Introduction:
On 19 February 2024, ConnectWise announced they had patched two critical vulnerabilities, tracked as CVE-2024-1709 and CVE-2024-1708. These vulnerabilities impact ScreenConnect versions 23.9.7 and earlier, posing a significant risk to on-premise users.
CVE-2024-1709 – Authentication Bypass Vulnerability:
ConnectWise identified CVE-2024-1709 as a critical authentication bypass vulnerability with the highest possible CVSS severity score of 10. In a technical analysis published by Huntress, researchers noted that exploiting this vulnerability is alarmingly trivial. By requesting the “/SetupWizard.aspx/” endpoint with virtually any trailing path value, threat actors can gain access to the setup wizard on already-configured ScreenConnect instances, overwrite existing user data, and execute code remotely by creating ScreenConnect plugins. The author of the corresponding Metasploit module for this vulnerability has noted that the exploit still works when altering the case of the “SetupWizard.aspx” path on a Windows target, but is case-sensitive when attempted on a Linux target.
CVE-2024-1708 – Path Traversal Vulnerability:
CVE-2024-1708 is a high-severity path traversal vulnerability affecting the same ScreenConnect versions as CVE-2024-1709. Once CVE-2024-1709 is exploited to take control of a device, CVE-2024-1708 can be leveraged to achieve remote code execution (RCE) on the instance.
Active exploitation of these vulnerabilities has already been widely observed, along with various post-exploitation activities. Research from Huntress shows threat actors have been observed attempting to deploy ransomware payloads, cryptocurrency miners, and additional remote access tools such as Cobalt Strike Beacon after gaining access to compromised devices. Sophos reported observing ransomware payloads built using a leaked LockBit ransomware builder. It is recommended to monitor Microsoft IIS logs for any requests to the “/SetupWizard.aspx” path that have a trailing path segment as an indicator of compromise.
ConnectWise released a patch for both vulnerabilities in version 23.9.8. Note that instances hosted in the cloud ( “screenconnect[.]com” and “hostedrmm[.]com,”) were automatically patched by the vendor. However, on-premise users are strongly urged to patch their instances to at least version 23.9.8. ConnectWise has waived license restrictions for this update, allowing all users, even those with expired licenses, to upgrade their instances.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added CVE-2024-1709 to its Known Exploited Vulnerabilities catalog (KEV) with a due date of 29 February for U.S. Federal agencies to secure their servers.
In this blog post, we will delve into the details of these vulnerabilities, Censys’s global view of the state of exposure and vulnerability, and the remediation steps to safeguard your systems.
Censys’s Perspective
As of Tuesday, 27 February, 2024, we have identified 3,434 potentially vulnerable IPv4 hosts exposed online. This number reflects a continued downward trend from the 6,000+ vulnerable hosts observed just over a week ago on 19 February.
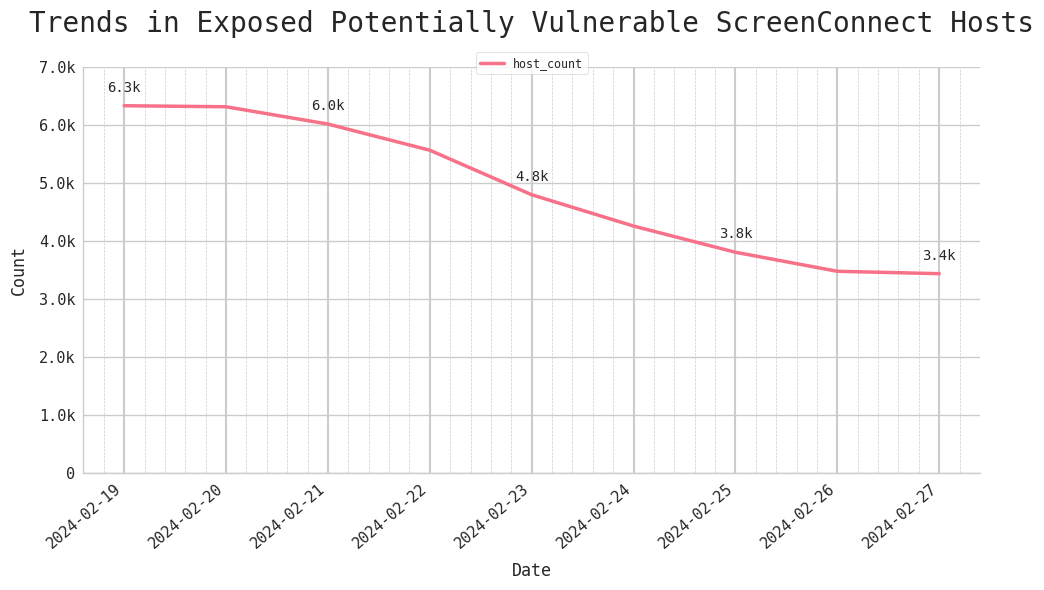
Figure 1. The Internet’s Response to Recent ScreenConnect Vulnerabilities CVE-2024-1709 and CVE-2024-1708, 19 — 27 February 2024
The figure below depicts a time lapse map of where vulnerable ScreenConnect hosts were located from 19 February to 27 February.
