Will the Real Volt Typhoon Please Stand Up?
One of the more powerful things you can do using Censys is track how a threat actor’s infrastructure changes over time or in response to external events.
In December 2023, the US Federal Bureau of Investigation (FBI) conducted a court-authorized disruption of the KV Botnet, by running a remote uninstall of infected systems in the United States. The KV Botnet is attributed to Volt Typhoon, a threat group originating from the People’s Republic of China (PRC) with a historical focus on critical infrastructure. While this disruption did not impact control infrastructure of the botnet, mass removal of bots is likely a way to spur a reaction from botnet administrators.
Despite both technical exposure by researchers and law enforcement disruption, this infrastructure has remained uncharacteristically consistent, only changing hosting providers. Given the contrasting high level of sophistication between Volt Typhoon’s activity within target organizations and their proxy network, it is possible the KV Botnet is operated by a party other than Volt Typhoon.
Based on Censys scanning and indicators publicly reported by Lumen, we were able to map control infrastructure for KV Botnet, specifically the JDY cluster, through 2024.
2024 Activity
The JDY cluster was first detailed by Lumen in 2023 and is believed to target Cisco RV320/RC325 routers for botnet propagation. On 14 November 2023, infected systems from this cluster were seen communicating with new control servers with a different certificate containing “jdyfj”, shown below:
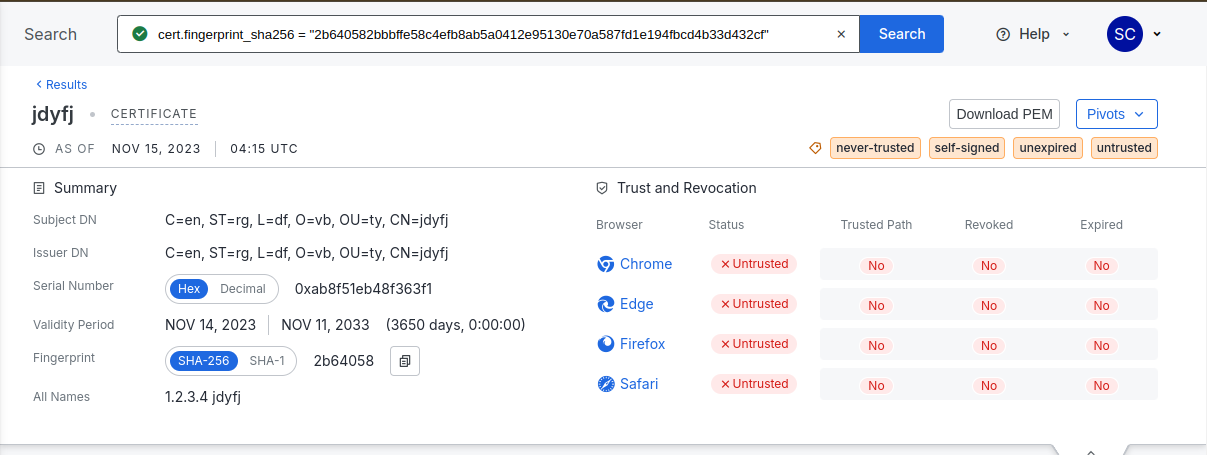
Example JDY C2 Server with a New Certificate Variant
Historical records for this certificate show the following hosts that may have previously been used by this actor:
| IP Address | Certificate First Seen | Certificate Last Seen | ASN |
| 45.32.174[.]131 | 28 December 2023 | 23 April 2024 | AS20473 – CHOOPA, US |
| 45.63.60[.]39 | 28 December 2023 | 24 April 2024 | AS20473 – CHOOPA, US |
| 159.203.113[.]25 | 18 November 2023 | 27 December 2023 | AS14061 – DIGITALOCEAN-ASN, US |
| 174.138.56[.]21 | 17 November 2023 | 2 December 2023 | AS14061 – DIGITALOCEAN-ASN, US |
| 108.61.132[.]157 | 15 November 2023 | 18 November 2023 | AS20473 – CHOOPA, US |
| 144.202.49[.]189 | 15 November 2023 | 27 December 2023 | AS20473 – CHOOPA, US |
Censys’s scans indicate that, following law enforcement action, 45.32.174[.]13 and 45.63.60[.]39 (highlighted in yellow above) were both likely brought online in response to disruption efforts. In April 2024, these servers were likely migrated to the infrastructure currently hosting this certificate. Notably, the current hosts have used different hosting providers each time servers have moved, shown in the table above, potentially to reduce impact of future disruption efforts.
The Censys research team has identified three hosts currently leveraging this certificate (SHA256 Hash: 2b640582bbbffe58c4efb8ab5a0412e95130e70a587fd1e194fbcd4b33d432cf):
| IP Address | Certificate First seen | Certificate Last Seen | ASN |
| 2.58.15[.]30 | 16 April 2024 | 6 January 2025 | AS199959 – CrownCloud, AU |
| 66.85.27[.]190 | 16 April 2024 | 7 January 2025 | AS8100 – Quadranet |
| 172.233.211[.]226 | 25 November 2024 | 7 January 2025 | AS63949 – AKAMAI-LINODE-AP Akamai Connected Cloud, SG |
Thoughts on attribution
Microsoft’s initial public report describes Volt Typhoon as a technically sophisticated threat actor, operating with a minimal toolkit and focus on stealth. However, following both technical exposure by researchers and disruption from law enforcement, operators of the KV Botnet have not taken any meaningful action to conceal their control infrastructure beyond migrating to new hosting providers. This notable difference calls into question the nature of the relationship between Volt Typhoon activity against target networks and the KV Botnet.


