TL;DR: Twenty-four ManageEngine products are vulnerable to a pre-auth RCE. Of the services Censys could identify, 70% report a vulnerable software version.
If you’re running one of the many ManageEngine products and have enabled SAML SSO-based authentication, currently or in the past, update it immediately!
Introduction
On January 10th, 2023, details emerged about a vulnerability affecting twenty-four different ManageEngine products that can result in pre-authentication remote code execution (RCE) if SAML authentication has ever been enabled. These vulnerable products use a ten-year out-of-date version of the open-source project “Apache Santuario”. This vulnerability has been assigned CVE-2022-47966.
ManageEngine is a company that develops a wide range of products, from Identity Management to IT ticketing and support systems. These products are found in almost every industry that uses technology: Education, Retail, Manufacturing, Healthcare, and more, and the type of data that an attacker can exfiltrate from a compromised system could be leveraged to move laterally within an organization.
We have found that of the total ManageEngine products Censys can identify, 67% of hosts on the internet are running a version of the software that may be vulnerable to this exploit. We use the word “may” because an administrator must enable SAML SSO authentication on the service (or, in some cases, enabled sometime in the past), and Censys does not have a way to determine if this is the case (we just see the HTTP response).
This issue is a simple exploit wrapped up in complexity, history, and technical wizardry. But before we go into the details of the exposures on the internet, I want to describe the general flow of a SAML SSO authentication request so that we have the right tools to understand why this vulnerability happens and why it is so easy to exploit.
Generally, when a user attempts to log in to a web application that uses SAML-based SSO authentication, the web server will respond with a SAML request. The user’s browser will then forward this request to an “Identity Provider” (defined by the web application and commonly resides on another server); this Identity Provider will then parse this SAML request and authenticate the client (usually by prompting for a username and password). Once the user has authenticated to this Identity Provider, the Identity provider will generate a SAML response, which is sent back to the client’s browser. In turn, the client’s browser will send this SAML response to the original web application. It is now up to the web application to verify that the SAML response is valid and legitimate and came from the identity provider.
This general flow of SAML SSO authentication means a user can modify and tamper with the contents of a SAML response from the Identity Provider before it’s sent back to the web application. In most cases, tampering will be easily identified by the web application since the response contains a cryptographically signed signature validating that the content is correct (XMLDSIG). And this is where things start getting weird.
To perform this message validation, ManageEngine products used the open-source API “Apache Santuario,” which handles the complexity of the XMLDSig specification and the process of verifying the “Signature” section of a SAML response. In older versions of this API, there was a bug where it would process and decode certain elements of this signature section before checking the validity of the entire “Signature” message.
One of the elements in the “Signature” section that will execute before validation includes the ability to do XSLT-based transformations (a Turing-complete system for converting one data type to another) on the input. And since a user can modify the SAML response before it is sent back to the web application, an attacker can pull off an XSLT injection on the server side. A malicious client can construct an XSLT payload so the Java runtime can be loaded by the server and used to execute a process.
If you’re interested in the gritty details about this vulnerability and the previous research around it, we highly recommend a post by the original researcher (archive link). This link is a good starting point for more information about XSLT injection vulnerabilities.
A proof of concept exploit has been released on Github, and exploitability is highly trivial. Rapid7 has reported that this vulnerability has been seen used in the wild and has posted several indicators of compromise in their blog.
Censys Findings
While the advisory is for twenty-four different ManageEngine products, Censys could only find references to nine of the products online and could only determine the running version of seven. That said, we will only cover the details of products we could associate with a version number. You can find all of the reported products in Censys search with this query.
