Date of Disclosure: 2024-10-02
A total of 14 vulnerabilities affecting DrayTek Vigor routers were disclosed yesterday in a report by Forescout. The vulnerabilities were scored as follows: 2 critical severity, 9 high severity, and 3 medium severity. Most of these vulnerabilities are found in DrayTek VigorConnect, the web control interface for Vigor routers.
Let’s examine the most severe vulnerability, CVE-2024-41592, which has been assigned the maximum CVSS score of 10.0. It’s a buffer overflow in the GetCGI() function of the VigorConnect Web UI that can be triggered by sending a specially crafted, excessively long query string to any of the CGI pages.
When exploited individually, CVE-2024-41592 allows a threat actor to potentially cause a Denial of Service. However, if chained with CVE-2024-41585—the second-most severe vulnerability, which is an OS command injection flaw—it is possible to gain remote root access to the host operating system. This exploit chain only affects Vigor router models 3910 and 3912.
If a router is compromised, a threat actor could leverage it to perform network reconnaissance and lateral movement to other devices within the network, deploy malware, or launch botnet activity.
| Field |
Details |
| CVE-ID |
CVE-2024-41592 – CVSS 10.0 (Critical) |
| Vulnerability Description |
Buffer Overflow in the “GetCGI()” function of the VigorConnect Web UI could lead to DoS or RCE |
| Date of Disclosure |
October 2, 2024 |
| Affected Assets |
DrayTek VigorConnect, the web-based control interface for Vigor Routers |
| Vulnerable Firmware Versions |
Vigor1000B, Vigor2962, Vigor3910, Vigor3912, Vigor165, Vigor166, Vigor2135, Vigor2763, Vigor2765, Vigor2766, Vigor2865, Vigor2866, Vigor2915, Vigor2620, VigorLTE200, Vigor2133, Vigor2762, Vigor2832, Vigor2860, Vigor2925, Vigor2862, Vigor2926, Vigor2952, Vigor3220 |
| PoC Available? |
Yes |
| Exploitation Status |
Currently no known exploitation of these newly disclosed CVEs, but note 4 older CVEs affecting various DrayTek routers are in CISA KEV. |
| Patch Status |
Patches are available for all affected devices, including EOL firmware versions (see table near the end for a full list of patches) |
DrayTek is a Taiwan-based network equipment manufacturer. Their Vigor routers are used by small to medium sized businesses and consumers worldwide.
Vigor routers have been targeted by exploitation in the past. Just last month, the FBI reported on Chinese-sponsored botnet activity that leveraged 3 older CVEs in DrayTek routers. Last year, the Chinese state-sponsored actor Volt Typhoon was observed exploiting exposed SOHO networking equipment to carry out attacks, including DrayTek devices.
Example VigorConnect Admin Interface Exposed on the Web
Networking admin interfaces are commonly targeted as initial access points by threat actors. When exposed on the public internet, these interfaces are easily discoverable and often exploited due to the wealth of information they provide. Compromising an admin interface can grant unauthorized access to larger networks, making them valuable for network reconnaissance and further attacks. CISA has issued directives in the past, such as Binding Operational DIrective 23-02, requiring Federal agencies to secure these networked admin interfaces from the public internet.
These administrative interfaces shouldn’t be directly accessible online outside of local networks, and should instead be protected using access controls such as firewalls or VPNs.
Let’s explore the digital footprint of exposed DrayTek Vigor routers.
Censys Perspective
As of this writing, Censys has identified 751,801 exposed DrayTek Vigor routers online. These devices are predominantly located in the United Kingdom, followed by Vietnam, the Netherlands, and Taiwan from our perspective, which aligns with findings from the original report.
Out of these, 421,476 devices are exposing the VigorConnect admin UI on the web.
