Healthcare data breaches are on the rise, and they have consistently been the most expensive type of breach across all industries over the past 13 years. In this sector, the disruption caused by a breach goes beyond financial loss—it can directly affect patient care and human health.
Censys investigated the exposure of various healthcare devices and data platforms online that interface with and in some scenarios allow unauthenticated access to sensitive medical data, including DICOM, PACS, and various electronic record and data exchange platforms.
Executive Summary:
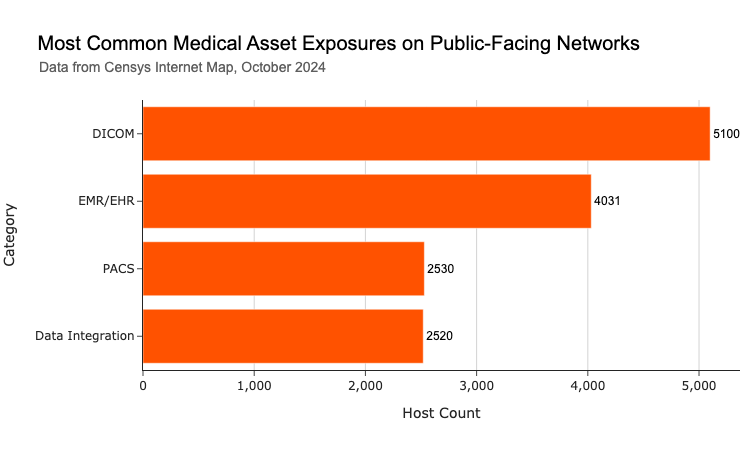
- Censys discovered 14,004 unique IP addresses exposing healthcare devices and data systems connected to potentially sensitive medical information on the public internet. These exposures greatly raise the risk of unauthorized access and exploitation. This figure likely reflects the lower bound of the total risk, as many more devices may be exposed but not publicly visible..
- Nearly 50% of the exposed hosts (6,884) are located in the United States, followed by 10.5% (1,476) in India. This is likely due to both countries having large, complex healthcare infrastructure that serves large populations, where organizations must handle vast amounts of sensitive data. Comparatively, we detected only 200 publicly available hosts in the United Kingdom, possibly a reflection of its more centralized healthcare infrastructure.
- Open DICOM ports and DICOM-enabled web interfaces intended for exchanging and viewing medical images account for 36% of the exposures, with 5,100 hosts publicly exposing these systems. This is concerning because DICOM is a legacy protocol with several known security weaknesses.
- EMR/EHR systems, which store and manage electronic health records, represent the second-largest exposure type at 28% with 4,031 interfaces publicly available. The exposure of the login interfaces to these systems potentially puts vast amounts of sensitive personal health data, including medical histories and social security numbers at risk.
- Healthcare organizations must prioritize securing their internet-exposed assets that handle sensitive patient data, particularly DICOM and EMR/EHR systems. This includes strengthening access controls, enforcing multi-factor authentication, and ensuring proper configurations in both cloud and on-premise environments to protect sensitive medical data.
Introduction
In February 2024, Change Healthcare—one of the world’s largest health payment processors—was paralyzed by a cyberattack from the ALPHV/BlackCat ransomware gang. The hackers claimed to have stolen 6TB of sensitive data, including patient Social Security numbers and medical records, demanding a $22 million ransom to prevent its release on the dark web. Despite the company paying the ransom, the data still ended up on the dark web. The breach sent huge disruptions through the U.S. healthcare system, causing massive delays in patient care and reimbursements, and leaving many smaller and rural practices struggling financially for months while systems were restored.
The Healthcare and Public Health sector is the top target for ransomware attacks, according to the FBI’s 2023 Internet Crime Report. It’s not difficult to understand why. Healthcare organizations manage highly sensitive patient information, and the critical nature of their operations means that disruptions can be life-threatening. Hospitals are often pressured to pay extremely large sums to restore critical systems and to prevent leaks of HIPAA-protected data. These incidents can severely disrupt healthcare operations, result in costly lawsuits, and, in extreme cases, threaten patient lives.
The Change Healthcare cyberattack stands as one of the most significant and impactful incidents ever against the U.S. healthcare system. Yet, the weaknesses exploited in the attack were painfully common—the attackers used stolen credentials to access an exposed remote access service that lacked multi-factor authentication (MFA).
While data breach attack vectors vary, a recurring weakness that makes breaches more likely is the exposure of devices to the public internet when it’s unnecessary—especially those that protect sensitive health data. Systems like medical imaging devices and electronic health records, when exposed online without safeguards such as firewalls or VPNs, become much easier targets for attackers. Basic security lapses, including weak credentials, unencrypted connections, or misconfigured permissions, can easily lead to unauthorized access and exploitation.
Exacerbating the situation is the under-resourced state of many hospital IT departments. IT teams in healthcare are often stretched thin, making it difficult to manage their organization’s external attack surface effectively. This is particularly difficult for large organizations with multiple locations and branches.
