Censys has visibility into 19.5k end-of-life Cisco devices for individuals and small businesses on the internet, which may be vulnerable to a new attack. And to make matters worse, there will not be an official fix.
Introduction
On January 11th, 2023, some details emerged about a critical vulnerability in Cisco’s small-business series of routers. This flaw is currently being tracked via CVE-2023-20025 and was discovered by researcher Hou Liuyang at Qihoo360 (via Bleeping Computer). Cisco noted that an exploit is floating around the internet, although it has not been made publicly available. But the good news is that Cisco is unaware of these exploits being used maliciously.
The vulnerability is apparently due to improper user input validation on the web-based administration tool, allowing unauthenticated clients to bypass authentication and obtain administrative privileges that can execute arbitrary commands.
The vulnerability exists in four different Cisco small business routers:
Cisco stated in their advisory that they have “not released software updates to address the vulnerabilities described in [the] advisory.” and that “there are no workarounds that address these vulnerabilities.”. Given that these devices are End of Life (meaning they are entirely unsupported by Cisco), there will not be an official fix for the vulnerabilities. If any of these devices are directly connected to the internet with the web administration interface enabled, they are vulnerable and will continue to be.
Visibility
By looking at only HTTP services that include the model numbers in either the “WWW-Authenticate” response header or an HTTPS service with a matching TLS organizational unit, Censys search results show around 20,000 hosts have indicators that they are potentially vulnerable to this attack.
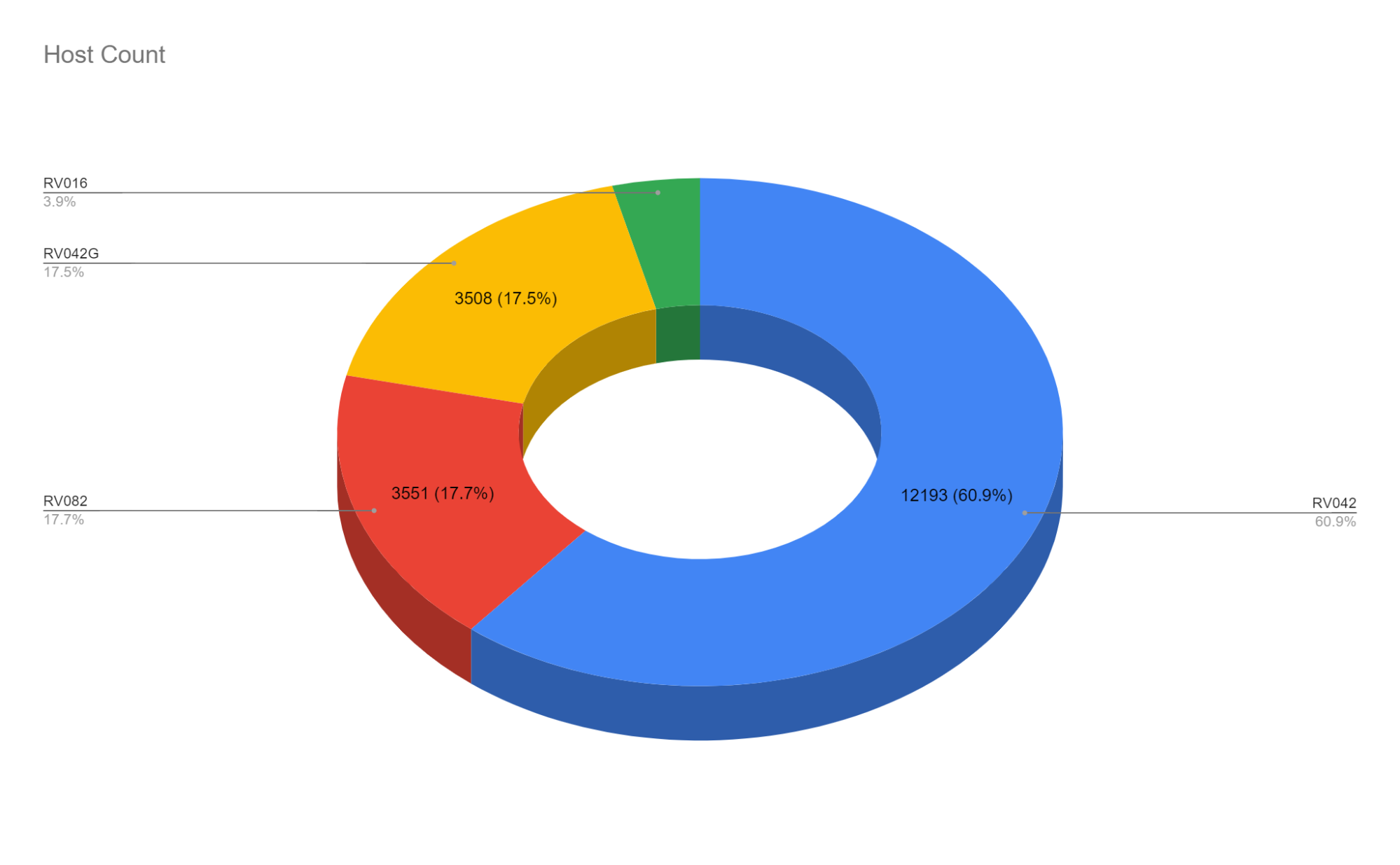
Of the four vulnerable models, the RV042 dominates the landscape, with over 12k hosts exposed to the internet. The RV082 and RV042 with 3.5k hosts, while the RV016 trails behind with only 784 internet-exposed assets.
