Setting the record straight
Summary
- Twenty different end-of-life D-Link Network-Attached Storage device models have been found to be susceptible to a critical-level vulnerability, which can result in a remote code execution.
- Many outlets are reporting that there are over 92,000 hosts that are vulnerable to this exploit, but after close analysis, this does not seem to be the case.
- Censys observes that less than 6,000 of these devices are connected to the Internet. This is still very high but far less than the reported numbers.
Analysis
On April 3rd, 2024, a critical-level vulnerability was announced in several end-of-life D-Link devices used for Network-Attached Storage (NAS). This vulnerability can result in remote code execution (RCE) against a specific API endpoint that uses hardcoded credentials for the username “messagebus” with an empty string for a password. Since these devices have reached end-of-life, there will not be any patches for this vulnerability. This means any device online that is running one of these is assumed to be vulnerable.
The author, netsecfish, released details about the vulnerability last month through public disclosure. Even though information about this vulnerability has been sitting in a GitHub repository since March 26th, the world did not seem to take notice until around April 4th, 2024, when an article about the vulnerability was published on securityonline.info (at least, this was the first mention that we could find).
Given that this vulnerability is remote, extremely easy to exploit, and details were made public almost immediately after release, many of the headlines around the internet focused on the potential widespread impact a mass-hacking campaign could have on internet assets. With headlines like “92,000+ internet-facing D-Link NAS devices accessible via backdoor”, “Critical takeover vulnerabilities in 92000 D-Link devices”, and “Critical Flaws Leave 92000 D-Link NAS Devices Vulnerable”, this seemed like a huge deal.
Censys started investigating the 92,000 D-Link NAS devices exposed to the internet. We were startled to discover that our results differed vastly from this number—so much so that we figured we must have been doing something wrong, given that multiple media outlets had quoted similar numbers.
We continued to tweak and validate our searches and got the same results repeatedly. Still only half-sure of ourselves, we decided to track down the source of this 92,000+ number, and that’s when things started to unravel.
On March 26th, 2024, the individual behind the advisory committed two screenshots to their GitHub repository:
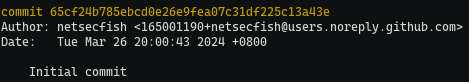
Of the two uploaded screenshots, one was of a search result from another network scanning product, FOFA, and the number 92,000+ seems to have originated from this. However, the original author may have misinterpreted the results they saw because there is no mention of 92,000 hosts even in their screenshot. However, it does mention 92,589, but for the number of services. Below is a clip from the author’s screenshot showing only 55,138 hosts (“unique IP”) in these results.
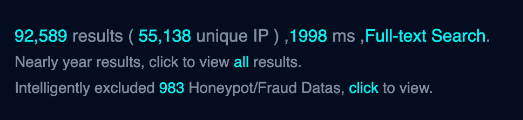
55,138 is still considerably different from what we saw in our data, so we explored the FOFA results to understand the discrepancies. And yes, their results matched what was posted in the original screenshot, but one of the bylines in the result description caught our eye:
“Nearly year results, click to view all results.”
To us, this text read like a poor English translation, and we also knew that FOFA was a Chinese-based operation and we were viewing their English translations, so we toggled the application to native Chinese and saw this:
“显示一年内数据,点击 all 查看所有”
This text, when run through Google Translate, has a slightly different but more meaningful result than the original translation:
“Display data within one year, click all to view all”
Well, that’s suspicious.
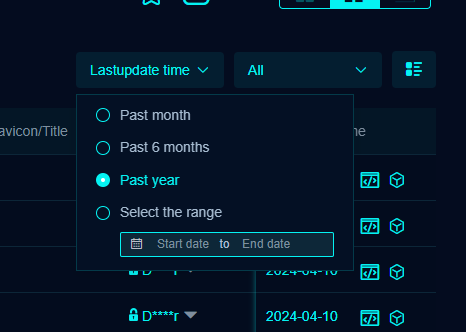
By default, the results displayed on the FOFA website are not the current list of hosts; they are all the hosts seen over the past year, whether or not they are currently up.
We further verified this by confirming that many of the host results were weeks to months old and, thus, did not accurately represent the actual fallout radius of this vulnerability.
This fact matters because most hosts running these D-Link NAS devices are found on residential networks, and there is a higher chance that a host will go down and come back up with a different IP address regularly. Hosts on residential networks come and go, so looking at them over a year not only results in duplicate devices (just with different IP addresses), but it’s also inaccurate when stating that “92k hosts are vulnerable”. In the graph below, we see that every network with the highest number of these hosts deals in residential internet services.
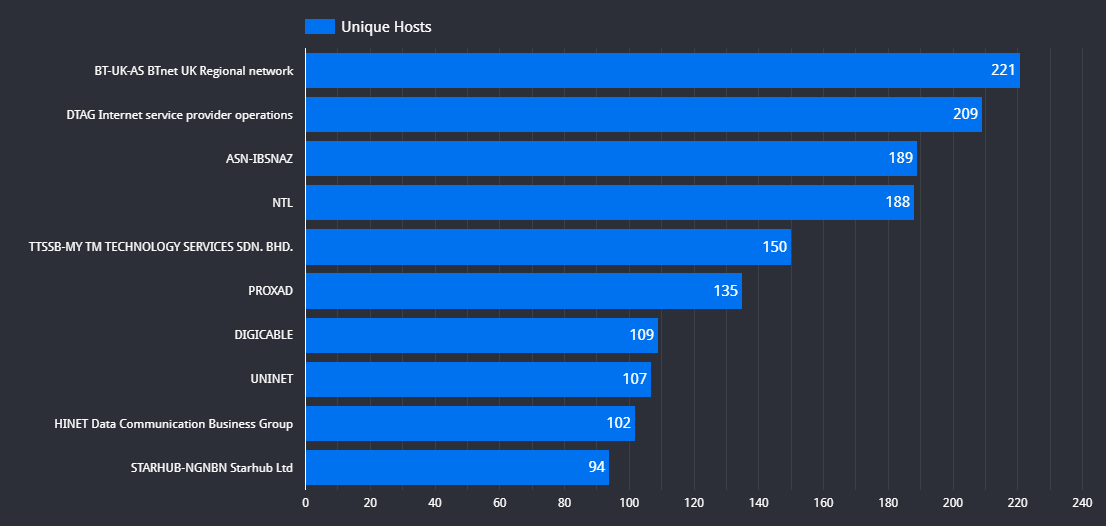 |
| Autonomous System |
Residential? |
Host Count |
| BT-UK-AS |
YES |
221 |
| DTAG Internet |
YES |
209 |
| ASN-IBSNAZ |
YES |
189 |
| NTL |
YES |
188 |
| TTSSB-MY |
YES |
150 |
| PROXAD |
YES |
135 |
| DIGICABLE |
YES |
109 |
| UNINET |
YES |
107 |
| HINET |
YES |
102 |
| STARHUB |
YES |
94 |
|
We also noticed that a set of hosts that were included in these results were running an open-source alternative to DLink NAS firmware called Alt-F, which is not vulnerable to this CVE and describes itself as follows:
“Alt-F provides a free and open source alternative firmware for the DLINK DNS-320/320L/321/323/325/327L and DNR-322L.”
In short, there are not 92,289 hosts running a D-Link NAS device or 55,138 hosts, as the screenshot would have you believe. Our results show that only 5,916 hosts match the indicators published in the CVE.
