When companies go to a trade show, many of them do things to try and stand out from the other booths on the floor. Typically you’ll see grand displays of products with compelling videos, or testimonials from high profile customers. Each booth tries to make a lasting impression that you’ll take with you to dinner, your hotel room, and hopefully back to work. At Censys, we created an omnipresent experience for our guests. We built a truly unique product demo that stays with you on and off the showroom floor. It’s something you can show off to your friends at the happy hours and back at the office. We hosted a capture the flag game playable during the Blackhat security conference. The capture the flag as a demo concept spun out of one of the winning projects from the Censys Hackathon and we’re excited to share how we did it, what we learned, and how you can participate.
Capture the Flag for Beginners
A capture the flag (CTF) is an exercise commonly done within the security community to train security experts and employees about the way hackers commonly prod your infrastructure. It starts with a synopsis of the scenario. In ours we said the CISO of the Arvala7 mercenary camp (these are all Mandalorian references) needed to find the best hackers & tools to protect their infrastructure. They said there were nine flags hidden in their infrastructure and challenged us to find all nine.
A flag is simply a string token (e.g. the text ctf{abc123}) hidden somewhere in the infrastructure where an average user is not supposed to be.
For example, one of the hosts Arvala7 setup had the following services:
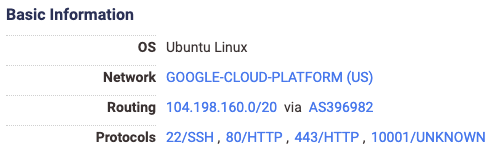
The first thing that catches an attacker’s attention is the unknown service on the non-standard port 10001. Upon further inspection we can see that this service has a rather interesting banner:
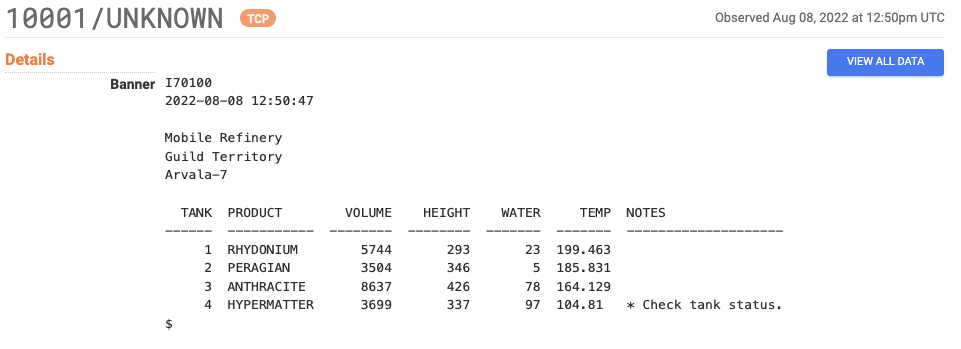
This looks rather similar to another service we index, Automated Tank Gauges (ATGs), which are devices that tell fuel station pump operators and vendors basic information about the gasoline in the tanks under your local gas station.

However, there appears to be one key difference between the two services. The unknown service ends with what looks like the start of a shell. Since this is part of the capture the flag and a host that we trust, we decided to open that shell with netcat. Pro tip – never attempt to open shells or gain access to computers without permission; you have no idea what’s on the other end or who’s watching!
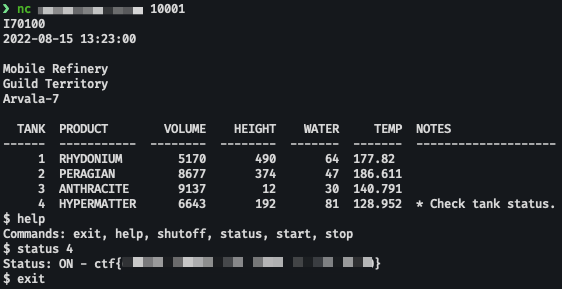
Immediately after entering the shell, we run help to get a list of all possible commands. We can see that there is a status command as well as a note about the status on tank four. After running the status command for tank 4 we find our flag. To get the credit – make sure to enter the flag into our CTF UI as shown.
What Did We Learn
We found that around 45% of participants with little to no prior experience with our app were able to find more than half of the flags, highlighting the simplicity of our search product and the power of the data backing it. We also learned that our users love the level of detail in our individual search results and the fact that they were able to see which services were running on which port. That’s all not to say we don’t have some more work to do to improve the user experience, and the insights we gained about how people approach these challenges like hackers gave us a significant boost in how we can plan for the future of Censys Search.
Missed It? No Problem
We totally understand if Blackhat was a complete blur. If you’re interested in finding out how Censys Search can help you answer questions that only knowing about everything on the internet can answer, or how Censys can illuminate your company’s infrastructure so you can find and fix flaws, give us a call. We can also stand up a CTF demo for you and your team so you can experience the true power of the best internet dataset at your fingertips.