This attack surface goes beyond just medical devices, but this class of devices in particular is often not designed with security in mind, while interfacing with highly sensitive patient data. Exposed medical devices and healthcare data systems can lead to compromised patient data, disrupted medical services, and even direct threats to patient safety.
This blog aims to shed light on the current state of internet-connected medical device and healthcare data system exposures. We leverage Censys’s global internet scanning perspective to analyze these exposures by specific product, vendor, geography, network presence, and the security implications of each. The findings presented here are crucial for healthcare providers, device vendors, and particularly cybersecurity policymakers to understand the potential risks associated with these exposed systems. By identifying and quantifying these exposures, we can better inform cybersecurity strategies and risk mitigation efforts across the healthcare sector.
It is important to note that our research focuses on exposures rather than vulnerabilities. While an exposed device is not inherently vulnerable, its presence on the public internet increases the attack surface of any sensitive medical data it interfaces with and increases the potential for exploitation.
Findings:
Censys identified 14,004 IPs that publicly expose healthcare-related devices and applications on the internet. Our efforts were focused on identifying publicly-accessible interfaces and services from an external attack surface perspective, so this figure likely captures only a portion of the full state of exposure, as many more systems are likely exposed but not openly accessible.
When we break down the types of assets exposed, DICOM servers make up the largest group, accounting for 36% of all exposures. These are primarily used for handling medical images, and often allow access to their connected databases of images without authentication, making their exposure a serious concern. EMR/EHR systems come next, representing 28% of the exposed devices. Other systems discovered include PACS imaging servers and healthcare data integration platforms like NextGen Healthcare’s Mirth Connect.
Below we dive into the security implications of each of these asset types.
DICOM
DICOM, or “Digital Imaging and Communications in Medicine,” is both a file format and a network protocol used to transmit medical images such as MRIs and CT scans. It was designed to connect radiology hardware with software for easier image analysis. DICOM has been a cornerstone of medical imaging for over 30 years, but like many protocols from the early internet era, it wasn’t built with security in mind, and its complexity makes it prone to misconfigurations. It should absolutely not be publicly accessible over the internet.
We identified 5,100 publicly exposed DICOM servers, after filtering out false positives and honeypots. This includes hosts exposing various DICOM-enabled image viewing web interfaces over HTTP, as well as hosts exposing the lower level DICOM protocol itself via layer 7.
