Executive Summary
- We’ve identified an additional 11 hosts that appear to have a variant of the ESXiArgs ransom note dating back to October 2022, only one of which appeared to pay the ransom.
- The new variant of ESXiArgs–with improved encryption and no Bitcoin addresses in the ransom notes–remains the dominant variant, accounting for 95% of currently observed infections.
- We developed a simple probe for the SLP protocol to better understand how many infected hosts are running SLP. Since deploying the probe on February 15, we’ve observed no more than 9% of infected hosts each day running SLP.
Last week, we discovered two potential early victims of ESXiArgs (Host-A, Host-B) after noticing that they were the only two hosts with the ransom note on February 1 and January 31, 2023. Manually searching our data, we determined that they’d had a variant of the ransom note since mid-October 2022, but we were curious whether more hosts were impacted prior to the ramp-up of the February 2023 campaign.
Historical Footprint
We searched weekly snapshots back to January 2022 across all of our Internet scan data and discovered an additional 11 hosts with the ransom note beginning in October 2022. This brings us to a total of 13 unique hosts with a variant of the ransom note prior to the early February 2023 campaign.
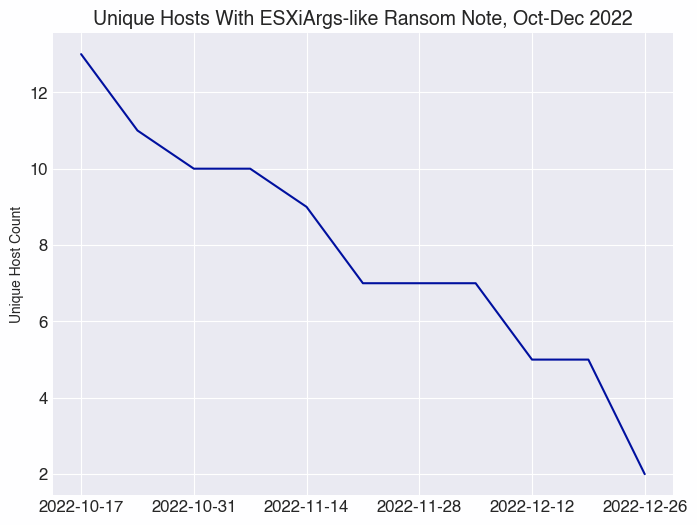
Host-A and Host-B are both hosted on French cloud provider OVH, one of the autonomous systems most affected by this ransomware campaign. The autonomous system breakdown of the 13 hosts observed in October is as follows:
| Autonomous System Name |
Number of Infected Hosts, October 2022 |
| OVH |
7 |
| HETZNER-AS |
4 |
| HZ-EU-AS, BG |
1 |
| AS-LUCKY Lucky Net Ltd, UA |
1 |
Host-A and Host-B are the only hosts we observed that maintained the ransom note from October 2022 through February 2023, when the most recent campaign began.
| Country |
Number of Infected Hosts, October 2022 |
| France |
4 |
| Germany |
3 |
| Poland |
3 |
| Ukraine |
1 |
| Finland |
1 |
| Russia |
1 |
Early Ransoms
A total of 10 distinct Bitcoin addresses were used in the ransom notes for these 13 hosts, all of which are prefixed with “bc1,” indicating Bech32-style addresses. This is in contrast to the February campaign, where the majority of addresses were prefixed with “1,” the Legacy variant of Bitcoin addresses. We’re unsure of why there was a shift in address types between these early ransoms and the February campaign. Based on data from a blockchain explorer tool, only one of the addresses (bc1q46zs36ey53lem5qv2pryumtmdtmtr352fdk4pj) appears to have received any payments at any point in time.
The payment received on October 14, 2023, is for 1.08381000 BTC, or $25,696.74 USD, which may correspond to a ransom demand of 1.08739 on host 185.104.194[.]13, as a ransom note with this address and BTC amount appeared in our October 19 data but was not observed with the ransom note the following week on October 24 (requires enterprise Censys account to view; archived raw JSON data for this host on October 19 can be found here).
All observed BTC addresses in 2022 ransom notes:
bc1q46zs36ey53lem5qv2pryumtmdtmtr352fdk4pj*
bc1qumexs7v2qtu5sx54y4mgmefn698gh9qq8cu8sp
bc1q0thcm5cc25u2jj78njxx7e9sa7z2dhdu59d0cw
bc1q2lh5umwu7pgszg56s76x9hx948rrkhjxfkff4x
bc1q6n2xd3zg8lqvtk57g8dq9r60zhz0czz9q87uag
bc1qdcadgtv5d6kqdl70g9vgg7u3vkqvfy3kwz66qj
bc1qh0dmcpd56kpx53ca65mmdnapdz3qw8pqpevh8g
bc1qj8hc3744eu6f8nyxlyl0wuqcdqaa4gcnznv4px
bc1qkrgdmdj4faw8mn0nca089w0crwg8t5hm7fuqz0
bc1qx59nlts3g24xp2j0pwkl3klsf9ue0qcuegxrqe
*Only address to receive payment.