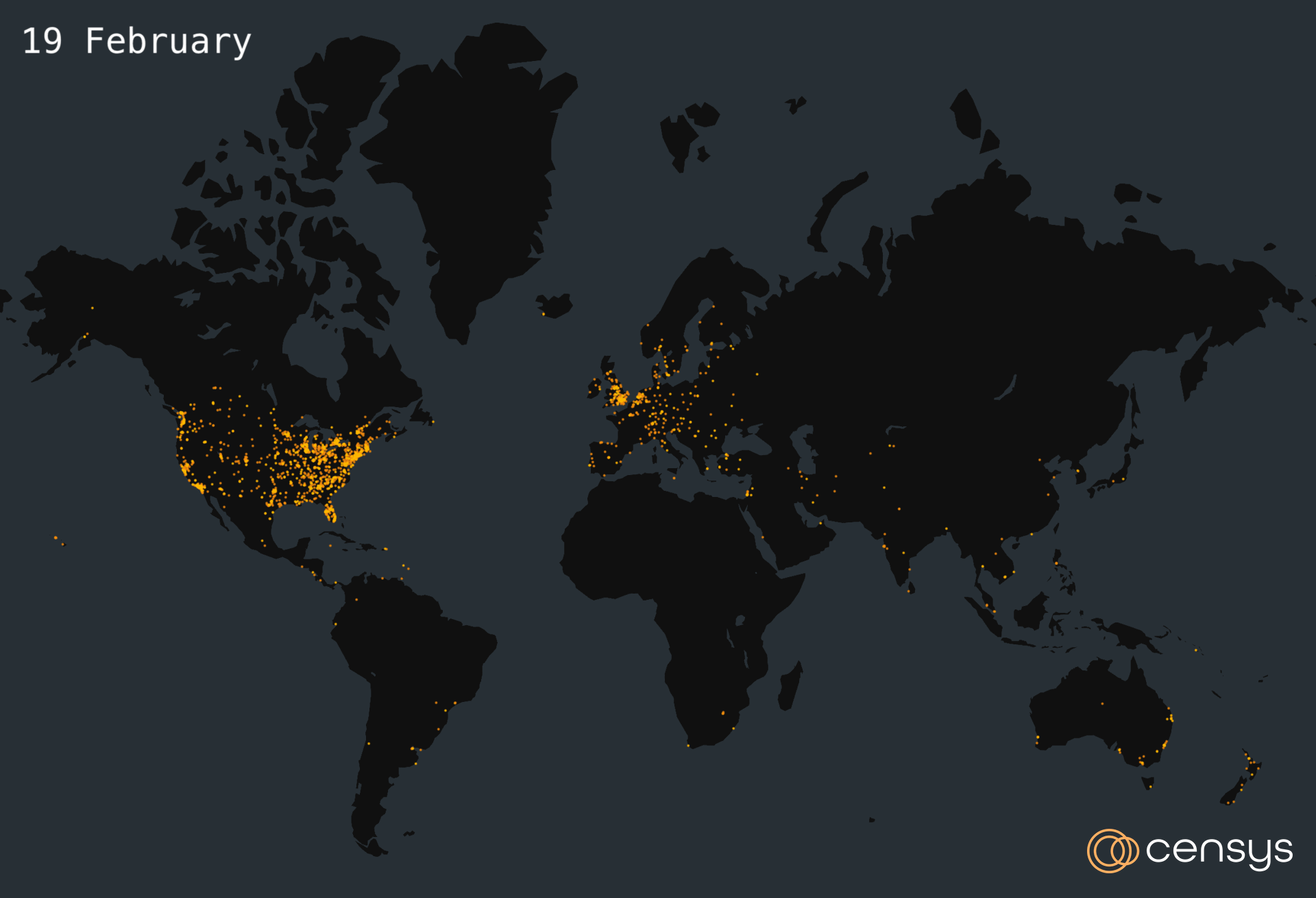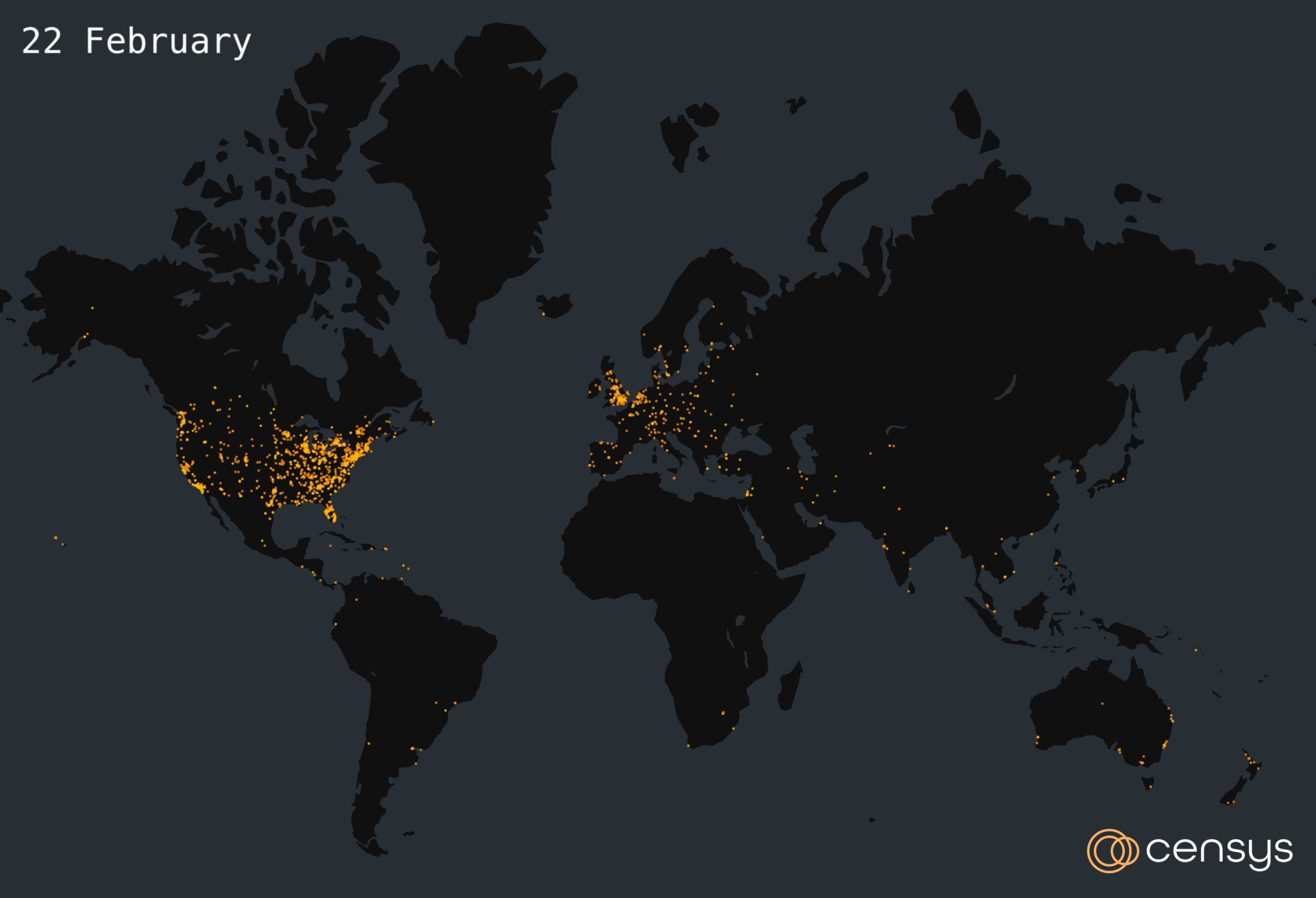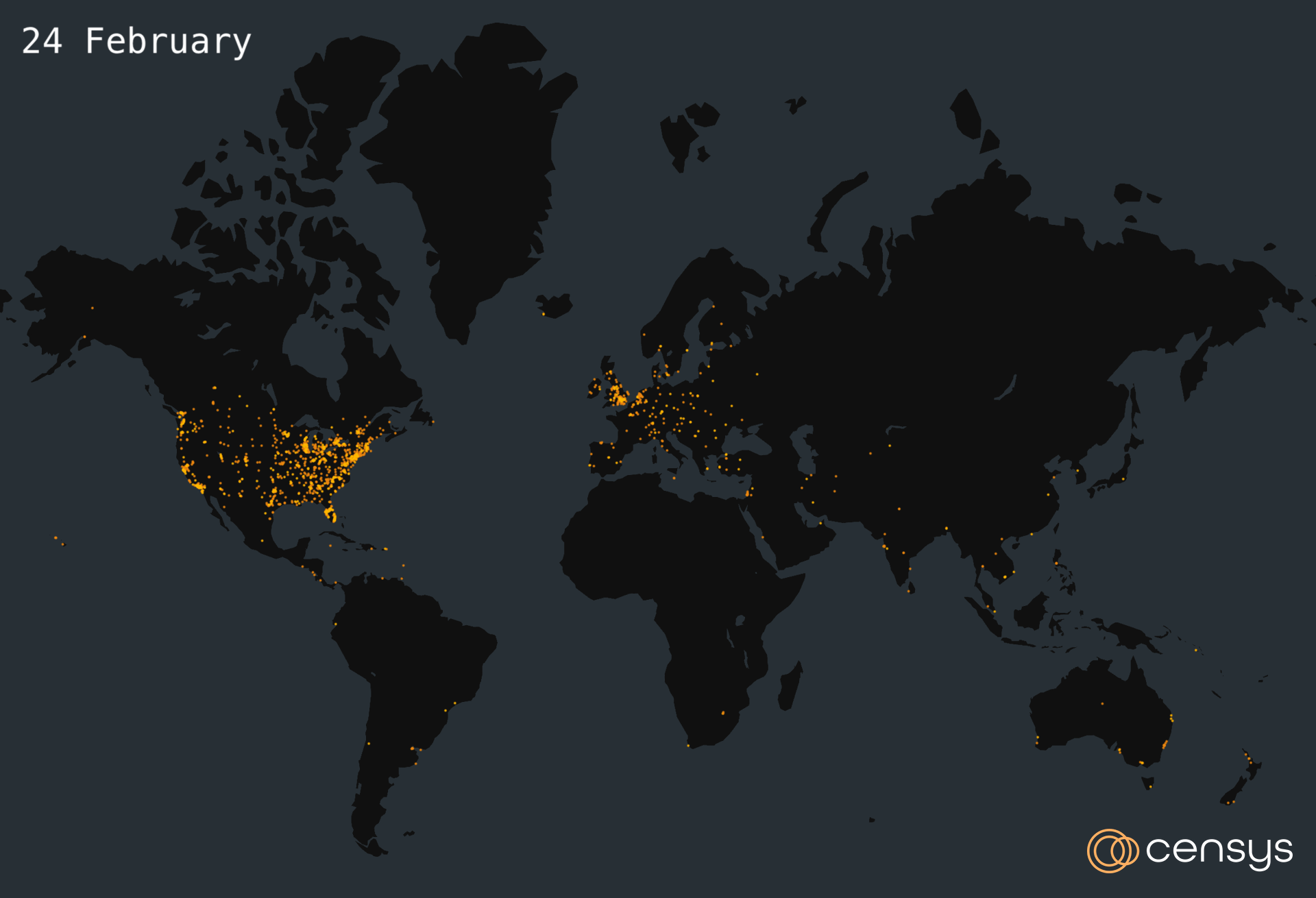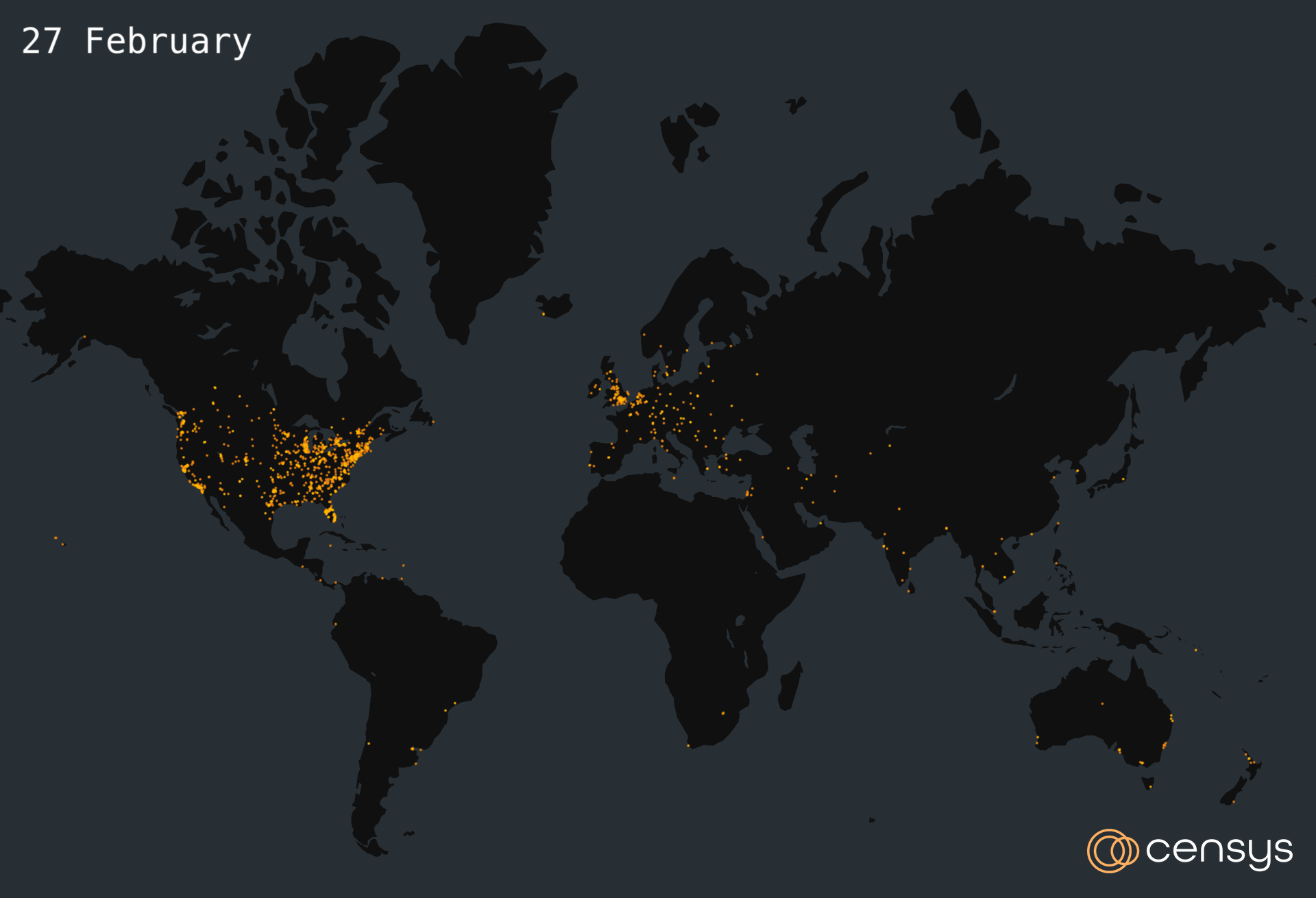
Figure 2. Time Lapse Map of The Internet’s Response to Recent ScreenConnect Vulnerabilities CVE-2024-1709 and CVE-2024-1708, 19 — 27 February 2024 (Created with kepler.gl)
TCP port 8040, which serves as the default outbound port for ScreenConnect, is by far the most common port we see vulnerable instances exposed on, followed by 80 and 443. Version 19.1.24566 is the most prevalent version we observe among vulnerable hosts.
The following graphs capture the current state of related exposures as of 27 February.
Note that ScreenConnect’s digital presence is mostly in the United States.
