Updates
April 15, 2023
- As stated previously, results are still coming in for the number of hosts running this MSMQ service. As of today, we have observed 465,263 MQMQ servers open to the internet.
- We have updated the graphs and metrics below to reflect this new set of hosts.
Summary
- CVE-2023-21554 is shaping up to be a very big problem if not dealt with quickly. This affects almost every version of the Windows OS running the Microsoft Messaging Queuing service.
- Censys has observed
383,554 465,263 hosts running the obscure MSMQ service that this vulnerability targets.
- Censys Search query: services.service_name=MSMQ
Introduction
On April 12th, 2023, Microsoft released a slew of new patches for its Windows operating system, one of which was to fix CVE-2023-21554, a remotely-exploitable vulnerability in the obscure Windows Message Queuing (MSMQ) service that can lead to remote code execution (RCE). The original analysis came from researchers Wayne Low of Fortinet and Haifei Li of Check Point, where they disclosed some details and general protection information about the vulnerability.
While this service is not enabled by default on Windows servers, Check Point noted that some enterprise applications (such as Microsoft Exchange Server) will automatically start and leave it running in the background, meaning a system may be running this service without an administrator ever knowing.
The good news is that no known public exploit is available for this vulnerability. The bad news is that the advisory mentions that exploiting this service requires zero authentication and can be triggered with a single TCP packet (which may mean the exploit could be found with a bit of time and fuzzing). In other words: no known public exploit is available for this vulnerability….YET!
“…an attacker could gain control of the process through just one packet to the 1801/tcp port with the exploit” – Check Point
If the news, advisories, and CVSS score are accurate, it is only a matter of time before we see something, especially given that it is such a high-value target with a reportedly low level of complexity to execute. If an exploit is dropped, there is no doubt that threat actors will immediately start a proverbial space race to own these devices.
Whether the service is firewalled from the internet or exposed publicly for a good reason, individuals and organizations must check whether the service is running on their servers. Administrators must ensure the latest Microsoft patches have been applied if the service is intentionally enabled.
Identifying
By default, this service listens on TCP port 1801. It uses a proprietary binary protocol for data communication, but Microsoft documentation luckily includes examples of an MSMQ connection request and an MSMQ connection response. Using this information, an analyst can quickly check to determine if there is a valid MSMQ service listening on the other end by using “netcat”, with the following command:
$ echo H4sIAAAAAAACAxM4wM3g4+kfZMPEwPAfCBgYmBguRhSHBkycOtVz+rZngq/UjrF3nnX2sRTsd3GdUDFh3oI/fqfuyQowM4yCEQ4AzGv6OzwCAAA= \
|base64 -d|zcat -|\
netcat $IP_ADDRESS 1801 |\
hexdump -C
If the output looks similar to the following hex dump, then the server is running MSMQ:
00000000 10 5a 0b 00 4c 49 4f 52 3c 02 00 00 ff ff ff ff |.Z..LIOR<.......|
00000010 00 00 12 00 d1 58 73 55 50 91 95 95 49 97 b6 e6 |.....XsUP...I...|
00000000 10 5a 0b 00 4c 49 4f 52 3c 02 00 00 ff ff ff ff |.Z..LIOR<.......|
00000010 00 00 12 00 d1 58 73 55 50 91 95 95 49 97 b6 e6 |.....XsUP...I...|
Alternatively, a user can check the local Windows system to determine whether the service is running by going to the Start Menu, then Control Panel, and clicking on the “Programs and Features” section. There should be an option to “Turn Windows features on or off.” From this window, we can scroll down to find an entry labeled “Microsoft Message Queue (MSMQ) Server.” If these checkboxes are enabled, this means the service is running.
MSMQ Observations

Geographic View of MSMQ Services on the Internet (via kepler.gl)
While an exploit for this vulnerability has not been published as of April 14th, 2023, it is good to know what problems could exist and at what scale if one is made available in the near future.
Censys has found that since we deployed our MSMQ scanner (on the evening of February 12th), over 465,000 hosts have been observed running the MSMQ service. Below are the continents and top ten countries where this service has been observed. Results are still trickling in, but we have seen that Hong Kong is the most significant user of MSMQ, with over 35% (167,418 hosts) of the total MSMQ hosts running this service on the internet.