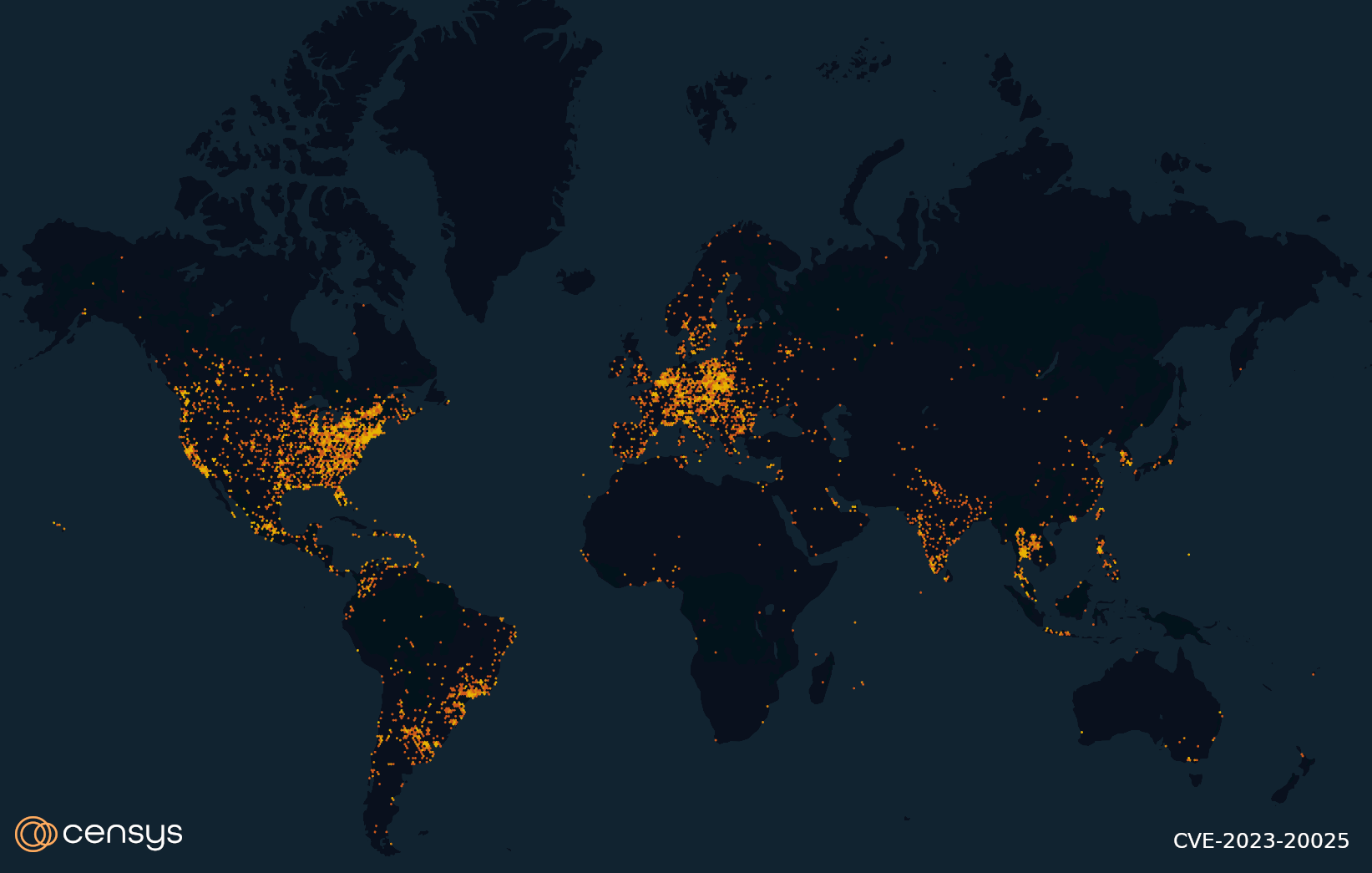
(Potentially vulnerable Cisco models)
Below are the top ten autonomous systems where these specific Cisco routers can be found. The reader will note that most of these autonomous systems are that of various residential internet service providers, meaning that small businesses and individuals are the most affected customer base. And while the businesses may be small, the number of these visible devices online can cause significant harm if this goes unnoticed.
| Top 10 Vulnerable Autonomous Systems |
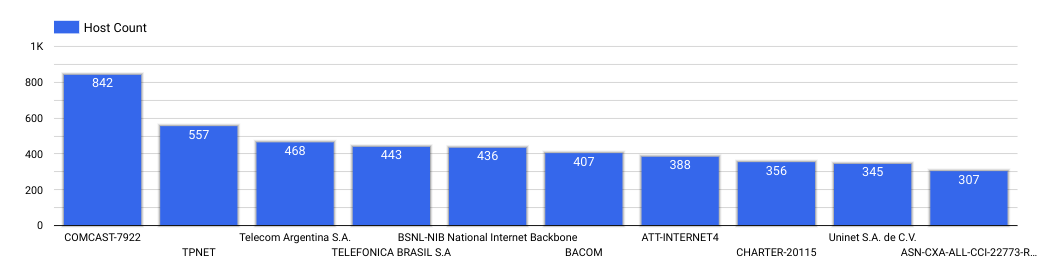 |
| AS Name |
Host Count |
| COMCAST-7922 |
842 |
| TPNET |
557 |
| Telecom Argentina S.A. |
468 |
| TELEFONICA BRASIL S.A |
443 |
| BSNL-NIB National Internet Backbone |
436 |
| BACOM |
407 |
| ATT-INTERNET4 |
388 |
| CHARTER-20115 |
356 |
| Uninet S.A. de C.V. |
345 |
| ASN-CXA-ALL-CCI-22773-RDC |
307 |
|