We analyzed the domain names and certificates linked to these DICOM exposures and made our best effort to associate them with real-world organizations. Most of the exposed servers we identified seem to be tied to independent radiology and pathology service providers, as well as imaging departments within larger hospital networks.
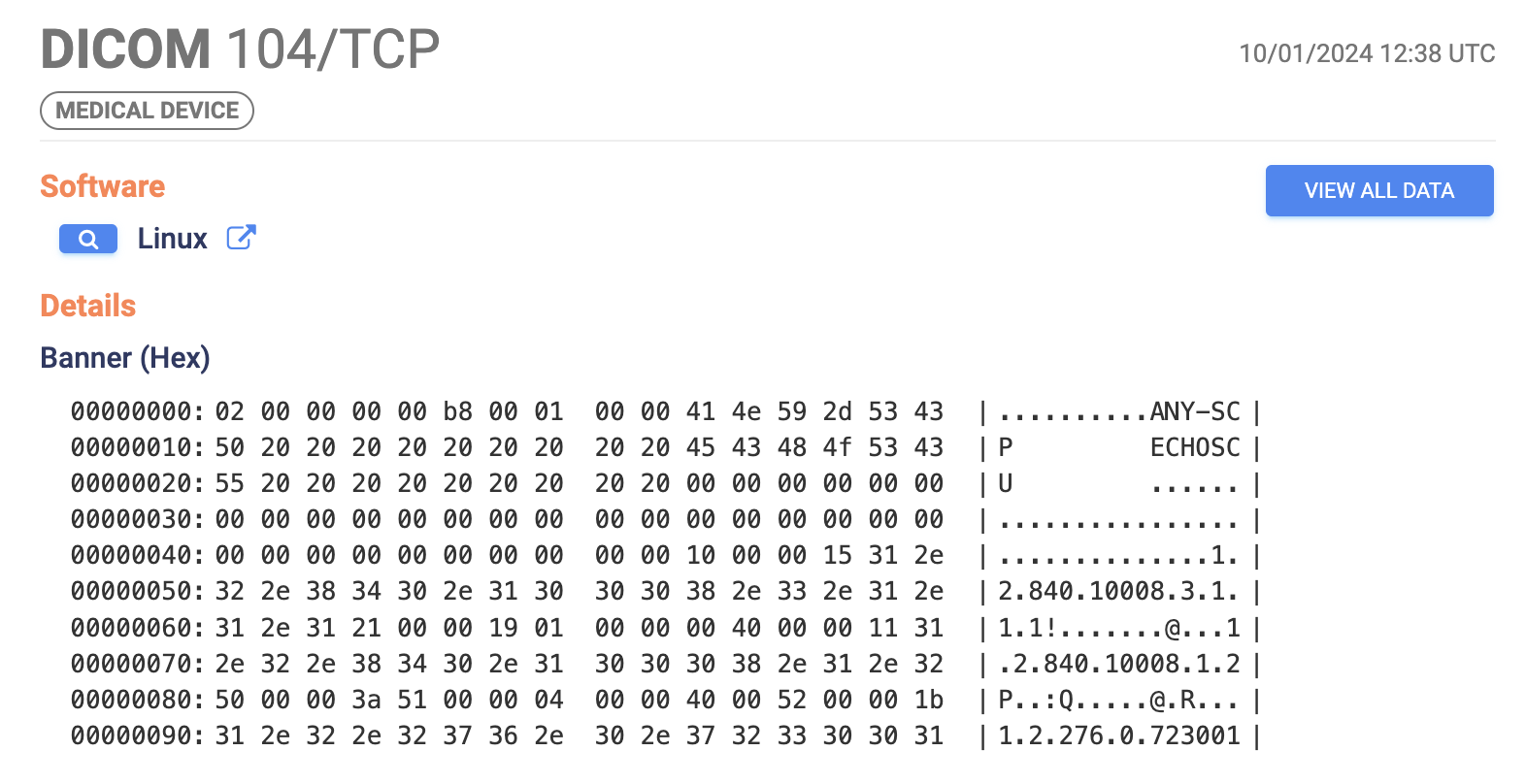
Example Response from an exposed DICOM service
This level of exposure is alarming due to the significant security risks associated with the DICOM protocol. While we’re focusing on exposures here rather than specific vulnerabilities, the significance of these exposures has been exemplified numerous times in prior research.
A 2023 study by Aplite GmbH revealed that less than 1% of the nearly 4,000 DICOM servers they scanned had proper authorization in place, exposing them to attacks that could lead to unauthorized access or tampering with sensitive patient data through techniques like database injection depending on the services exposed. Although healthcare organizations are required to anonymize protected health information (PHI) in these files under HIPAA, this isn’t always enforced.
Another particularly dangerous issue with DICOM was highlighted in 2019 by Cylera researchers, who found that malware could be embedded in the 128-byte preamble of a DICOM file without affecting its readability. Given the nature of these files, that malware could even inadvertently fall under HIPAA protection, making detection and removal more complicated.
DICOM exposures are, unfortunately, not a new issue, although the scale of exposure reported here exceeds most prior research. So why do these exposures continue to persist?
It’s likely because radiology practices and researchers often need to share and review images with external parties outside of their networks, leading to configurations that prioritize accessibility over security. This often results in DICOM servers and interfaces being deployed on the public internet without proper access controls like firewalls or VPNs. It’s telling that the top two most commonly exposed DICOM web-based interfaces we observed were open source solutions (OHIF Viewer and Orthanc Explorer). Many organizations are likely relying on lightweight tools and setting up their own configurations.
Table 1: Most commonly exposed DICOM web viewer interfaces
| Application |
Host Count |
| OHIF DICOM Viewer |
902 |
| Orthanc Server Orthanc |
500 |
| NeoLogica RemotEye |
215 |
| XERO Viewer |
178 |
| Philips IntelliSite Digital Pathology |
82 |
| Butterfly Network Ultrasound |
14 |
Unfortunately, many of these Orthanc servers had woefully insecure configurations from Censys’s scanning perspective, with most allowing unauthenticated remote access directly to their medical imaging databases. To that effect, several of these interfaces featured a prominent banner at the top with detailed information about their security configurations, including whether remote access was permitted and whether authentication was enabled:

Exposed unauthenticated Orthanc Explorer DICOM viewer web interface with an insecure configuration
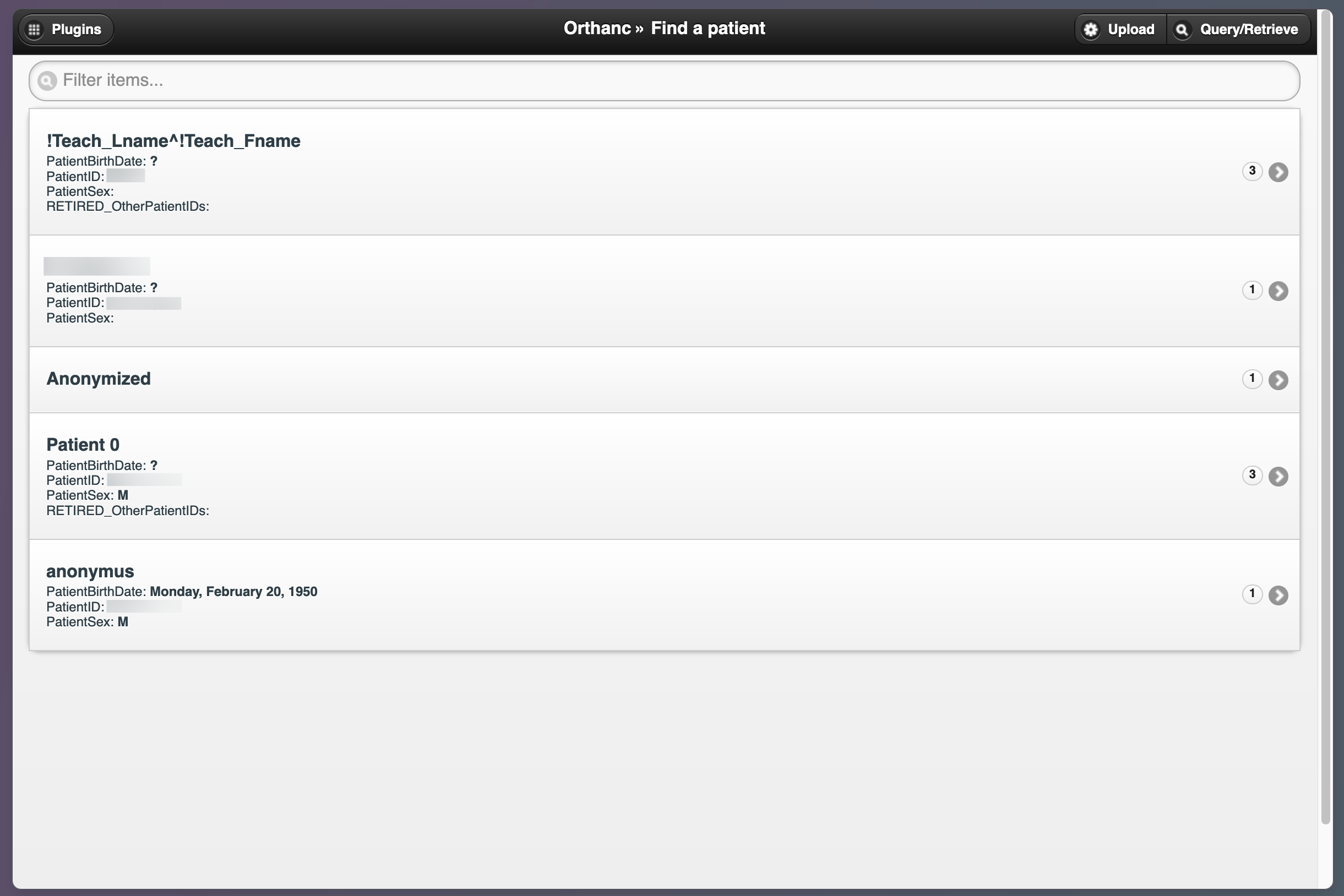
Exposed unauthenticated Orthanc Explorer DICOM viewer hosting medical imaging database files.
Of all the different types of assets we analyzed, DICOM exposures arguably represent the greatest security risk due to the protocol’s vulnerabilities and the sensitive nature of the data involved. They are also relatively easy to discover on the public internet with simple scanning tools – even more so for sophisticated threat actors. In light of this, it is incredibly concerning that they make up the largest portion of exposures we observed. A top priority for these organizations should be to secure them from public internet access.
EMR/EHR Systems
The second largest category of exposed medical assets we found were login pages for Electronic Medical Records (EMRs) and Electronic Health Records (EHRs). Although the terms are often used interchangeably, there is a slight difference: EMRs typically refer to digital versions of paper charts used within a single healthcare practice, while EHRs are more comprehensive and can be shared across different healthcare providers. Despite this distinction, from a security perspective, they share similar risks.
Both EMRs and EHRs are web-based software applications commonly used by hospitals to store sensitive patient information, such as medical histories, clinical results, and insurance details. Patients also use these platforms to communicate with healthcare providers, schedule appointments, and make payments. In the U.S., under the American Recovery and Reinvestment Act of 2009, federal mandates were passed that required both public and private healthcare providers to adopt electronic medical records by January 2014 to maintain their Medicare and Medicaid reimbursement levels. As a result, the use of digitized record systems has surged – not just in the U.S., but worldwide.
We observed 4,031 instances of publicly accessible EMR and EHR systems, specifically login interfaces over HTTP. Epic’s EMR solution was the most common platform, followed by others like the open-source OpenMRS and HospitalRun projects, both built to help increase EMR adoption in developing countries. Unlike DICOM servers, which should never be publicly accessible, EMRs and EHRs are designed to be available online for patient access. So why include them in this study along with DICOM?
EMRs and EHRs are among the most frequently targeted assets in healthcare data breaches due to the vast amount of protected health information they store, including social security numbers, biometric data, contact information, and medical images—valuable data for malicious actors looking to profit on the dark web.