Below is the raw Censys search query one can use to find these hosts; it should be noted that a research or pro-level account is required to use regular expressions.
services: ((
tls.certificates.leaf_data.issuer.common_name=/DNS-320L([a-fA-F0-9]{12}|-.*)/
or tls.certificates.leaf_data.issuer.common_name=/DNS-325([a-fA-F0-9]{12}|-.*)/
or tls.certificates.leaf_data.issuer.common_name=/DNS-327L([a-fA-F0-9]{12}|-.*)/
or tls.certificates.leaf_data.issuer.common_name=/DNS-340L([a-fA-F0-9]{12}|-.*)/
or tls.certificates.leaf_data.issuer.common_name=/DNS-320([a-fA-F0-9]{12}|-.*)/
or tls.certificates.leaf_data.issuer.common_name=/DNS-320LW([a-fA-F0-9]{12}|-.*)/
or tls.certificates.leaf_data.issuer.common_name=/DNS-345([a-fA-F0-9]{12}|-.*)/
or http.response.body: "<img border=\"0\" src=\"/web/images/logo.png\""
or (
http.response.headers.key: `WWW-Authenticate`
and http.response.headers.value.headers: {
`Basic realm=\"DNR-322L\"`, `Basic realm=\"DNR-202L\"`
}
))
and not (
http.response.html_title:"ALT-F"
)
)
The same hosts can also be found with free accounts using the following search query, but at the time of writing (April 12th, 2024), the software labels have yet to be fully indexed, so these results may be incomplete until that process is finished (within the next 48 hours).
services.software: (
vendor: "D-Link"
and product={
"DNS-320L","DNS-325","DNS-327L",
"DNS-340L","DNR-202L","DNS-320",
"DNS-320LW","DNR-322L","DNS-345","ShareCenter"})
One may have noticed that we have included “ShareCenter” in both queries. This is because not every device running D-Link’s ShareCenter explicitly states what model it is running; we’re only including it because it was in the original author’s query in their screenshot:
However, even including all ShareCenter services, the actual numbers are still far below the reported 92,000.
There are two extra methods one can employ to pull the model information from these ShareCenter services if they don’t explicitly provide that data:
~ % curl http://$HOST:$PORT/xml/info.xml
<info>
<ip>X.X.X.X</ip>
<device>dlink-03BFF4</device>
<hw_ver>DNS-325</hw_ver>
<version>1.05</version>
<url>http://www.dlink.com/</url>
</info>
Timeline of Events
2024-03-26
“On March 26, 2024, a 3rd Party security research VulDB Coordination brought a public disclosure to our attention.”
2024-04-03
2024-04-04
2024-04-06
2024-04-07
2024-04-08
2024-04-10
References
Below is a table of every affected D-Link model pulled from the official D-Link advisory.
| Model |
End of Service Life |
Conclusion |
| DNS-120 |
01/01/09 : Link |
Retire & Replace Device |
| DNR-202L |
06/30/2020 : Link |
Retire & Replace Device |
| DNS-315L |
09/11/2014 |
Retire & Replace Device |
| DNS-320 |
12/1/2018 : Link |
Retire & Replace Device |
| DNS-320L |
05/31/2020 : Link |
Retire & Replace Device |
| DNS-320LW |
05/31/2020 |
Retire & Replace Device |
| DNS-321 |
5/5/2013: Link |
Retire & Replace Device |
| DNR-322L |
11/30/2021 : Link |
Retire & Replace Device |
| DNS-323 |
5/5/2013 : Link |
Retire & Replace Device |
| DNS-325 |
09/01/2017 : Link |
Retire & Replace Device |
| DNS-326 |
6/30/2013 : Link |
Retire & Replace Device |
| DNS-327L |
05/31/2020 : Link |
Retire & Replace Device |
| DNR-326 |
2/28/2018 : Link |
Retire & Replace Device |
| DNS-340L |
07/31/2019 : Link |
Retire & Replace Device |
| DNS-343 |
2/28/2020 : Link |
Retire & Replace Device |
| DNS-345 |
2/1/2019 : Link |
Retire & Replace Device |
| DNS-726-4 |
7/1/2014 : Link |
Retire & Replace Device |
| DNS-1100-4 |
6/1/2018 : Link |
Retire & Replace Device |
| DNS-1200-05 |
4/30/2020 : Link |
Retire & Replace Device |
| DNS-1550-04 |
4/30/2020 : Link |
Retire & Replace Device |