Tracking Original and New Variants
When we discuss the “original” and “new” variants of ESXiArgs, we make the distinction based on the contents of the ransom note. Because our scanners are passive, we’re unable to determine anything ourselves about the encryption method used on a given host. However, based on reports from other researchers, we feel comfortable stating that if a host has the “new” ransom note variant (i.e., no Bitcoin address), it’s highly likely that the encryption method is also of the “new” variant.
Since February 8, we’ve observed a dramatic shift in the dominant variant of ESXiArgs infections. Prior to February 8, the “original” ransomware used an encryption method that could be circumvented by CISA’s decryptor tool, and it included Bitcoin addresses on the ransom notes.
On February 8, seemingly as a direct response to CISA’s tool and researchers tracking ransom payments, the actor changed the encryption method and removed Bitcoin addresses from the ransom notes.
Our snapshot for February 8 reflects that 73% of infected hosts that day (whether they were new or “upgraded” infections) had the new variant. On February 9, it jumped to 91% of all infected hosts.
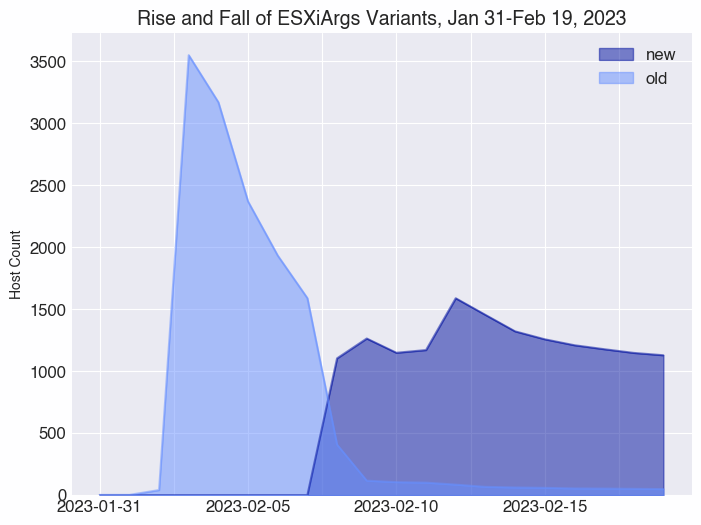
As of February 20, 2023, 49 hosts still appeared to be infected with the original variant that included Bitcoin addresses in the ransom notes:
| Country |
Total Hosts with Original Variant |
| France |
15 |
| United States |
12 |
| United Kingdom |
4 |
| Germany |
4 |
| Canada |
4 |
| Turkey |
3 |
| Taiwan |
3 |
| Singapore |
1 |
| Netherlands |
1 |
| Hong Kong |
1 |
| Czechia |
1 |
SLP’s Role in ESXiArgs
Early reports of ESXiArgs attacks pointed to CVE-2021-21974, a vulnerability in SLP dating back to February 2021, as a possible explanation as to how threat actors may have gained access to the infected hosts. However, victims who claimed they weren’t running SLP at the time of the infection soon came forward, suggesting there may be more to the story. VMWare now states as a part of their FAQ on ESXiArgs that the vulnerabilities involved in the attacks remain unclear.
As a result of the questions around SLP’s role in this campaign, we deployed a simple SLP probe that allows us to determine whether a host is running SLP. Our probe was deployed on February 15, and since then, we’ve observed the following:
| Date |
Count of Infected Hosts
Running SLP |
Percent of Infected Hosts
Running SLP |
| 2023-02-15 |
69* |
5% |
| 2023-02-16 |
102 |
8% |
| 2023-02-17 |
114 |
9.2% |
| 2023-02-18 |
116 |
9.6% |
| 2023-02-19 |
113 |
9.5% |
| 2023-02-20 |
106 |
9.2% |
| 2023-02-21 |
102 |
9.1% |
*This lower number may be explained by our rollout of the probe on February 15, 2023.
Given the relatively low number of infected hosts that also appear to be running SLP, we believe it’s likely there are other vulnerabilities or methods of access involved in these attacks.
You can continue monitoring ESXiArgs infections on our dashboard.