Table 2: Most commonly exposed EMR/EHR platforms
| Application |
Host Count |
| Epic EMR |
3678 |
| MyHealthcare OPD EMR |
106 |
| OpenMRS |
81 |
| zHealth EHR |
59 |
| Glenwood Systems Glace EMR |
27 |
| HospitalRun EHR |
4 |
Again, these login interfaces are designed for public access; however, because they control access to remote servers containing valuable data, any security weaknesses or misconfigurations can make them susceptible to attacks like brute force attempts or credential theft. Unfortunately, the extent of these security measures often depends on the software vendor. Anecdotally, many EMR and EHR products do not implement multi-factor authentication or VPN tunneling as standard features, and users are left to implement their own security setups. On a positive note, Epic does support MFA for its EMR solution; however, there is still a ways to go before this becomes the standard among EMR software vendors.
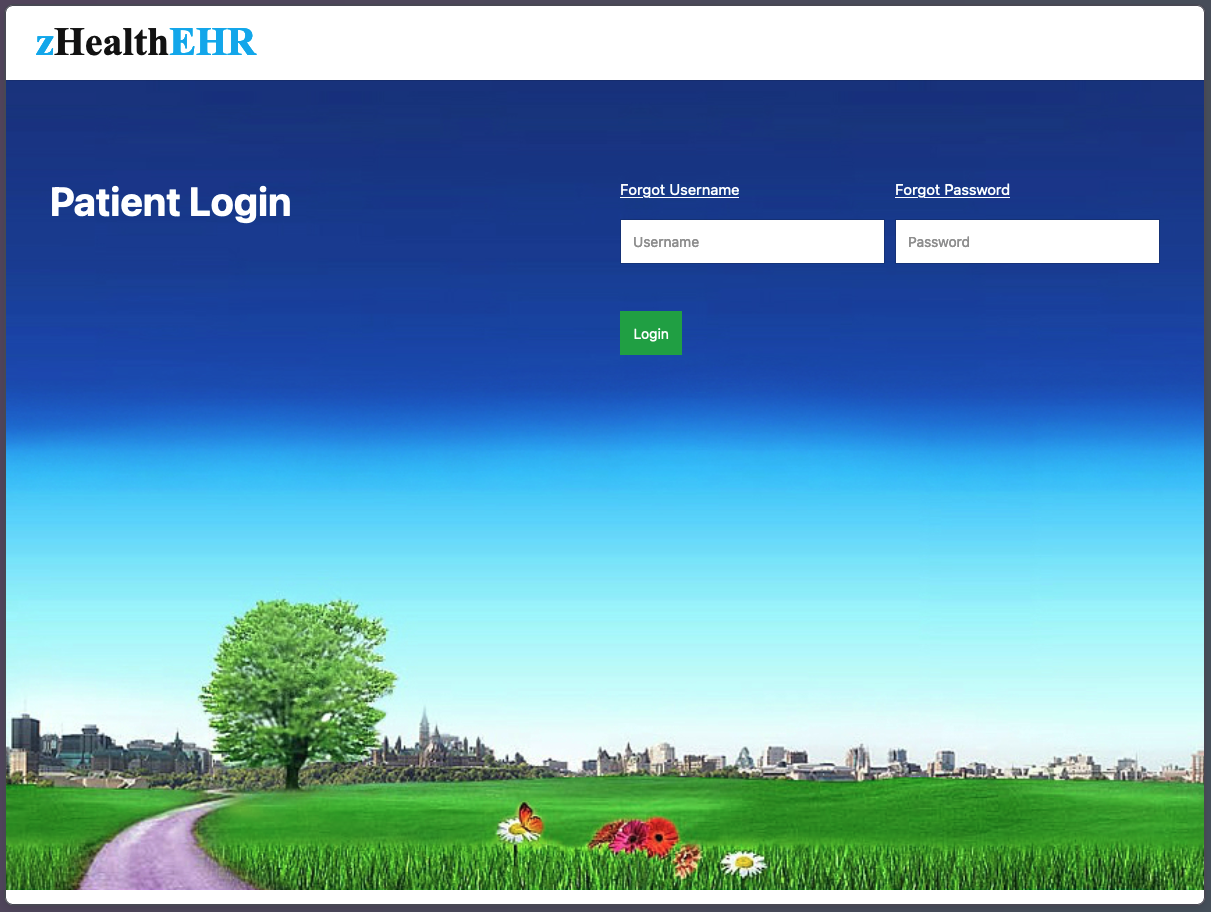
Exposed zHealth EHR Login Portal
To secure EMR and EHR data, the U.S. Department of Health and Human Services (HHS) recommends connecting to platforms via a VPN with MFA for applications that face the internet, particularly those that expose Remote Desktop Protocol (RDP) services and other remote access tools. It’s also highly recommended to audit your EMR/EHR tools for any data encryption blind spots while it is being exchanged between your organization’s network to external cloud applications. These measures add an extra layer of protection against unauthorized access. Censys did not evaluate these devices for the presence of MFA or other controls.
PACS
PACS, or “Picture Archiving and Communication System,” is a technology used to store, manage, and access medical images, which are typically in DICOM format. PACS and DICOM are closely connected, as PACS relies on the DICOM protocol to handle the transmission and storage of these images.
