Date of Disclosure: July 9, 2024
Date added to CISA KEV: October 22, 2024
CVE-2024-38094, CVE-2024-38024, and CVE-2024-38023 are remote code execution (RCE) vulnerabilities affecting Microsoft Sharepoint. CVE-2024-32987 is an information disclosure vulnerability affecting Microsoft Sharepoint. The Server Subscription Edition, Server 2019, and Enterprise Server 2016 Sharepoint products are all affected by these exploits.
CVE-2024-38094 was added to CISA’s list of known exploited vulnerabilities (KEV) on October 22, 2024. In a recent blog post from Rapid7, their incident response team detailed an active exploitation of Microsoft SharePoint, where attackers leveraged the CVE-2024-38094 vulnerability to gain unauthorized access. This breach allowed the attackers to install malicious tools, disable security defenses, and move laterally across the network, compromising the entire domain. Their post includes various indicators of compromise observed on the victim host following the attack.
The Microsoft SharePoint products affected by these vulnerabilities – namely SharePoint Server Subscription Edition, SharePoint Server 2016 Enterprise, and SharePoint Server 2019 – are often accessible over the internet due to their design for collaboration and document sharing. Organizations commonly configure SharePoint to be internet-facing to support remote access, allowing employees and partners to connect from anywhere.
This exposure can also create security risks if not properly secured with updated patches and configurations. When SharePoint servers must be accessible over the internet, organizations should implement VPN or Zero Trust access, enforce multi-factor authentication, regularly apply patches, and utilize web application firewalls to protect against unauthorized access and exploitation.
| Field |
Details |
| CVE-ID |
CVE-2024-38094 – CVSS 7.2 (High) assigned by Microsoft |
CVE-2024-38024 – CVSS 7.2 (High) assigned by Microsoft |
CVE-2024-38023 – CVSS 7.2 (High) assigned by Microsoft |
CVE-2024-32987 – CVSS 7.5 (High) assigned by Microsoft |
| Vulnerability Description |