| Hosts running MSMQ per Continent |
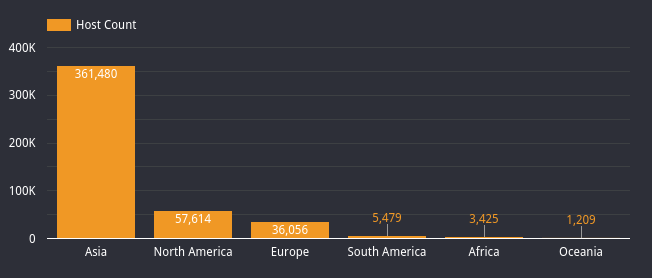 |
| Continent |
Host Count |
% |
| Asia |
361,480 |
77.69% |
| North America |
57,614 |
12.38% |
| Europe |
36,056 |
7.75% |
| South America |
5,479 |
1.18% |
| Africa |
3,425 |
0.74% |
| Oceania |
1,209 |
0.26% |
|
| Top 10 Countries Running MSMQ |
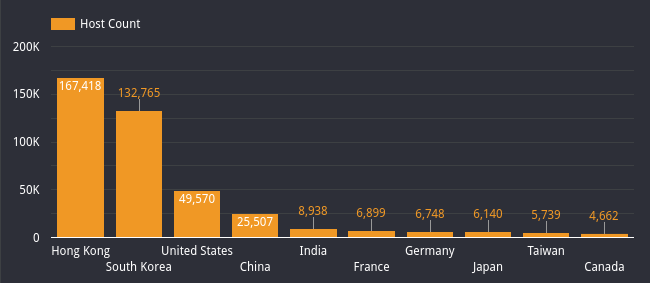 |
| Country |
Host Count |
% |
| Hong Kong |
167,418 |
35.98% |
| South Korea |
132,765 |
28.54% |
| United States |
49,570 |
10.65% |
| China |
25,507 |
5.48% |
| India |
8,938 |
1.92% |
| France |
6,899 |
1.48% |
| Germany |
6,748 |
1.45% |
| Japan |
6,140 |
1.32% |
| Taiwan |
5,739 |
1.23% |
| Canada |
4,662 |
1.00% |
|
As for the types of networks this service has been observed running in, we see a mix of enterprises, cloud hosting providers, and general broadband internet service providers. Here are the top ten autonomous systems and networks where we have seen MSMQ services listening (Note: this does not mean they are vulnerable, just that this MSMQ service is running):
| Top 10 Autonomous Systems Running MSMQ |
 |
| Autonomous System |
Name |
Host Count |
% |
| 134548 |
DXTL-HK |
102,246 |
21.98% |
| 4766 |
KIXS-AS-KR |
67,403 |
14.49% |
| 134175 |
SH2206-AP-SILVERCORP-INTL |
44,629 |
9.59% |
| 3786 |
LGDACOM LG DACOM Corporation |
43,139 |
9.27% |
| 9318 |
SKB-AS SK BROADBAND |
18,217 |
3.92% |
| 135097 |
MYCLOUD-AS-AP |
9,533 |
2.05% |
| 16276 |
OVH |
7,649 |
1.64% |
| 45090 |
TENCENT-NET-AP |
5,661 |
1.22% |
| 58658 |
DXTL-AS-AP DXTL |
5,599 |
1.20% |
| 37963 |
ALIBABA-CN-NET |
5,549 |
1.19% |
|
GreyNoise (an organization that collects and analyzes data about hosts on the internet that attempt to scan or exploit vulnerabilities) has seen a recent uptick in scanning and recon activity around the MSMQ service. In the last three days, GreyNoise has noted 592 unique IP addresses attempting to find MSMQ services (a few of those are probably Censys :)).
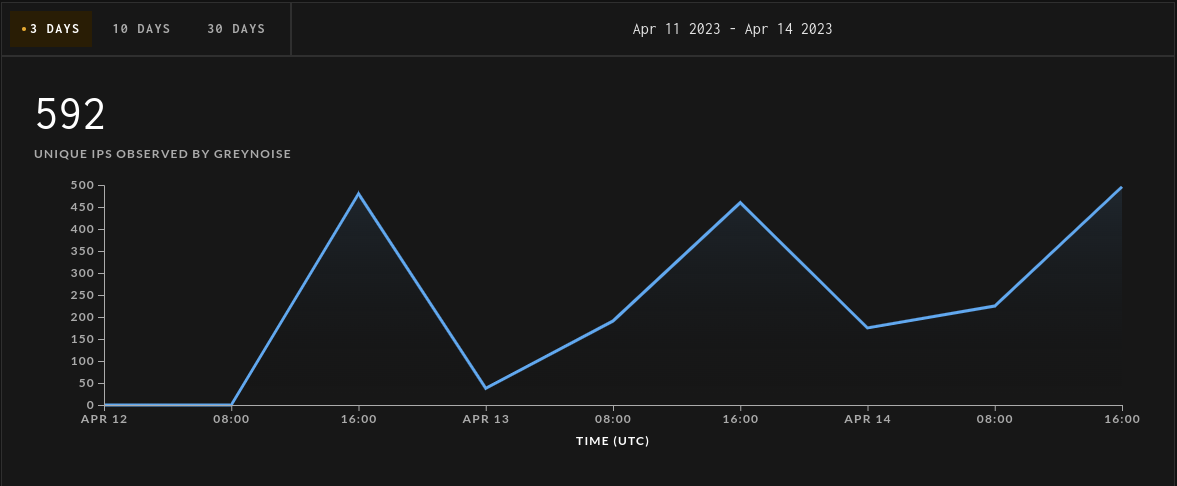
(GreyNoise’s view of internet hosts scanning for MSMQ servers)