In a typical setup, medical imaging hardware like MRI or CT scanners generate images in DICOM format, which are then transmitted to a PACS server. The PACS server stores these images and allows them to be accessed and viewed through DICOM-compatible software.
We observed 2,530 exposures of PACS server login portals on the public internet – the most popular of which were Intelerad’s IntelePACS solution and Konica Minolta’s Exa PACS.
Table 3: Most commonly exposed PACS interfaces
| Application |
Host Count |
| Intelerad IntelePACS |
625 |
| Konica Minolta Exa PACS |
503 |
| IMAGE Information Systems iQ-WEB |
209 |
| MedicalExpo ECS Imaging |
141 |
| Lifetrack PACS |
115 |
| ResolutionMD PACS |
71 |
| OptosAdvance Image Management |
68 |
| sepStream PACS |
49 |
| Santesoft Sante PACS Server |
31 |
| Softneta MedDream PACS |
29 |
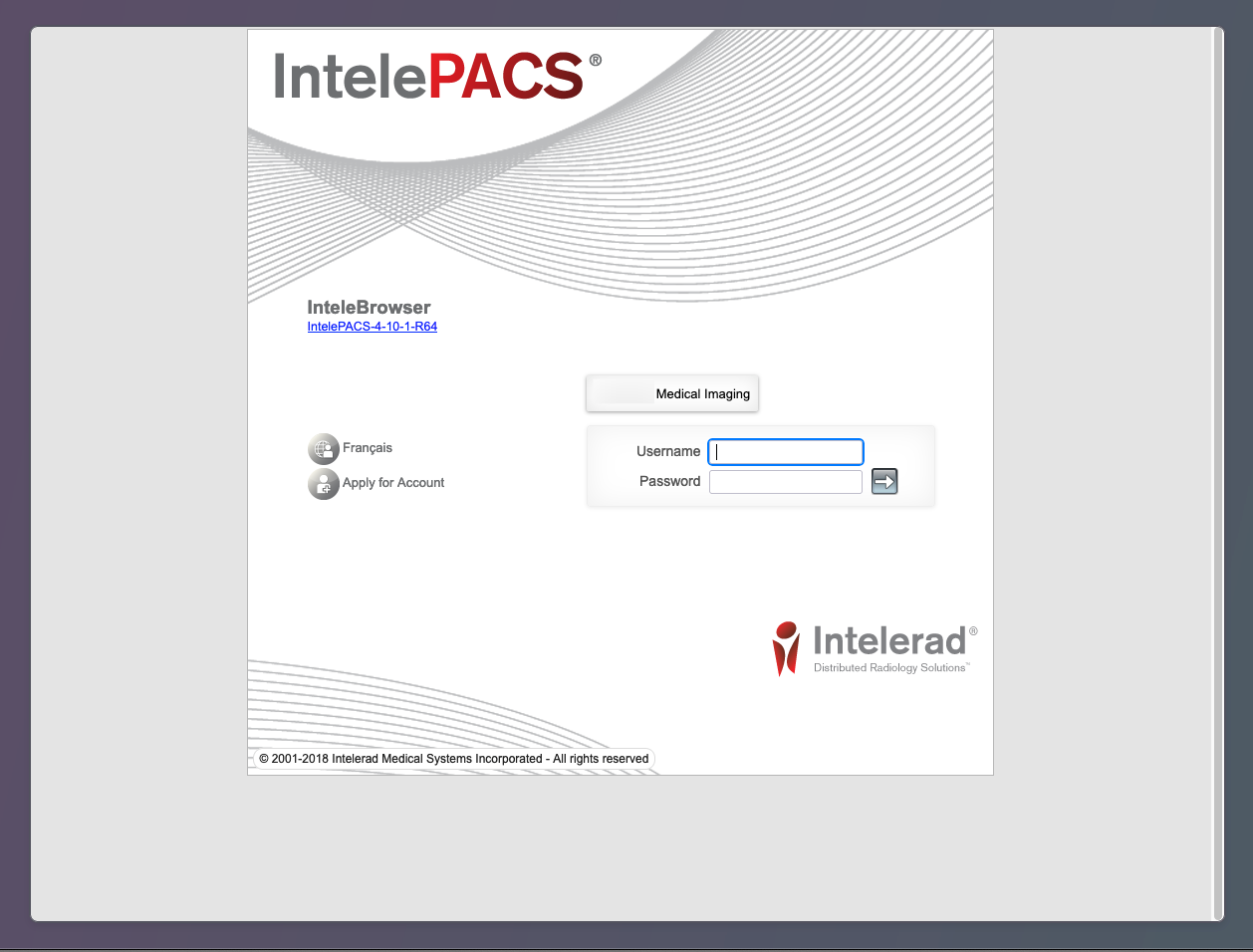
Example PACS login page exposing ownership details (redacted)
Similar to DICOM exposures, PACS exposures likely result from organizations prioritizing accessibility over security – or, potentially not even being aware that an asset is exposed. Any security weaknesses in a single login gateway could be enough for a threat actor to gain unauthorized access and potentially compromise a connected database of sensitive data.
