Your phone rings in the middle of the night, and when you answer, it’s a call you’ve been dreading. Your company has been the target of a cyberattack. The fallout? Unknown at the moment, but a million scenarios run through your mind. Has customer data been compromised? How much will this cost our organization? Will we end up on the front page of The New York Times?
Cyberattacks are a growing reality for organizations across all industries. The rise of hybrid work environments and an expanding array of cloud-based assets has made detecting and defending against these attacks increasingly challenging for security teams. When tech expands faster than what IT teams can keep up with, visibility is lost. And what you don’t know, you can’t protect. Companies without a solid strategy for Attack Surface Management can let days, weeks, or even months pass before they’re able to detect a threat.
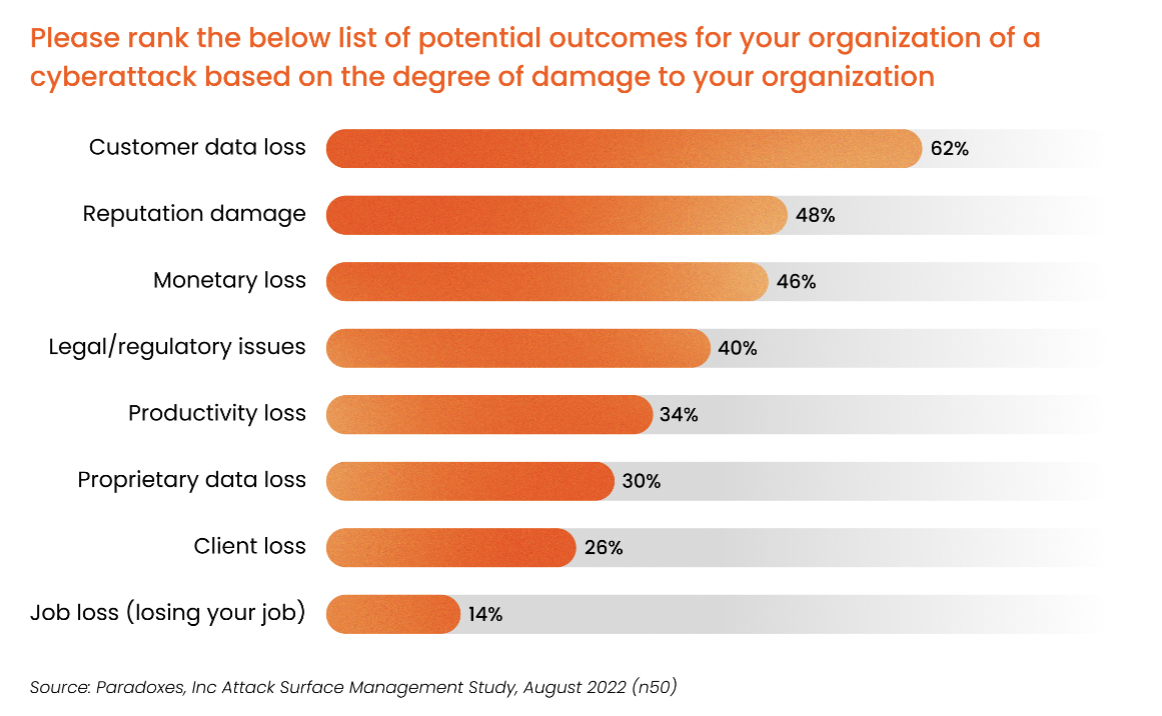
What worries cybersecurity professionals most?
Recent research compiled as part of our 2022 State of the Internet Report found that 62% of security professionals surveyed say customer data loss resulting from a cyberattack is their greatest fear. This was followed by reputation damage, monetary loss, and legal action. Security professionals and business leaders alike know that any one of these consequences can result in major disruption to the organization, and often, create a public relations nightmare.
“[If cybersecurity risks are not mitigated] It would impact productivity, and the success of our company. Ultimately, it could result in catastrophic business destruction.” – CISO, Health Care
When it comes to attack tactics, 70% of professionals surveyed by Paradoxes Inc said that ransomware was the top security threat to their organization. This was followed by phishing/spear phishing attempts (52%) and malware attacks (48%). Preventing and detecting these three threats requires continuous scanning of all of an organization’s assets. That means uncovering any Shadow IT assets that may exist across multiple cloud servers. And if you think your organization couldn’t possibly have any unknown assets – when Censys evaluated the attack surfaces of 37 large organizations, we found that on average, they have 44 different domain registrars and presence in 17 different hosting providers.
“…Every month, I find out about new publicly facing assets we have that I didn’t know about.” – Senior Engineer, Technology
Threat detection, defense, and remediation with Attack Surface Management
An Attack Surface Management platform can provide the continual scanning that can help organizations detect, defend, and remediate the cyberattacks that may threaten your business. ASM’s comprehensive, up-to-date view of your organization’s entire external attack surface provides a better understanding of each asset’s level of exposure, which means stakeholders at all levels of the organization, from software security engineers to your CISO, can do their jobs more effectively can stay one step ahead of threats.
Learn more about avoiding cyberattack worst-case scenarios, and find insights from top security professionals, in our ebook: Threat Detection, Defense & Remediation using ASM.
Download ebook