Attack Surface Management
Continuous Internet Asset Discovery and Inventory
Let's get proactive. Discover unknown, unmanaged internet-facing assets.
Know now. Know always.
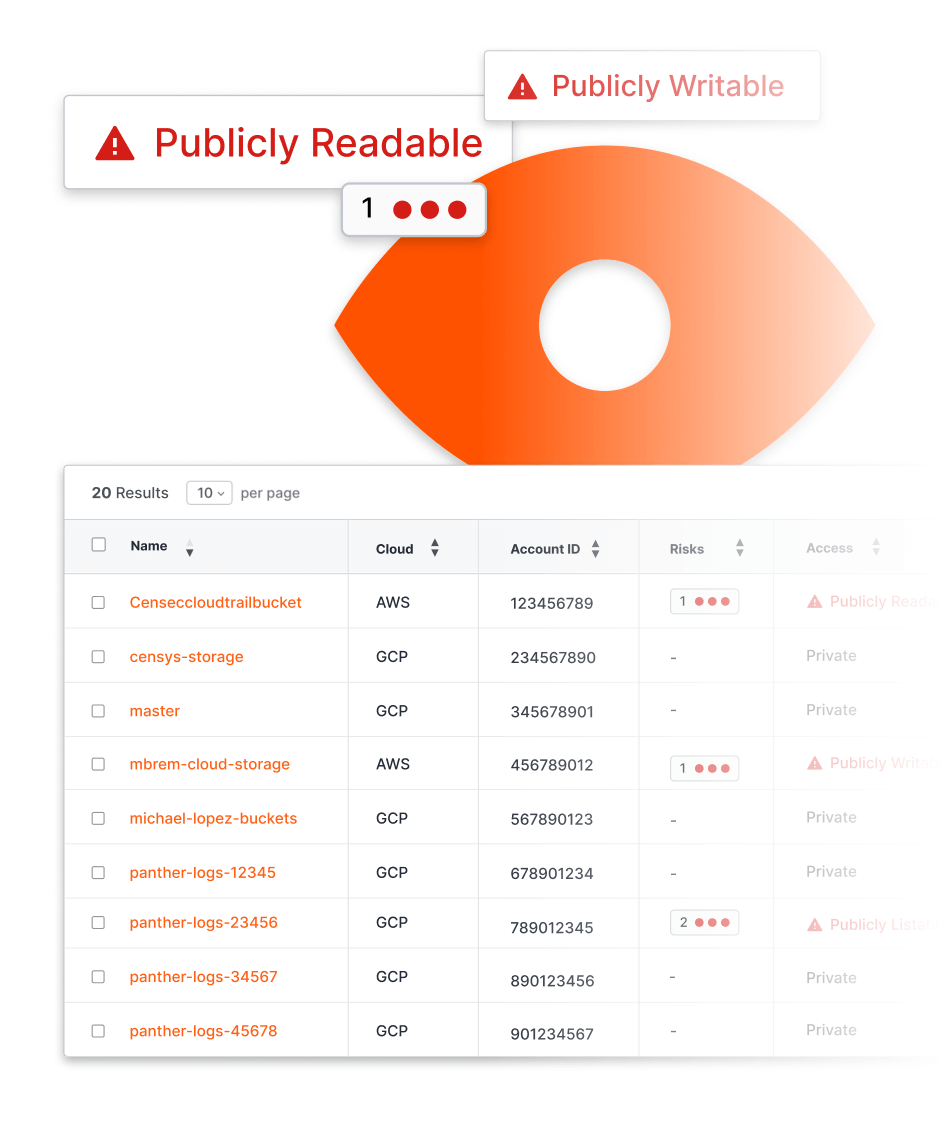
The foundation of Attack Surface Management lies in the initial and ongoing discovery of internet-facing assets and risks. To find unknown assets, Censys ASM continuously trawls internet data sources such as Certificate Transparency logs, passive DNS sinks, and internet scans to uncover assets that you own. Censys discovers unknown and unmanaged internet-facing assets — including services, hosts, websites, storage buckets, and cloud accounts — across all clouds and networks in real time.
Did you know?
50% of enterprises
50% of enterprises will unknowingly and mistakenly have some IaaS storage services, network segments, applications, or APIs directly exposed to the public Internet
Unknown Assets
up to 80% unknown
Censys has found up to 80% of customers' internet-exposed assets are previously unknown to defenders.
Data is dynamic. So are we.
Censys Attack Surface Management provides you with a comprehensive inventory of your internet assets regardless of the network, cloud provider, or account they’re hosted in. As risks to your internet-facing assets are remediated Censys provides a logbook of activity related to your assets giving you an ongoing source of truth for changes to your attack surface.
We never stop.
Discovery scans are performed on several schedules based on the popularity of certain ports and networks in the IPv4 address space. Every day, every known service in our entire dataset is evaluated for its age, and any service older than 24 hours is rescanned to verify its accuracy.
See the world through attackers’ eyes.
Attack Surface Management extends your team’s visibility well beyond what existing tools can provide with its outside-in perspective. While existing tools scan from inside-out, ASM provides the attacker’s view so you know what to secure first. Building your security posture with ASM as the foundation gives your security teams the context they need to prioritize risks and vulnerabilities reported from vulnerability scanners, penetration tests, and cloud security tools.
Featured
Censys Threat Researcher, Mark Eilizey breaks down how to find unauthenticated services that allow users to manage a device remotely via telnet.