Introduction:
On April 18, 2023, the NCSC, NSA, CISA, and the FBI released a joint security advisory regarding the TTPs behind a 2021 malware campaign by APT28 (also known as Fancy Bear), a Russian state-sponsored threat actor group. The campaign targeted unpatched Cisco routers running exposed Simple Network Management protocol (SNMP) by exploiting multiple RCE vulnerabilities in SNMP (CVE-2017-6742) to deploy malware on these devices. As a result, several U.S. government assets and approximately 250 victims in Ukraine were compromised. These vulnerabilities are still being actively exploited.
SNMP was developed to enable remote monitoring of network devices. However, it can be used for malicious purposes to access internal network data. In the most severe scenarios, attackers can leverage SNMP to assume control over the device, create a comprehensive map of the entire network, and pinpoint other potential targets on the network.
CVE-2017-6742 affects all versions of SNMP (1, 2c, and 3), and an attacker could exploit these vulnerabilities by sending a specially crafted SNMP packet to a vulnerable device via either IPv4 or IPv6. By leveraging tools like net-snmp, one can easily obtain routing tables, arp tables, and detailed information about the runtime. Poorly configured devices using default or easily guessable community strings are particularly open to such attacks. In addition to exploiting CVE-2017-6742, APT28 managed to access router information through the exploitation of weak SNMP community strings, including the default “public.” See the Jaguar Tooth malware analysis report for more detail on TTPs.
Per Cisco’s 2017 security advisory, the 9 SNMP Management Information Bases (MIBs) affected by this vulnerability are:
- ADSL-LINE-MIB
- ALPS-MIB
- CISCO-ADSL-DMT-LINE-MIB
- CISCO-BSTUN-MIB
- CISCO-MAC-AUTH-BYPASS-MIB
- CISCO-SLB-EXT-MIB
- CISCO-VOICE-DNIS-MIB
- CISCO-VOICE-NUMBER-EXPANSION-MIB
- TN3270E-RT-MIB
“All of the MIBs listed above are enabled by default when SNMP is enabled. Some of the MIBs may not be present on all systems or versions but are enabled when present.” reads the advisory.
Regardless of whether your Cisco devices are vulnerable to this particular exploit, in general it’s important for both individuals and organizations to check if SNMP is enabled on their Cisco devices. SNMP is an example of a tool that is powerful for network management, but dangerous in the wrong hands. Cisco routers are often among an organization’s critical infrastructure assets and shouldn’t have public SNMP running. If the service must be public, administrators need to make sure that they have applied the latest Cisco patches and to mitigate the threat from this malware activity, especially now as the exploitation tactics have been published.
The types of networks we see these devices running in are a mixture of telecommunications companies and ISPs. The network with the highest concentration of exposures is SOVAM-AS, belongs to PJSC VimpelCom, a major Russian telecom company.
| Top 10 Autonomous Systems with Cisco Routers Exposing SNMP |
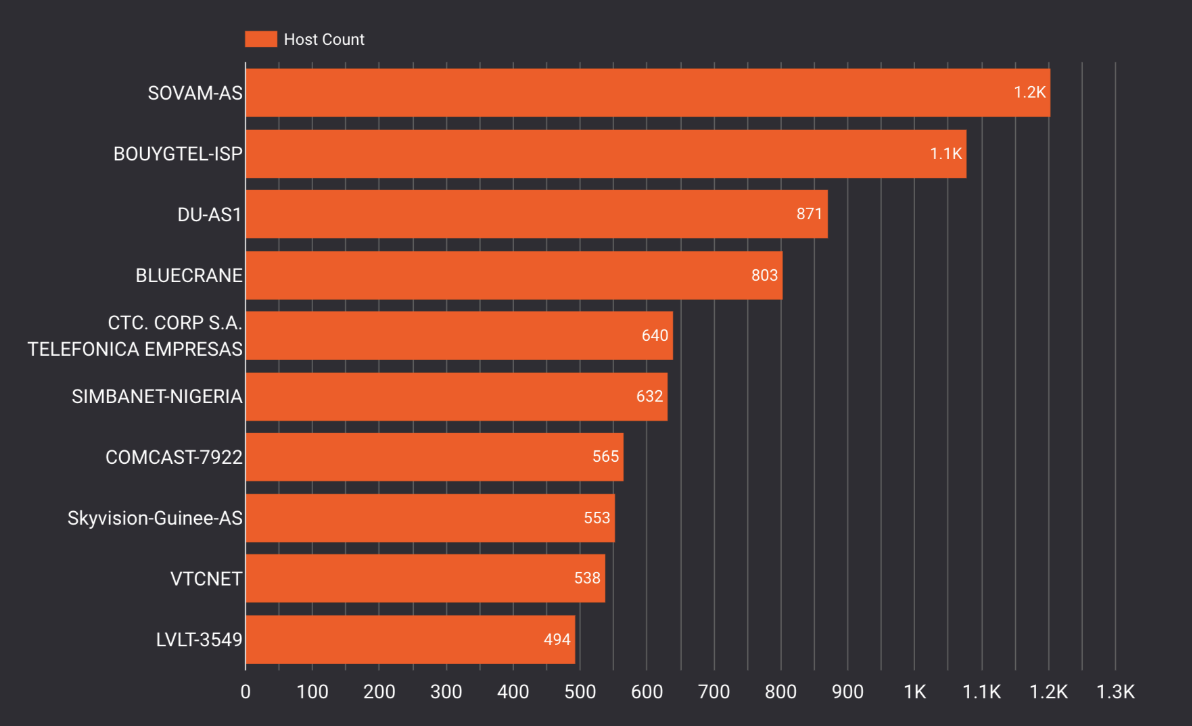 |
| Name |
ASN |
Host Count |
% |
| SOVAM-AS |
3216 |
1203 |
3.05% |
| BOUYGTEL-ISP |
5410 |
1079 |
2.74% |
| DU-AS1 |
15802 |
871 |
2.21% |
| BLUECRANE |
328198 |
803 |
2.04% |
| CTC. CORP S.A. TELEFONICA EMPRESAS |
37200 |
640 |
1.62% |
| SIMBANET-NIGERIA |
16629 |
632 |
1.60% |
| COMCAST-7922 |
7922 |
565 |
1.43% |
| Skyvision-Guinee-AS |
328244 |
553 |
1.40% |
| VTCNET |
19881 |
538 |
1.36% |
| LVLT-3549 |
3549 |
494 |
1.25% |