Summary
- Sisense, a BI and analytics platform trusted by many enterprises, experienced a data breach, with a notification to customers sent on April 10, 2024.
- Few details have been made publicly available, but from what we know based on suggested mitigations for customers, this incident could have widespread impacts across a variety of industries.
- Censys observes Sisense instances across the US, UK, Canada, and other countries, and impacted organizations in Sales and Marketing, Finance and Insurance, and Healthcare and Social Assistance, among others.
Introduction
On Wednesday, April 10, 2024, Brian Krebs posted a screenshot of a message sent to Sisense customers reporting that “certain Sisense company information may have been made available” to unauthorized parties via “a restricted access server.” Further, the message urged recipients to “promptly rotate any credentials” used in their Sisense applications.
Sisense, a business intelligence and analytics platform, boasts a number of prominent customers, including Nasdaq, PagerDuty, and Air Canada, according to their website.
The following day, CISA released a brief advisory urging Sisense customers to reset any credentials exposed to or used to access Sisense services.
Minimal details about the scope of the breach were initially available, and though additional information has emerged, we wanted to understand more about the potential impact of this incident by examining the Sisense instances visible to Censys.
The Censys View
Sisense documentation reveals that they offer several deployment options for their analytics tooling, including self-hosted installations and managed cloud hosting. While self-hosted instances could be tricky to identify given that they may be behind a firewall or on RFC1918 IP space, we suspected that the cloud–hosted instances might be more straightforward to find.
We began by using Censys data to perform subdomain enumeration, which provided us with a list of *.sisense.com sites recently seen by Censys scanners. Reviewing the results, we discovered names of well-known organizations and decided to investigate further.
Using our list of subdomains, we generated a screenshot for each one to facilitate analysis and better understand what organization a Sisense site might belong to, as many included customized brand logos.

Sample screenshot collection output
Of the roughly 500 endpoints we obtained screenshots for, at least 25 appear to belong to Sisense itself (e.g., community, dev, and docs sites). Many sites displayed the default Sisense login (shown above), which, in some cases, made it more challenging to determine an owner despite the subdomain.
There were often several companies with names similar to a subdomain in question. Absent a company logo on the Sisense login page or a redirect to a branded SSO portal, we were often unable to confidently identify which company was responsible for a given Sisense instance.
Ultimately, we were able to identify owners for 120 Sisense instances, which we explore below. We are careful to note that the data below is not meant to be representative of the Sisense customer population, but rather a look at some of the industries that could potentially see impact as a result of the incident.
Industry and Geography
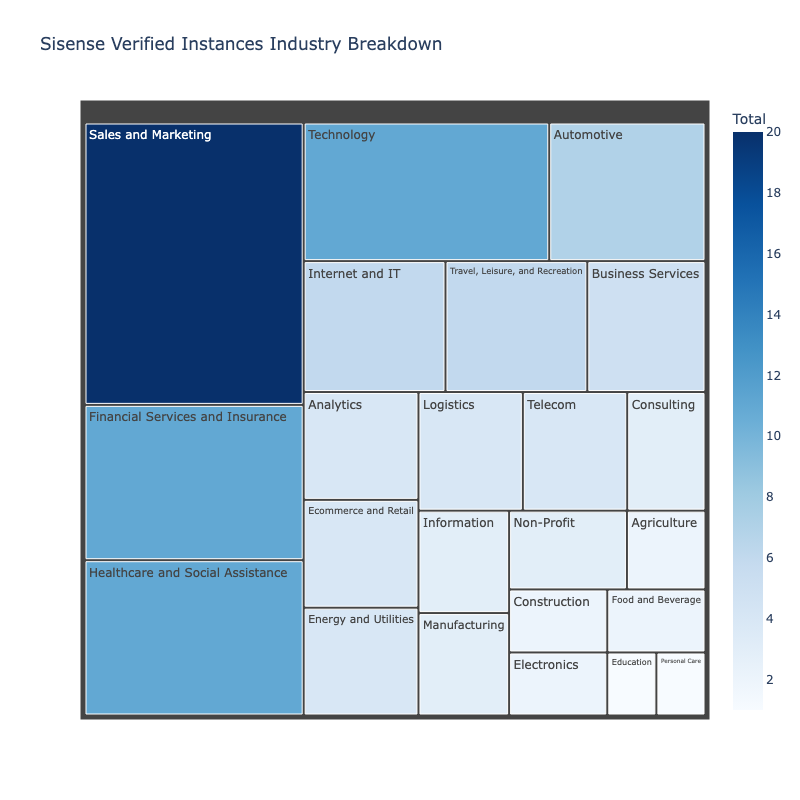
Sales and Marketing, Finance and Insurance, and Healthcare and Social Assistance were the largest categories of organizations we identified in our data. We also note the presence of industries like Internet and IT, Technology, Logistics, and Energy and Utilities.
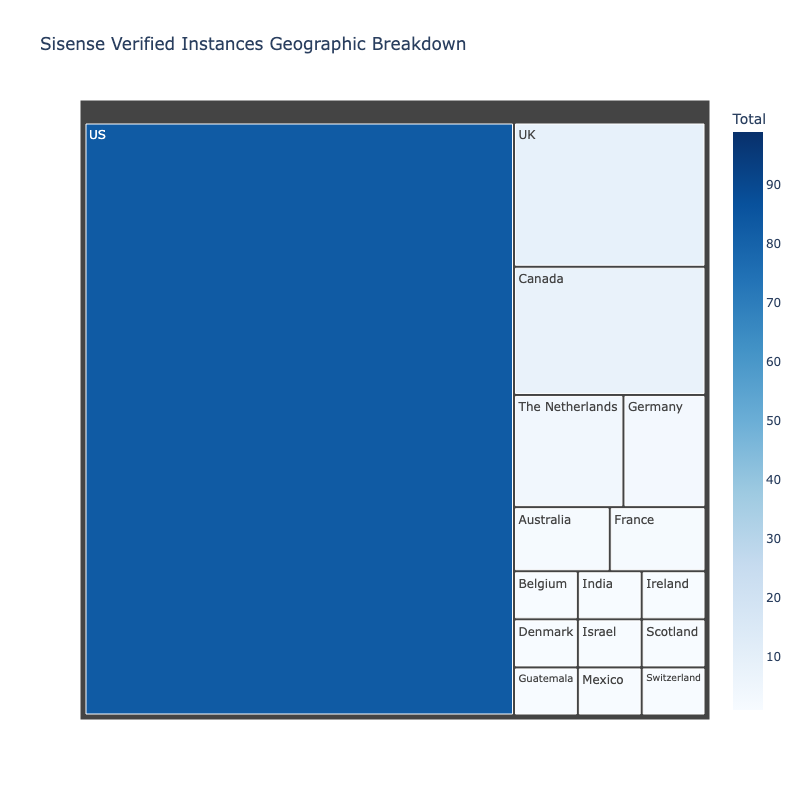
The majority of instances we discovered and identified owners belong to US-based organizations, though we saw several instances from organizations based in the UK, Canada, The Netherlands, and other countries.
Many of the organizations in the US appear to have an international presence–so while they may be headquartered in the US, they have operations overseas as well.
Conclusion
While the industry and geographic breakdowns here represent a subset of Sisense customers, our findings are somewhat reminiscent of our study of MOVEit, the managed file transfer tool exploited by Clop in a campaign that began in the summer of 2023.
Back office software, especially software that manages or otherwise holds data about a company’s customers, continues to be a rich target for threat actors.