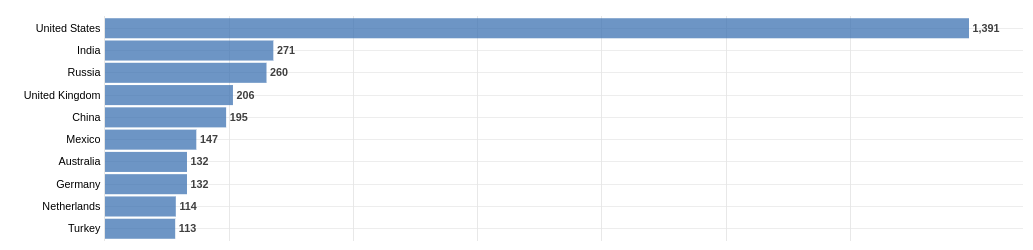
Before going into the version details, here is a breakdown of these products by country, with the United States holding the number one spot with over a thousand unique hosts.
| Product |
Non-Vulnerable Hosts |
Vulnerable Hosts |
Total Hosts |
| ManageEngine ServiceDesk Plus |
1,748 (29.5%) |
4,416 (70.5%) |
6,164 |
| ManageEngine ServiceDesk Plus MSP |
173 (27.64%) |
453 (72.36%) |
626 |
| ManageEngine SupportCenter Plus |
492 (78.22%) |
137 (21.78%) |
629 |
| ManageEngine ADManager Plus |
143 (30.3%) |
329 (69.7%) |
472 |
| ManageEngine AdAudit Plus |
35 (29.91%) |
82 (70.09%) |
117 |
| ManageEngine Asset Explorer |
8 (10.53%) |
68 (89.47%) |
76 |
| ManageEngine ADSelfService Plus |
3 (60%) |
2 (40%) |
5 |
| Total |
2,602 |
5,487 |
8,089 |
ManageEngine ServiceDesk Plus
 |
|
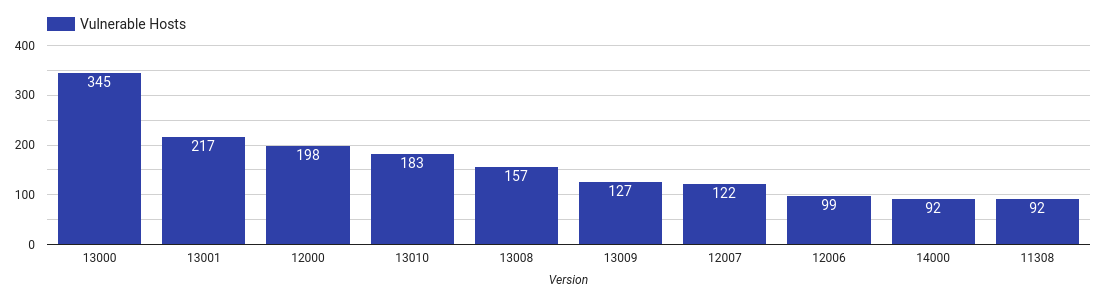
Top 10 vulnerable Service Desk Plus versions
|
This service is a web-based IT service management (ITSM) system primarily used for ticketing, change and incident management. This product is by far the most deployed ManageEngine product that Censys could identify, with over six-thousand hosts on the internet showing signs of it being run. Of those 6,164 hosts, we have found that over 70% display a version vulnerable to this attack.
The reader should note that the service will only be vulnerable if SAML-based SSO has been configured at least once, regardless of the current status. Meaning if an administrator had ever configured it, it is currently vulnerable.
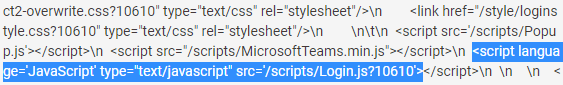
The version can be found in the HTTP response body as an argument to the Javascript inclusion of “/scripts/Login.js,” for example, in the following screenshot, we see the value of “10610”.
