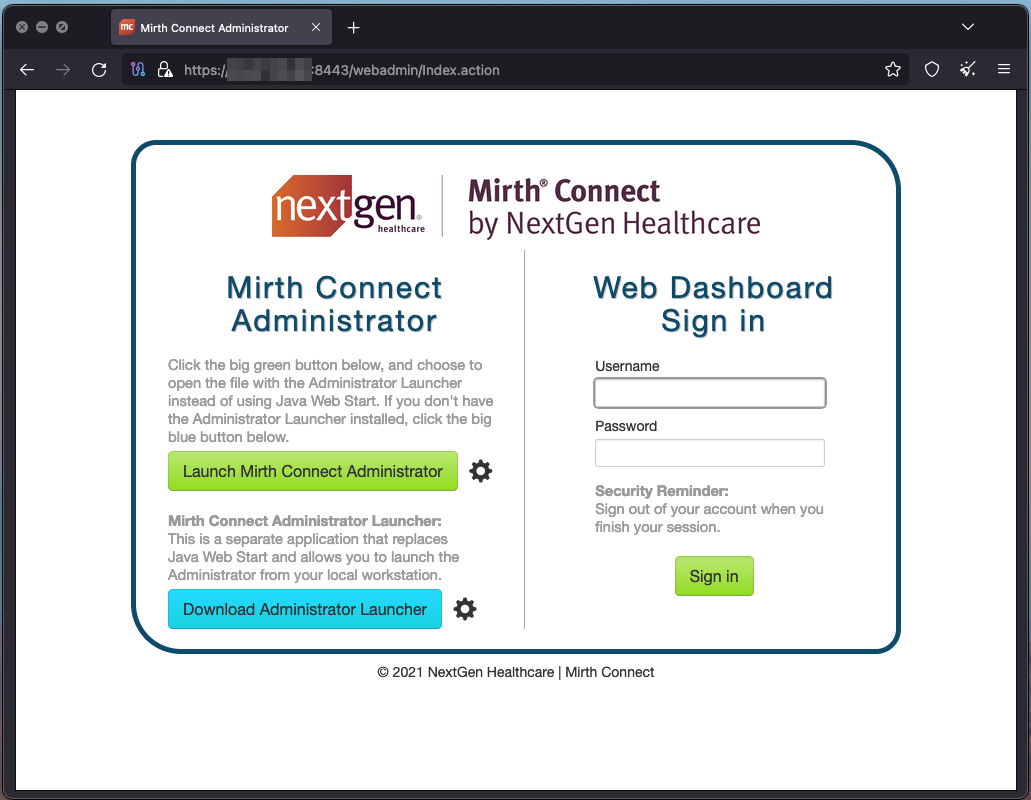
Example Exposed Mirth Connect Administrator interface
These exposures are most heavily concentrated in the United States, making up just under 45% of all the hosts we observe.
Top 5 Countries with Hosts Exposing Mirth Connect
| Country |
Host Count |
Percentage |
| United States |
474 |
44.67% |
| Germany |
78 |
7.35% |
| India |
64 |
6.03% |
| Brazil |
51 |
4.81% |
| Indonesia |
50 |
4.71% |
The top two autonomous systems with the greatest concentrations of exposed Mirth Connect hosts appear to be AMAZON-AES and AMAZON-02, both related to Amazon’s AWS cloud infrastructure.
Top 5 Networks with Hosts Exposing Mirth Connect
| Autonomous System |
Host Count |
Percentage |
| AMAZON-AES |
169 |
15.93% |
| AMAZON-02 |
159 |
14.99% |
| MICROSOFT-CORP-MSN-AS-BLOCK |
85 |
8.01% |
| DATABANK-LATISYS |
73 |
6.88% |
| HETZNER-AS |
41 |
3.86% |
Apart from the above hosts, we also detected 13,657 hosts appearing to be running Mirth Connect instances labeled “tarpits” in our data – meaning they have specific characteristics indicative of being a deceptive honeypot.
In previous investigations, we’ve identified a particular variety of honeypot-like entities that seem designed to catch internet scanners. They attempt to emulate many different services, often have self-signed certificates with domains that appear to be generated from a predefined list of keywords, and roar to life around the time a new (or newly exploited) vulnerability announcement is released.
These honeypot-like services were distributed across hosts in these networks:
| Autonomous System |
Host Count |
Percentage |
| AMAZON-02 |
12357 |
90.46% |
| AMAZON-AES |
1300 |
9.52% |
The autonomous systems where we observe these duplicitous services largely mirror where we’ve observed them before, primarily in Amazon-owned networks.
Recommendations for Remediation
It’s recommended to upgrade all Mirth Connect instances to 4.4.1 ASAP. Admin interfaces such as these should typically never be exposed on the public internet – it’s good practice to implement network segmentation and other access controls to prevent them from being internet-facing.
References: