There has been a recent discussion regarding a vulnerability affecting specific Zyxel network devices (CVE-2023-28771), and it raises significant concerns due to thousands of these devices that can be found exposed online. Additionally, researchers at Rapid7 have conducted an analysis that essentially transforms this vulnerability into a scriptable attack. And as of May 25th, 2023, this vulnerability is reported as being mass exploited by the Mirai botnet.
While Internet Key Exchange (IKE) is the protocol used to initiate this exploit, it’s not a vulnerability in IKE itself, but it seems to be a result of this rogue debugging function that shouldn’t have made it into a production build of the firmware. But since IKE is the only known protocol where the path to this vulnerability can be triggered, it’s much more likely that only the Zyxel devices that are running IKE are actually vulnerable to this attack.
This vulnerability stems from a problematic logging function. Instead of employing a secure file handling mechanism by opening up a file handle and writing data to that handle, Zyxel chose a different approach: They constructed an “echo” command by incorporating user-controlled input data. This echo command is subsequently executed through a system() call, writing the output to a file in /tmp. This implementation introduces an OS command injection vector, as the command construction process can be influenced by user-controllable input, and there is no data sanitization.
This means all an attacker had to do was figure out how to trigger this logging condition in the code remotely. As it turns out, this logging code is reachable during the decoding process of an IKEv2 notify message, and since IKE runs over UDP, to trigger this, all a client has to do is send an IKE Notify message where the payload includes a simple OS command injection (i.e., “; cat /etc/shadow” or in the case of the Rapid7 analysis, pop a reverse shell using “/dev/tcp”).
According to the CVE, the following Zyxel devices and versions are vulnerable:
Among the 24,457 Zyxel devices we observed, it was found that a significant majority, approximately 86.72% (21,210 devices), was running the IKE protocol. This indicates that these devices are potentially susceptible to this particular vulnerability. On the other hand, only 3,247 devices, accounting for approximately 13.28% of the total, were not utilizing the IKE protocol and, therefore, may not be directly affected by this vulnerability.
We can view the list of hosts that may be vulnerable to this attack by using the following Censys search query:
(services.http.response.html_title={
"ATP100", "ATP200", "ATP500",
"ATP700", "ATP800", "USG FLEX 100",
"USG FLEX 100W", "USG FLEX 200",
"USG FLEX 50", "USG FLEX 700",
"VPN100", "VPN1000", "VPN300", "VPN50"
}
OR
same_service(
services.software.product:"usg310"
and
services.software.vendor:"Zyxel"
)
OR
same_service(
services.software.product:"usg100"
and
services.software.vendor:"Zyxel"
))
And if we only want to view the hosts which also have IKE running, we can append the following to the above search query: and services.service_name=IKE
These devices are deployed in all sorts of residential and business networks, both large and small. So the majority of networks these devices can be found in will be telecoms and other types of service providers. Still, unlike most of the vulnerabilities we discuss here at Censys, most of the Zyxel devices we see exposed to the internet are in Europe.
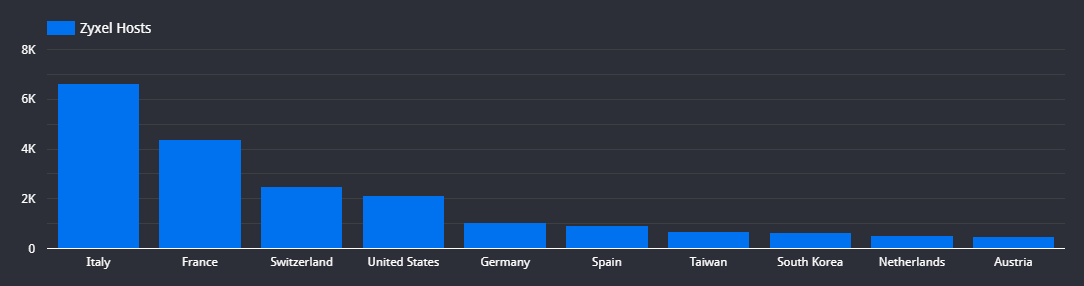
Primarily, these devices are prevalent within Italian ISPs such as Telecom Italia (AS3269) with 2,005 hosts, Vodafone (AS30722) with 885 hosts, and Fastweb (AS12874) with 826 hosts, resulting in a total of 6,645 devices deployed across Italy.
Additionally, they can also be found in France, with a total of 4,385 hosts distributed among notable ISPs like France Telecom (AS3215) with 1,563 hosts, along with business ISP SERVEURCOM (AS57809) with 599 hosts. Furthermore, we found that Switzerland accommodates 2,500 exposed Zyxel routers.
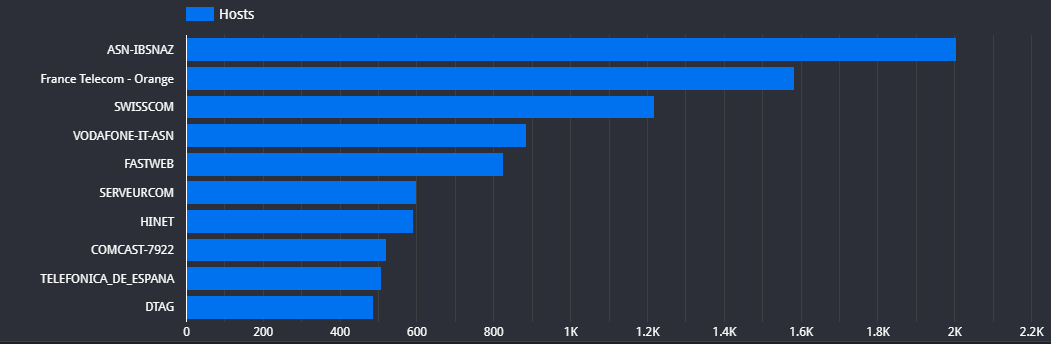
Below are the top-ten autonomous systems (network providers) with Zyxel routers that may potentially be vulnerable to this attack.
 |
| Autonomous System |
Hosts With IKE |
Hosts Without IKE |
Total Hosts |
| ASN-IBSNAZ |
1,532 |
473 |
2,005 |
| France Telecom |
1,349 |
234 |
1,583 |
| SWISSCOM |
1,161 |
58 |
1,219 |
| VODAFONE-IT-ASN |
791 |
94 |
885 |
| FASTWEB |
751 |
75 |
826 |
| SERVEURCOM |
520 |
79 |
599 |
| HINET |
515 |
77 |
592 |
| COMCAST-7922 |
490 |
32 |
522 |
| TELEFONICA_DE_ESPANA |
431 |
76 |
507 |
|