ManageEngine ServiceDesk Plus MSP
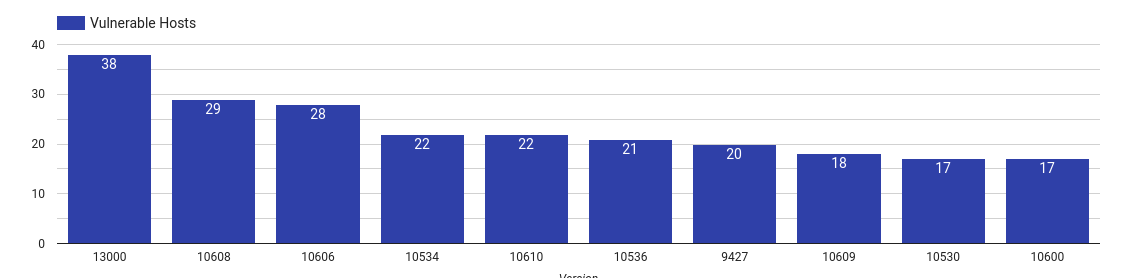 |
| Top 10 vulnerable Service Desk Plus MSP versions |
This is the same service as ManageEngine ServiceDesk Plus but geared towards “Managed Service Providers.”
ManageEngine SupportCenter Plus
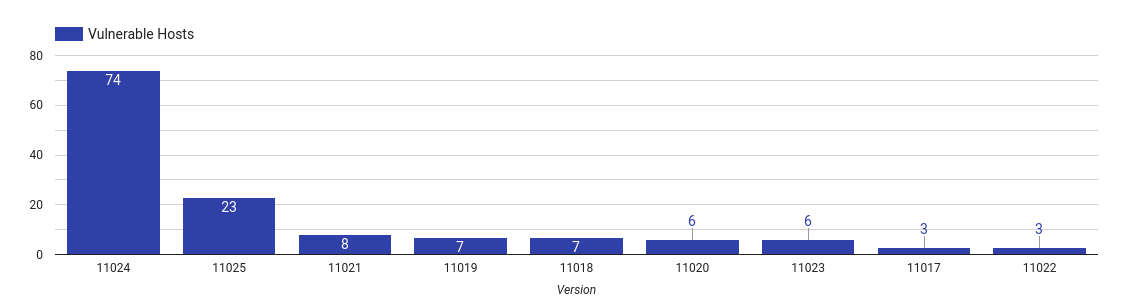 |
|
Top 10 vulnerable SupportCenter Plus versions
|
ManageEngine SupportCenter Plus is a customer service and support software that helps organizations manage customer interactions and service requests.
ManageEngine ADManager Plus
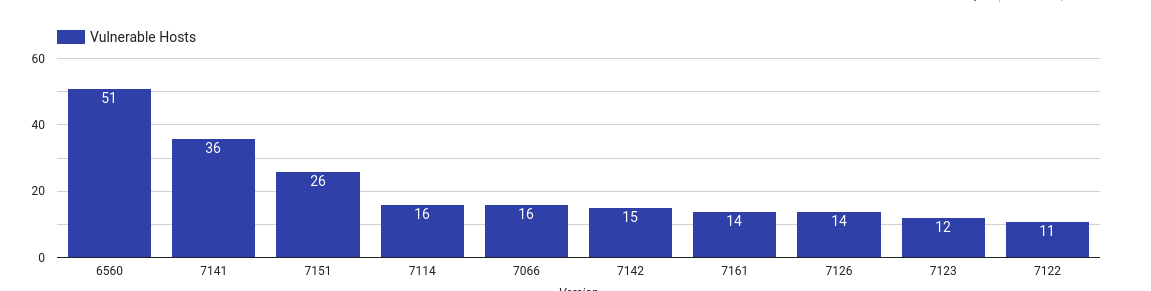 |
|
Top 10 vulnerable ADManager Plus versions
|
ManageEngine ADManger Plus is an Active Directory management and reporting tool.
ManageEngine ADAudit Plus
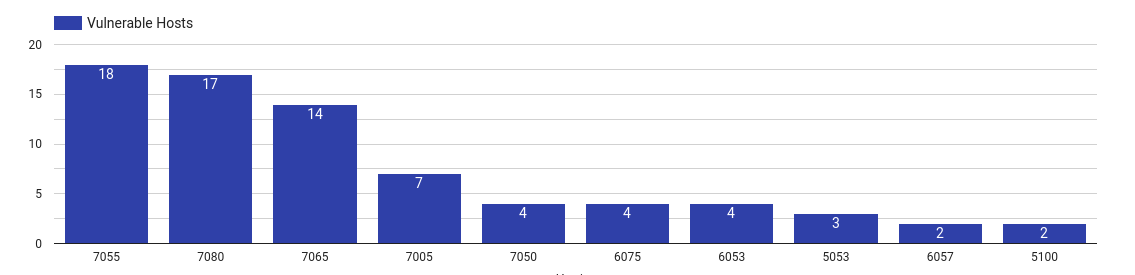 |
|
Top 10 vulnerable ADAudit Plus versions
|
ManageEngine ADAudit Plus provides real-time change notification of an organization’s Active Directory infrastructure. Compromising a system like this could provide an attacker with access to security and compliance audits, and internal information about the systems and networks running inside the organization.
