Summary:
- Juniper Networks recently patched a critical pre-authentication Remote Code Execution (RCE) vulnerability in the J-Web configuration interface across all versions of Junos OS on SRX firewalls and EX switches.
- Unauthenticated actors could exploit this vulnerability to gain root access or initiate Denial of Service (DoS) attacks on devices that have not been patched. Ensure your systems are updated promptly to mitigate this risk.
- Check for exposed J-Web configuration interfaces using this Censys Search query: services.software.uniform_resource_identifier: `cpe:2.3:a:juniper:jweb:*:*:*:*:*:*:*:*`.
- As emphasized last year in CISA’s BOD 23-02 guidance, exposed network management interfaces continue to pose a significant risk. Restrict access to these interfaces from the public internet wherever possible.
Per Juniper’s security advisory the following versions are affected on SRX and EX devices:
- Junos OS versions earlier than 20.4R3-S9;
- Junos OS 21.2 versions earlier than 21.2R3-S7;
- Junos OS 21.3 versions earlier than 21.3R3-S5;
- Junos OS 21.4 versions earlier than 21.4R3-S5;
- Junos OS 22.1 versions earlier than 22.1R3-S4;
- Junos OS 22.2 versions earlier than 22.2R3-S3;
- Junos OS 22.3 versions earlier than 22.3R3-S2;
- Junos OS 22.4 versions earlier than 22.4R2-S2, 22.4R3.
The vulnerability is patched in versions 20.4R3-S9, 21.2R3-S7, 21.3R3-S5, 21.4R3-S5, 22.1R3-S4, 22.2R3-S3, 22.3R3-S2, 22.4R2-S2, 22.4R3, 23.2R1-S1, 23.2R2, 23.4R1, and all subsequent releases.
Censys’s Perspective:
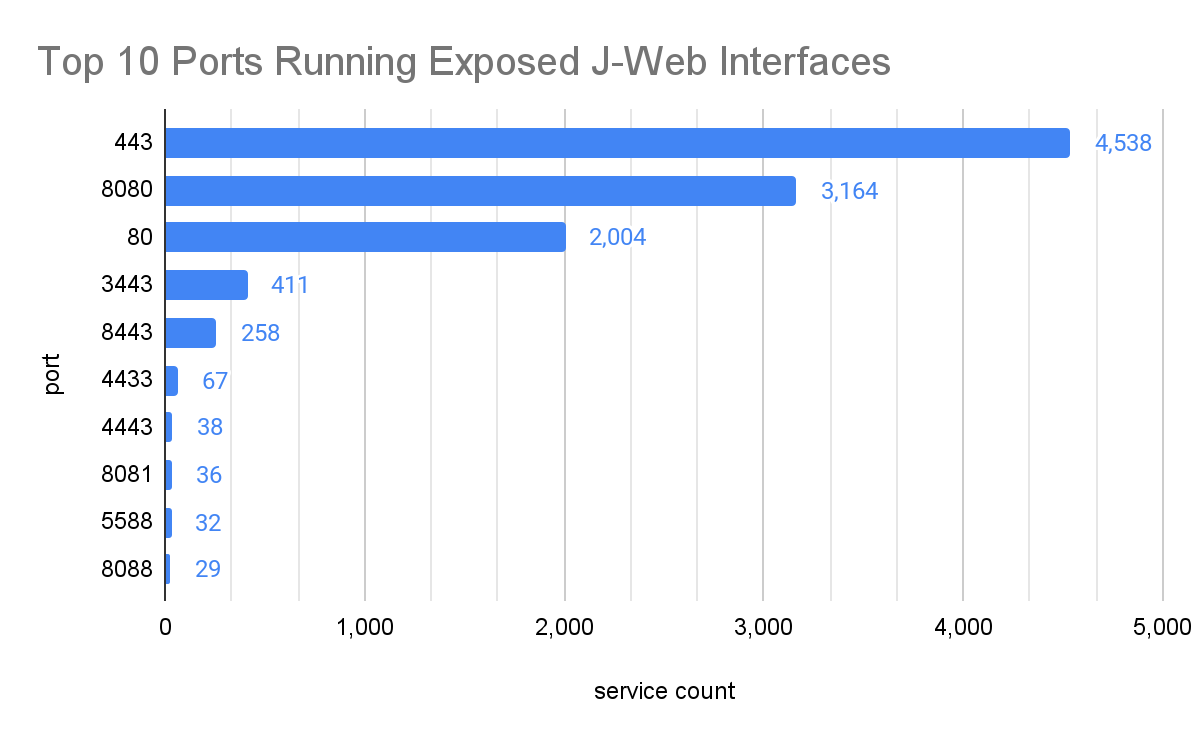
As of Thursday January 11, 2024, Censys observed over 11,500 exposed J-Web interfaces online. Most of them were running on standard HTTP ports: 443, 8080, and 80.
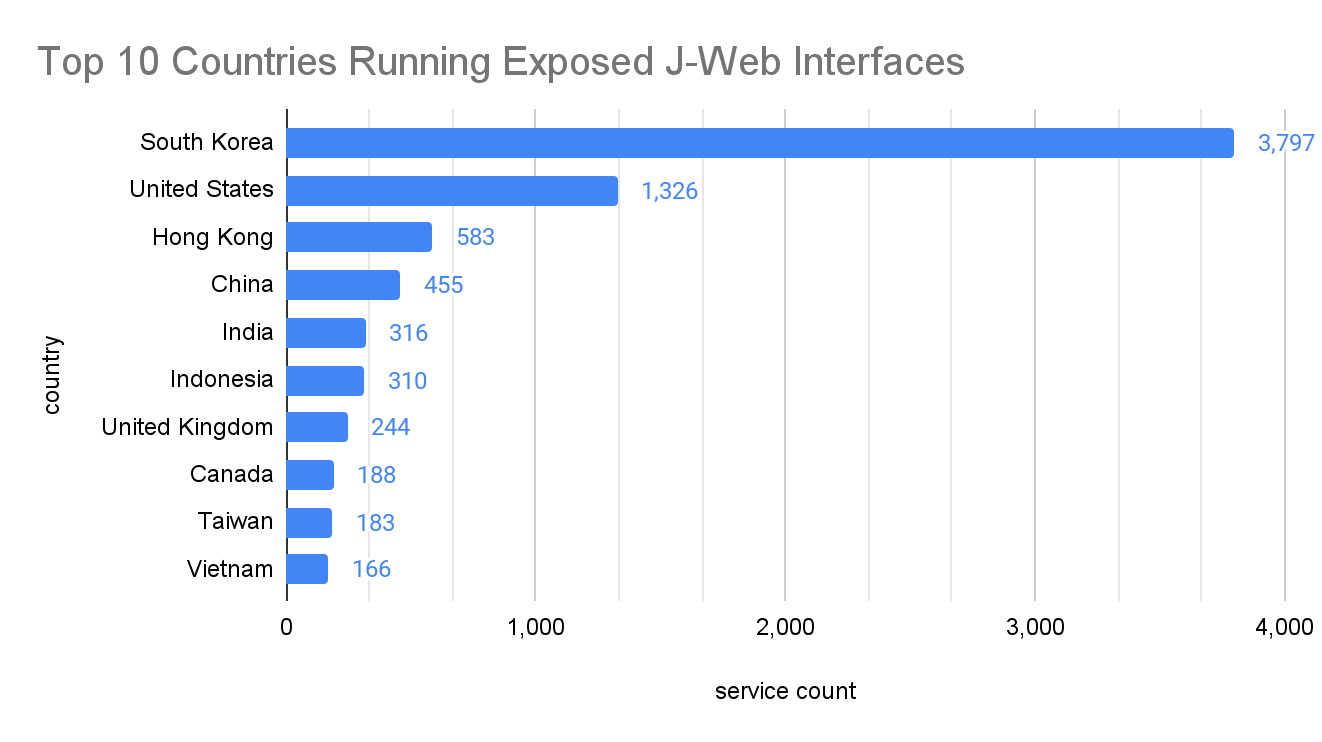
These devices appear to have a heavy presence across Asia, with notable exposure in South Korea and Hong Kong.
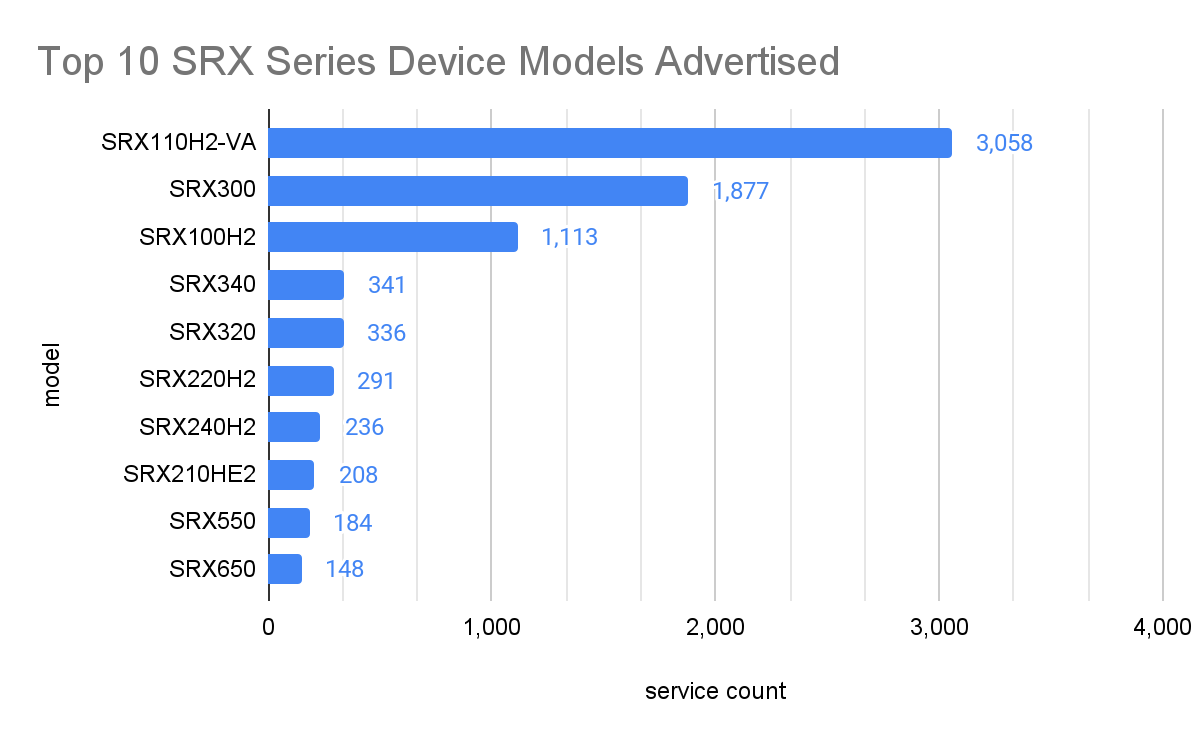
Something we discovered is that many J-Web interfaces advertised the model numbers of their associated SRX firewall devices. The most common device exposing a J-Web config panel was the SRX110H2-VA, which was announced as end-of-life back in May 2018.