Advisory
June 27, 2024 Advisory: Critical Command Injection Vulnerability in EOL Zyxel NAS Models Exploited by Botnet [CVE-2024-29973]
June 27, 2024
- Date Published: June 4th, 2024
- CVE-ID and CVSS Score: CVE-2024-29973 (CVSS 9.8 – Critical)
- Issue Name and Description: A critical command injection vulnerability exists in the ‘setCookie’ parameter of certain Zyxel NAS devices that allows unauthenticated remote attackers to execute arbitrary OS commands via a specially crafted HTTP POST request.
- Asset Description: Zyxel NAS (Network Attached Storage) is a centralized file storage device allowing multiple users to access data over a network. This vulnerability specifically affects Zyxel NAS326 and NAS542 models with firmware versions prior to V5.21(AAZF.17)C0. Note that these are both End-of-Life (EOL) products, but a patch is still available from the vendor.
- Vulnerability Impact: If successfully exploited, attackers could gain full control over the affected NAS devices with root privileges, allowing them to execute malicious code, steal sensitive data, install malware, and use the compromised device as a pivot point for further network attacks.
- Exploitation Status:
- A proof-of-concept (PoC) exploit is publicly available.
- While not currently in CISA KEV, this vulnerability has a high EPSS score of 0.93664, indicating a higher likelihood of exploitation.
- As of June 24, 2024, there are reports of this vulnerability being actively exploited by a “Mirai-like botnet” according to Shadowserver.
- As of the time of writing, GreyNoise has detected 3 IPs attempting this exploit against its sensors – 1 of them tagged as being associated with known bot activity
- Patch Availability: Zyxel has released patches for the affected NAS326 and NAS542 models, despite these devices having reached End-of-Life (EoL) status in December 2023. It’s recommended for users to update to firmware version V5.21(AAZF.17)C0 or later
- Censys Perspective: As of June 27, 2024, Censys observed 1,194 exposed Zyxel devices running NAS326 or NAS542. It’s unclear how many of these are patched vs. vulnerable. These are concentrated primarily in Europe – particularly in Italy (197 hosts), Russia (166), Hungary (149) and Germany (144).
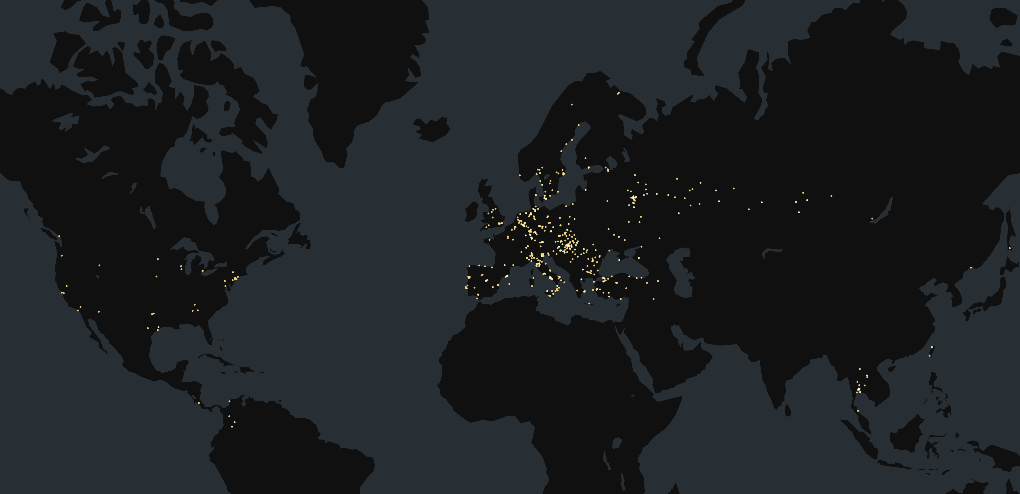
Map of Censys-visible Zyxel NAS326 and NAS542 Devices as of June 27, 2024
- Detection with Censys: The following queries can be leveraged to identify all Censys-visible public-facing Zyxel NAS326 and NAS542 instances. Note that we do not have visibility into firmware versions.
- Censys Search query: services.software: (vendor: “Zyxel” and product: {“NAS326”, “NAS542”})
- Censys ASM query: host.services.software: (vendor: “Zyxel” and product: {“NAS326”, “NAS542″}) or web_entity.instances.software: (vendor:”Zyxel” and product:{“NAS326”, “NAS542”})
- References:
- https://www.zyxel.com/global/en/support/security-advisories/zyxel-security-advisory-for-multiple-vulnerabilities-in-nas-products-06-04-2024
- https://outpost24.com/blog/zyxel-nas-critical-vulnerabilities/
- https://infosec.exchange/@shadowserver/112654674785669239
- https://nvd.nist.gov/vuln/detail/CVE-2024-29973
- https://github.com/RevoltSecurities/CVE-2024-29973