Last week, a security researcher known as “Janggggg” published a proof of concept (PoC) exploit for the latest “ProxyNotShell” vulnerabilities in Microsoft Exchange that were discovered in September.
ProxyNotShell is already confirmed to be actively exploited by a Chinese nation-state threat actor at the time of the vulnerability announcement by Microsoft. The attack was initially observed to be isolated to a single threat actor group and carried out on a small set of victims. Given the attack’s complexity and the vulnerability requiring valid credentials, there was a low expectation for this vulnerability to be exploited widely. Now that a PoC of the exploit is publicly available, we expect to see an uptick in the number of threat actors attempting to exploit ProxyNotShell flaws on hosts with weak credentials that remain accessible on the internet.
Background
ProxyNotShell is a variation of the exploit ProxyShell, which was first discovered in August 2021. The ProxyShell attack consists of three separate vulnerabilities chained together to achieve remote code execution, allowing attackers to establish a persistent foothold into your Exchange environment. It was first announced at Blackhat 2021 by security researcher, Orange Tsai. Due to the nature of its discovery, PoCs have been available since announcement, and it is still being actively exploited in the wild.
During the initial publication in August 2021, Censys identified over 175,300 hosts that ran the Exchange Simple Mail Transport Protocol (SMTP) service. Over 50,000 hosts have either been patched or removed external internet access as the count currently stands at over 135,000 hosts. Of the hosts running the Exchange SMTP service, approximately 135,000 ran some form of Microsoft Internet Information Server alongside SMTPD. The count currently stands at over 104,000 hosts, with over 30,000 taken offline or patched. We differentiate these two since the full attack requires both services for successful exploitation, but the reader should note that these two services can live on separate hosts. While the CVE was not made public until July, Microsoft silently addressed the vulnerability in the April 2021 update.
About a year later, in September 2022, ProxyNotShell was first discovered, and Microsoft announced they had confirmed two new exploits currently being tracked as CVE-2022-41040 and CVE-2022-41082. This exploit is remarkably similar to its predecessor ProxyShell and leverages a similar exploitation approach.
The first CVE, CVE-2022-41040, is a Server-Side Request Forgery vulnerability that an attacker can leverage with CVE-2022-41082 to achieve a Remote Code Execution (RCE). The vulnerability impacts Exchange Server 2013, Exchange Server 2016, and Exchange Server 2019. The reader can find additional details in our initial coverage here.
On Nov. 3rd, 2022, Microsoft released a patch to address the vulnerability stating, “Because we are aware of active exploits of related vulnerabilities (limited targeted attacks), our recommendation is to install these updates immediately to be protected against these attacks,” — So let’s keep patching, folks!
How can Censys help?
We have created an interactive dashboard for tracking these Microsoft Exchange services with Censys scan data. This vulnerability has been reported to work on the following:
- Exchange Server 2013
- Exchange Server 2016
- Exchange Server 2019
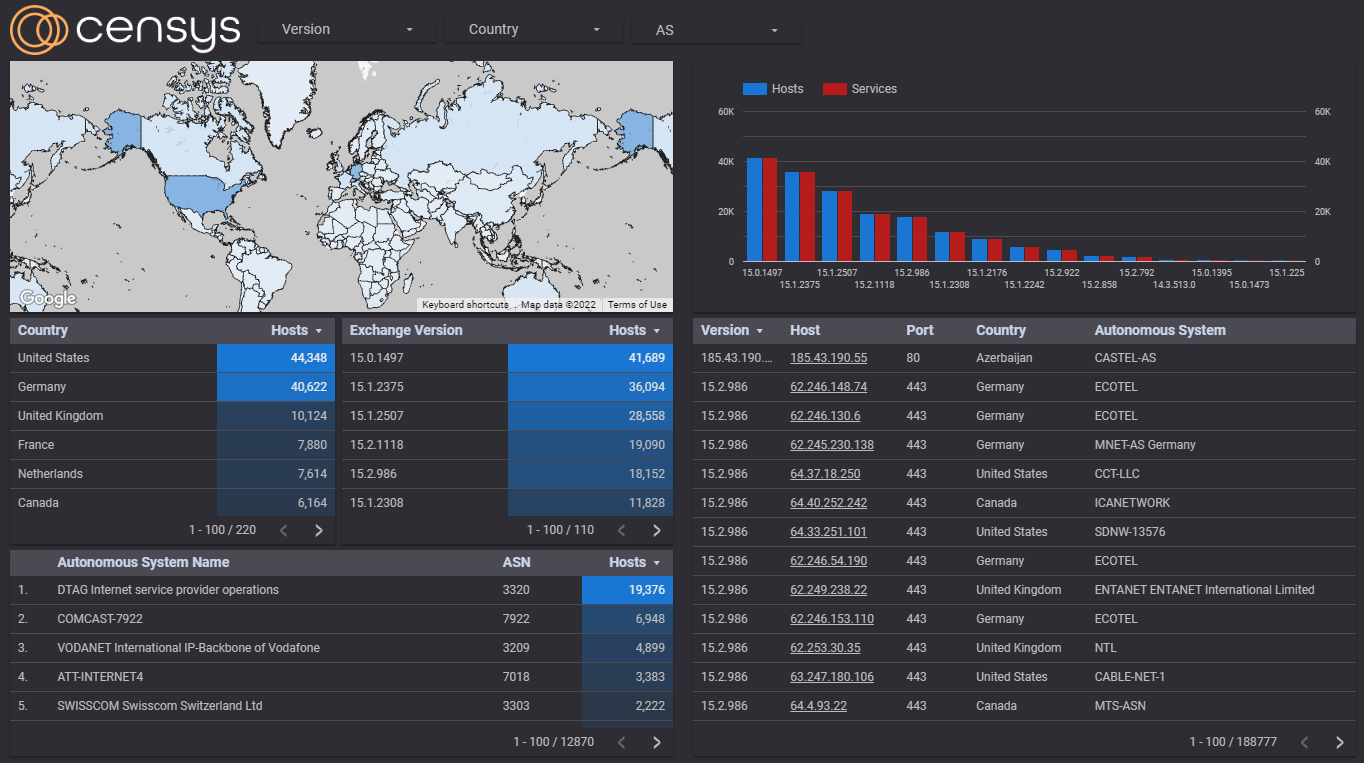
At the moment, the best way to identify these Exchange servers by using Censys is by using the following search query:
same_service(services.http.response.favicons.name: */owa/auth/* and services.http.response.html_title={“Outlook Web App”, “Outlook”})
Censys ASM customers will now have access to a new risk covering these two vulnerabilities. All ASM risks related to Microsoft Exchange can be found here using the search term: “risks.name: exchange”