Introduction
On May 24, 2023, Microsoft announced that they’d discovered “stealthy and targeted malicious activity” focused on communications critical infrastructure of the US and Guam. The attacks are attributed to a Chinese state-sponsored actor dubbed Volt Typhoon, who has been active since mid-2021.
One of Volt Typhoon’s primary techniques is living off the land, which involves leveraging tools and services that already exist in the compromised environment. This allows them to more effectively subvert detection and increase their dwell time in the environment.
Volt Typhoon leverages compromised small office and home office (SOHO) networking equipment, such as routers, to proxy attack traffic to their targets. Again, with a focus on avoiding detection, proxying their traffic through these residential and small office devices allows them to more easily fade into typical network activity. Notably, affected devices observed appear to have SSH or HTTP open to the internet.
Microsoft and a Joint Cybersecurity Advisory by the NSA and others have detailed SOHO devices they’ve observed involved in these attacks, including those made by Cisco, Draytek, FatPipe, Netgear Prosafe, and Zyxel. Below, we explore the internet presence of these devices that also have HTTP or SSH open to the internet.
SOHO Device Exposure
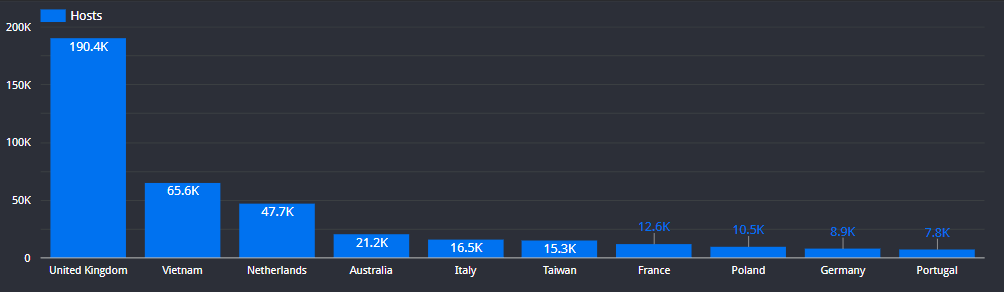
In total, we observed 510,384 total hosts (1,113,901 services) running one of these SOHO routers with either the HTTP management port or SSH service running.
Conclusion
With over half a million small office or home office networking devices exposing HTTP or SSH to the internet, threat actors like Volt Typhoon have ample opportunities for potential exploitation of these devices for nefarious purposes.
If you’re running a SOHO device, ensure that the administrative login and controls aren’t accessible from the public internet. Check out me.censys.io to see if your router is exposing any unexpected services to the public internet.