Given the increased targeting of PHI and the significant financial and regulatory costs of a breach, there is simply no good reason for not securing these servers behind managed firewalls or VPNs.
Data Integration Systems
Healthcare organizations must manage the flow of large volumes of data between databases, EHRs, machinery, hardware, and the various interactions between practitioners and patients. Data integration systems have emerged to streamline this process and facilitate smoother data exchanges while maintaining compatibility with a range of data standards.
All of the data integration system exposures we identified involved NextGen Healthcare’s Mirth Connect tool, a popular data integration platform that refers to itself as “the swiss army knife of healthcare integration.” Approximately 18% of the total exposures we identified—2,520 hosts—were Mirth Connect login pages (excluding honeypots).
In May, CISA issued a warning about active exploitation of a year-old vulnerability (CVE-2023-43208) in Mirth Connect, which allowed unauthenticated attackers to compromise login gateways and access sensitive healthcare data.
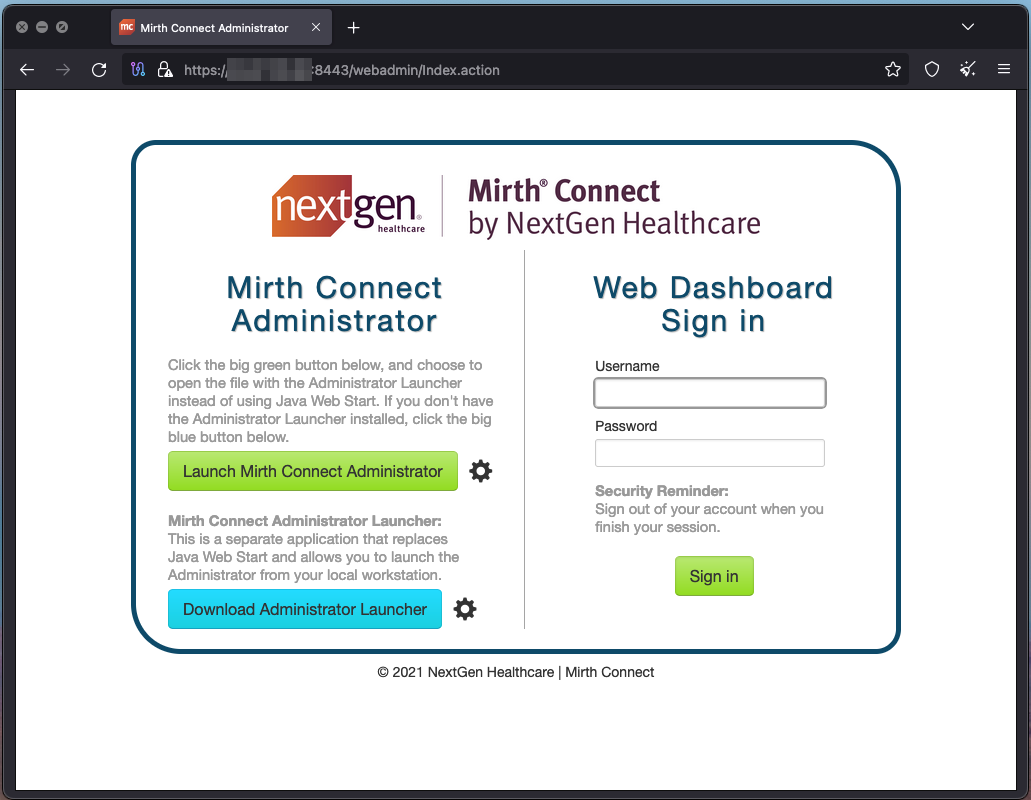
Example Exposed Mirth Connect Administrator interface
In Q1 of 2024, Microsoft reported that nation-state and cybercrime ransomware actors were exploiting vulnerabilities in Mirth Connect (CVE-2023-37679, CVE-2023-43208) and other flaws as common entry points into networks.
Incidents like this highlight the critical importance of measures like MFA for securing login gateways– particularly when they guard sensitive healthcare data. Like EMR/EHR portals, Mirth Connect is designed to be web-accessible but should not permit unrestricted remote access. Even if not directly vulnerable to these known exploits, any security weaknesses in the gateway’s configuration like default credentials or authentication bugs can be leveraged by attackers to gain unauthorized access.
Geographic and Network Distribution
Almost half of these exposures (6,884 hosts) are in the U.S., with India accounting for another 10.5%. This is likely owing to the large, decentralized nature of the U.S. healthcare system, and to the enforcement of federal mandates for U.S. practitioners to use electronic medical record systems.