ManageEngine AssetExplorer
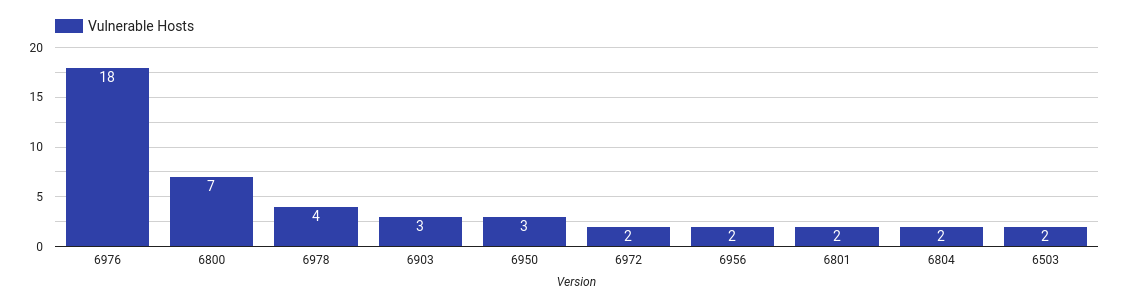 |
|
Top 10 vulnerable AssetExplorer versions
|
ManageEngine AssetExplorer is a web-based tool for infrastructure and inventory management. Along with asset tracking, one can also manage purchase-orders for new infrastructure.
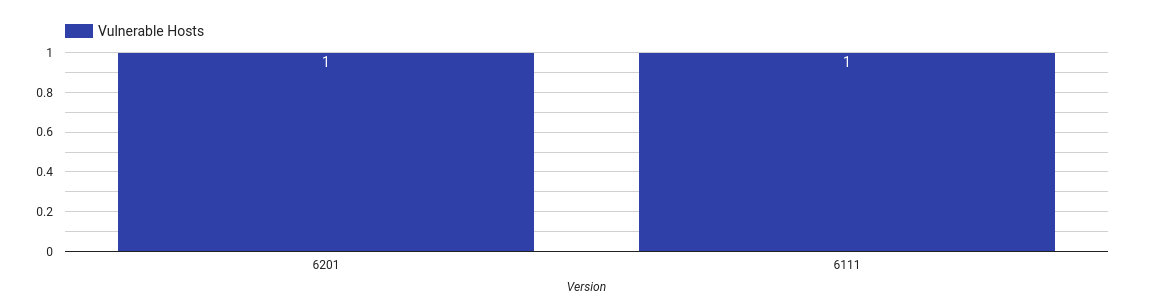
ManageEngine ADSelfService Plus
ManageEngine ADSelfService Plus is a tool that can provide users of an organization the means to reset and change their own passwords. Compromising a system like this could put the entirety of a network at risk.
 |
|
The only two vulnerable ADSelfService Plus versions
|
ManageEngine Key Manager Plus
ManageEngine Password Manager Pro
What can be done?
- ManageEngine users are urged to upgrade to the latest software version.
- Censys ASM customers have access to a risk that will identify both exposed, and outdated versions of the following products:
- ManageEngine ServiceDesk Plus
- ManageEngine ServiceDesk Plus MSP
- ManageEngine SupportCenter Plus
- ManageEngine ADManager Plus
- ManageEngine ADAudit Plus
- ManageEngine AssetExplorer
- ManageEngine ADSelfService Plus