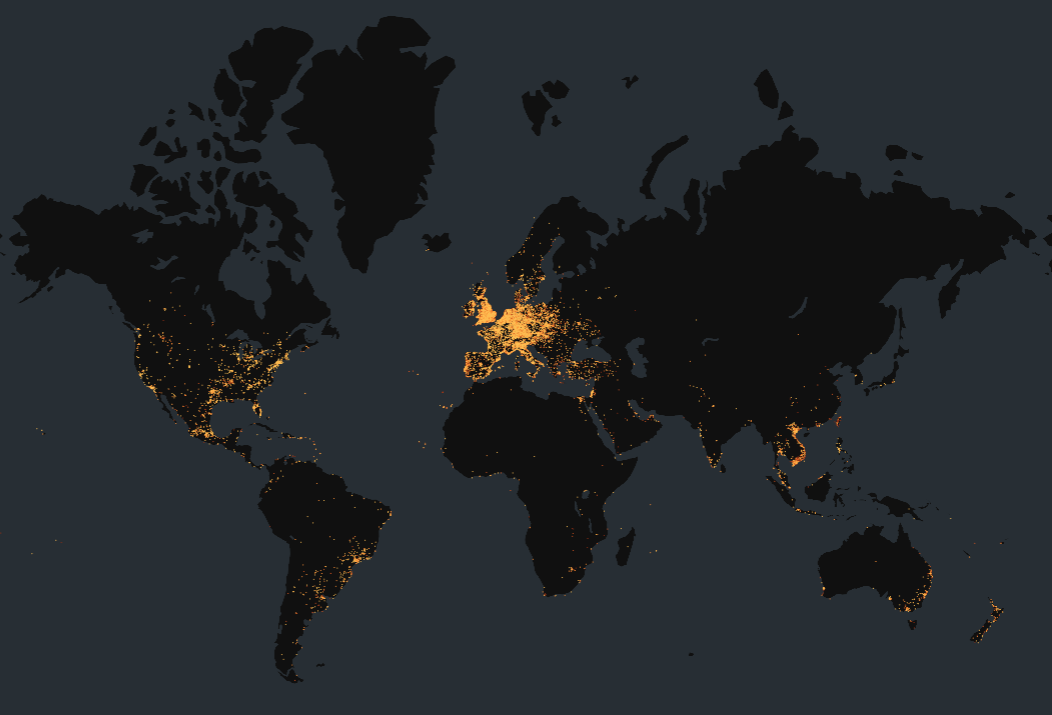
Map of all publicly exposed VigorConnect Router admin interfaces on the web (created with kepler.gl)
The networks with the largest concentrations of these admin interfaces are a mix of large national ISPs and regional telecom providers. Leading the list is Taiwan-based HINET, which makes sense given that DrayTek is a Taiwanese company.
| ASN |
AS_Name |
Organization |
Country |
Scale |
Host Count |
| 3462 |
HINET Data Communication Business Group |
HINET |
Taiwan |
Major ISP |
41,969 |
| 31655 |
ASN-GAMMATELECOM |
Gamma Telecom |
U.K. |
Significant Telecom Provider |
35,866 |
| 2856 |
BT-UK-AS BTnet UK Regional network |
British Telecommunications |
U.K. |
Major ISP |
31,959 |
| 45899 |
VNPT-AS-VN VNPT Corp |
Vietnam Posts and Telecommunications Group |
Vietnam |
Major ISP |
31,561 |
| 5413 |
AS5413 |
Daisy Communications |
U.K. |
Significant Telecom Provider |
21,275 |
| 13037 |
ZEN-AS Zen Internet – UK |
Zen Internet |
U.K. |
Medium-sized ISP |
13,147 |
| 18403 |
FPT-AS-AP FPT Telecom Company |
FPT Telecom |
Vietnam |
Major ISP |
12,132 |
| 7552 |
VIETEL-AS-AP Viettel Group |
Viettel Group |
Vietnam |
Major ISP |
11,756 |
| 1136 |
KPN KPN National |
KPN |
Netherlands |
Major ISP |
9,921 |
| 3320 |
DTAG Internet service provider operations |
Deutsche Telekom AG |
Germany |
Major ISP |
7,732 |
It’s important to note that not all observed routers are necessarily vulnerable, as specific device versions were not available. To identify exposed VigorConnect admin page instances in your networks, you can use the following Censys queries:
Censys Search Query: [Link]
services: (http.response.status_code=200 and http.request.uri:"/weblogin.htm" and (http.response.html_title:"Vigor" or http.response.favicons.md5_hash="208b1c5af9e2cc7d46e3ec5bf4d12001"))
Censys ASM Query: [Link]
host.services: (http.response.status_code=200 and http.request.uri:"/weblogin.htm" and (http.response.html_title:"Vigor" or http.response.favicons.md5_hash="208b1c5af9e2cc7d46e3ec5bf4d12001")) or web_entity.instances: (http.response.status_code=200 and http.request.uri:"/weblogin.htm" and (http.response.html_title:"Vigor" or http.response.favicons.md5_hash="208b1c5af9e2cc7d46e3ec5bf4d12001"))
Censys Risk Query: [Link]
risks.name="Exposed DrayTek Vigor Router"
What Can be Done?
It’s recommended to patch your DrayTek firmware according to your device model, either through the web interface or using the Firmware Upgrade utility. It’s good practice to back up your config before patching.
It’s also wise to restrict your VigorConnect admin web UIs from public remote access and enable two-factor authentication to further lower the risk of unauthorized access.
| Device Model |
Fixed Versions |
EoL? |
| Vigor1000B, Vigor2962, Vigor3910 |
4.3.2.8 and 4.4.3.1 |
No |
| Vigor3912 |
4.3.6.1 |
No |
| Vigor165, Vigor166 |
4.2.7 |
No |
| Vigor2135, Vigor2763, Vigor2765, Vigor2766 |
4.4.5.1 |
No |
| Vigor2865, Vigor2866, Vigor2915 |
4.4.5.3 |
No |
| Vigor2620, VigorLTE200 |
3.9.8.9 |
Yes |
| Vigor2133, Vigor2762, Vigor2832 |
3.9.9 |
Yes |
| Vigor2860, Vigor2925 |
3.9.8 |
Yes |
| Vigor2862, Vigor2926 |
3.9.9.5 |
Yes |
| Vigor2952, Vigor3220 |
3.9.8.2 |
Yes |
Source: Forescout (p.11)
References