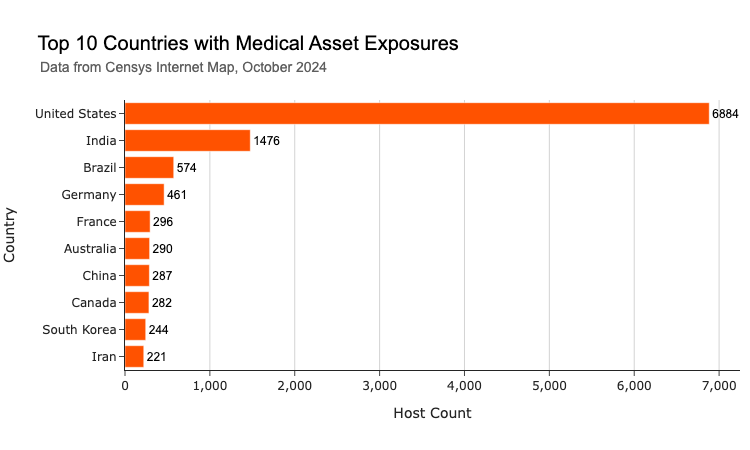
The United Kingdom, which hosts around 200 publicly available healthcare technologies, is notably absent from the top 10. This smaller footprint may reflect the more centralized nature of the U.K.’s healthcare infrastructure, where services are consolidated under fewer organizations. Stricter regulations on data protection may also be a factor resulting in fewer publicly accessible systems compared to the decentralized landscape in the U.S.
When it comes to network exposure, what’s interesting is that while many of these systems are hosted on major cloud platforms like AWS, Microsoft Azure, Cloudflare, and Google Cloud, we’re also seeing a number on proprietary healthcare networks like Epic’s Epic Hosting service (AS10747) and Konica Minolta’s managed All Covered infrastructure (AS393571).
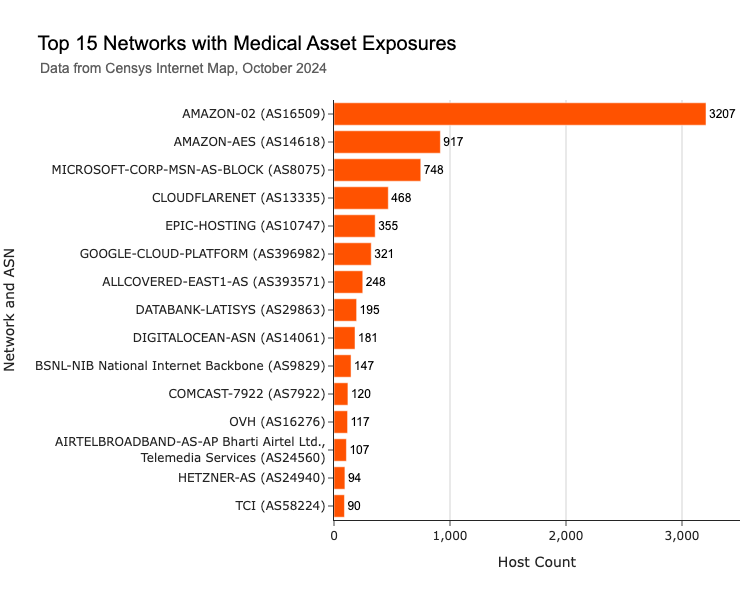
Another interesting detail is the presence of exposed healthcare systems on various residential and consumer ISPs. Notable examples include Bharat Sanchar Nigam Limited (AS9829) in India, Comcast (AS7922) in the U.S., and Airtel (AS24560) in India, along with the Telecommunication Company of Iran (AS58224). It’s possible that these belong to small to midsize organizations such as private practices and smaller specialized clinics. The use of residential ISPs for hosting critical infrastructure instead of more secure enterprise or cloud networks raises questions about the level of security and IT infrastructure in these setups. Smaller organizations can be more susceptible to attack because they are often less prepared to defend against sophisticated methods.
Outreach and Responsible Disclosure
Censys’s mission is to make the internet a more secure place for everyone. This goal drives our commitment to responsible disclosure when identifying exposed systems – particularly those in the critical infrastructure sector. As part of this research, we made every effort to attribute each device or web asset to the appropriate organization(s) and disseminate exposure notifications to their security contacts. By providing these organizations with visibility into their external attack surface, we aim to help them strengthen their security posture and resilience against malicious attacks. Our scanning perspective offers a valuable exposure inventory that organizations can use to better understand and prioritize potential risks.
Suggestions for Strengthening Healthcare Networks
Healthcare organizations and policymakers can take several key steps to strengthen healthcare networks and improve the management of external exposures. First, the critical importance of implementing robust access controls, such as multi-factor authentication, is hard to exaggerate. This is a must for securing sensitive systems like EMR/EHR platforms that must be accessible over the web. Additionally, using protective barriers like firewalls to restrict malicious traffic to critical systems can significantly reduce the risk of unauthorized access – particularly “high-risk” ports exposing remote access tools (SSH, RDP, etc) that are frequently targeted by attackers. Lastly, continuous monitoring of the external attack surface with tools like automated scanning platforms can help organizations quickly identify and remediate potential exposures before they can be exploited.
References