Date of Disclosure: October 2, 2024
CVE-2024-9441 is an OS command injection vulnerability affecting the Linear eMerge e3-Series through version 1.00-07. If exploited, a remote and unauthenticated attacker can execute arbitrary OS commands via the login_id parameter when invoking the forgot_password functionality over HTTP.
Linear eMerge is a browser-based access control platform designed to manage and secure physical entry points within organizations. The system allows administrators to control access permissions, monitor entry activities, and generate reports.
The Flax Typhoon botnet, among other botnets linked to state-sponsored activities in China, has a history of targeting this device by exploiting the older command injection vulnerability CVE-2019-7256 in versions <=1.00-06. While the newer CVE-2024-9441 is not currently actively exploited, device owners are advised to take measures to harden their systems.
When exposed to the public internet, the eMerge e3-Series presents a web-based login portal. This interface is intended for authorized personnel to access the system remotely. If not properly secured, this exposure can be exploited by unauthorized users. To secure access to the eMerge e3-Series web portal, users should restrict access to internal networks or VPNs only, disable public internet exposure, and enforce multi-factor authentication for remote access if necessary.
 Exposed Linear eMerge web Interface
Exposed Linear eMerge web Interface
| Field |
Details |
| CVE-ID |
CVE-2024-9441 – CVSS 9.8 (Critical) assigned by VulnCheck |
| Vulnerability Description |
The Linear eMerge e3-Series through version 1.00-07 is vulnerable to an OS command injection vulnerability. A remote and unauthenticated attacker can execute arbitrary OS commands via the login_id parameter when invoking the forgot_password functionality over HTTP. |
| Date of Disclosure |
October 2, 2024 |
| Affected Assets |
login_id parameter when invoking the forgot_password functionality over HTTP. |
| Vulnerable Software Versions |
Versions through 1.00-07 |
| PoC Available? |
Yes, this advisory from SSD Secure Disclosure details how the vulnerability can be exploited. VulnCheck has also published a PoC. |
| Exploitation Status |
The same device was previously targeted by the Flax Typhoon botnet using older vulnerabilities like CVE-2019-7256, but this CVE-2024-9441 has not appeared on CISA’s list of known exploited vulnerabilities or in GreyNoise at the time of writing. |
| Patch Status |
At the time of writing, there is no available patch for this CVE. In the absence of a patch, it’s recommended that users isolate or take affected devices offline, implement network segmentation to restrict access to unauthorized personnel, or utilize monitoring solutions to detect unusual activity. |
Censys Perspective
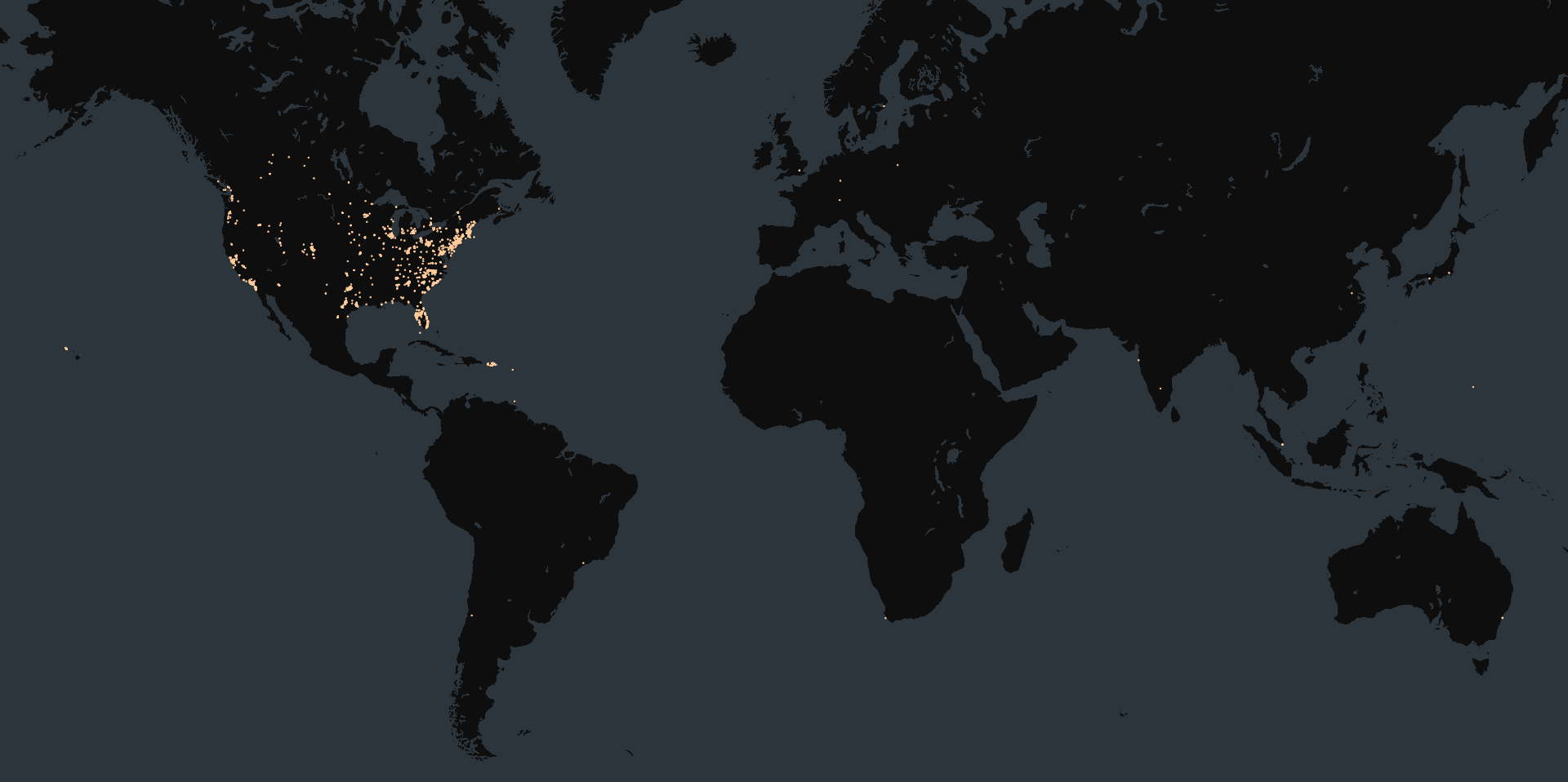
At the time of writing, Censys observed 2,706 exposed Linear eMerge e3-Series web portals online, filtering out honeypots. The vast majority of these (95%) are geolocated in the United States. Censys observed about 22% of the exposed instances to be associated with Comcast (ASN 7922). Note that not all of these are necessarily vulnerable, as specific device versions are not available.
Map of exposed Linear eMerge e3-Series instances:
Censys Search Query:
services.software: (vendor="Linear" and product="eMerge")
Censys ASM Query:
host.services.software.vendor="Linear" AND host.services.software.product="eMerge"
References