CVE-2024-38094, CVE-2024-38024, and CVE-2024-38023 are remote code execution vulnerabilities where the product deserializes untrusted data without sufficiently verifying that the resulting data will be valid. CVE-2024-32987 is an information disclosure vulnerability where the web server receives a URL or similar request from an upstream component and retrieves the contents of this URL, but it does not sufficiently ensure that the request is being sent to the expected destination. |
| Date of Disclosure |
July 9, 2024 |
| Affected Assets |
- Microsoft SharePoint Server Subscription Edition
- Microsoft SharePoint Server 2019
- Microsoft SharePoint Enterprise Server 2016
|
| Vulnerable Software Versions |
Currently unknown |
| PoC Available? |
Yes, PoC code is available here on GitHub for CVE-2024-38094, CVE-2024-38024, and CVE-2024-38023. At the time of writing, we did not observe PoC code available for CVE-2024-32987. |
| Exploitation Status |
CVE-2024-38094 is being actively exploited and appears on CISA KEV. At the time of writing, the remaining vulnerabilities were not observed being actively exploited despite existing PoC code being available for CVE-2024-38024 and CVE-2024-38023. |
| Patch Status |
Microsoft released a security update with links to each of the vulnerabilities addressed in this advisory, including instructions for upgrading to the latest build for each of the affected products. |
Censys Perspective
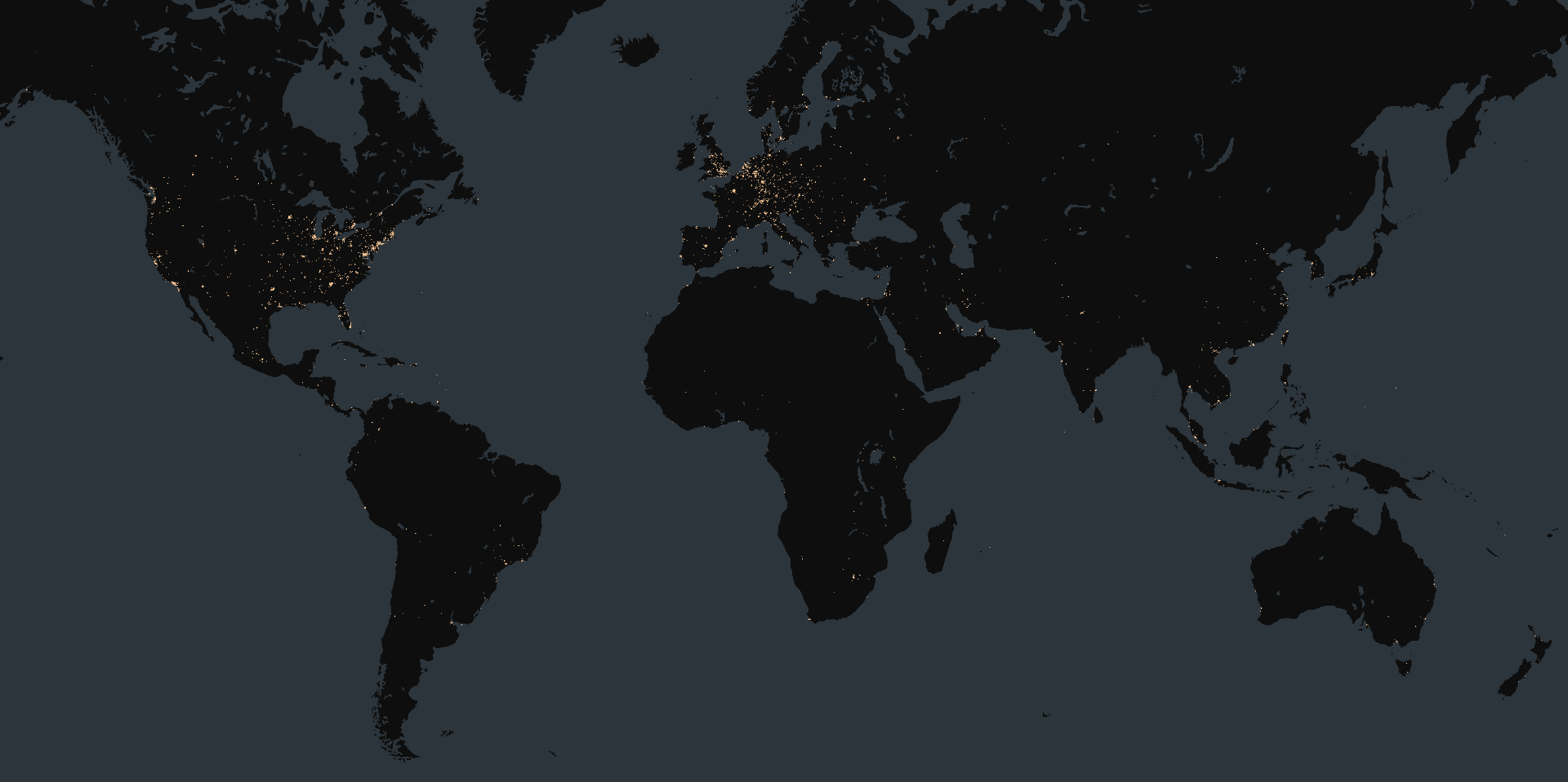
At the time of writing, Censys observed 486,182 exposed Microsoft Sharepoint instances online, filtering out honeypots. The vast majority of these (74%) are geolocated in the United States. Censys observed about 93% of the exposed instances to be associated with Microsoft Corporation (ASN 8075). Note that not all of these are necessarily vulnerable, as specific device versions are not always available.
Map of exposed Microsoft SharePoint instances:
Censys Search Query:
services.software: (vendor="Microsoft" and product="SharePoint") and not labels: {tarpit, honeypot}
Censys ASM Query:
host.services.software.vendor="Microsoft" AND host.services.software.product="SharePoint" and not host.labels: {tarpit, honeypot}
References