In the expansive and ever-changing landscape of attack surfaces, few things surprise us anymore, but sometimes, they still manage to amuse us. Imagine discovering that part of your organization’s corporate infrastructure is hosting a Minecraft server. While it might seem innocuous or even quirky, this setup could represent a serious security risk. We will explore how these unsanctioned servers can slip under the radar, how Censys helps identify them, and why they are far from harmless fun.
The Hidden Risk of Minecraft Servers
Minecraft servers, beloved by gamers worldwide, are typically designed for recreational use, not for deployment on corporate infrastructure. Yet, it is not uncommon to find them running within organizational networks. In fact, we recently observed a Minecraft server deployed on the corporate infrastructure of a Fortune 50 company. This might be as simple as a test server someone forgot to shut down or an entirely unauthorized setup running mods that introduce vulnerabilities.
Over the years, Minecraft mods have been notorious for containing security flaws, including Remote Code Execution (RCE) vulnerabilities. For example, in July 2023, the “BleedingPipe” vulnerability exposed thousands of Minecraft mods to RCE risks, leaving users vulnerable to exploitation. Read more about it here: Minecraft Mods Hit by Massive ‘BleedingPipe’ Vulnerability. A breach stemming from a Minecraft server is not just a hypothetical scenario; it is a tangible risk that can compromise sensitive data, impact system integrity, and tarnish organizational reputations.
How Does Censys Help?
At Censys, we excel at illuminating the dark corners of your attack surface. Our global scanning coverage and port-agnostic protocol detection make it possible to identify assets you might not even know existed, including rogue Minecraft servers.
Here are two approaches to uncovering these hidden threats using Censys:
Search
Our Censys Search platform allows you to craft targeted queries to identify Minecraft servers. For example:
services.service_name: “minecraft”
This query surfaces devices identified as running Minecraft server protocols on any port. By extending it with additional filters, such as organization name or IP range, you can refine the results to focus on assets linked to your organization.
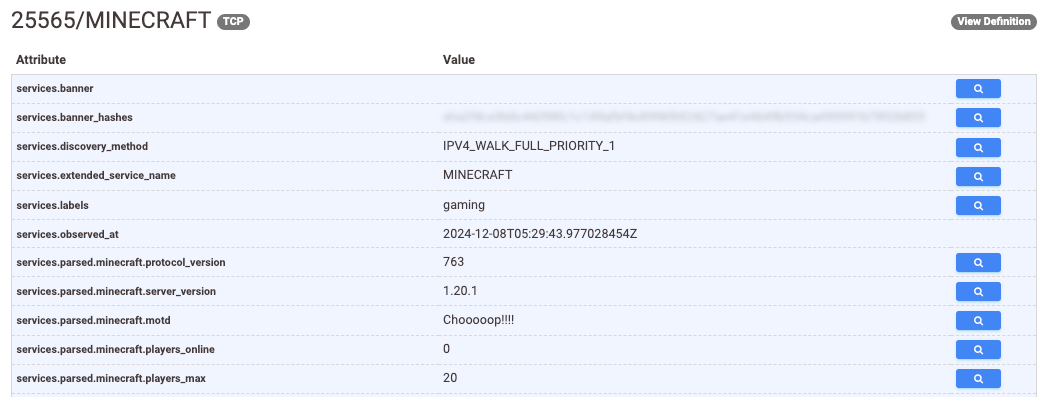
ASM
Using the Censys Attack Surface Management (ASM) dataset, you can contextualize findings within your known inventory. A sample query might look like this:
host.services.service_name: “minecraft”
The Serious Implications of a Funny Concept
While it is tempting to view a Minecraft server on corporate infrastructure as a harmless distraction, the risks tell a different story:
- Exploitation of Known Vulnerabilities: Mods and outdated server versions often come with unpatched vulnerabilities that attackers can exploit.
- Unauthorized Access Points: A Minecraft server’s very presence expands your attack surface, creating a vector for attackers to pivot into more critical systems.
- Compliance Risks: Unsanctioned software can violate industry regulations or internal IT policies, leading to audit failures or penalties.
Keeping It Fun, But Focused
At Censys, we understand the importance of balancing vigilance with approachability. A Minecraft server on your infrastructure might elicit a laugh, but resolving the issue requires serious action. Tools like ours empower organizations to find, assess, and address these unexpected risks, ensuring your attack surface remains secure.
The next time you think about your attack surface, consider the unconventional. Could there be an unsanctioned Minecraft server lurking somewhere? With Censys, you can find out and take action before it becomes a liability.
Schedule a demo today and learn how Censys can help uncover the hidden threats within your organization’s infrastructure, from misconfigured databases to the most surprising of server setups.