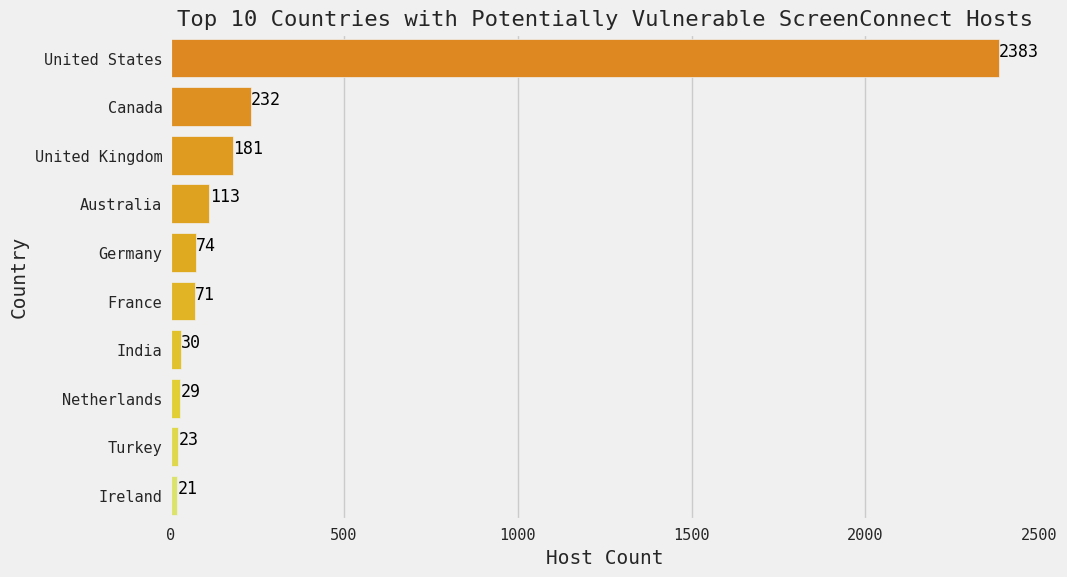
Figure 3. Top Countries with Exposed Potentially Vulnerable ScreenConnect hosts, 27 February 2024
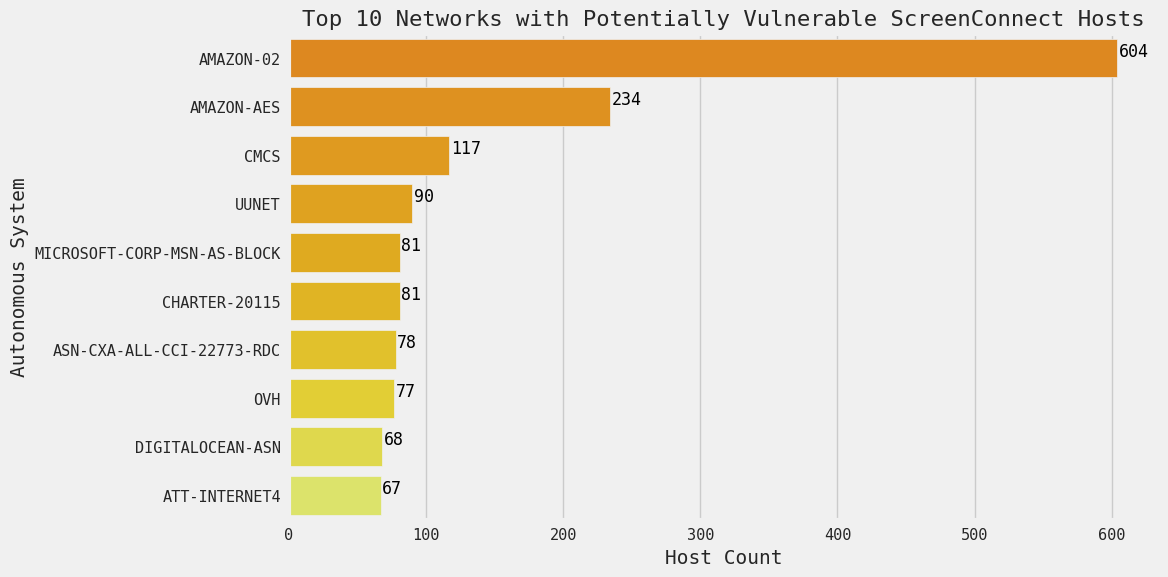
Figure 4. Top Networks with Exposed Potentially Vulnerable ScreenConnect hosts, 27 February 2024
Among potentially vulnerable hosts, there appears to be a particularly heavy presence of instances hosted in AWS (AMAZON-02 and AMAZON-AES).
Readers familiar with previously published Censys Research blogs may recognize these two networks, which have previously been identified as networks with observed deceptive honeypot activity and false positive data on multiple occasions. As of the time of writing, there is no strong evidence of similar deceptive behavior actively taking place on these networks in connection with ScreenConnect software.
Given the simplicity and attractiveness of this exploit, we would anticipate that any publicly exposed, vulnerable ScreenConnect instances are very likely at a high risk for compromise in the immediate future.